Computer Science > EXAM > CS 345 Quiz 2 | Questions with 100% Correct Answers (All)
CS 345 Quiz 2 | Questions with 100% Correct Answers
Document Content and Description Below
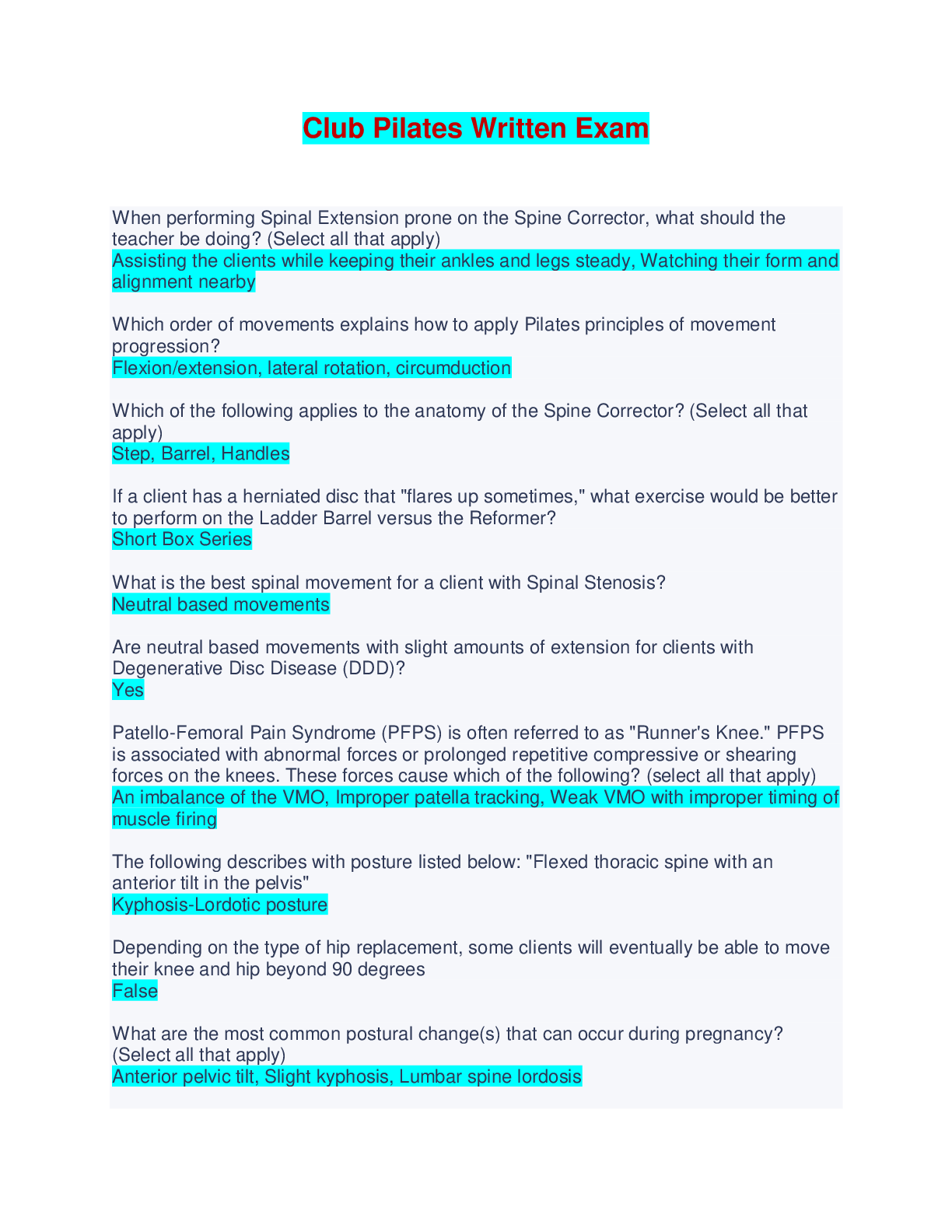
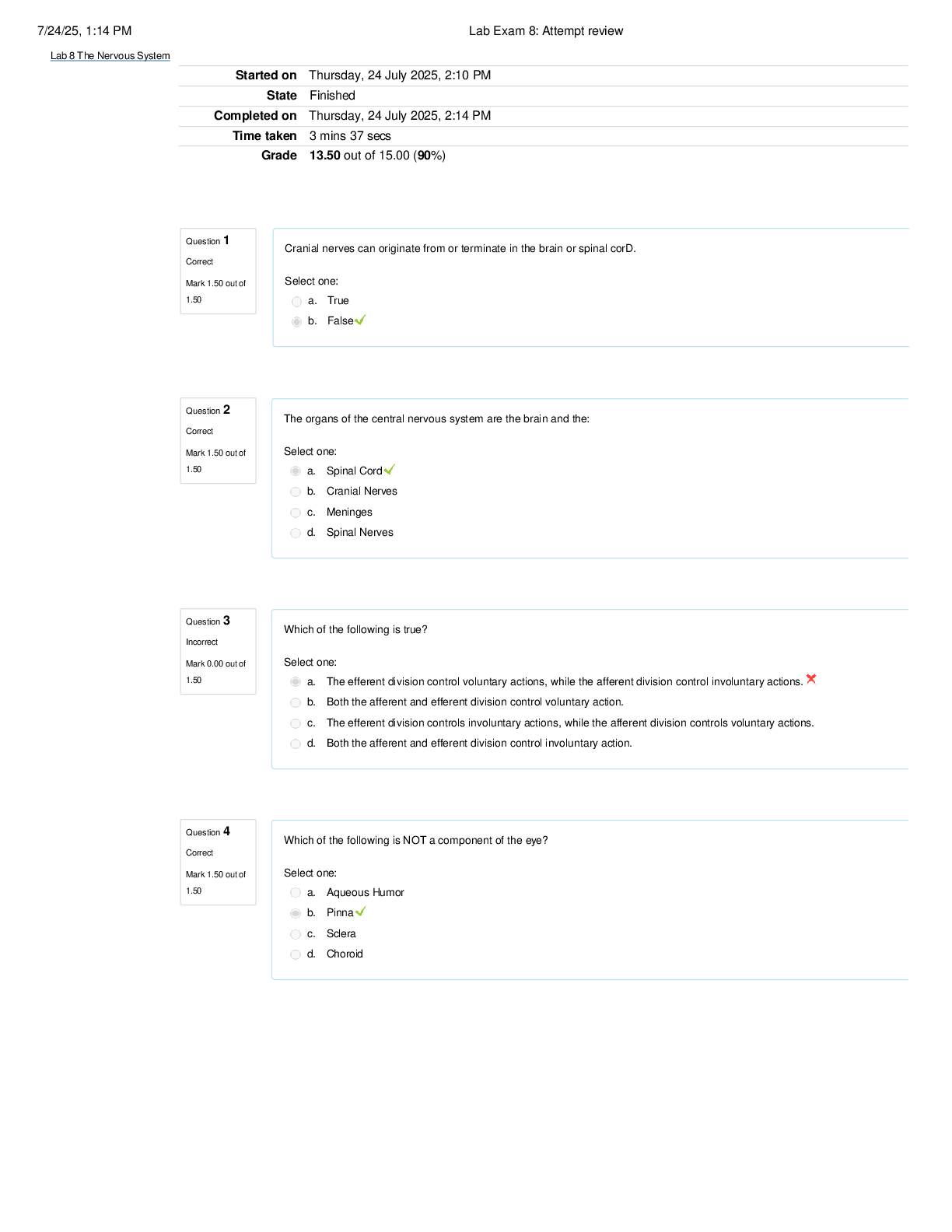
CS 345 Quiz 2 | Questions with 100% Correct Answers In 2008, the _______ granted expanded authority to collect, without court-approved warrants, international communications as they flow through th ... e network equipment and facilities. Foreign Intelligence Surveillance Act Amendments Act A(n) _____ is a device that records the originating number of incoming calls for a particular phone number Trap and Trace _______ have become a common and easily created form of malware that are creating using applications such as Visual Basic or VBScript. Macro Viruses The Organization for Economic Co-operation and Development's _______, established in 1980, are often held up as the model of ethical treatment in consumer data. Fair information practices The _____ bars the export of data to countries that do not have data privacy protection standards comparable to those of its member countries. European Union Data Protection Directive _____ are poorly trained and inadequately managed employees who mean well but have the potential to cause much damage. Negligent Insiders A _____ attack keeps the target so busy responding to a stream of automated requests that legitimate users cannot get in. Distributed denial-of-service In Doe v. Holder, the courts ruled that the NSL gag provision violates the _____. First Amendment The _____ prohibits the government from concealing the existence of any personal data record-keeping systems. Privacy Act In computing, a(n) _____ is a term for any sort of general attack on an information system that takes advantage of a particular system vulnerability. Exploit _____ is an annual gathering in Las Vegas of computer hackers. DEFCON In the context of the Fourth Amendment, the courts have ruled that _____. Without a reasonable expectation of privacy, there is no privacy right The _____ prohibits unauthorized access to stored wire and electronic communications, such as the contents of email inboxes, instant messages, message boards, and social networking sites. Electronic Communications Privacy Act The Children's Online Privacy Protection Act _____. Does not cover the dissemination of information to children The _____ is a federal law that provides a definition of the term cyberterrorism and under which young people primarily involved in what they consider to be minor computer pranks have been tried as cyberterrorists. USA Patriot Act Installation of a corporate _____ is the most common computer security precaution taken by businesses. Firewall Spammers can defeat the registration process of free email services by launching a coordinated _____ attack that can sign up for thousands of untraceable email accounts. Bot _____ test the limitations of information systems out of intellectual curiosity to see whether they can gain access and how far they can go. Hackers The _____ protects against unreasonable search and seizure. Fourth Amendment The _____ regulates the collection of the content of wire and electronic communications. Wiretap Act The _____ allows consumers to request and obtain a free credit report each year from each of the three primary credit reporting companies. Fair and Accurate Credit Transactions Act A _____ is a form of Trojan horse which executes when it is triggered by a specific event such as a change in a particular file, by typing a specific series of keystrokes, or by a specific time or date. logic bomb Under the _____, the Federal Communications Commission responded to appeals from the Department of Justice by requiring providers of Internet phone services and broadband services to ensure that their equipment accommodated the use of law enforcement wiretaps. Communications Assistance for Law Enforcement Act In the context of tenets of the The European Union Data Protection Directive, _____ refers to an individual's right to challenge the accuracy of the data and provide the corrected data. Correction The _____ enables the public to gain access to certain government records. Freedom of Information Act _____ is the act of fraudulently using email to try to get the recipient to reveal personal data. Phishing _____ is the sending of fraudulent emails to an organization's employees designed to look like they came from high-level executives from within the organization. Spear-Phishing The _____ included strong privacy provisions for electronic health records and bans the sale of health information, promotes the use of audit trails and encryption, and provides rights of access for patients. American Recovery and Reinvestment Act One purpose of a(n) _____ is to capture and record data that can be used by the manufacturer to make future changes to improve vehicle performance in the case of a crash. Event data Recorder The _____ policy is a template available from the SANS Institute that defines the means to establish a culture of openness, trust, and integrity in business practices. Risk Assessment _____ pledged to deliver on a trustworthy computing initiative and defined four pillars of trustworthy computing. Microsoft _____ is the abuse of email systems to send unsolicited email to large numbers of people. Spam A _____ is defined as an exploit that takes place before the security community or software developer knows about the vulnerability or has been able to repair it. [Show More]
Last updated: 1 year ago
Preview 3 out of 6 pages

Loading document previews ...
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

CS 345 QUIZ 1 - 4 BUNDLE
CS 345 QUIZ 1 - 4 BUNDLE
By Nurse Henny 1 year ago
$20
4
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Oct 10, 2024
Number of pages
6
Written in
All
Additional information
This document has been written for:
Uploaded
Oct 10, 2024
Downloads
0
Views
29