Information Technology > QUESTIONS & ANSWERS > FedVTE CASP Questions and Answers with Complete Solutions (All)
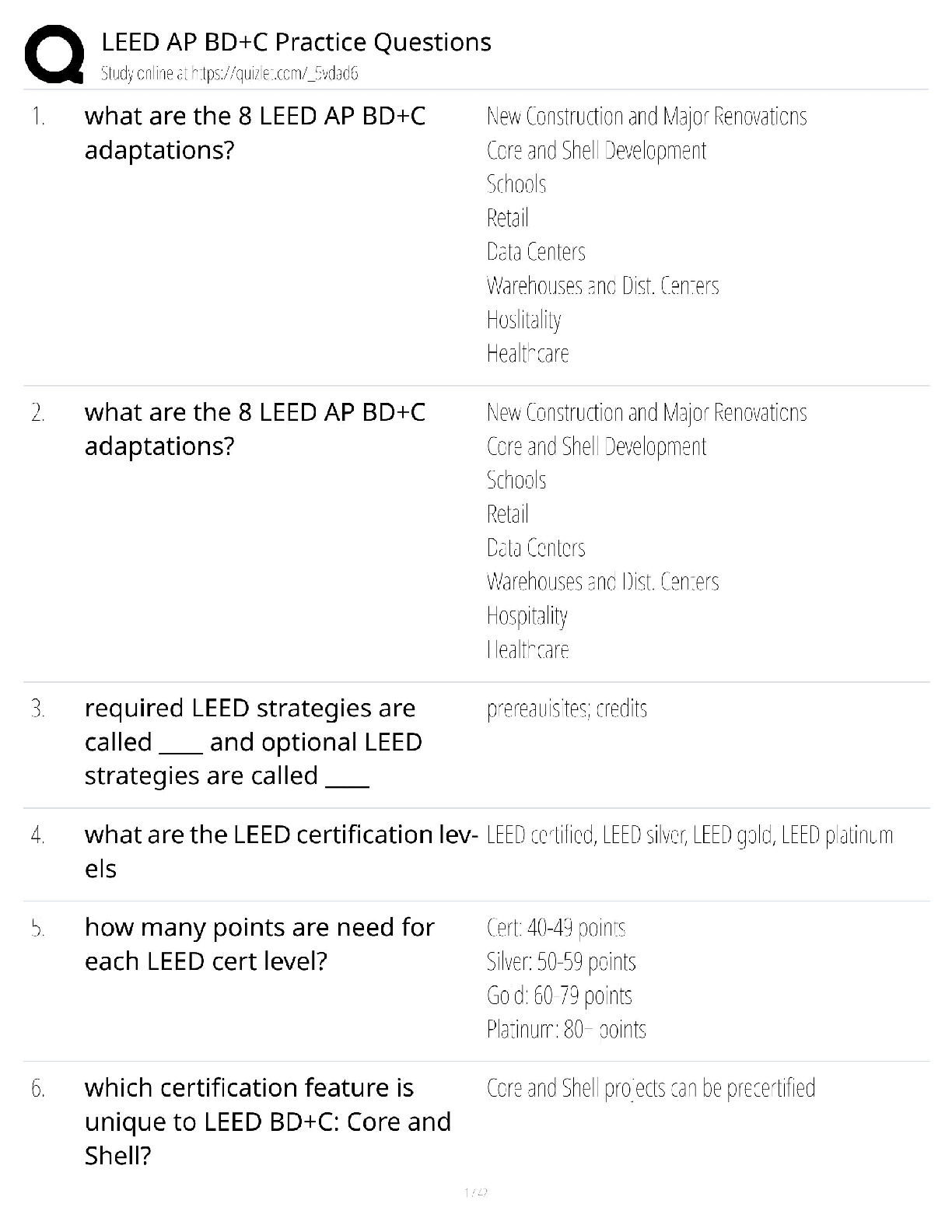
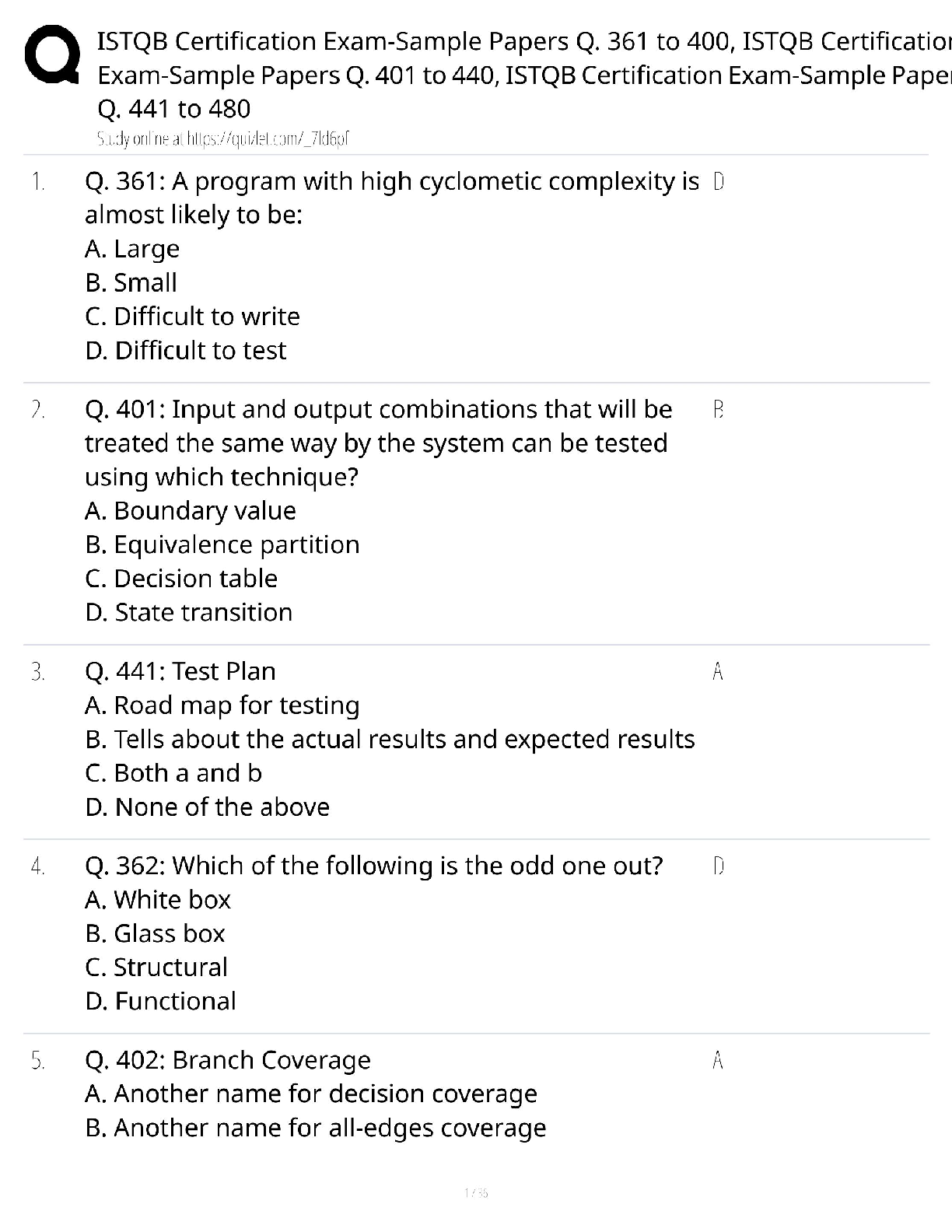
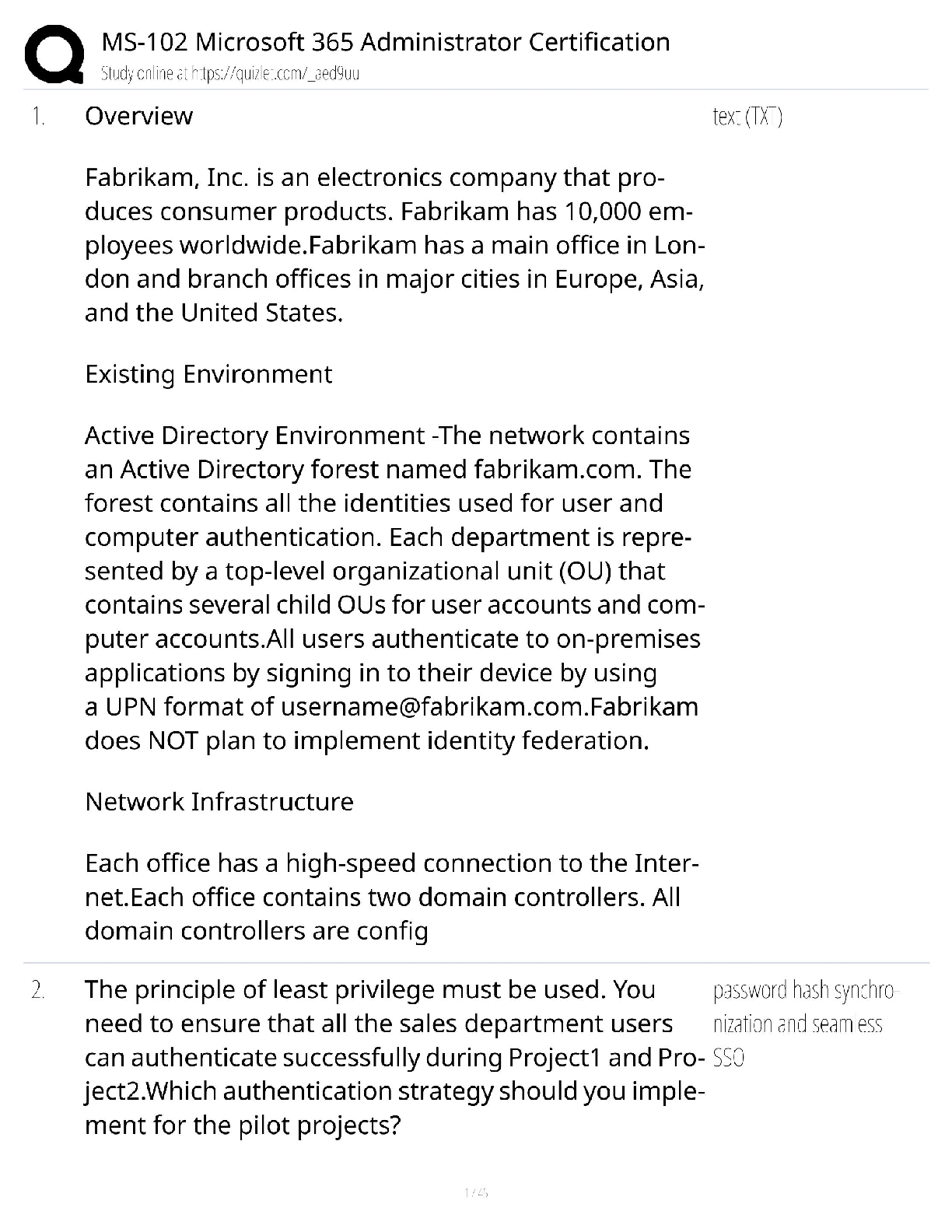
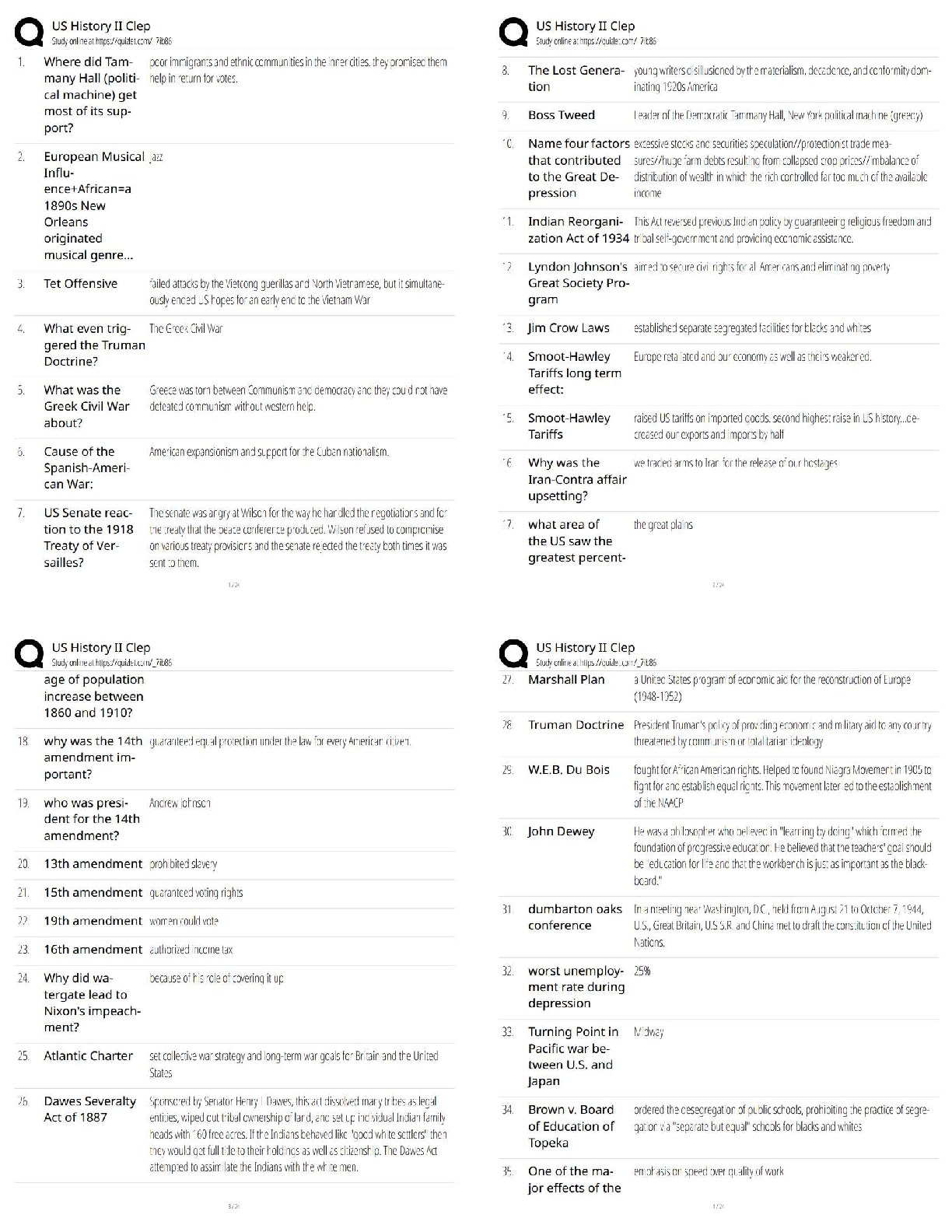
FedVTE CASP Questions and Answers with Complete Solutions
Document Content and Description Below
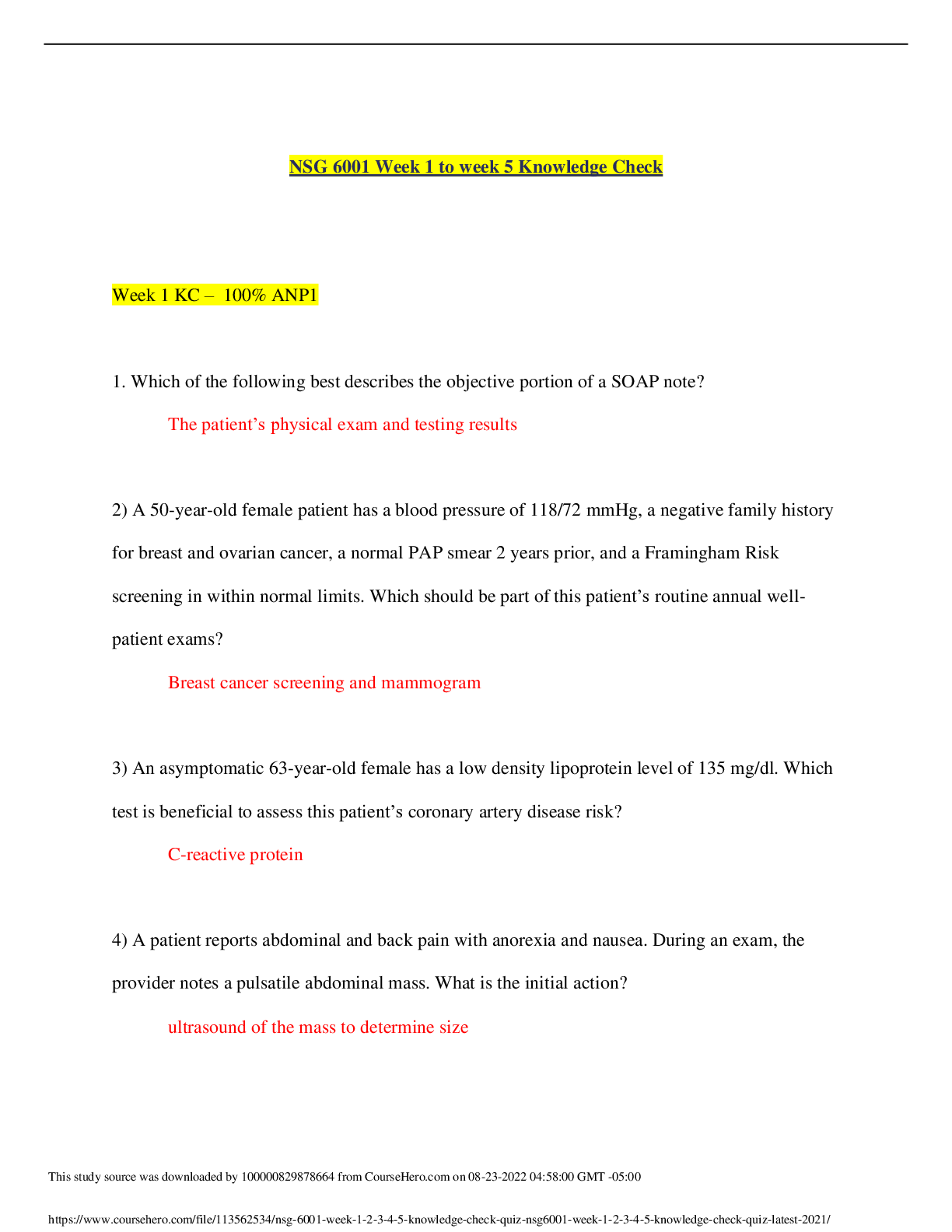
FedVTE CASP Questions and Answers with Complete Solutions A flaw in an online sporting goods website allows customers to purchase multiple quantities of goods and only be charged the single quantit ... y price. To improve the site, management is demanding that the ecommerce application be tested to insure this flaw is corrected. Which of the following is the BEST combination of tools and or methods to use? ✔✔A. Blackbox testing using outside consultants C. Fuzzer and HTTP interceptor All adverse impacts of a security event can be measured quantitatively? ✔✔False An active\passive cluster of redundant routers and firewalls has been installed in the network edge by your enterprise LAN/WAN engineer. The firewalls are using stateful firewall inspection. Even with the redundant equipment, there are still multiple reports of dropped connections with external clients. Which of the following is MOST likely the cause of this problem? ✔✔TCP sessions are being rejected because they are being handled by asynchronous route paths through the firewalls. Which of the following describes a single sign on implementation? ✔✔A web access load balancer passes the same authentication attributes in a HTTP header to multiple applications. What does the access control term AAA stand for? ✔✔Authentication, Authorization, Accounting A government agency has a major new initiative to virtualize as many servers as possible, due to power and rack space capacity at its two data centers. The agency has prioritized virtualizing older servers first as the hardware is nearing end of life. The two initial migrations include Windows 2000 hosts (domain controllers and front-facing web servers) and open source Linux hosts (front facing web servers). Which of the following should occur based on best practices? ✔✔Each data center should contain separate virtual environments for the web servers and for the domain controllers. Shifting the responsibility for a risk to a third party is which strategy for managing risks? ✔✔Transfer Audit logs can be used to prevent users from performing unauthorized operations. ✔✔False The CISO at a software development company is concerned about weaknesses in the review processes his company has for their major product. Testing was performed in house by a small review team, and the previous projects have been found to have that only limited test cases were used and many of the code paths remained untested. The CISO raised concerns that this product cannot fail in an upcoming large scale deployment. Which of the following will provide the MOST thorough additional testing? ✔✔Run a small pilot test at the customers site before rolling out the complete deployment. Which of the following is the process of determining whether someone or something is who or what it declares itself to be? ✔✔Authentication Which of the following is an incremental update between service packs or versions to fix outstanding issues? ✔✔Maintenance release A new IDS appliance is generating a very large number of events, most of which are not security-related. Select the approach which best resolves this issue. ✔✔Adjust IDS filters that are creating false positives. Which recovery site is fully equipped and is capable of restoring data and configurations within hours? ✔✔B. Hot Site C. Mirrored Site Which of the following is the best choice for ensuring continuous availability? ✔✔Redundancy A retail merchant has had a number of issues in regards to the integrity of sensitive information across all of its customer databases. This has resulted in the merchants share price decreasing in value by more than one third and the merchant has been threatened with losing their ability to process credit card transactions. The new Chief Information Security Officer (CISO) as a result has initiated a program of work to solve the issues. The business has specified that the solution needs to be enterprise grade and meet the following requirements: Work across all major platforms, applications and infrastructure; Tracks activity of all users, including administrators; Operates without negatively impacting the performance of production platforms, applications, and infrastructures; Provides real-time incident reporting; Displays incidents in a dashboard view for easy recognition; Includes a report generator where business units are able to query against companys system assets. In order to solve this probl [Show More]
Last updated: 2 years ago
Preview 1 out of 13 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)
.png)
[SOLVED] FedVTE BUNDLED EXAMS QUESTIONS AND ANSWERS WITH COMPLETE AND VERIFIED SOLUTIONS
[SOLVED] FedVTE BUNDLED EXAMS QUESTIONS AND ANSWERS WITH COMPLETE AND VERIFIED SOLUTIONS
By Nutmegs 2 years ago
$20
20
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jan 02, 2023
Number of pages
13
Written in
All
Additional information
This document has been written for:
Uploaded
Jan 02, 2023
Downloads
0
Views
189








.png)