MIS ch 8 quiz
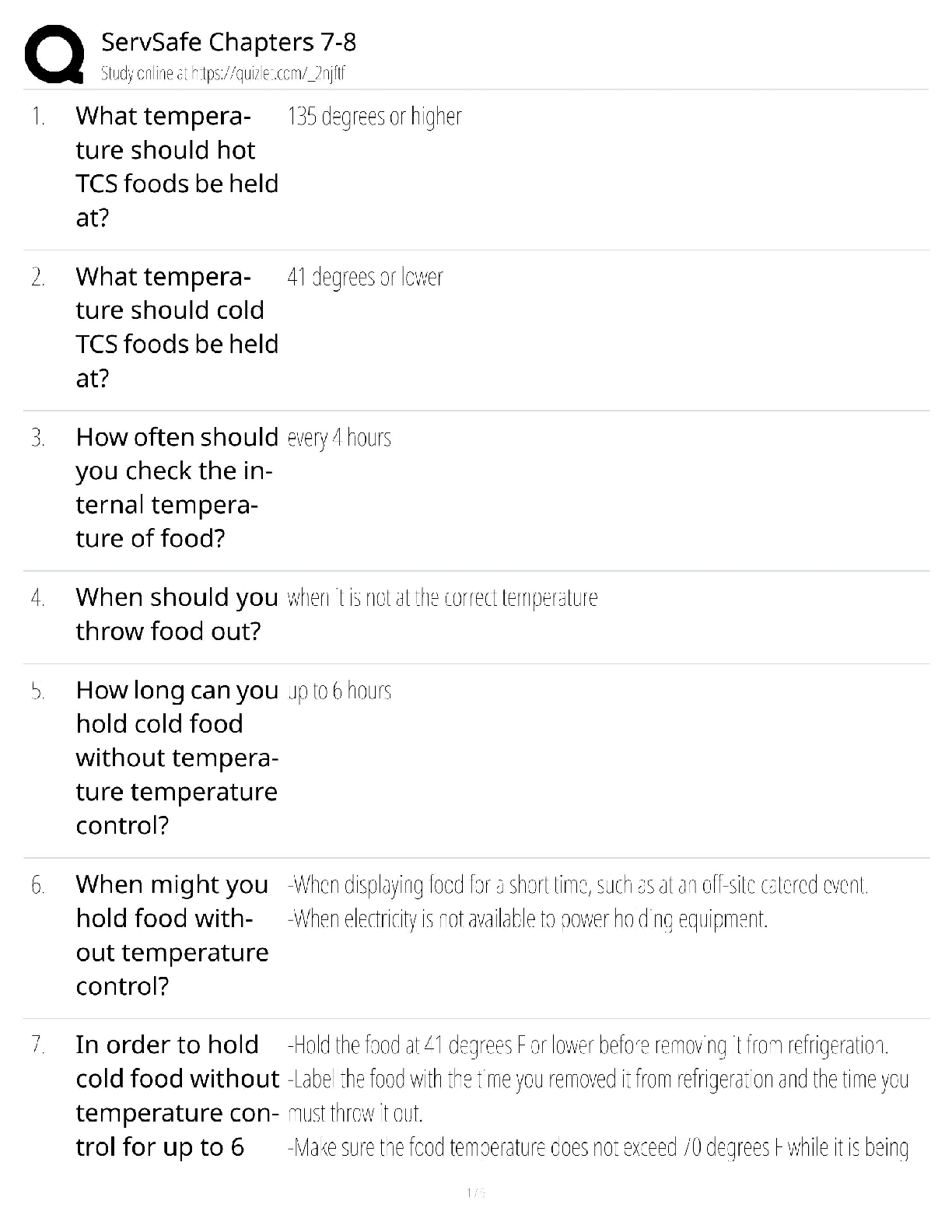
________ includes computer viruses, worms, and Trojan horses. - ✔✔malware
Viruses differ from worms because worms ________. - ✔✔can operate on their own without
attaching to other computer program files
...
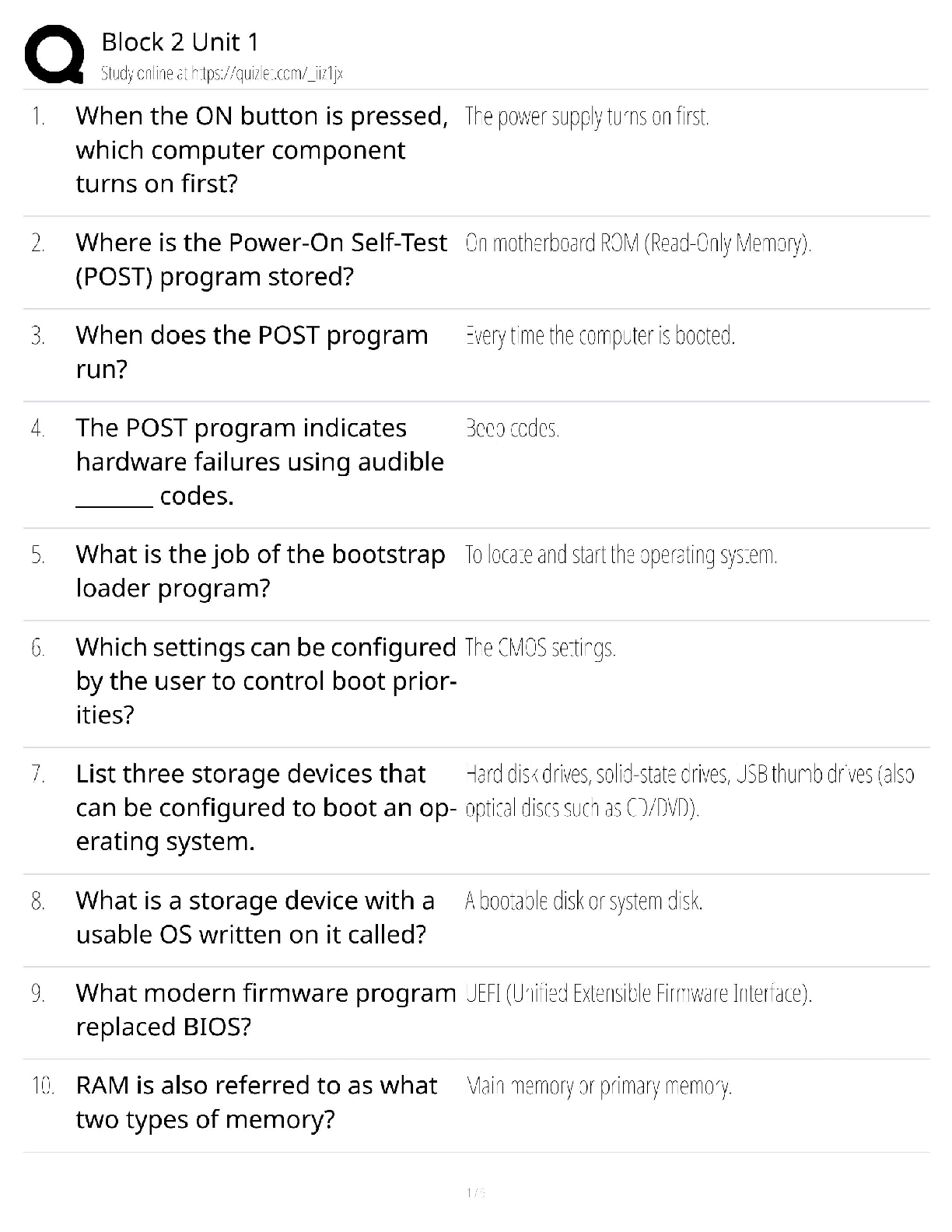
MIS ch 8 quiz
________ includes computer viruses, worms, and Trojan horses. - ✔✔malware
Viruses differ from worms because worms ________. - ✔✔can operate on their own without
attaching to other computer program files
According to McAfee, ________ now pose the greatest security risks. - ✔✔mobile devices
A ________ is a software program that mimics another program and often causes damage. -
✔✔trojan horse
SQL injection attacks are related to ________. - ✔✔databases
If someone loads a program that tracks everything you type, the specific spyware is a ________.
- ✔✔key logger
Someone who intends to gain unauthorized access to a computer system is considered to be a
________. - ✔✔hacker
A ________ is a program that monitors information traveling over a network and ________. -
✔✔sniffer; can be used for criminal purposes
Regarding IS security, DoS represents ________. - ✔✔denial of service
If someone sends you an email trying to appear as a normal site you commonly visit to obtain
unauthorized information, they are ________. - ✔✔phishing
If someone asks you to stay home and click advertising without being interested in the product or
service, they may be asking you to commit ________. - ✔✔click fraud
________ was passed in 1996 to protect medical records. - ✔✔HIPPA
In 2002, the ________ Act was passed to help protect investors with new financial statements
reforms. - ✔✔Sarbanes-Oxley
A(n) ________ outlines acceptable uses of information systems assets. - ✔✔acceptable use
policy
MasterCard having a duplicate computer center in multiple cities is an example of ________ in
case operations at one location are disrupted. - ✔✔disaster recovery planning
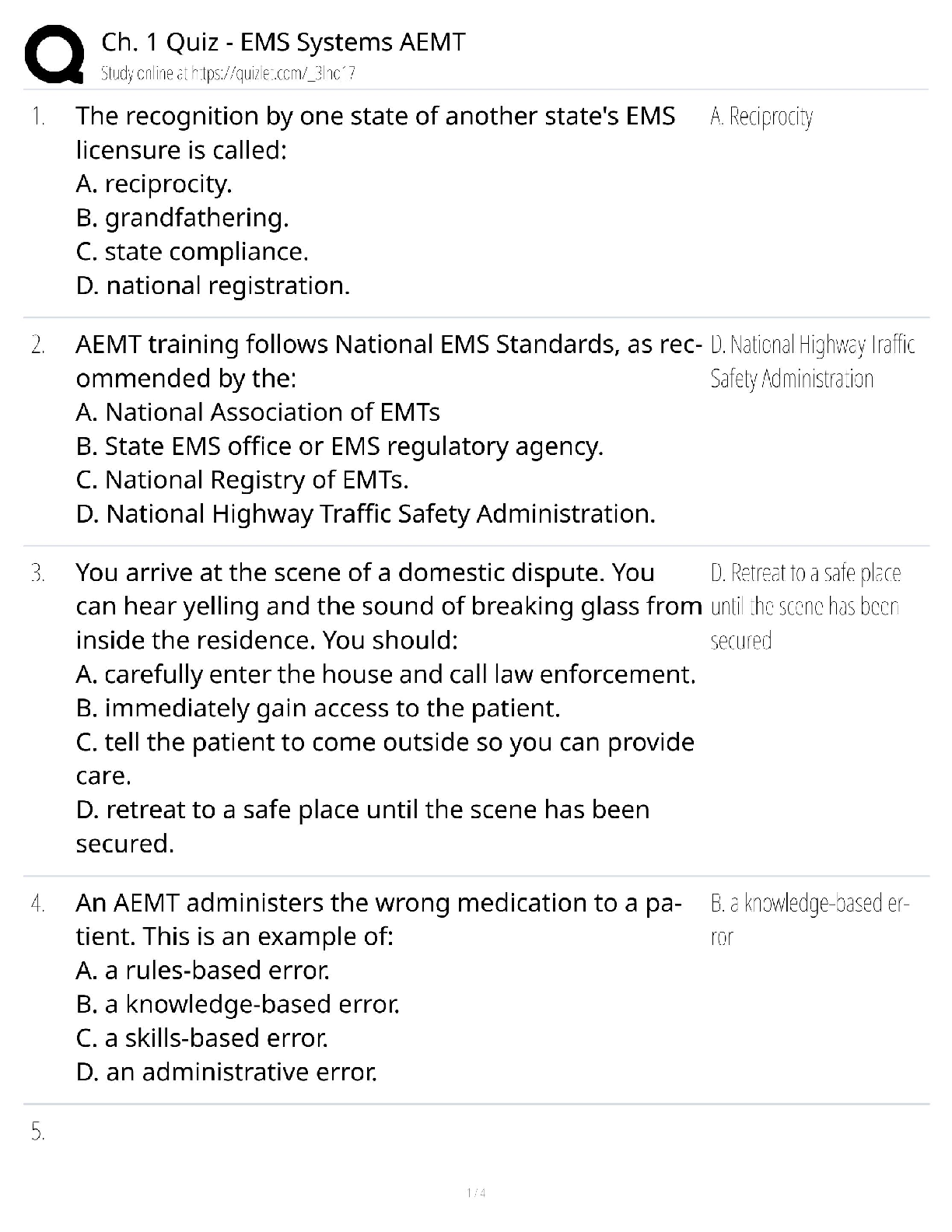
An information systems ________ examines a firm's overall security environment and
determines if the organization is properly prepared to address threats. - ✔✔audit
________ help(s) ensure that important network traffic receives high priority, and less-critical
network traffic receives lower priority. - ✔✔deep packet inspection
________ is used to ensure the person is who he/she claims to be. - ✔✔authentication
The most commonly used authentication technique used for end users is a(n) ________. -
✔✔password
Using your handprint to access a safe deposit box is an example of ________ authentication. -
✔✔biometric
IS security firewalls are an example of a ________. - ✔✔gatekeeper
An intrusion detection system (IDS) ________. - ✔✔helps protect a system using full-time
monitoring tools
________ is a method for encrypting network traffic on the Web. - ✔✔SSL
Public key encryption uses ________ key(s). - ✔✔two
________ are data files used to identify and protect online transactions using a trusted third
party. - ✔✔digital certificates
[Show More]



.png)