Computer Science > EXAM > CTC 362 Midterm Exam | Questions with Verified Answers (All)
CTC 362 Midterm Exam | Questions with Verified Answers
Document Content and Description Below
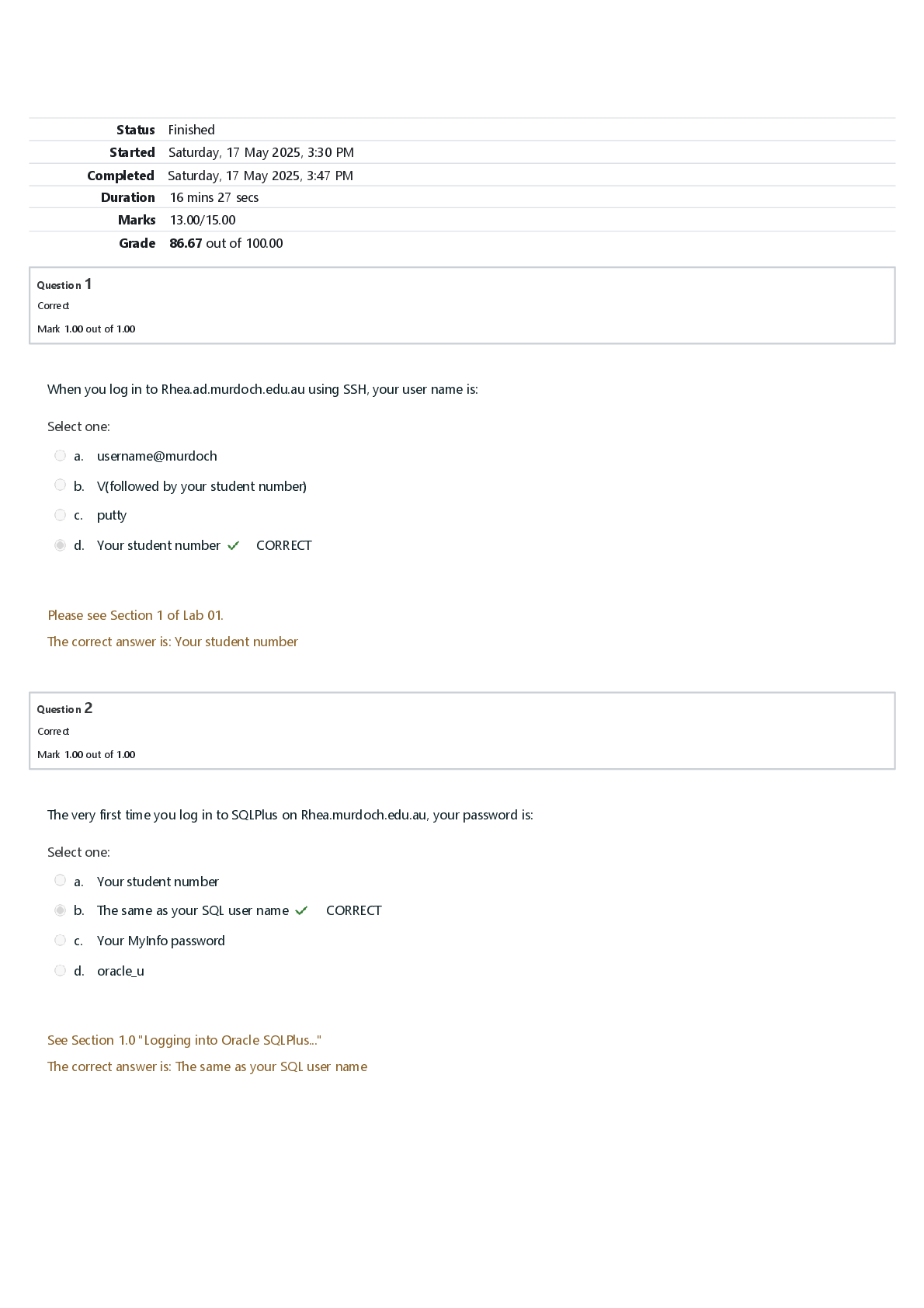
CTC 362 Midterm Exam | Questions with Verified Answers The firewall device must never be accessible directly from the ________________ network. Public ____________________ is a firewall type that k ... eeps track of each network connection between internal and external systems using a table and that expedites the processing of those communications. Stateful packet inspection (SPI) _____________ firewalls combine the elements of other types of firewalls — that is, the elements of packet filtering and proxy services, or of packet filtering and circuit gateways. Hybrid The restrictions most commonly implemented in packet-filtering firewalls are based on __________. a. IP source and destination address b. TCP or UDP source and destination port requests c. Direction (inbound or outbound) d. All of the above Since the bastion host stands as a sole defender on the network perimeter, it is commonly referred to as the __________ host. Sacrificial Which of the following is not a major processing-mode category for firewalls? Router Passthru __________ is the protocol for handling TCP traffic through a proxy server. SOCKS The ____________________ packet-filtering firewall allows only a particular packet with a particular source, destination, and port address to enter through the firewall. Dynamic A ___________ mode VPN establishes two perimeter tunnel servers to encrypt all traffic that will traverse an unsecured network, with the entire client packet is encrypted and added as the data portion of a packet addressed from one tunneling server to another. Tunnel Kerberos is based on the principle that the ____________________ knows the secret keys of all clients and servers on the network. Key Distribution Center (KDC) The dominant architecture used to secure network access today is the __________ firewall. screened subnet SESAME uses ____________________ key encryption to distribute secret keys. Public The primary benefit of a VPN that uses _________ is that an intercepted packet reveals nothing about the true destination system. tunnel mode A(n) ____________________ contains a computer chip that can verify and validate several pieces of information instead of just a PIN. smart card A(n) ______________ filter is a software filter — technically not a firewall — that allows administrators to restrict access to content from within a network Content __________ filtering requires that the filtering rules governing how the firewall decides which packets are allowed and which are denied be developed and installed with the firewall. Static The ____________________ Access Controller Access Control System contains a centralized database, and it validates the user's credentials at this TACACS server. Terminal __________ inspection firewalls keep track of each network connection between internal and external systems. Stateful The application firewall is also known as a(n) ___________ server. Proxy __________ and TACACS are systems that authenticate the credentials of users who are trying to access an organization's network via a dial-up connection. RADIUS A(n) __________ is a private data network that makes use of the public telecommunication infrastructure, maintaining privacy through the use of a tunneling protocol and security procedures. VPN The ____________________ describes the number of legitimate users who are denied access because of a failure in the biometric device. This failure is known as a Type I error. false reject rate The ____________________ authentication system is named after the three-headed dog of Greek mythology, that guards the gates to the underworld. Kerberos A(n) ____________________ dialer is an automatic phone-dialing program that dials every number in a configured range, and checks to see if a person, answering machine, or modem picks up. War In __________ mode, the data within an IP packet is encrypted, but the header information is not. Transport Which of the following version of TACACS is still in use? TACACS+ A(n) ___________ is a combination of hardware and software that filters or prevents specific information from moving between the outside world and the inside world. Firewall Known as the ping service, ICMP is a(n) __________ and should be ___________. common method for hacker reconnaissance, turned off to prevent snooping In most common implementation models, the content filter has two components: __________. rating and filtering The __________ is an intermediate area between a trusted network and an untrusted network. DMZ __________ firewalls examine every incoming packet header and can selectively filter packets based on header information such as destination address, source address, packet type, and other key information Packet-filtering The proxy server is often placed in an unsecured area of the network or is placed in the _______ zone. Demilitarized In Kerberos, a(n) ____________________ is an identification card for a particular client that verifies to the server that the client is requesting services and that the client is a valid member of the Kerberos system and therefore authorized to receive services. ticket A __________ filtering firewall can react to an emergent event and update or create rules to deal with the event. Dynamic Telnet protocol packets usually go to TCP port __________ whereas SMTP packets go to port __________. 23, 25 A packet-____________________ firewall installed on a TCP/IP based network typically functions at the IP level and determines whether to drop a packet (deny) or forward it to the next network connection (allow) based on the rules programmed into the firewall. Filtering __________ firewalls are designed to operate at the media access control sublayer of the data link layer of the OSI network model. MAC layer Terminal emulation, especially the unprotected ____________________ protocol, should be blocked from any access to all internal servers from the public network. telnet A(n) ____________ is a honey pot that has been protected so that it cannot be easily compromised. padded cell A(n) __________ IDPS is focused on protecting network information assets. network-based Some vulnerability scanners feature a class of attacks called _________, that are so dangerous they should only be used in a lab environment. Destructive A packet ____________________ is a software program or hardware appliance that can intercept, copy, and interpret network traffic. Sniffer The ability to detect a target computer's __________ is very valuable to an attacker. operating system __________ applications use a combination of techniques to detect an intrusion and then trace it back to its source. Trap and trace _________ benchmark and monitor the status of key system files and detect when an intruder creates, modifies, or deletes monitored files. HIDPSs A(n) __________ is an event that triggers an alarm when no actual attack is in progress. false attack stimulus Under the guise of justice, some less scrupulous administrators may be tempted to ____________________, or hack into a hacker's system to find out as much as possible about the hacker. back hack A __________ port, also known as a monitoring port, is a specially configured connection on a network device that is capable of viewing all of the traffic that moves through the entire device. SPAN Alarm ____________________ and compaction is a consolidation of almost identical alarms that happen at close to the same time into a single higher-level alarm. Clustering A __________ vulnerability scanner listens in on the network and identifies vulnerable versions of both server and client software. Passive To secure data in transit across any network, organizations must use ____________________ to be assured of content privacy Encryption The attack ____________________ is a series of steps or processes used by an attacker, in a logical sequence, to launch an attack against a target system or network. Protocol In ____________ protocol verification, the higher-order protocols are examined for unexpected packet behavior, or improper use. application Intrusion __________ activities finalize the restoration of operations to a normal state and seek to identify the source and method of the intrusion in order to ensure that the same type of attack cannot occur again. Correction To use a packet sniffer legally, the administrator must __________. be on a network that the organization owns be under direct authorization of the network's owners have knowledge and consent of the content's creators Using __________, the system reviews the log files generated by servers, network devices, and even other IDPSs. LFM __________ is the action of luring an individual into committing a crime to get a conviction. Entrapment A(n) ____________________ system contains pseudo-services that emulate well-known services, but is configured in ways that make it look vulnerable to attacks. Honeypot Activities that scan network locales for active systems and then identify the network services offered by the host systems is known as __________. Fingerprinting In order to determine which IDPS best meets an organization's needs, first consider the organizational environment in technical, physical, and political terms. True HIDPSs are also known as system ____________________ verifiers. Network The ongoing activity from alarm events that are accurate and noteworthy but not necessarily significant as potentially successful attacks is called ____________________. Noise When the measured activity is outside the baseline parameters, it is said to exceed the ____________________ level. Clipping ____________________ is the process of attracting attention to a system by placing tantalizing bits of information in key locations. Enticement In TCP/IP networking, port __________ is not used. 0 Network Behavior Analysis system __________ sensors are typically intended for network perimeter use, so they would be deployed in close proximity to the perimeter firewalls, often between the firewall and the Internet border router to limit incoming attacks that could overwhelm the firewall. Inline With a(n) ____________________ IDPS control strategy all IDPS control functions are implemented and managed in a central location. Centralized Which of the following ports is commonly used for the HTTP protocol? 80 A(n) ___________-based IDPS resides on a particular computer or server and monitors activity only on that system. Host _________ is the process of classifying IDPS alerts so that they can be more effectively managed. Alarm filtering To determine whether an attack has occurred or is underway, NIDPSs compare measured activity to known __________ in their knowledge base. Signatures A(n) ____________________ IDPS can adapt its reactions in response to administrator guidance over time and circumstances of the current local environment. Smart __________ is a systematic survey of all of the target organization's Internet addresses. Fingerprinting ________ are usually passive devices and can be deployed into existing networks with little or no disruption to normal network operations. NIDPSs A(n) ____________________ occurs when an attacker attempts to gain entry or disrupt the normal operations of an information system, almost always with the intent to do harm. intrusion Most network behavior analysis system sensors can be deployed in __________ mode only, using the same connection methods as network-based IDPSs. Passive A(n) __________ works like a burglar alarm in that it detects a violation (some system activities analogous to an opened or broken window) and activates an alarm. IDPS Security tools that go beyond routine intrusion detection include honeypots, honeynets and padded cell systems. True A(n) ____________________ vulnerability scanner is one that initiates traffic on the network in order to determine security holes. Active When a collection of honeypots connects several honeypot systems on a subnet, it may be called a(n) ___________. Honeynet _________ testing is a straightforward testing technique that looks for vulnerabilities in a program or protocol by feeding random input to the program or a network running the protocol. Fuzz A(n) __________ is a software program or hardware appliance that can intercept, copy, and interpret network traffic. packet sniffer Intrusion detection and prevention systems perform monitoring and analysis of system events and user behaviors. True ___________________ scanning will allow the Nmap user to bounce your scan across a firewall by using one of the idle DMZ hosts as the initiator of the scan. Idle __________ is an integrated system of software, encryption methodologies, protocols, legal agreements, and third-party services that enables users to communicate securely. PKI _________ functions are mathematical algorithms that generate a message summary or digest to confirm the identity of a specific message and to confirm that there have not been any changes to the content. Hash [Show More]
Last updated: 1 year ago
Preview 1 out of 16 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$15.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Oct 30, 2024
Number of pages
16
Written in
All
Additional information
This document has been written for:
Uploaded
Oct 30, 2024
Downloads
0
Views
15