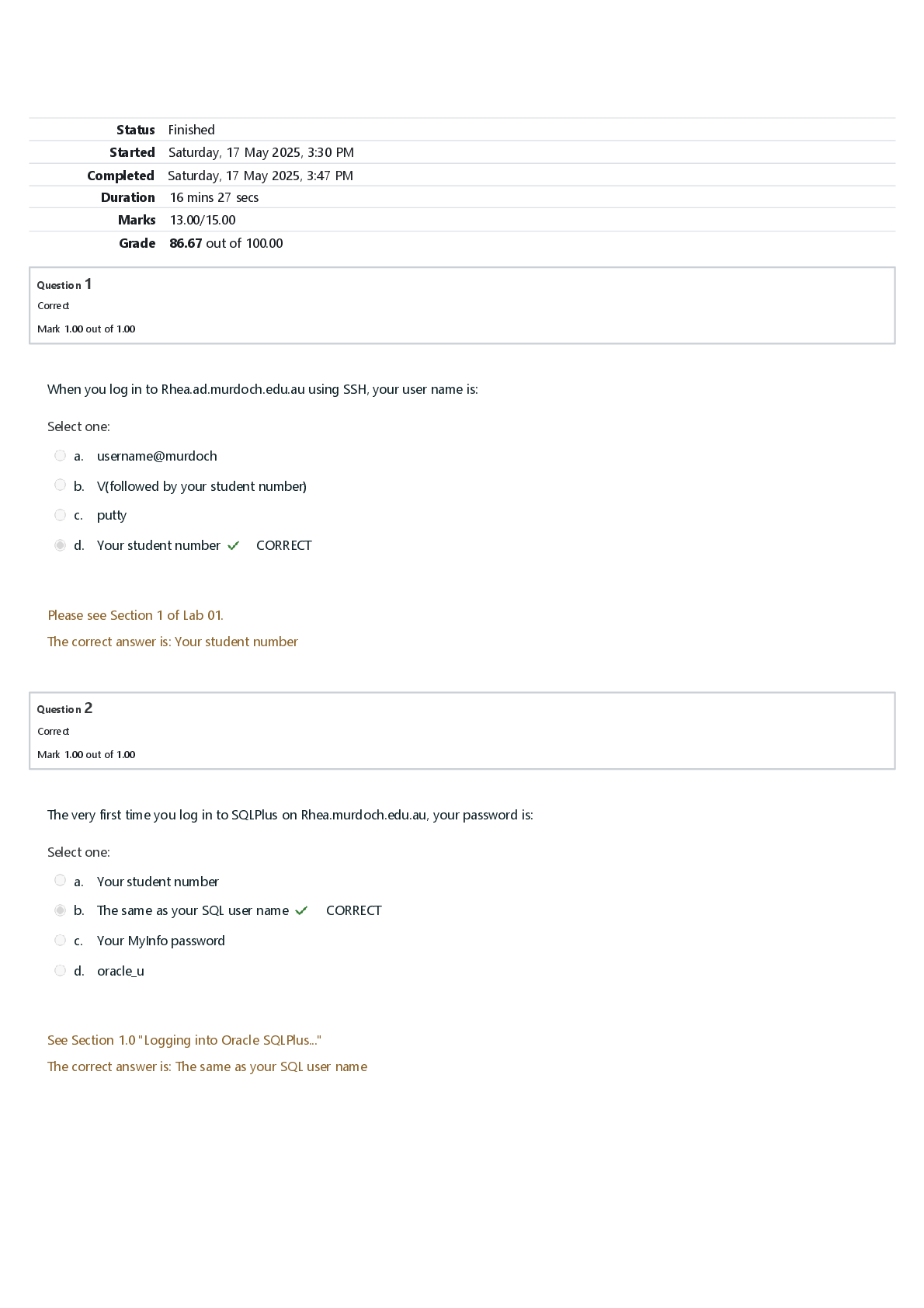
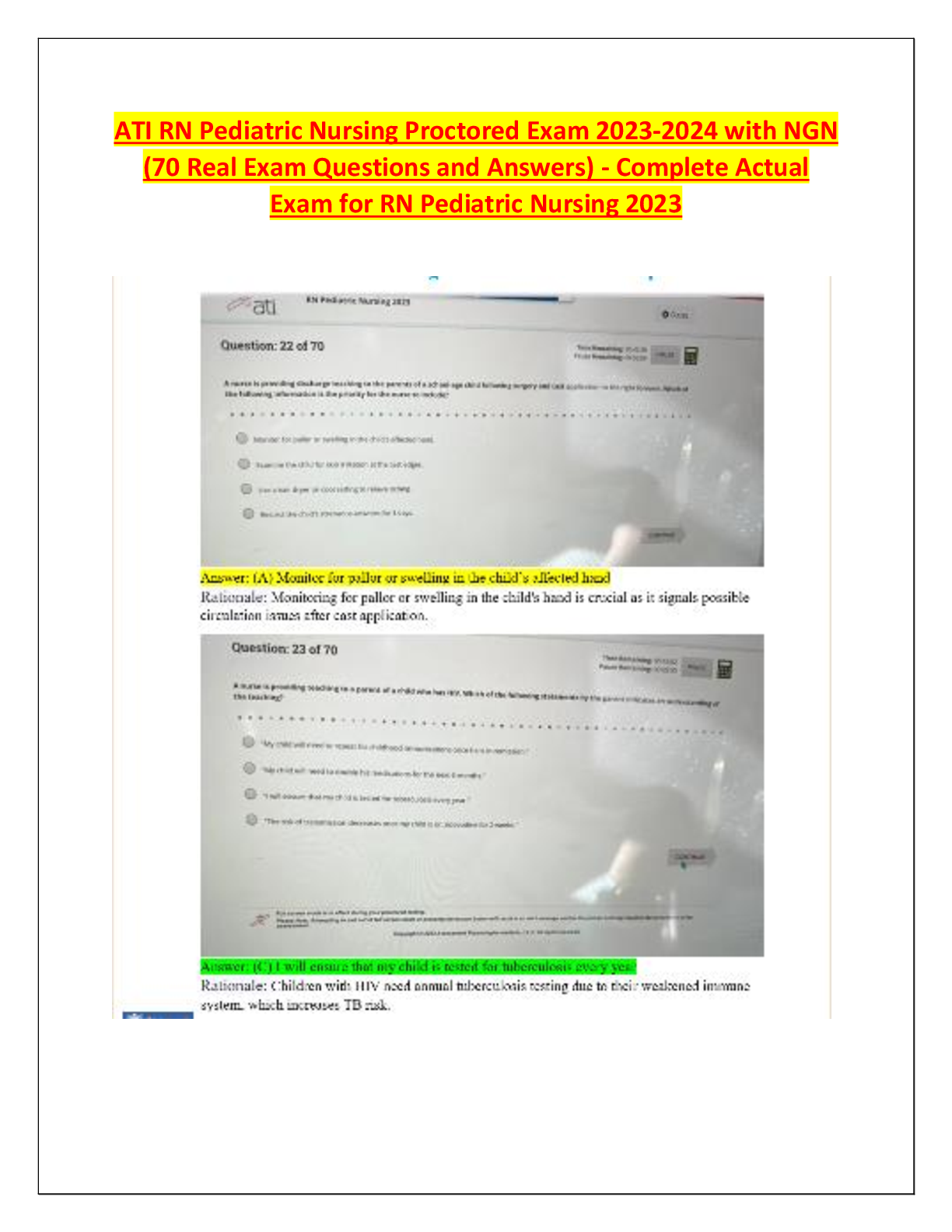
Information Systems Management > EXAM > INFO 360 Final Exam | Answered with complete solutions (All)
INFO 360 Final Exam | Answered with complete solutions
Document Content and Description Below
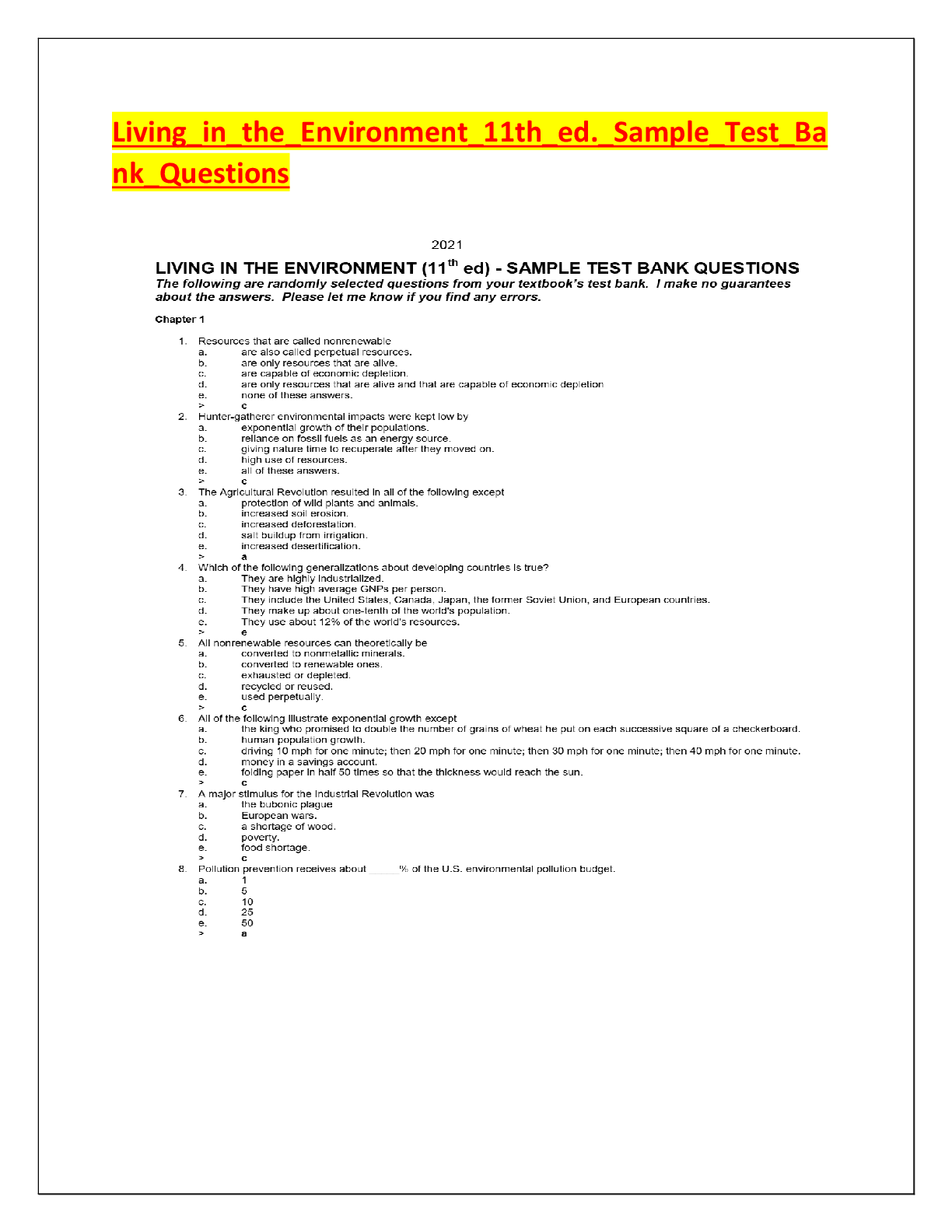
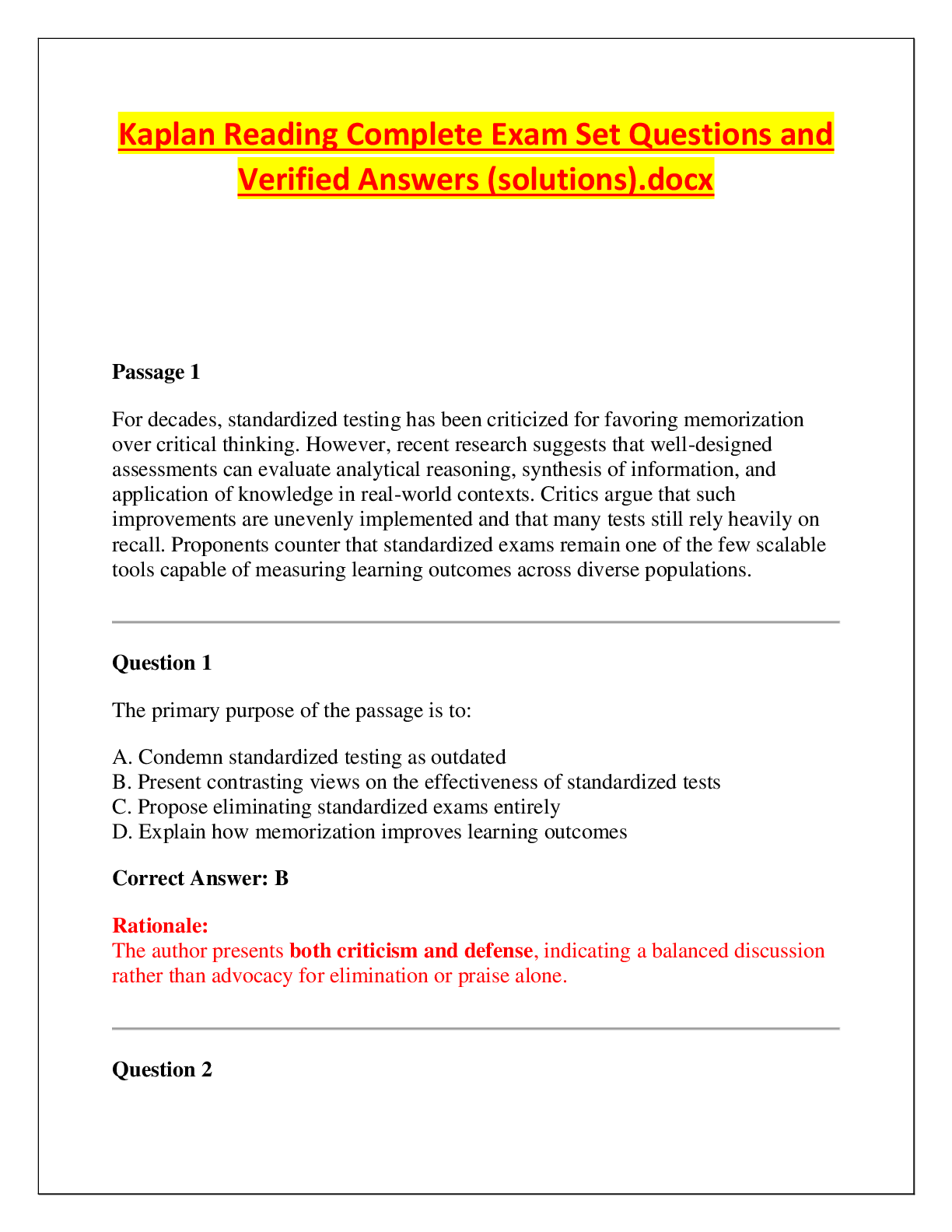
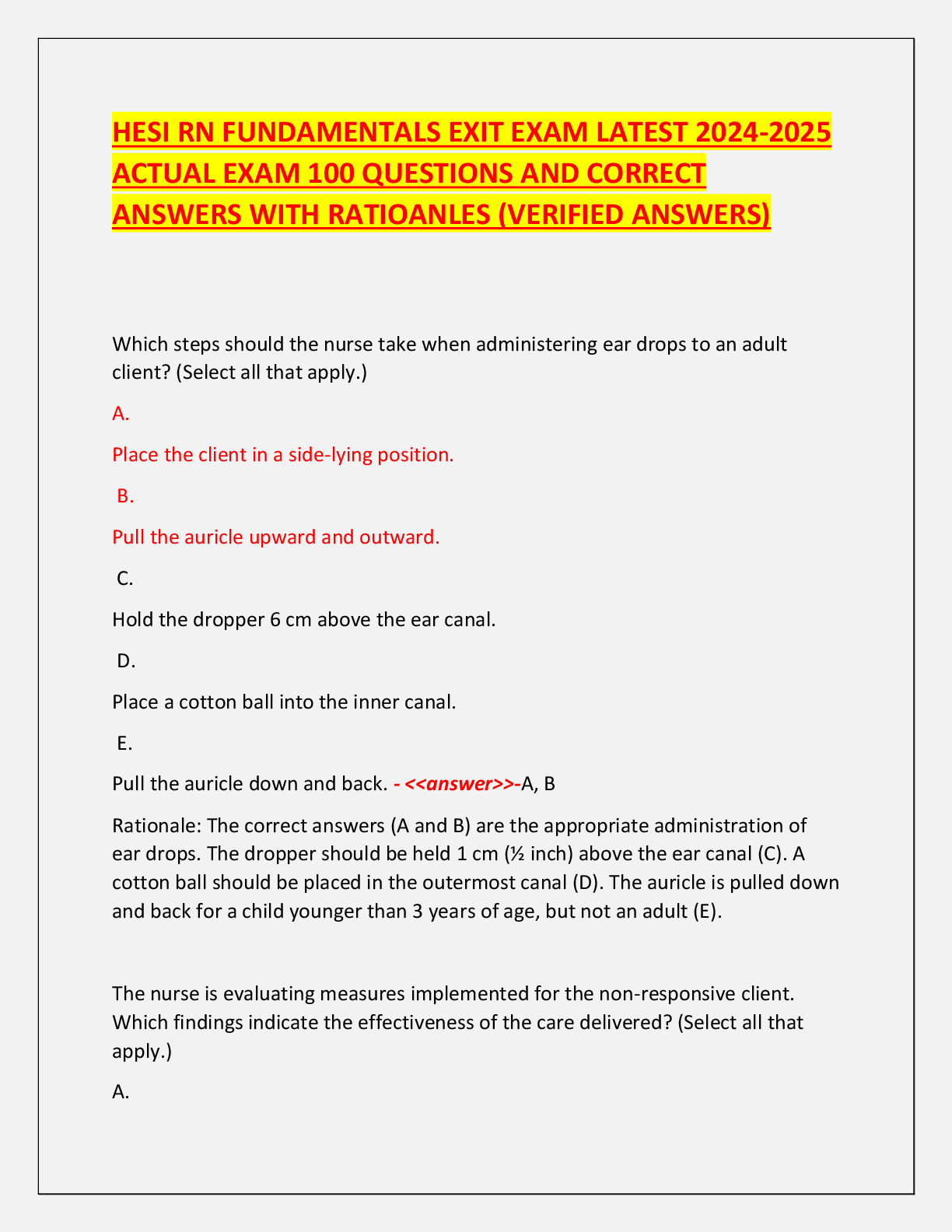
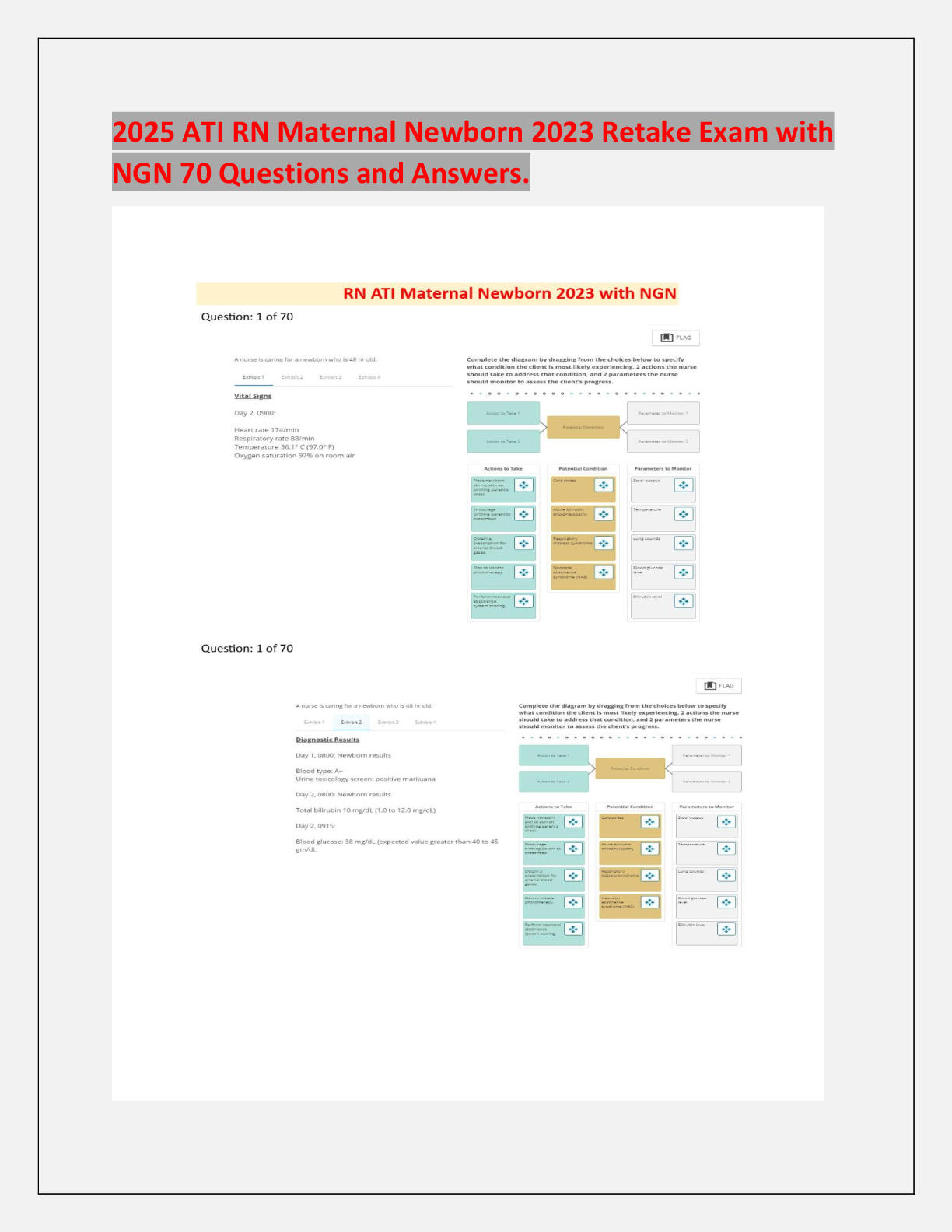
INFO 360 Final Exam | Answered with complete solutions Employee monitoring software observes computer use of all employees from a central location. Cloud computing can best be described as using th ... e Internet to store and access resources Aa common, basic condition for most flextime policies is the requirement that employees must be able to fulfill their work responsibilities, including attending certain meetings or events in-person What function of a micro-networked POS system is responsible for increased accuracy of employees when ringing up customer purchases? the total button which automatically added up the amount owned for items. Mmainframes were originally developed for their reliability of handling transactions. The main function of executive support system (ESSs) is to turn data information to support high-level decision making. A long standing company is expanding their existing workforce. what, in all likelihood, would they invest in terms of computing capabilities? personal computers Who is quoted "Do what you do best and outsource the rest"? Peter Drucker Fayol's principles for structuring organizational roles and authority emphasize order and unity, so that employees understand their roles and report to only one person. In addition to advancements in computer hardware, what drove improvements to POS ( point-of-sale) system in the 1990's? an increasingly diverse group of users and their needs Search engine optimization (SEO) can be _________ through the information gained by web mining Enhanced Popular applications used by today's organizations in web mining included Google Analytics, Data Mining, and _____ Tableau Database reports are useful in many ways; one way a report is used is to provide details about individual records and to create _____ Labels Forms are created using _____ software DBMS Reports offer a way to view, format, and summarize the information in a ____ Database Relational database organize data into ____ based on structured data groupings. Tables One reason to create database policies is to specify the ____ used in database design ( how the data is structured) Rules The DBMS (Database Management System) is designed to administer and ___ a database Organize Data marts are used to track ____, purchase transactions, and the supply chain. Inventories The acronym for Data Governance is DG Someone who possesses the knowledge of processing software, business strategy, and analytical skill to deliver data and reports that guide management and executives as they create well-informed decision making is known as a data Analyst Collections of related fields in a database are referred to as Records In order to be considered open data, databases must provide access rights so that they can be Redistributed The 3-step data visualization process consist of exploring the data sets for patter, then planning for visuals and finally creating your visuals Data analysts must blend facts and data with knowledge about the business or organization Qualitative data that is not categorized is called nominal data. Qualitative data that is categorized (ranked for example) is considered ____ data Ordinal Data-driven decision making (DDDM) can be facilitated through a six-step processes of Ask, Prepare, Process, Analysis, Share, and Act. Which of these steps refers to creating visualizations and presentations for key stakeholders? Share When data is anonymized, the PII is eliminated or encrypted. PII includes names, social security numbers, address, and more and stands for ____ identifiable information Personal SQL allows users to isolate specific information contained in a database, as well as to aid in the selection, creation, addition, and extraction of data from a database. SQL stands for ______ query language. Structured SQL usually pronounced "sequel" is quite useful when working with large data sets. the Q in SQL stands for Query Which of the following is an example of an activity that would be useful during the planning stage of the plan-protect-respond cycle? attempting to exploit flaws from the outside, simulating attacks that a hacker would try How are data in process different from data at rest or data in storage? it is held in the device's RAM until it can be processed by the CPU or GPU The Stored Communications Act prohibits which activity? accessing the communications of an organization without authorization Why is it important to preserve the integrity of data, information, and systems? These assets lose their usefulness and value if their consistency, accuracy, or dependability is compromised. For which type of cybersecurity vulnerability do organizations maintain and share databases of known problems? security weaknesses in operating systems or application software What does the General Data Protection Regulation (GDPR) regulate? how companies protect personal data The NIST Cybersecurity Framework is a voluntary guide for organizations. Why is establishing authentication procedures a common cybersecurity goal? Verifying that users are authorized to access systems, data, and resources is fundamental to preventing their unauthorized use. What part of the plan-protect-respond cycle is occurring when an organization limits access to sensitive documents on a server to only those with the required security clearance? Protect Which statement accurately describes the need to keep sensitive data, information, and systems confidential? It is both a major goal and a requirement for cybersecurity. What occurs during the process optimization step of business process management? Managers adapt (modify) the process to enhance process performance. what is gathering, storing, and searching relevant data known as? Data Science The practice of human resources management originated with or before the ancient Egyptians, who had many scribes and priests dedicated to organizing workforces. Which phase of the project management process involves feasibility studies? Phase 1: initiation phase Along with salary, human resources (HR) managers typically need to track employee hiring dates, marital status, number of dependents, and benefits choices and usage. To ensure this is done correctly, nearly all firms use a system that manages benefits. In addition to the probable outcome, what other information does modern business intelligence software provide? the degree of likelihood of the outcome Which stage of the project management process involves documenting the lessons learned during the project's execution? Closure Stage Because accurate tracking of employee performance will always be critical to good management, most firms invest in a software that manages employee evaluation. Why is the meeting between all project stakeholders and key players scheduled as the final step in the planning phase? the budgets and timelines need to be finalized before stakeholders and key players can understand the scope of the projects and their role within the project The ultimate purpose of a customer relationship management system (CRM) is to increase sales, market share, and profit. Which of the following is an example of an organization using knowledge gained from social media to make better strategic decisions. An organization analyzes engagement with different sponsored posts to determine which ones generate the most engagement with their target audience. If an organization wants to increase user engagement on social media, it wants to increase the conversion rate of its social media posts to interactions with users. What is the purpose of the Twitter report card? It highlights high-performing tweets. Correct. Influencers are introduced to their target audience through the Twitter report card. Which statement best explains why knowing an organization's value proposition is important for creating its social media information system (SMIS)? The organization can increase its exposure and user engagement on social media by designing an SMIS that enables it to reinforce and build on its identified strengths. What do most companies use as their main conduit for reaching and connecting with customers? their website The primary goal of a company's social media strategy is to engage potential customers. What is the final step in the six-step process of creating an SMIS? analyze the collected data Of the listed methods of collecting demographic information, which is the most effective for organizations defining their target market? social media What is the main benefit of having a social media information system (SMIS) that gathers and analyzes a company's social media data? If the data show that a social media campaign is not attracting the desired attention or level of engagement, the company can change its campaign strategies. Which would organizations be interested in the information on interactions and preferences that social media sites can provide? The more an organization knows about users' interactions and preferences, the more strategic their targeting can be. While a religious leader may provide guidance on how to uphold high morals, ________ provide the reasons for acting morally. Ethics The Act that is important in specifically protecting email and VoIP communications is the Electronic Communications Privacy Act. Which step of an ethical analysis is designed to enable a manager to obtain guidance or insights from other managers? searching for precedents Which of the following statements encapsulates the purpose of the Federal Information Security Management Act? protect government assets against cybersecurity events In 2013 the U.N. General Assembly adopted a resolution affirming that the rights held by people offline must also be protected online, calling for its member nations to respect the right to privacy in digital communication. Which of the following statements applies to the real-life impact of this resolution? This sounds good, but users should be aware that digital privacy is not honored by many on the Internet. A company wants to begin monitoring the Internet usage of its office employees to ensure that their working hours are spent productively. What is the least that the company should do to respect its employees' rights to information privacy? Inform employees of the monitoring and obtain their consent. Which dimension of ethical behavior in the digital age includes the question of how much time employees are allowed to spend browsing social media? establishing standards The Act that signed into law to monitor terrorist activities and communications following the 9/11 attacks and the 2001 anthrax attack on Congress is the USA PATRIOT Act/USA Freedom Act. How many dimensions or categories can the ethical concerns of the digital age be divided into? Five A company regularly honors its employee-of-the-month with a congratulatory post on its social media pages. Which standards should the company establish and enforce to best protect the privacy rights of these employees? rules of conduct for how social media followers and visitors respond to the posts Online marketplaces where one consumer sells to another consumer are called consumer-to-consumer (C2C). A sales associate has been hired to write blog posts that will be regularly published on a blog about new beauty products. The blog posts are designed to include the SEO terms that relate to the company's newest skin care product, using the keywords that will also be used in their advertising campaigns. What part of the e-commerce timeline would this be a part of? Implementation E-commerce ________ is the ability of an organization to create a strong presence among consumers in many places, with minimal time constraints, to sell them products and services. Ubiquity The organizations likely to benefit the most from the global reach of e-commerce are those that previously depended on foot traffic into one physical store to sell their products. Online content that has been created and posted by unpaid contributors such as customers or fans of a product or service is referred to as user-generated. Manuel runs a small business that paints residential interiors. He has decided most of his current customers can best be reached by sending out a seasonal email newsletter. He will target new customers by placing ads on Facebook targeted at people located within 20 miles of his business who have searched for house painters. Where would he place this information on an e-commerce presence map? type of presence What does business-to-consumer (B2C) e-commerce replace? brick-and-mortar store locations E-commerce ________ includes creating marketing messages that contain the individual's name, appeal to his/her interests, and take their purchase behavior into account. Personalization M-commerce is a subset of traditional e-commerce. As e-commerce continues to develop, many retailers are likely to maintain some type of "brick-and-mortar" store or physical location primarily because consumers expect integrated shopping experiences that include face-to-face options. Coffee vendors who operate small, drive-up coffee stands find it difficult to charge significantly higher prices than their many competitors do. What aspect of the coffee stand business makes raising prices difficult? its low barriers to entry According to Professor Porter, a business must differentiate itself from its competitors. One method is to encourage customers to believe that an organization provides higher quality goods or better service, then the organization can charge a premium, or gain market share, or (ideally) both. For example, by placing a swoop icon on a sweatshirt, Nike is able to charge a higher price. This methodology is called monopolistic competition. With the increasing presence of Internet e-commerce sites, the force of customers has Increased A business must not only look at its direct competitors, but also must contend with those firms that offer a product that a consumer might alternatively choose. For example, McDonald's and Burger King can be considered competitors and if one firm raises prices the other firm might gain its customers. However, if both firms raise their prices, customers may choose to purchase pizza instead. Porter refers to this as the force of substitutes. Apple uses Corning's glass products for all its devices, such as the Gorilla Glass 6 used in the iPhone 11 series. To ensure that it continues to have a strong relationship with this glass industry leader, Apple has invested nearly $500 million toward Corning's advanced glass research division. By building up this relationship, Apple seeks to maintain some control over which of Porter's 5 forces? Suppliers Professor Michael E. Porter published "How Competitive Forces Shape Strategy" in the Harvard Business Review. In this paper, he described how all organizations must develop plans to deal with certain factors if they wish to succeed, or even continue to exist. These became known as Porter's 5 Forces. Under what type of system are employees encouraged to halt the manufacturing process in the event of a manufacturing error or safety risk? lean manufacturing system When competitors seek to gain competitive advantage through price leadership or by making product improvements, Professors W. Chan Kim and Renee Mauborgne would say they are using a(n) red ocean strategy. Using technology to transform a market or to create an entirely new market is called creating a(n) ________ innovation. Disruptive Management information systems allow managers to build upon an organization's existing strengths to create competitive advantages. What distinguishes the two main types of cybercrimes? their frequency (how often they are committed) As reported by Andrei Ene, one of the worst malware attacks in the last 10 years is the TBT, or Tiny Banker Trojan. How does a firewall work? It determines what Internet traffic can leave or enter a network or computer. What is a characteristic shared by all devices that can be infected by a computer virus? They are connected to the Internet. Recently, TechJury compiled a list of cybersecurity statistics that show the impact of different malware and network attacks. What percentage of cyberattacks are aimed at small businesses? 43% A program that appears to be legitimate but executes an unwanted activity when activated is called a trojan. The security firewall serving Vantage's email program catches an impressive number of both irrelevant and illegitimate messages, to the point where employees usually do not even see them. Occasionally, however, an unsolicited message will catch managing partner Carl's eye. Because one new message looks to come from a potential new client, he's interested but careful, aware that the boutique consulting firm has a very targeted marketing system and clients usually do not appear out of thin air. What type of security concern is causing Carl's suspicion? Phishing One version of this type of malware encrypts a victim's data until a payment is made. Another version threatens to make public a 'victim's personal data unless a payment is made. This type of malware is called ransomware. [Show More]
Last updated: 9 months ago
Preview 4 out of 15 pages

Loading document previews ...
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$15.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Apr 08, 2025
Number of pages
15
Written in
All
Additional information
This document has been written for:
Uploaded
Apr 08, 2025
Downloads
0
Views
13