
SBA LOAN (UPGRADED METHOD) BY RANHACKER 2021
$ 7

eBook The Shape of Space (Textbooks in Mathematics) 3rd Edition By Jeffrey R. Weeks
$ 29
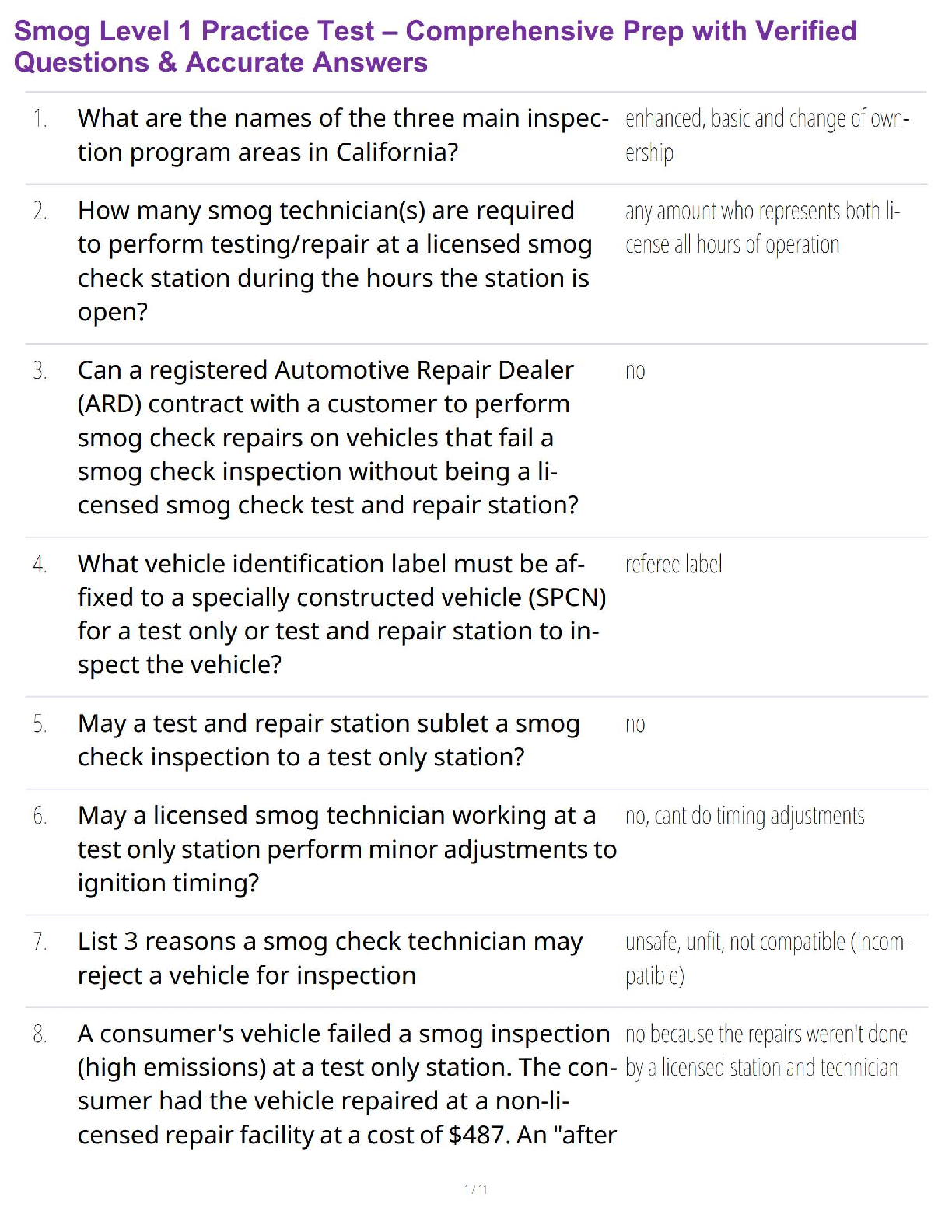
Smog Level 1 Practice Test – Comprehensive Prep with Verified Questions & Accurate Answers
$ 12.5

WGU C777 Unit 1: HyperText Markup Language(Solved)2022 Latest Update
$ 9

Environmental Chemistry, 10e Stanley E Manahan (Answer Manual)
$ 25

Structure and Function of the Cardiovascular and Lymphatic Systems Huether & McCance: Understanding Pathophysiology, 6th Edition MULTIPLE CHOICE
$ 11

INT222 – CA 3 Format | Advanced Web Development (Lovely Professional University, Computer Science and Engineering) | Complete Guide with Verified Solutions | 100% Accurate | Grade A
$ 15

PEARSON EDEXCEL AS LEVEL FURTHER MATHS PAPER 28 AS Decision Mathematics 2 June 2023 | MARKSCHEME
$ 9

AZ 104 Renewal assessment for Microsoft Certified: Azure Administrator Associate - Questions 2022

.png)

.png)

.png)
.png)














