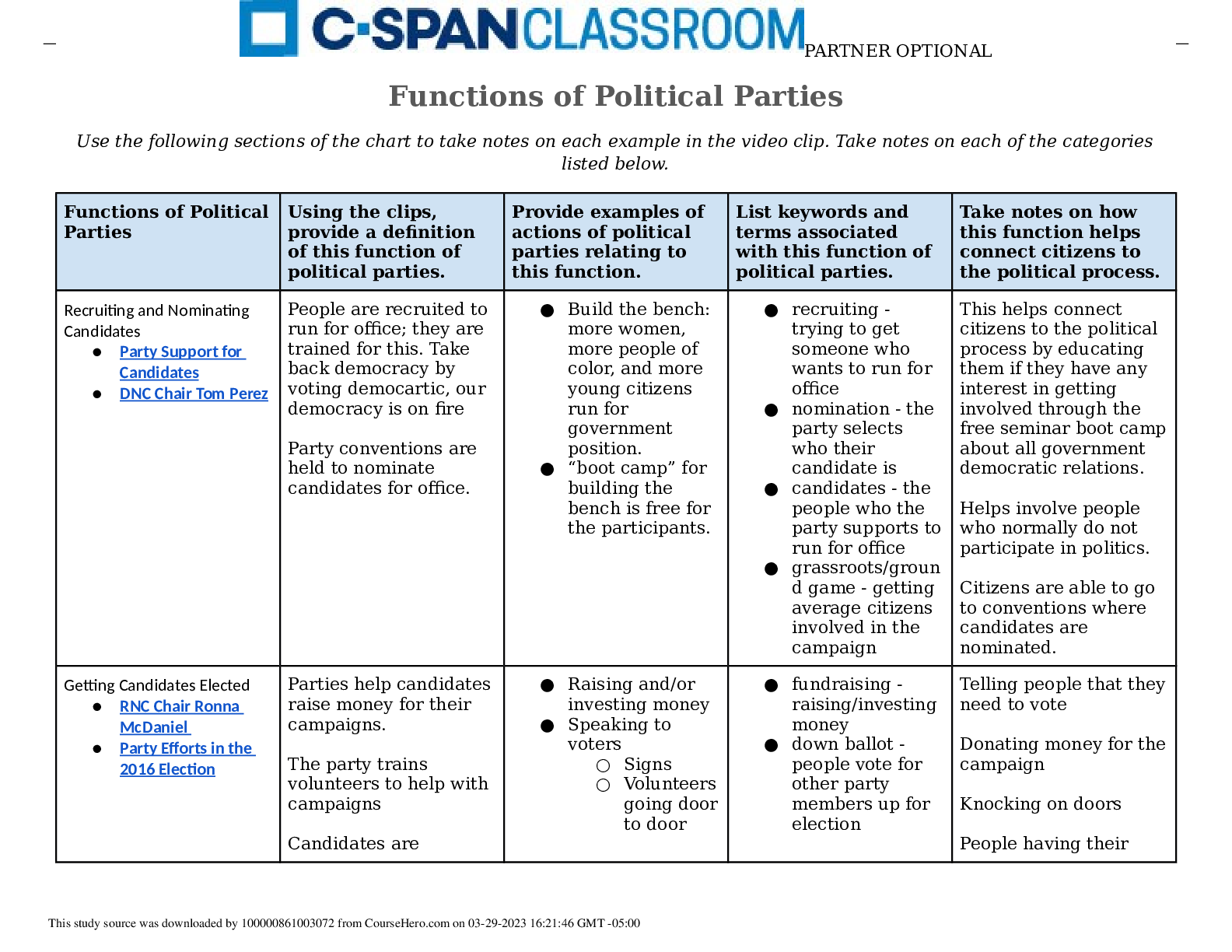
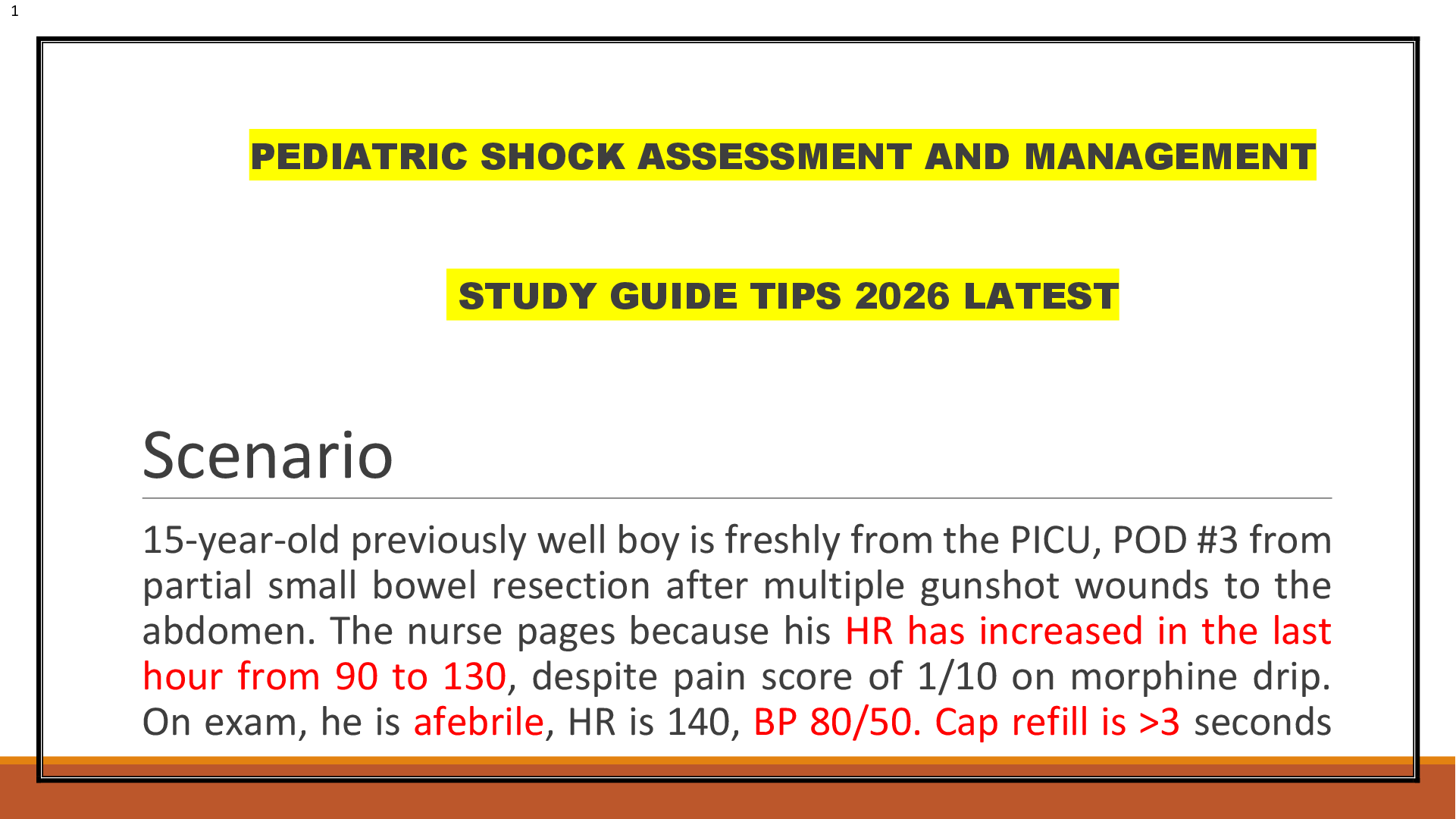
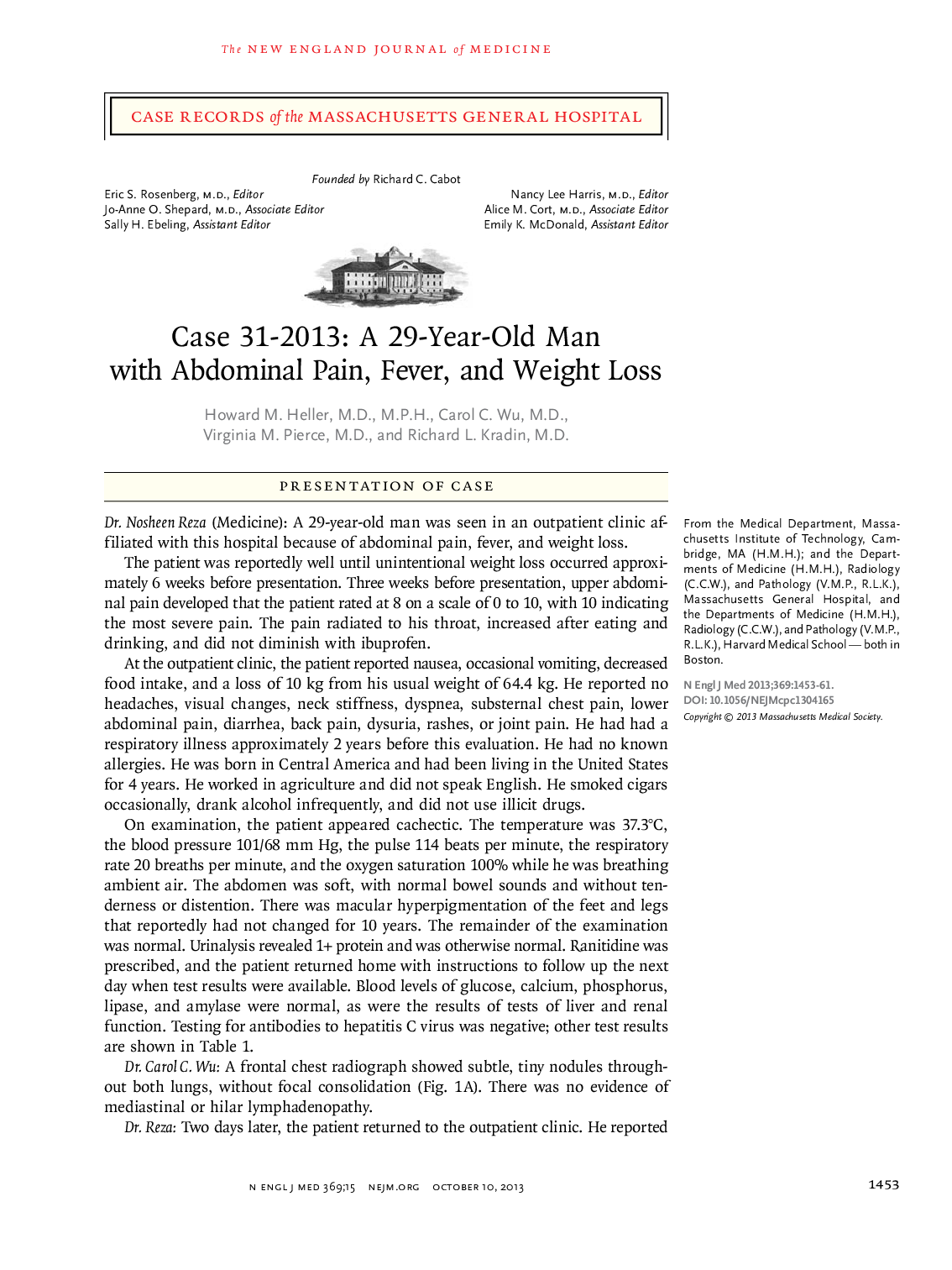
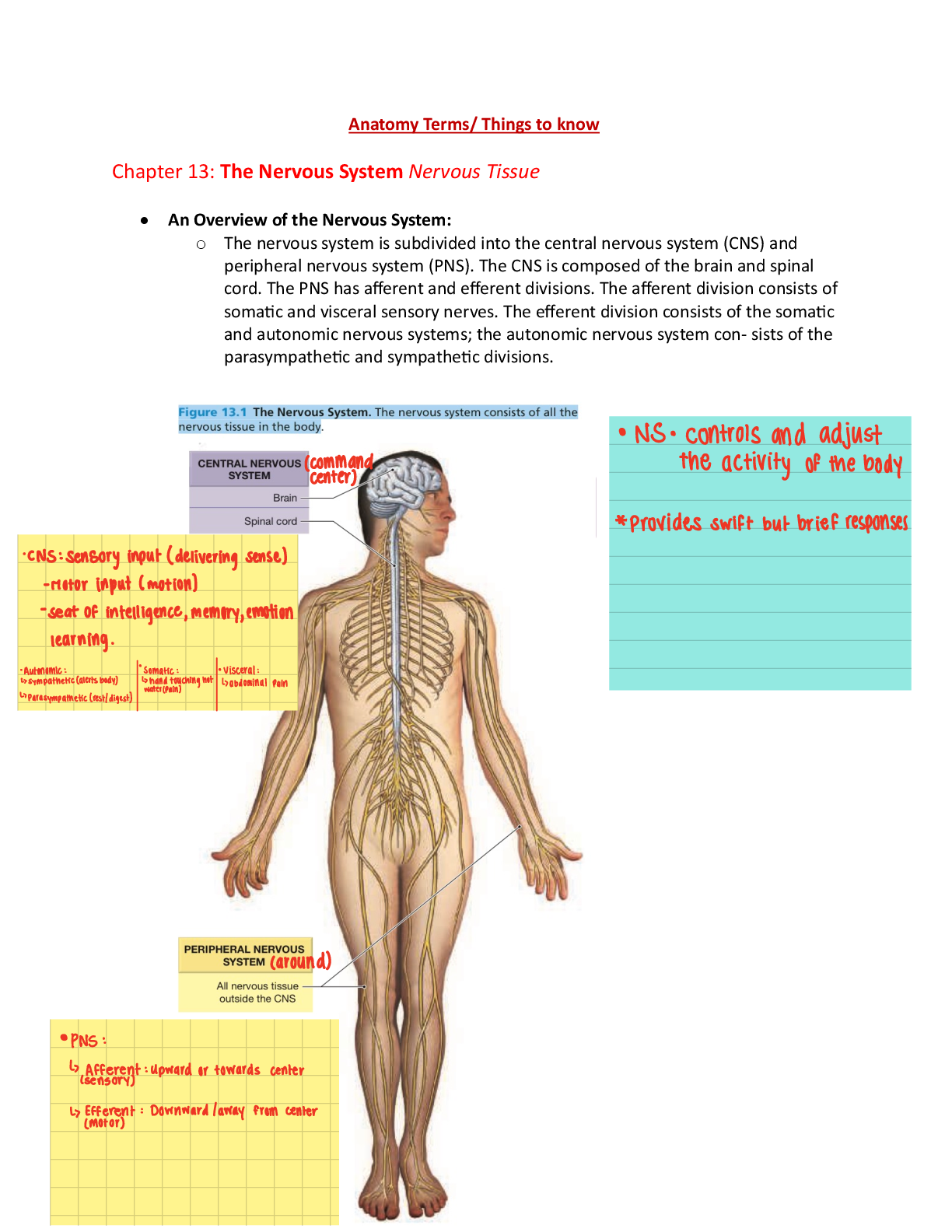
RN VATI Adult Medical Surgical 2019. Questions and Answers.
$ 11
APEA FNP PREDICTOR EXAM TEST BANK SPECIFIC TO 2025-2026 SITTING EXAM
$ 35.5

NURS 101 | Introduction to Nursing | Kaplan Level I | Highline College | 2025
$ 11.5

AQA AS CHEMISTRY 7404/2 Paper 2 Organic and Physical Chemistry Mark scheme June 2021 Version: 1.0 Final
$ 7.5

Kami__Pablo_Cantu__Gizmo waves_2022__Examinable
$ 7

AQA A-level PHYSICS 7408/1 Paper 1 Mark scheme June 2021 Version: 1.0 Final
$ 12

Praxis Test 3, praxis test 4, PRAXIS SLP, ETS Praxis Review 2, Praxis Review test 1 & 2
$ 10

PROJ 420 Week 7 Course Project Final Paper: The RMP
$ 15

2506 8MA0-21 EDEXCEL AS Statistics – June 2025 mark scheme
$ 2.5

A-level FRENCH 7652/1 Paper 1 Listening, Reading and Writing Mark scheme June 2021 Version: 1.0 Final
$ 5.5

NR 565 Week 8 Reflection Assignment (LATEST UPDATE)
$ 11

eBook (EPUB) Artificial Intelligence in Healthcare Emphasis on Diabetes, Hypertension, and Depression Management 1st edition By Gourav Bathla, Sanoj Kumar, Harish Garg, Deepika Saini
$ 30
 (1).png)
OCR Interchange A Level Physics B (Advancing Physics A+) H557/03 Practical skills in physics
$ 12

(WOCNCB) CWCN-AP Domain I Comprehensive Assessment Comprehensive Pre - Assessment Guide Q & S 2024
$ 11

Report > Porter's Five Forces Analysis of the App-Based Taxi Industry Metropolitan State University Of Denver_ MBA 604, D1: Managerial Economics
$ 4

AQA AS PHYSICS PAPER 2 SECTION 1 - 5 EXAM GUIDE QNS & ANS MAY 2024
$ 11

Pearson Edexcel Level 3 GCE 9ST0/01 Statistics Advanced PAPER 1: Data and Probability question paper 1 j une 2023 + mark scheme
$ 10

Solutions Manual for Fundamentals of Open Channel Flow, 2nd Edition By Glenn Moglen