Computer Science > QUESTIONS & ANSWERS > Questions & Answers> I_SECURITY QUIZ. What is the best way to secure passwords? Which of the followi (All)
Questions & Answers> I_SECURITY QUIZ. What is the best way to secure passwords? Which of the following determines user privileges? Information security policies/procedures for TCS are applicable to,...How frequently should the system login password be changed..?
Document Content and Description Below
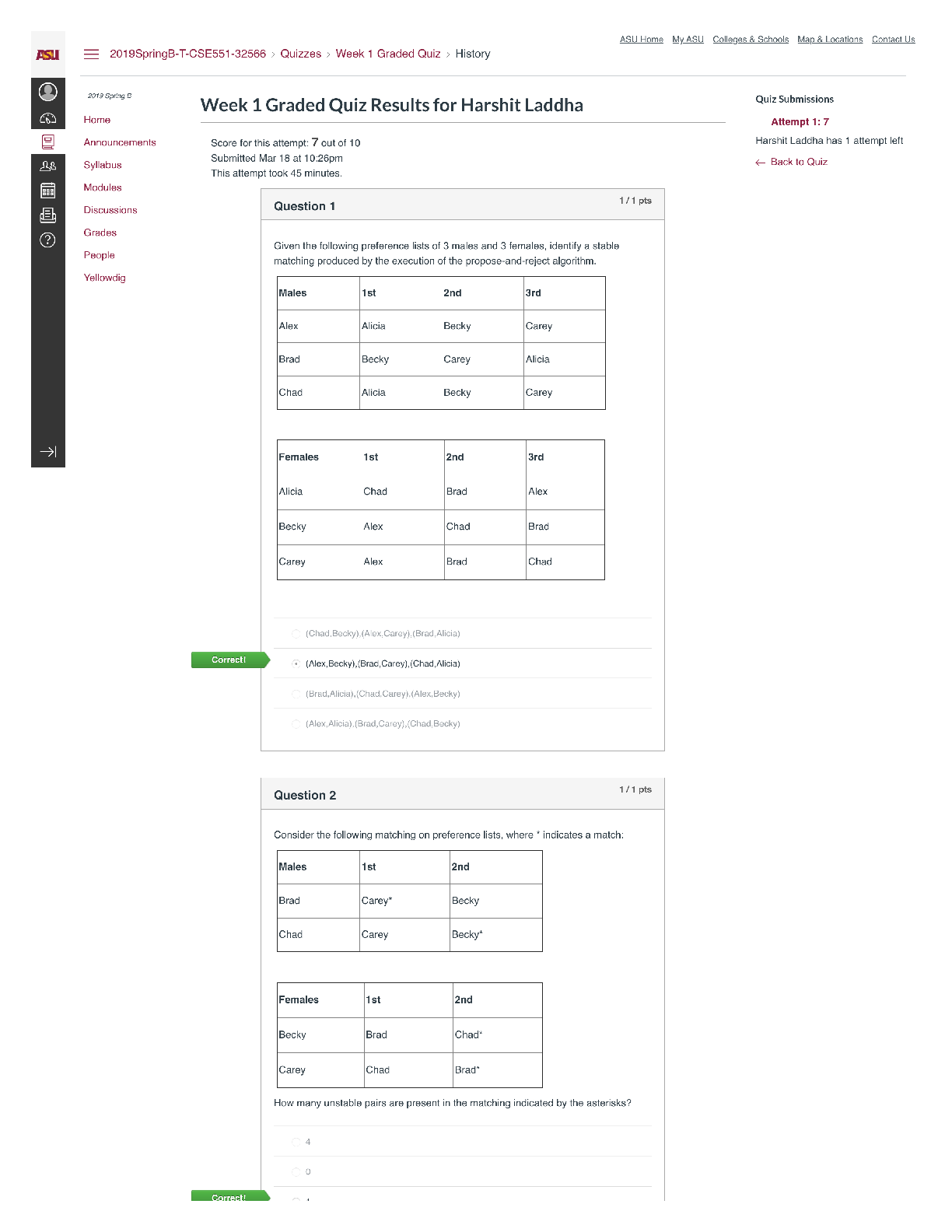
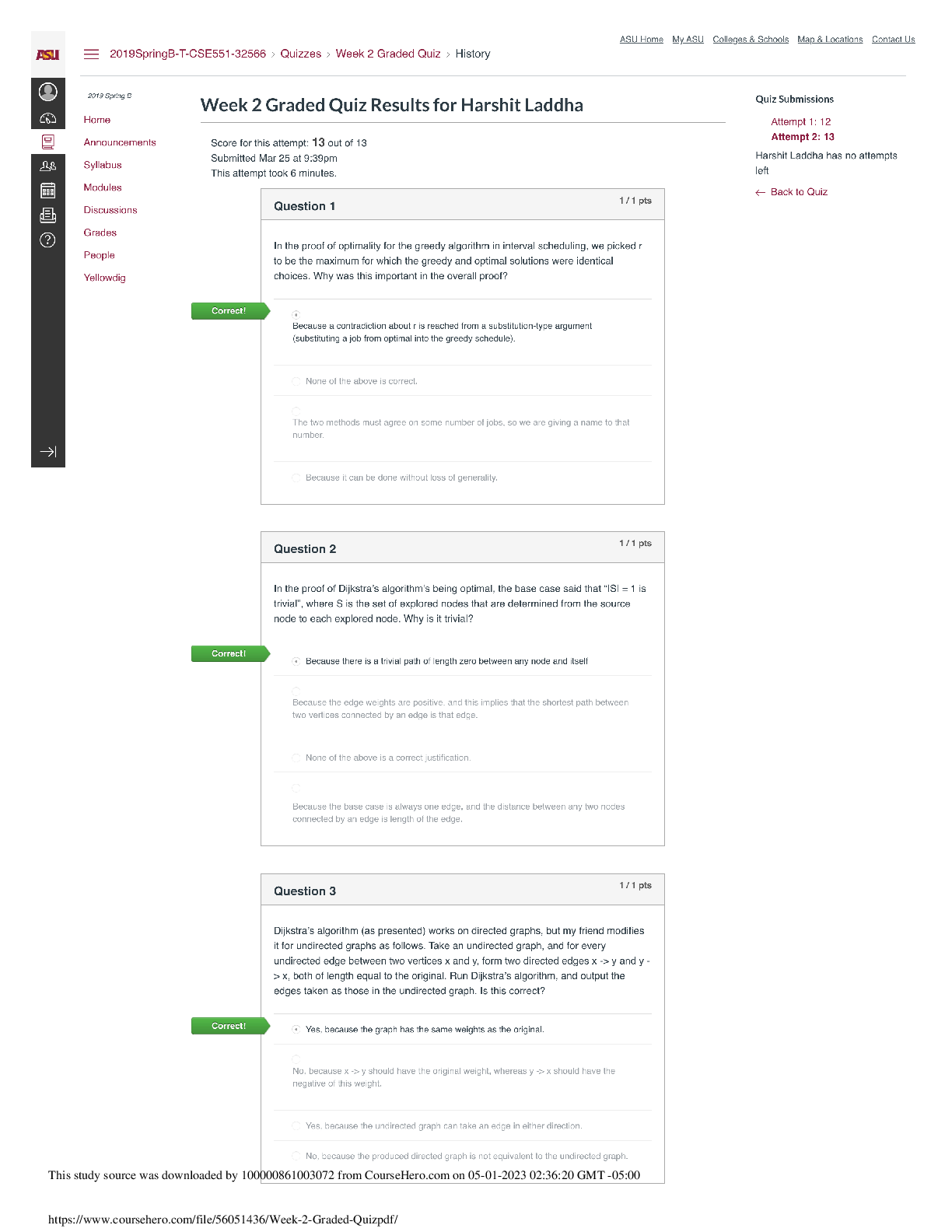
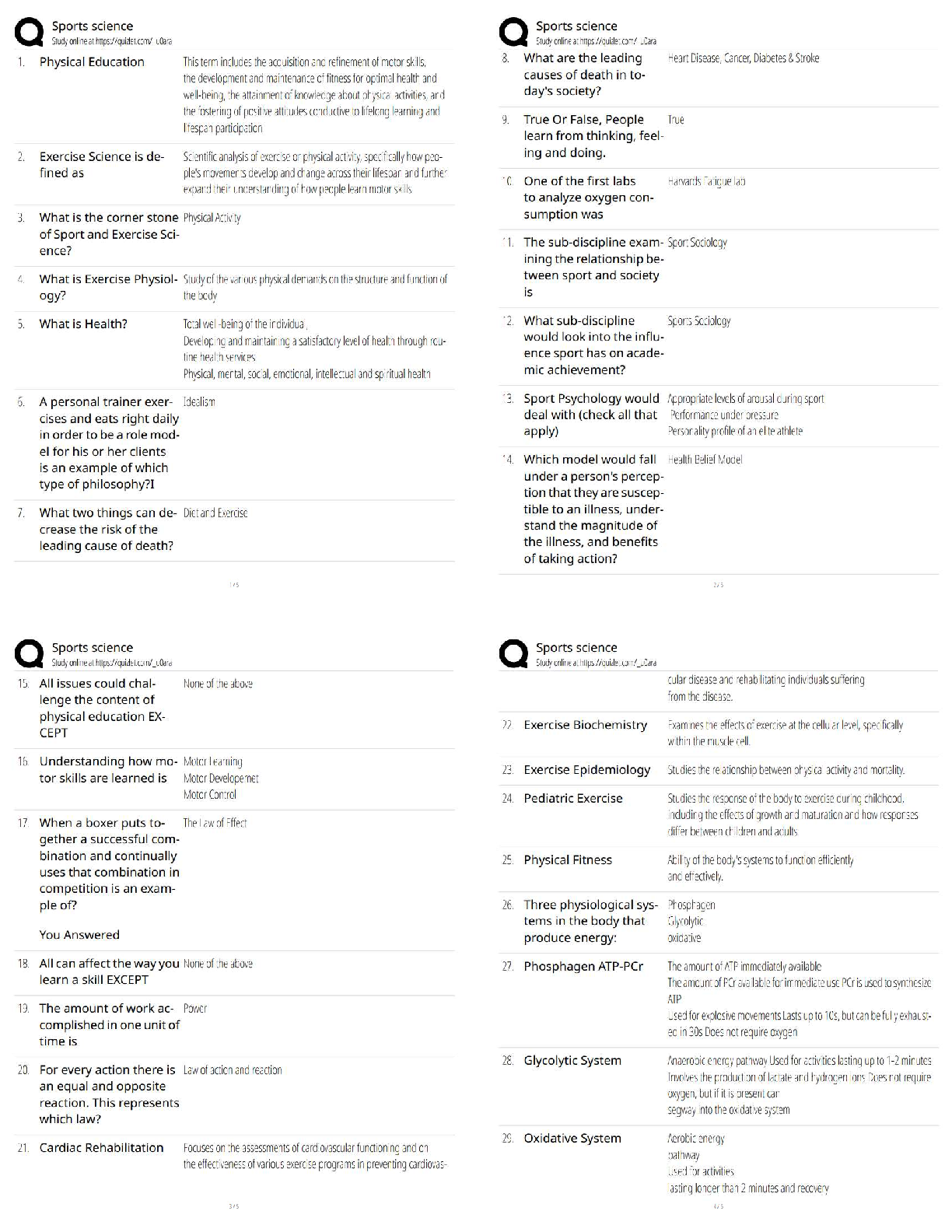
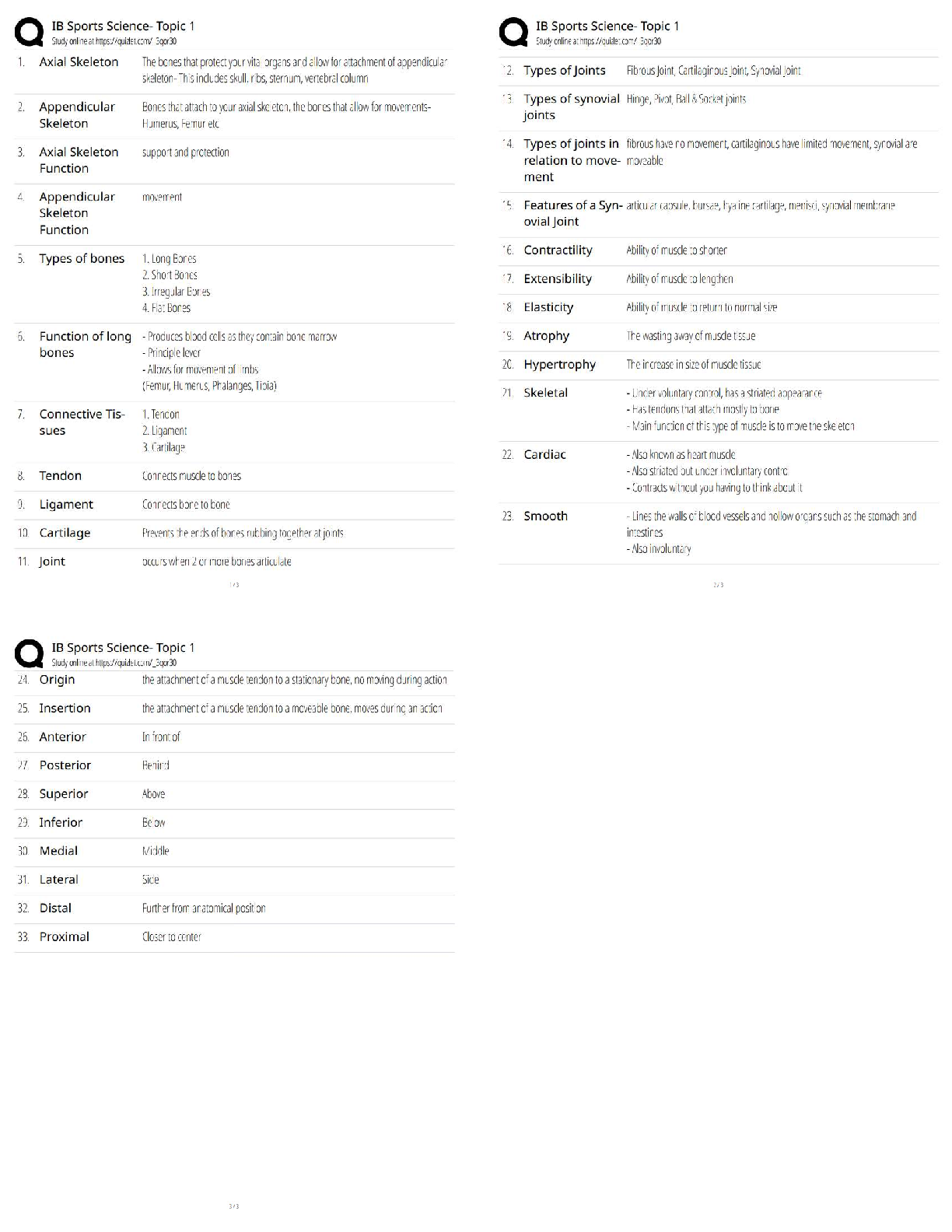
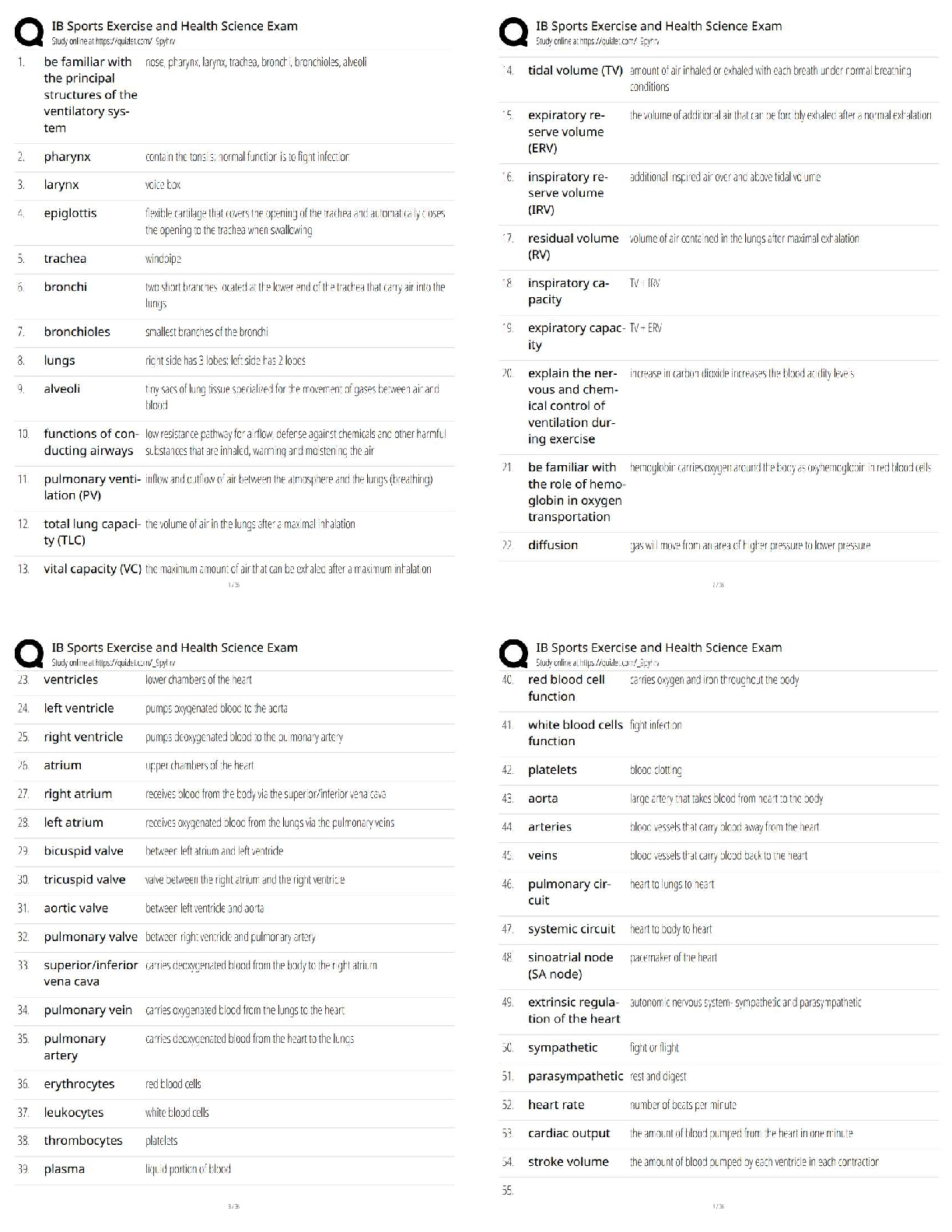
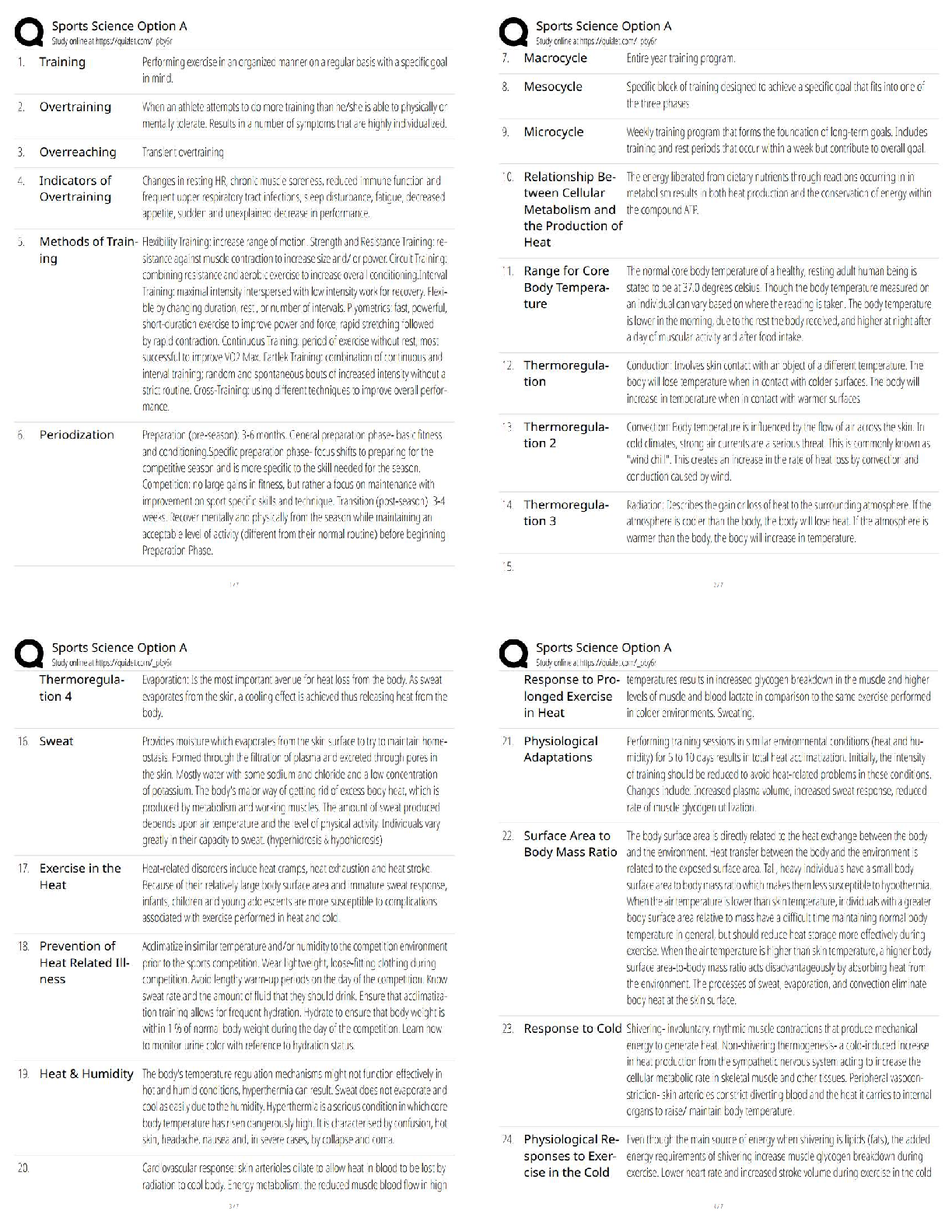
ISECURITY QUIZ Who heads the corporate inf… CEO What is the best way to secure passwords… Memorize the password Which of the following determines user privileges… Access control list Pass ... word can be shared It can never been shared Information security policies/procedures for TCS are applicable to: All TCS associates and third parties having access… SOE means The baselines software on… What is DOS attack An attack to prevent access to a resource… A person responsible for unauthorized software installed… Associate whom the PC assigned How frequently should the system login password be changed One in a month You just got brand new computer and it has anti-virus software installed. It is right… No. You will need to make sure that both anti-virus software… If you ever receive an unsolicited telephone call from someone claiming… Refuse and report inmediatly What is a computer program that has useful functions, but which also contains additional hidden functions Trojan horse I have project related sensitive documents which I should Share only with authorized individuals Data classification addesses following attribute of data Confidenciality TCS password policy mandates that passwords must be Complex password Your collegues calls you from the TCS entry gate informing that you guard… None above Your receive a call from your friend asking you leave inmediatly as there is some unrest in a certain part of the city Inform the Admin/CML about the call and wait for their instructions Which of the following aspects does a recovery strategy not considered Expensive recovery The motive behind carrying out business continuity mock drills is to All above The objective of the BCP is All above How do you destroy TCS/customer confidential hard copy information? Disposing it using a shredder Valuable information of the client is classified as TCS customer confidential The key to good information security is All the above What is NOT mandated for the physical security of workstation? Removable medias drives ISM stands for Information security manager Is photography allowed inside TCS’ premises No, photography is not allowed… If your planning to bring your family inside the office, what are you required to do? You are allowed to bring your family to the office, only on TCS’s family day Which of the following choices describes the reason for using cable locks for laptos To prevent the theft of the unit You just received an email from your bank asking you to confirm your online activities… If is possible, call your bank to confirm… MP3 songs can be stored on desktop FALSE, it is copyright violation What are the three basic principles of security Confidentiality, integrity, availability A pop up ad appears on you computer screen offering an anti-spyware product.. Close the popup. If you want… [Show More]
Last updated: 2 years ago
Preview 1 out of 5 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$4.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jan 19, 2023
Number of pages
5
Written in
All
Additional information
This document has been written for:
Uploaded
Jan 19, 2023
Downloads
0
Views
65