Computer Science > EXAM > CS 345 Quiz 4 | With 100% Correct Answers (All)
CS 345 Quiz 4 | With 100% Correct Answers
Document Content and Description Below
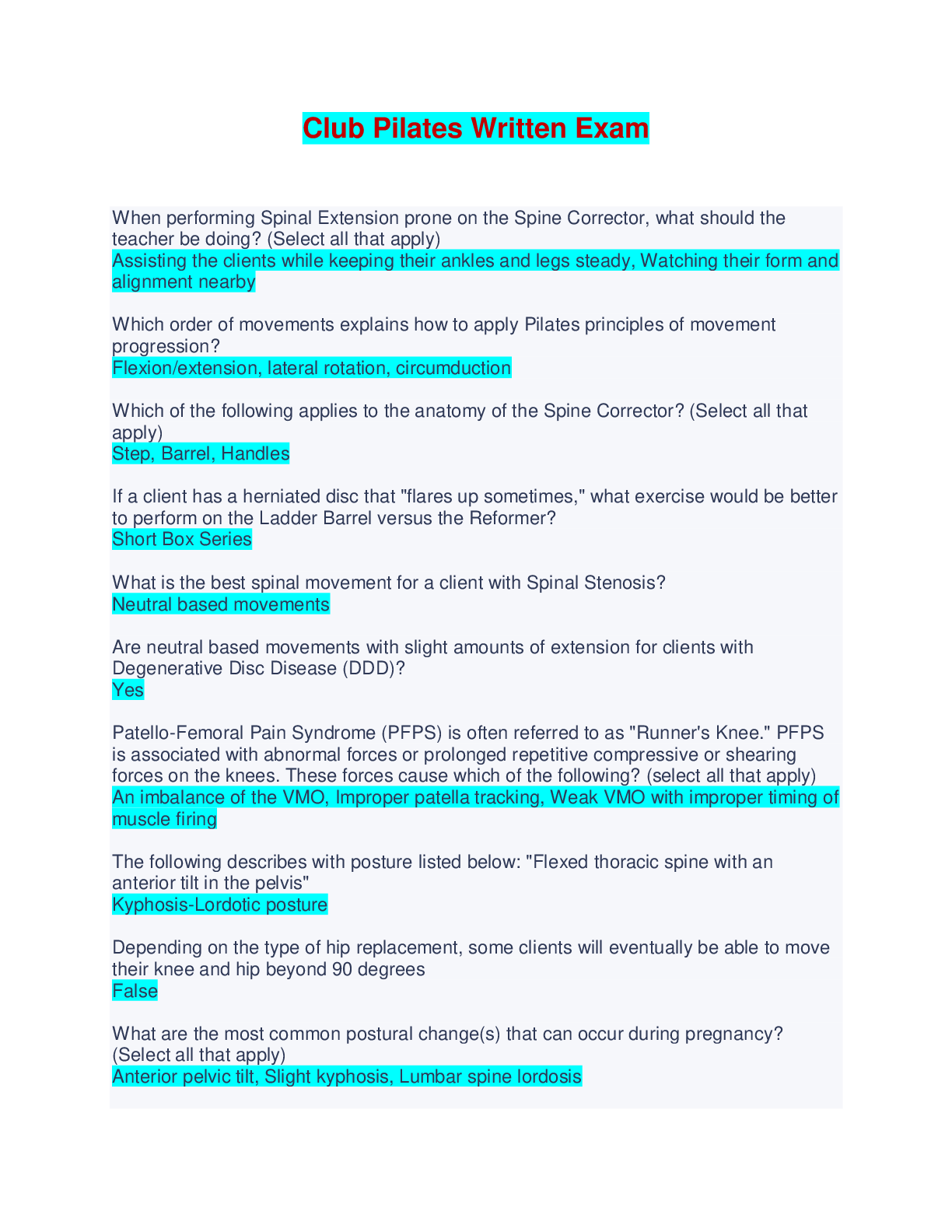
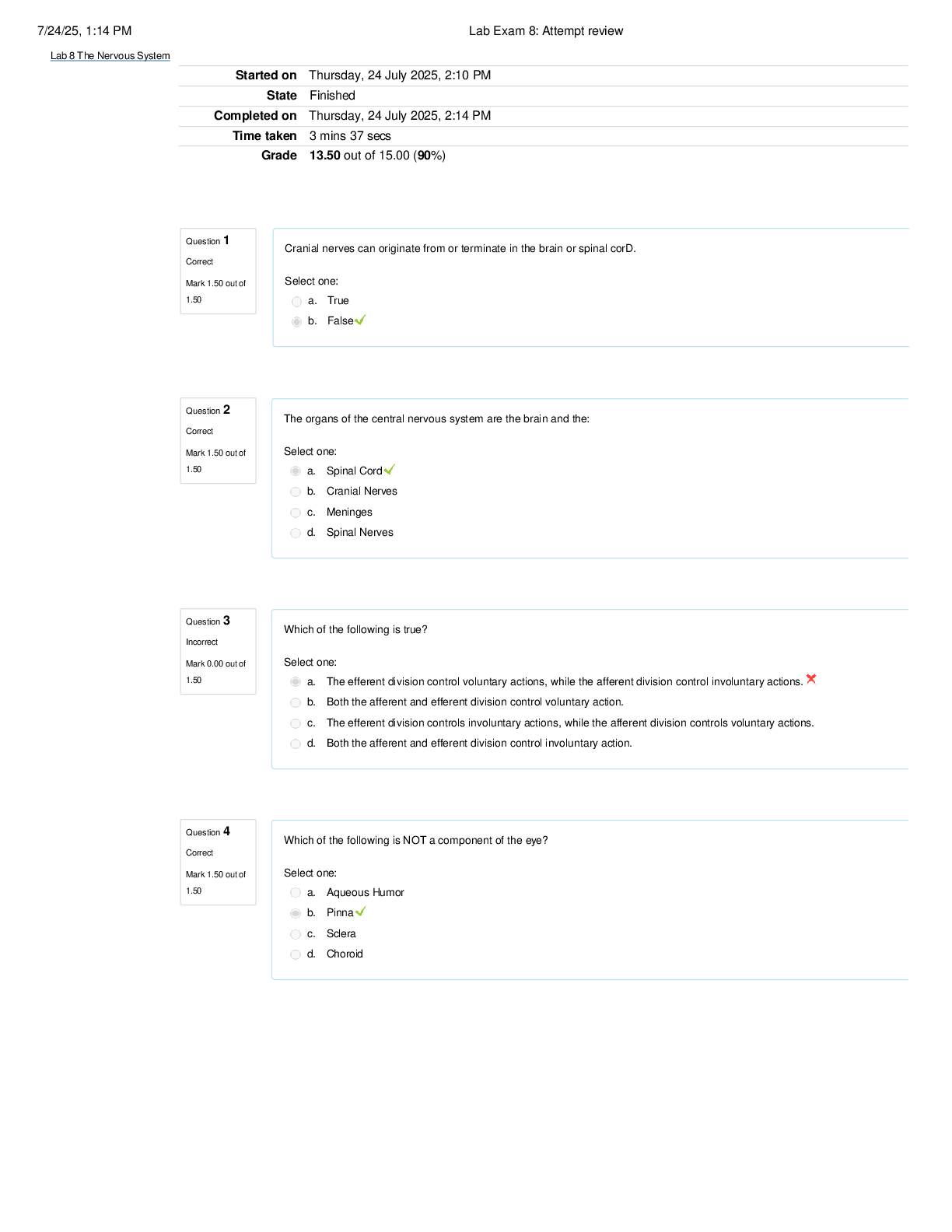
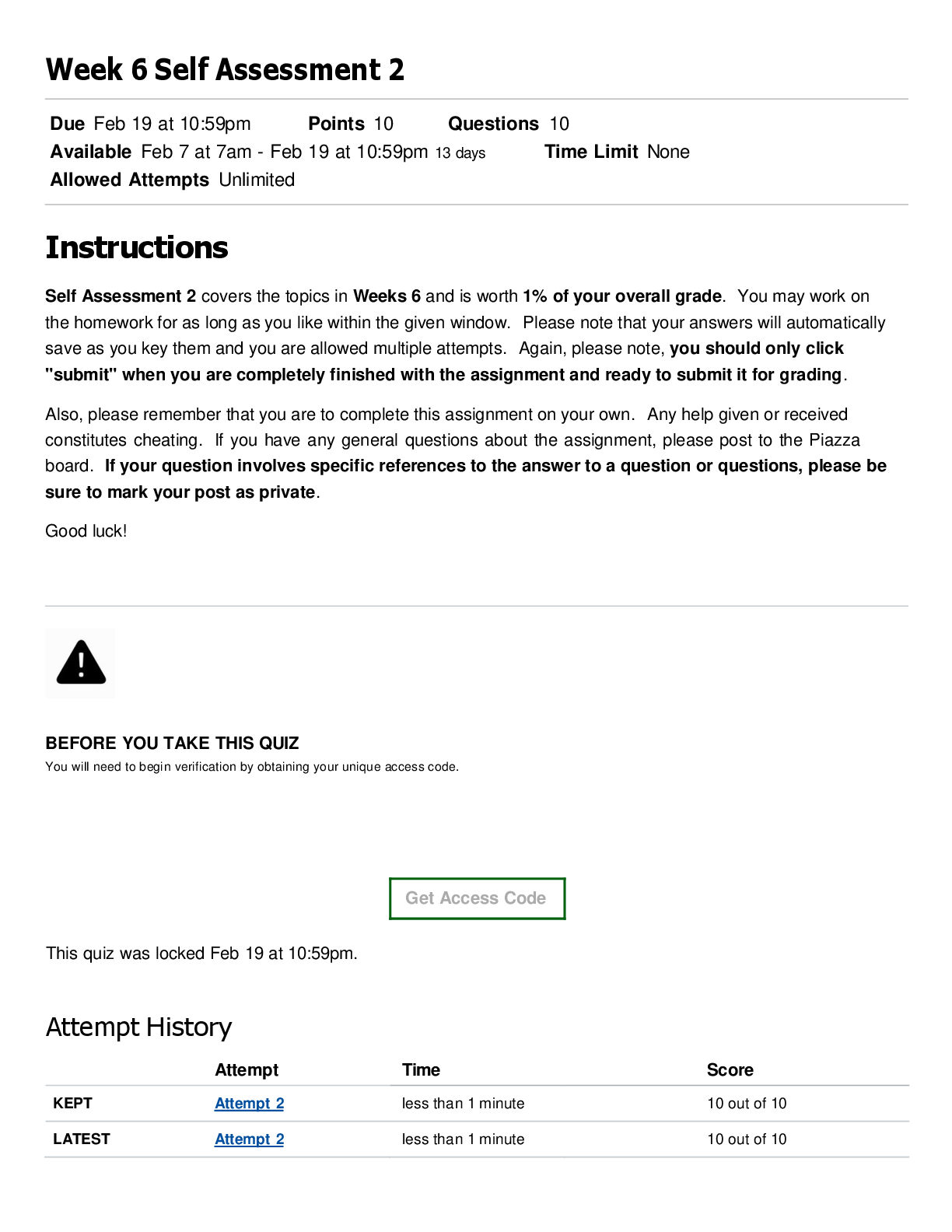
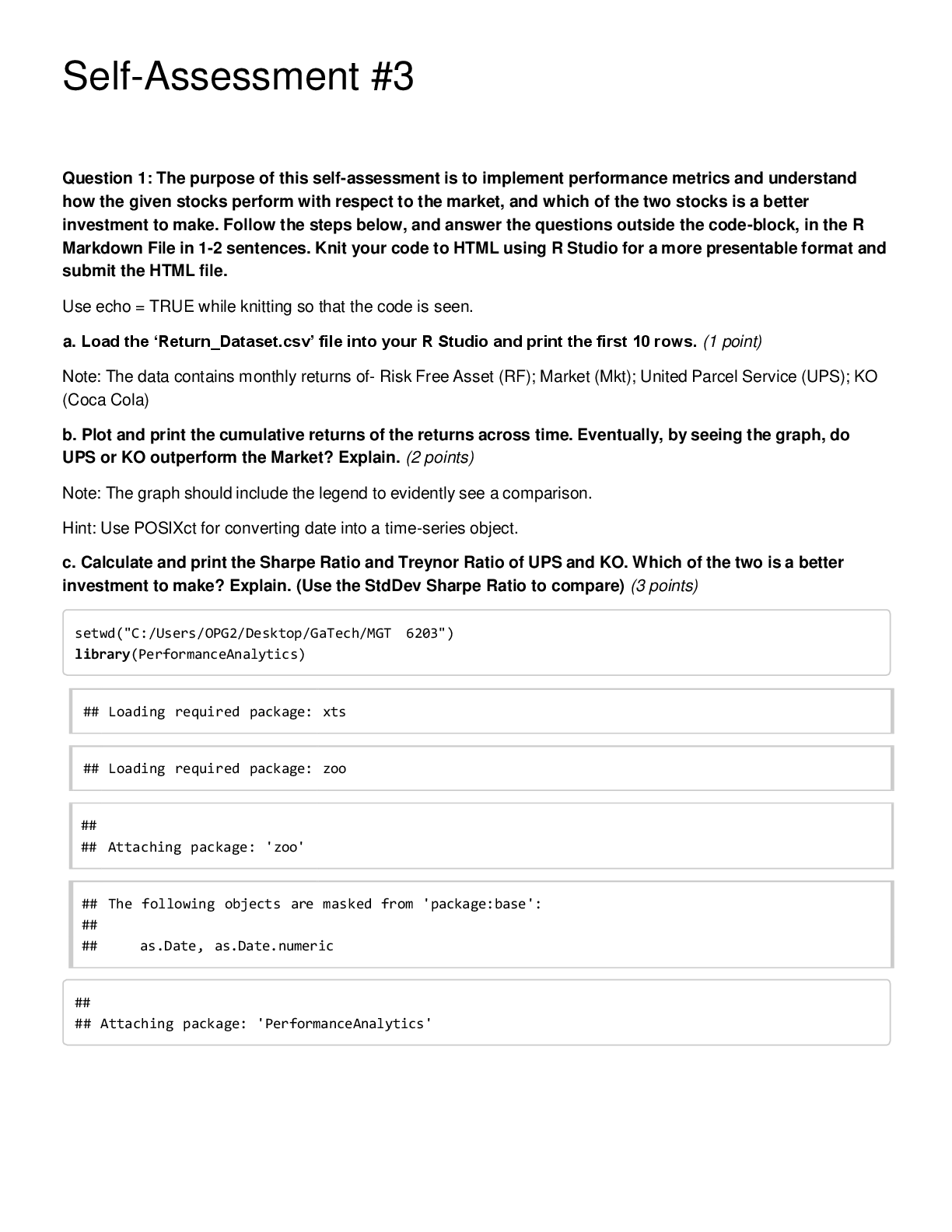
CS 345 Quiz 4 | With 100% Correct Answers In the context of Capability Maturity Model Integration, process is ad hoc and chaotic; organization tends to overcommit and processes are often abandoned ... during times of crisis in the _____ maturity level. Initial Products, such as statements of requirements, flowcharts, and user documentation, are known as _____. Deliverables Which of the following is true about online virtual worlds? Strict liability _____ means that the defendant is held responsible for injuring another person, regardless of negligence or intent. Strict liability Which safety critical system failures resulted in 5 incorrect reportings of missile firings? Soviet Early Warning System Failure (1983) Unless organizations _____ social networks, their customers are left to resolve their issues and questions on their own, often in ways that are not ideal. Monitor A safety critical system is one whose failure may cause all of the following except Financial Hardship _____ is threatening behavior or unwanted advances directed at an adult using the Internet or other forms of online and electronic communications. Cyberstalking It is difficult to quantify how much the use of IT has contributed to worker productivity because _____. many other factors influence worker productivity rates besides IT In one lawsuit in the early ____, a financial institution became insolvent because defects in a purchased software application caused errors in several of its systems. 1990s In the context of development of safety critical systems, if an undesirable event has a one percent probability of occurring, a 25 percent chance of going undetected, and a potential cost of $1,000,000, then the risk can be calculated as _____. $2500 _____ is the probability of an undesirable event occurring times the probability that the event would go undetected times the magnitude of the event's consequences if it does happen. Risk _____ typically involves the use of social networks to communicate and promote the benefits of products and services. Social network advertising After successful unit testing, the subsystems are combined to test the entire system as a complete entity using _____. integration testing An electronic health record includes _____ patient's immunization records If the product fails to meet the terms of its written guarantee, the buyer or lessee can sue for _____. breach of warranty A complex system used in IT is a redundant array of independent disks (RAID), which is commonly used in _____ for file servers. high-volume data storage The full name of the E-Rate program is ___ Schools and Libraries Program of the Universal Service Fund _____ requires the presence of patients and healthcare providers at different sites at the same time and often involves a videoconference link between the two sites. Live telemedicine About _____ of material is being uploaded to YouTube every minute making it difficult to review all material submitted for posting. 100 hours A majority of social shopping Web sites generate revenue through _____ retailer advertising The Health Information Technology for Economic and Clinical Health Act is intended to increase the use of health information technology by _____. saving the government $10 billion through improvements in the quality of care, care coordination, reductions in medical errors, and duplicate care Remote monitoring is also known as _____ home monitoring The _____ is a small, inexpensive computer with either 256 MB or 512 MB of RAM, a 700 MHz processor, one or two USB ports, and an Ethernet port—but no case and no monitor. Raspberry Pi After an organization decides to adopt _____, it must conduct an assessment of its software development practices to determine where they fit in the capability model. CMMI-DEV Which of the following is true of the International Organization for Standardization? It is a worldwide federation of national standards bodies from 161 countries A type of business system is the _____, which is used to develop accurate forecasts of customer demand, recommend stocks and bonds for an investment portfolio. decision support system In 2006, _____ introduced a low-cost laptop called the Classmate PC. Intel While using social networks as part of the hiring process, employers can _____. look at the profiles of potential candidates Most social networking Web sites have terms of use agreement that states the Web site has the right to _____. delete material that violates the site's policies The Bureau of Labor Statistics tracks U.S. productivity on a(n) _____ basis Quarterly Employers can legally reject a job applicant based on the contents of the individual's social networking profile as long as the company is not violating federal or state ______ laws. discrimination The _____ regards it as a federal crime to enter a social networking site in violation of the terms of service Department of Justice _____ is the country in Europe with the highest Internet penetration. Monaco All of these technology failures constitute a failure of a safety critical system except The Millennium Bug (2000) The safety engineer uses a logging and monitoring system to track _____ from a project's start to its finish Initial _____ means that the defendant is held responsible for injuring another person, regardless of negligence or intent. Strict liability Oil companies are increasingly relying on _____ to connect a nurse or EMT on an oil platform to emergency physicians at a major medical center. live telemedicine _____ is a social networking site where entrepreneurs and small-business people collaborate to help each other to succeed. Biznik One approach to quality assurance is to test the code for a completed unit of software by actually entering test data and comparing the results with the expected results in a process called _____. dynamic testing The _____ standard serves many industries and organizations as a guide to quality products, services, and management. ISO 9001 _____ involves viewing the software unit as a device that has expected input and output behaviors but whose internal workings are unknown. Black-Box testing An advantage of social network advertising over traditional advertising media is that _____. ads can be targeted to reach people with the desired demographic characteristics _____ refers to methods within the development cycle that guarantee reliable operation of the product. Software quality assurance The _____ is a low-cost computer that runs a Linux-based operating system and comes with a suite of 300 or so learning applications called Sugar. OLPC XO-4 [Show More]
Last updated: 1 year ago
Preview 3 out of 9 pages

Loading document previews ...
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

CS 345 QUIZ 1 - 4 BUNDLE
CS 345 QUIZ 1 - 4 BUNDLE
By Nurse Henny 1 year ago
$20
4
Reviews( 0 )
$11.50
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Oct 10, 2024
Number of pages
9
Written in
All
Additional information
This document has been written for:
Uploaded
Oct 10, 2024
Downloads
0
Views
34