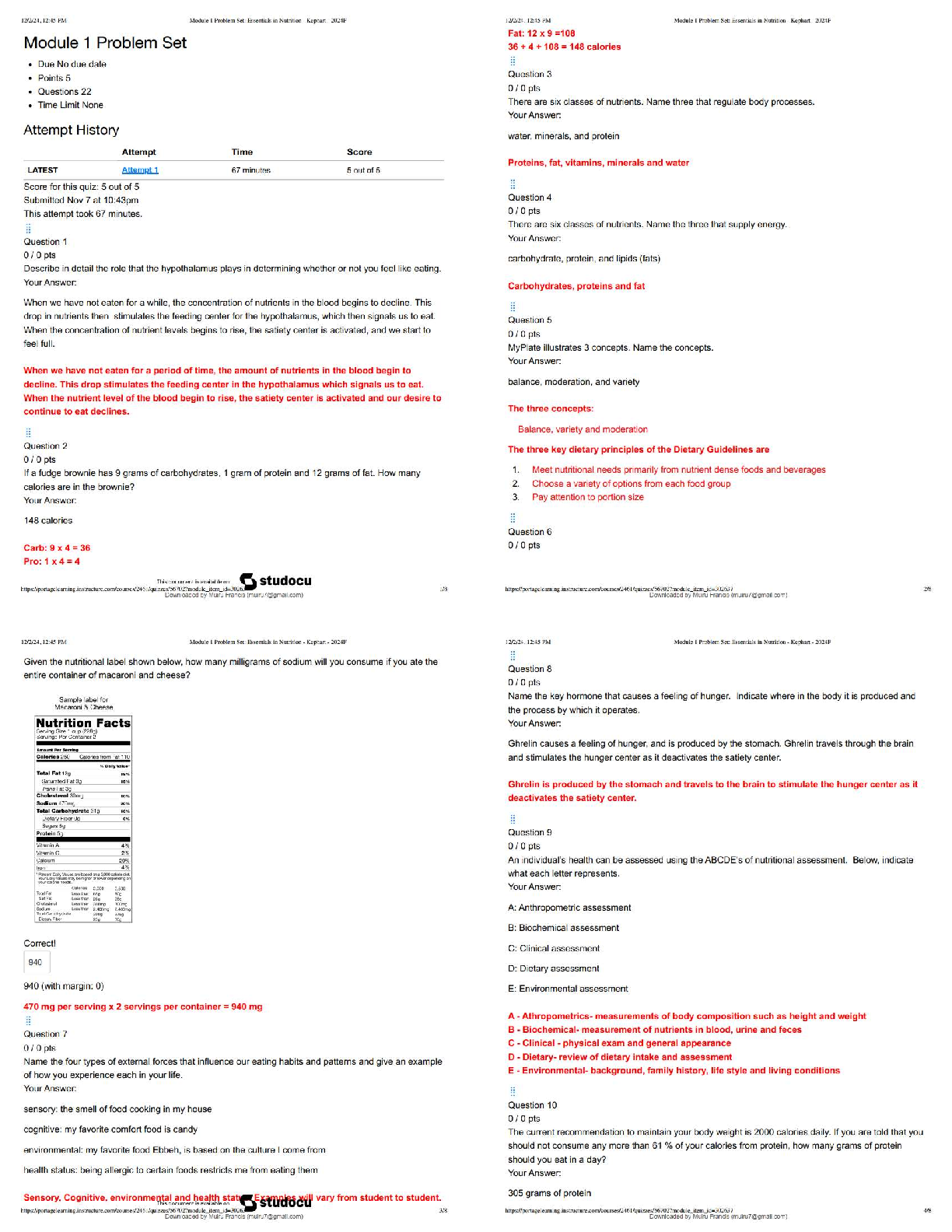
ISC3701 – Assignment 5 MEMO (2025) Instructional Studies in Context | University of South Africa | Due 22 November 2025 Grade A
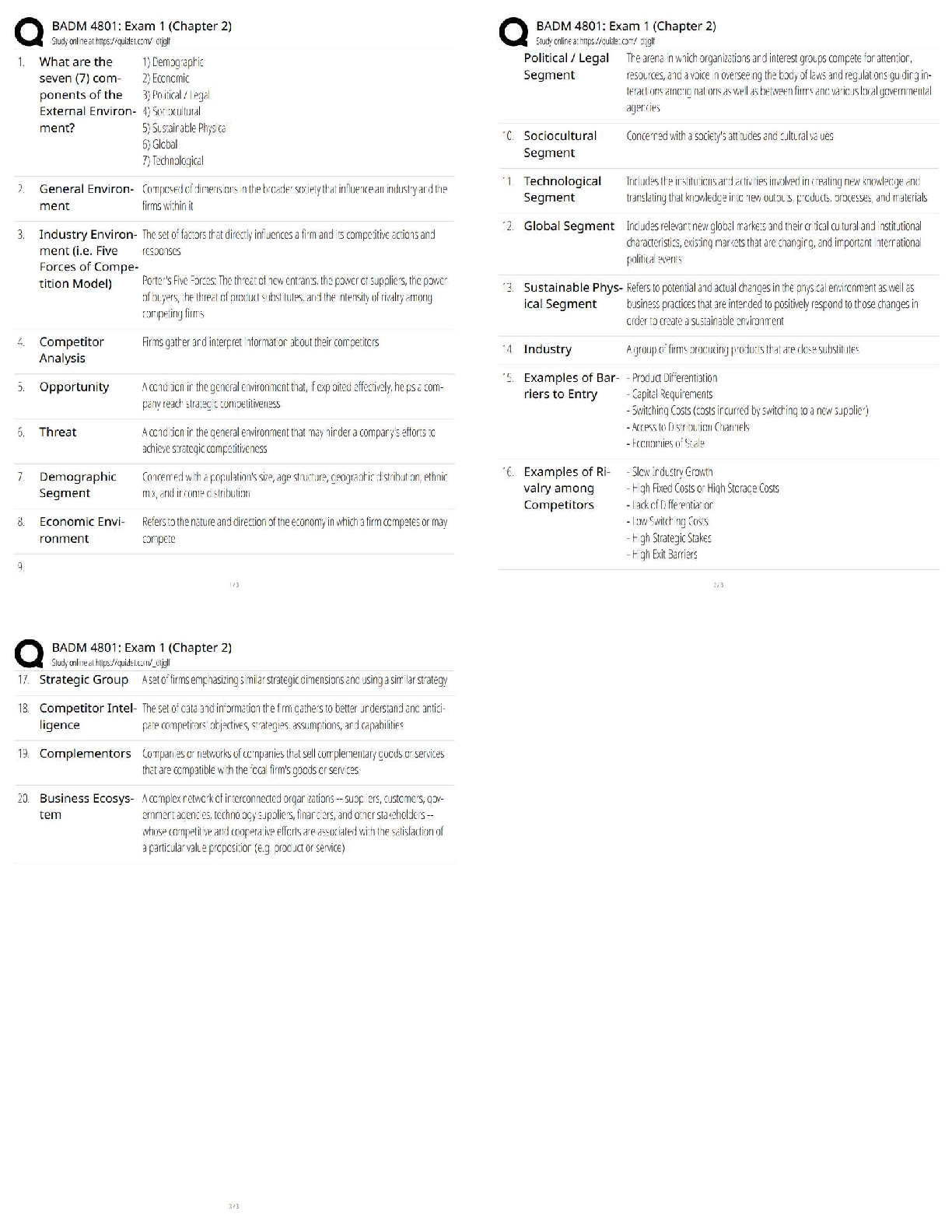
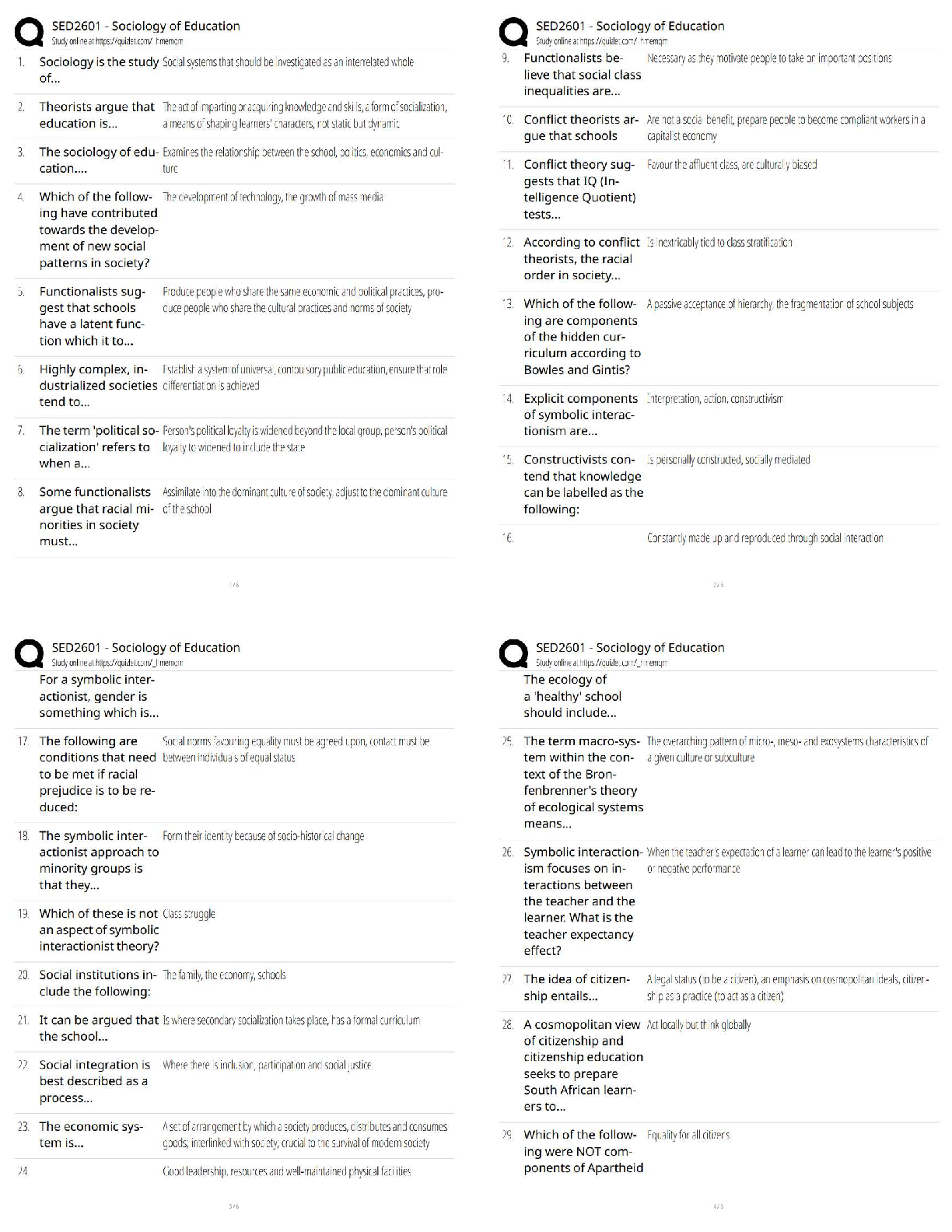
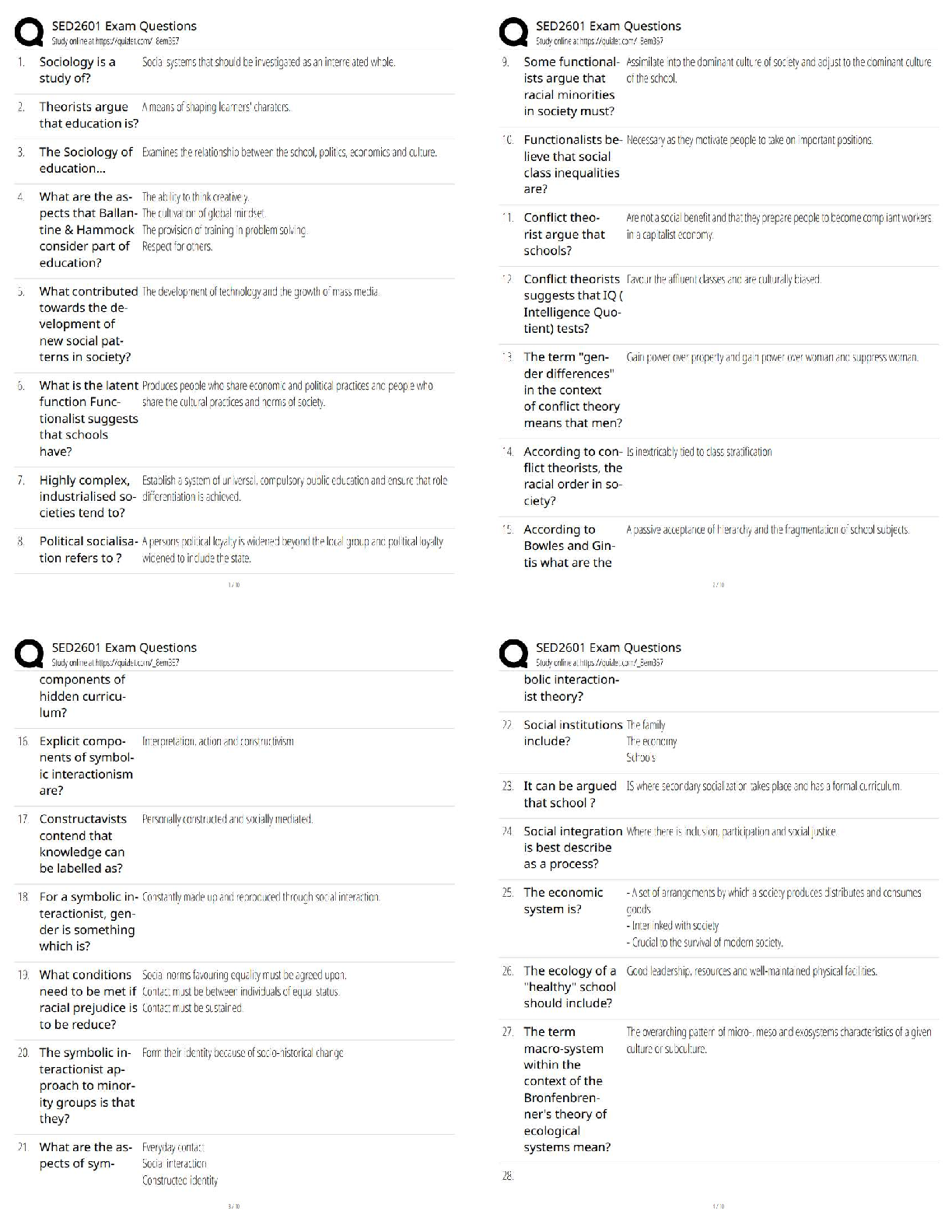
$ 12

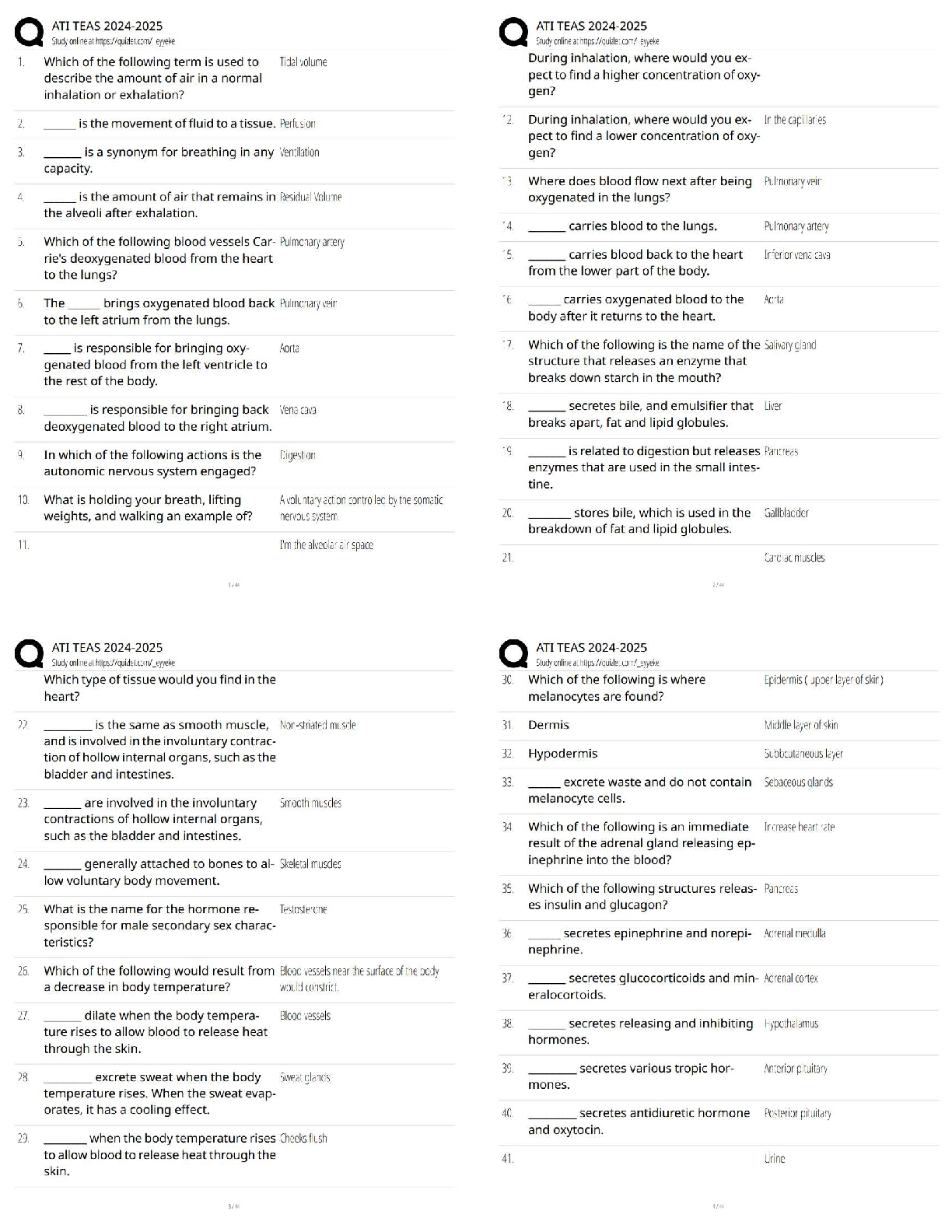
HESI Physics Questions with Answers and Explanations
$ 15

AQA AS PHYSICS 7407/2 Paper 2 mark scheme June 2021
$ 7

GCSE PHYSICS 8463/2F Paper 2 Foundation Tier Mark scheme June 2021
$ 7.5
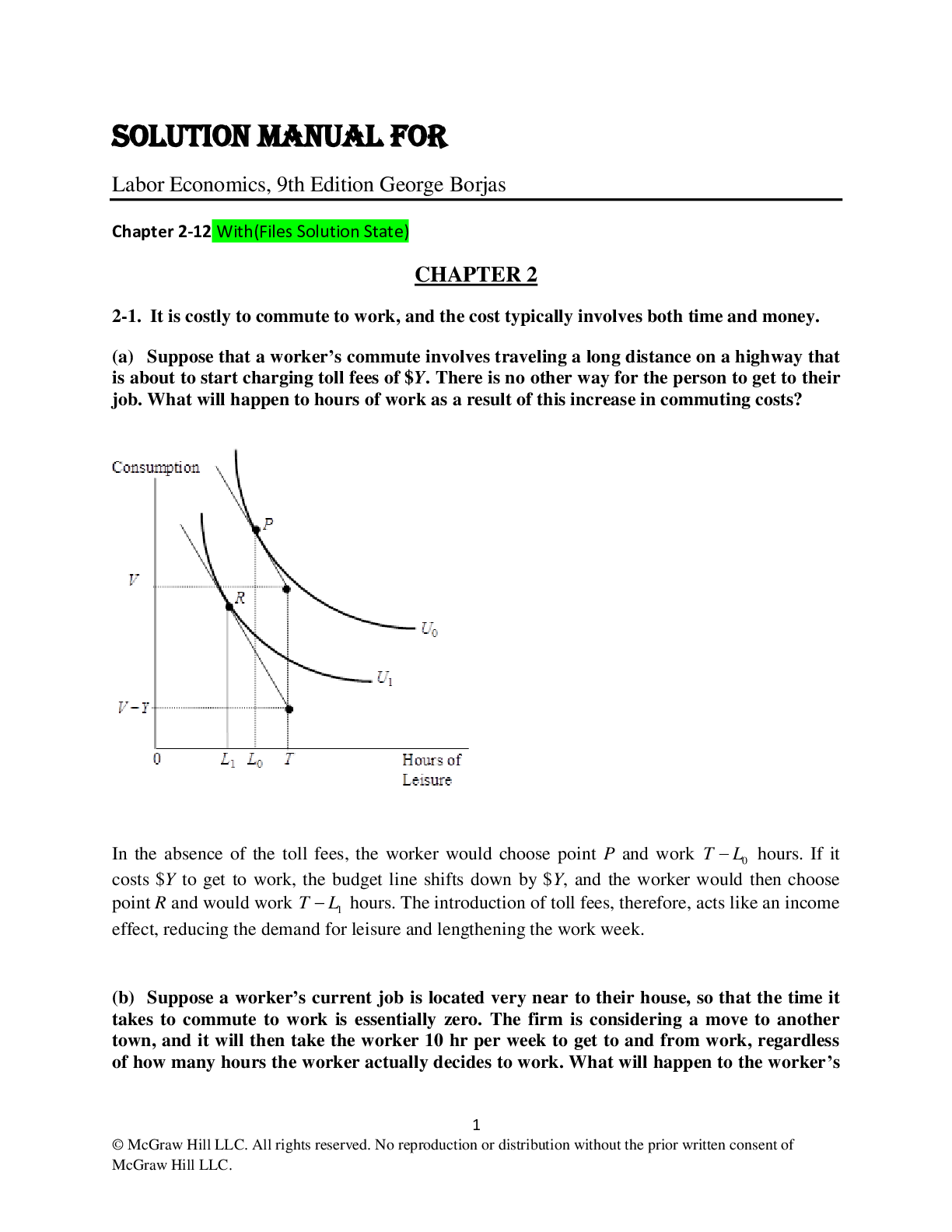
Solution Manual For Labor Economics, 9th Edition George Borjas | Chapter(2-12)
$ 19

hesi-exit-rn-exam-v5-2022-new
$ 16

WGU Course C170 - Data Management (Applications) Questions And Answers(Top Solution)
$ 14

STR 581 Week 6 Final Strategic Plan - Amazon University of Phoenix
$ 14
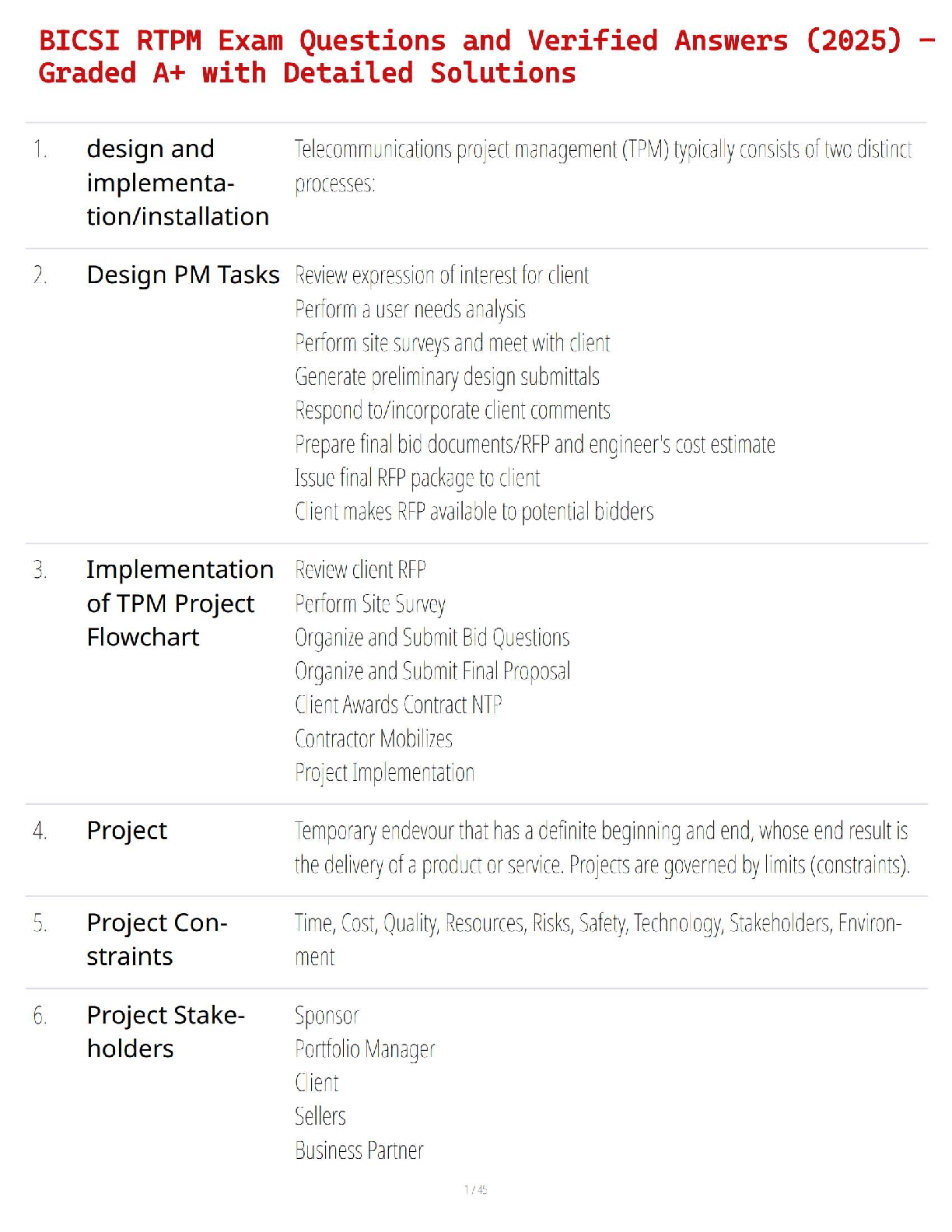
BICSI RTPM Exam Questions and Verified Answers (2025) – Graded A+ with Detailed Solutions
$ 28.5

BUS 206 Project 3 Contract Law.docx BUS 206 BUS 206 Project Three “ Contract Law New Hampshire University There are four elements to a contract: offer, acceptance, consideration, and capacity. The four elements must be present for a valid contract
$ 7

Kathleen Parks Comprehensive IHuman Case Week #9 26 Year Old Female Reason For Encounter: Frequent Severe Headaches Location; Outpatient Clinic Case Study (Class 6512)
$ 24

OCR A Level Business H431/03 The global business environment June 2025
$ 15
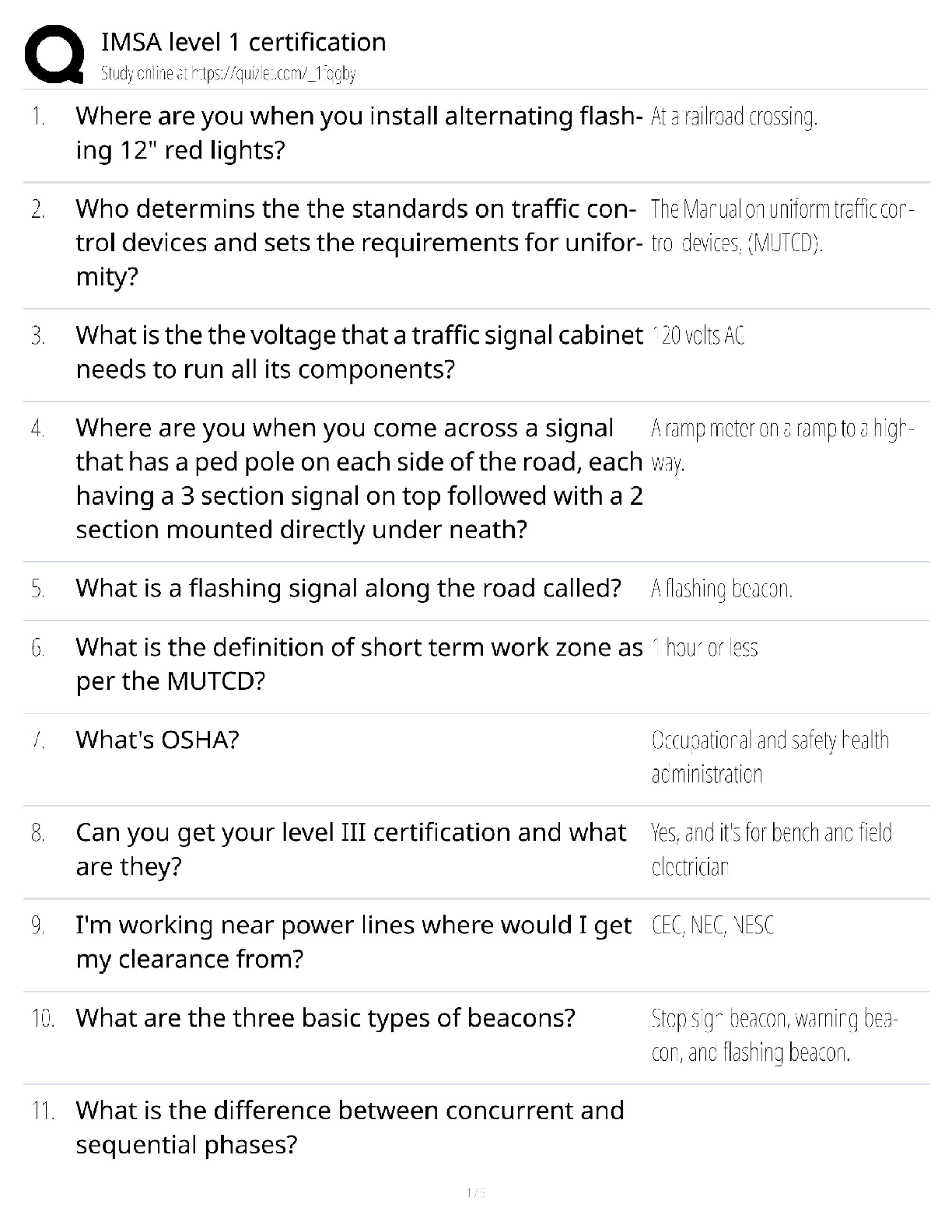
IMSA Level 1 Certification 2024 / Traffic Signal Technician Exam Prep / Practice Tests
$ 6.5

CST 610 PROJECT 2: Risk Assessment of a Small Business Local Area Network (LAN) and Wide Area Network (WAN) | University of Maryland Global Campus.
$ 7

Summary_A-Level_2020_Business_Studies_Paper_1_Mark Scheme
$ 11

CHAPTER SOLUTIONS > Chapter 12 Tourism Components and Supply Virginia Tech HTM 2454
$ 4

GLO-BUS Decisions & Reports years 6/ GLOBUS Decisions & Reports years; Latest 2019/20 Complete Guide, Already Graded A.
$ 8
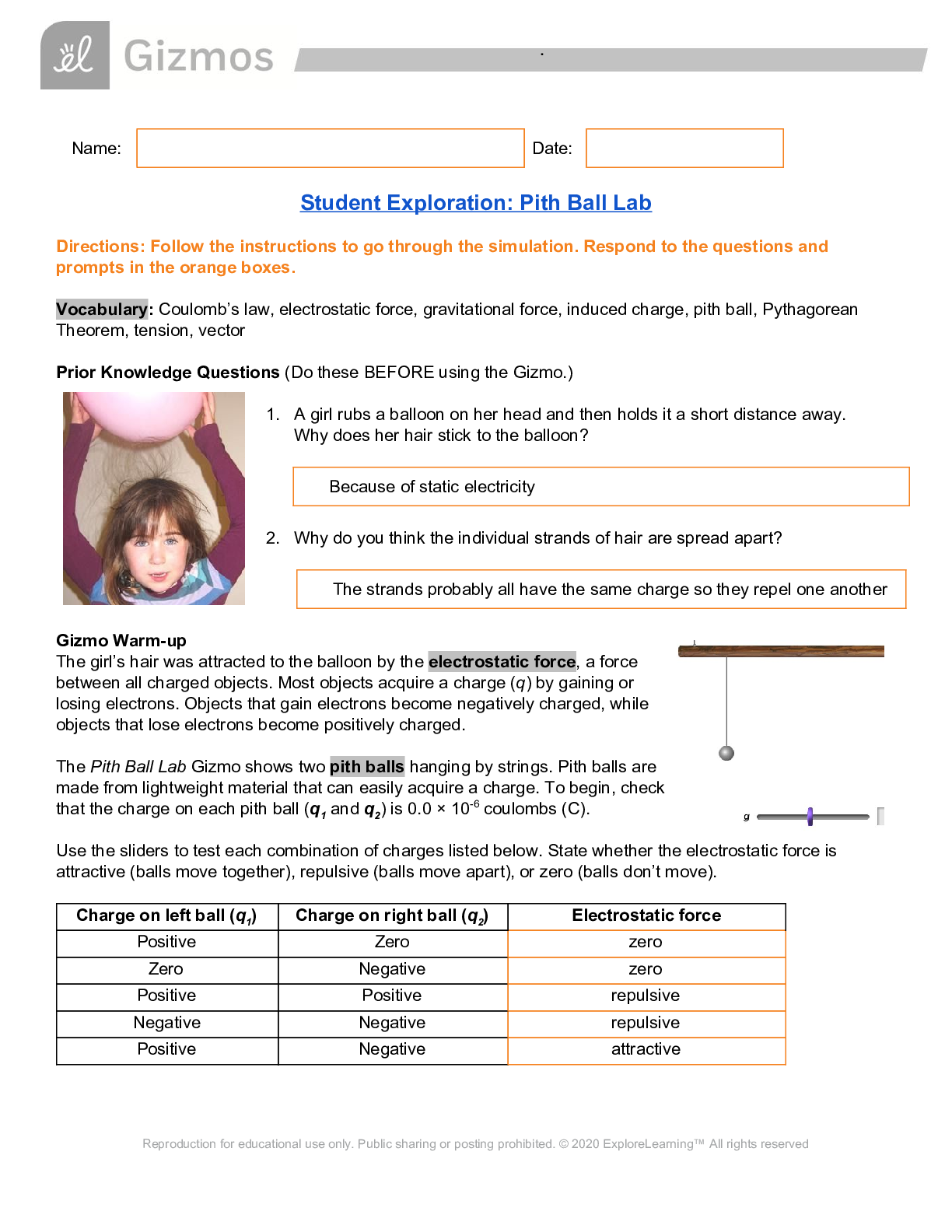
Pith Ball Lab (answered) Gizmoz; Student Exploration: Pith Ball Lab 2021
$ 8

Grand Canyon University BUS 485 Executive Summary.
$ 7

Business Analytics, Communicating with Numbers, 2nd Edition by Sanjiv Jaggia, Alison Kelly, Kevin | Solutions Manual
$ 24
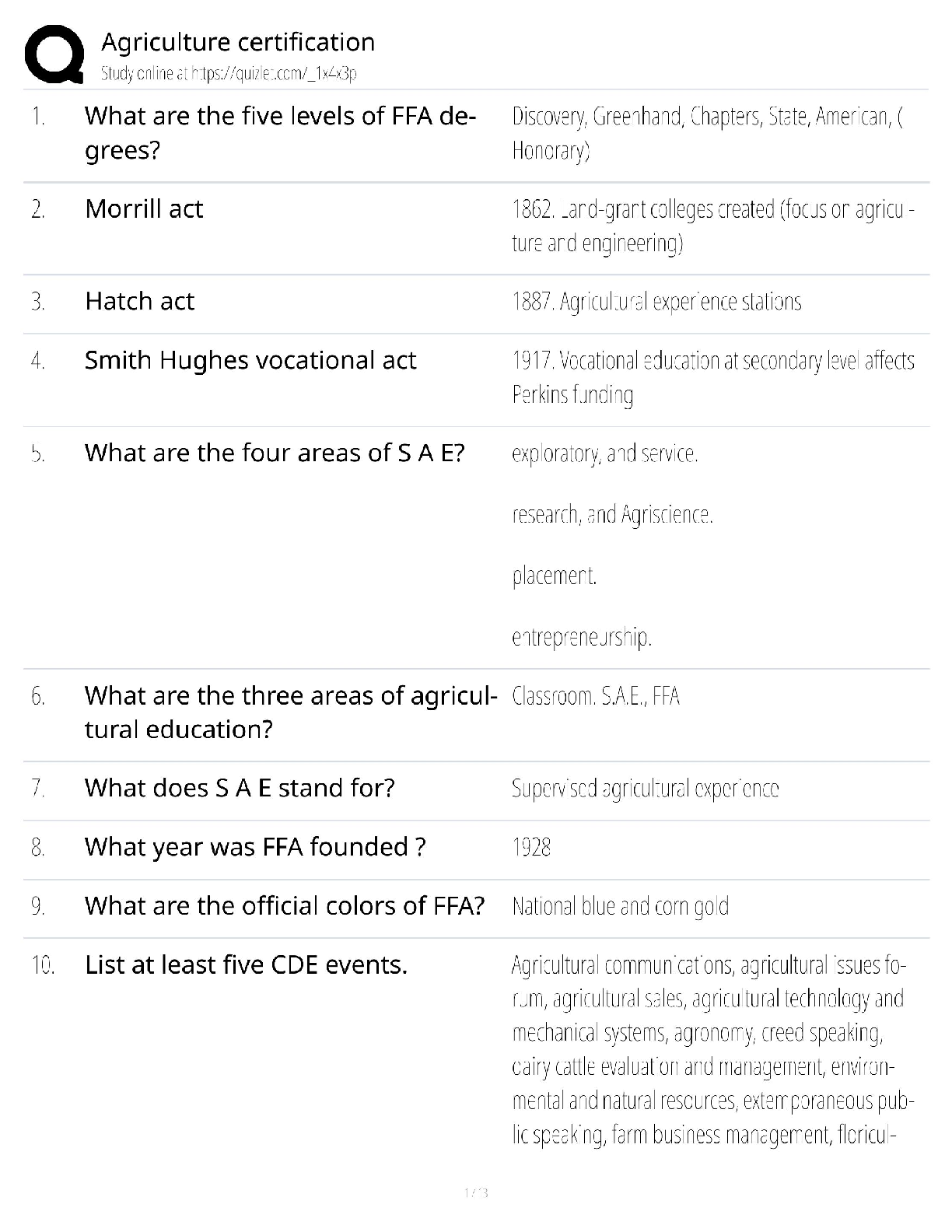
Agriculture Certification / Professional Agronomy & Crop Advisor Exam / 2025 Study Guide & Practice Test / Pass Guarantee
$ 29.5

Solutions Manual For Modern Compressible Flow With Historical Perspective 4th. Edition By John Anderson
$ 20
WGU D210 - DTAN 6204 Representation & Reporting - Comprehensive OA Guide 2024
$ 11
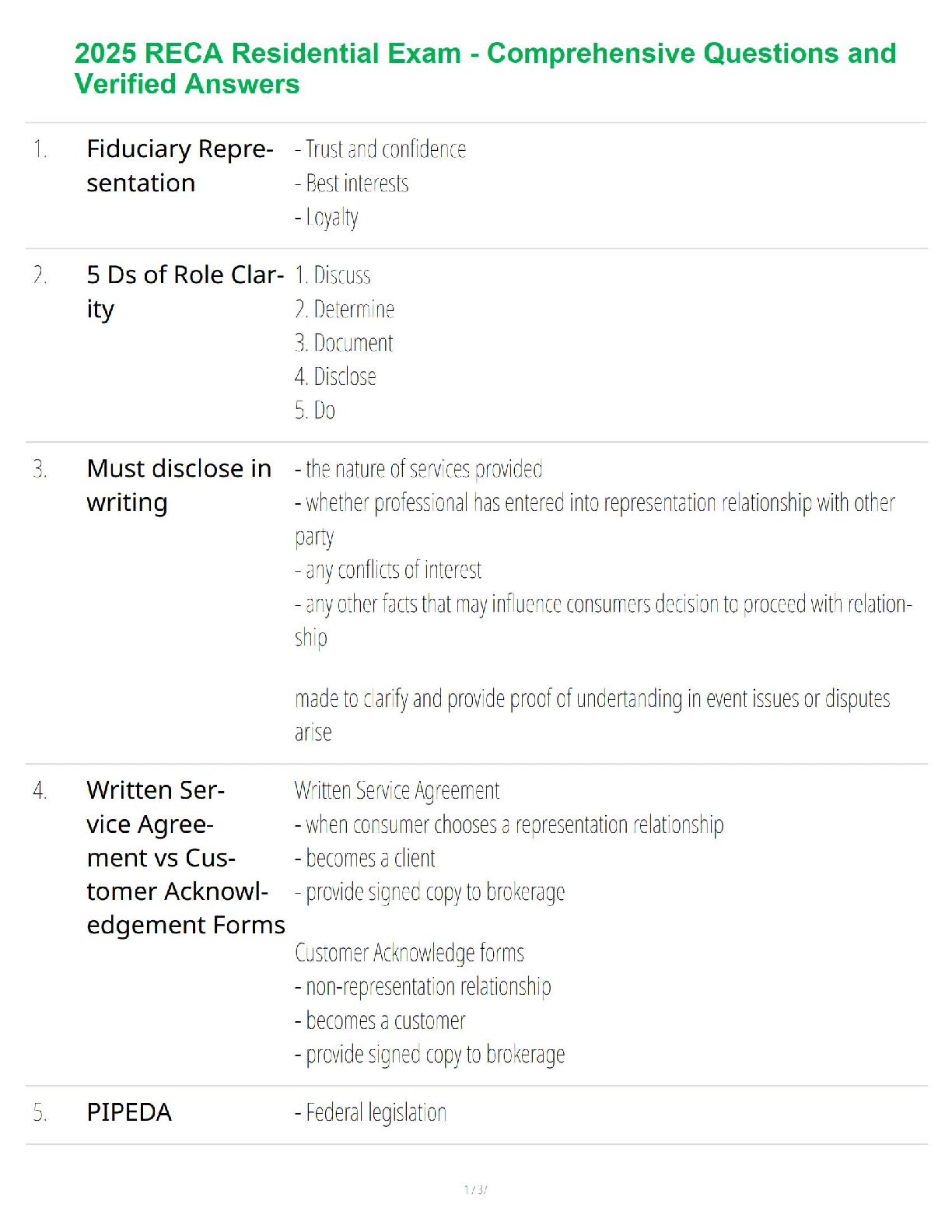
2025 RECA Residential Exam - Comprehensive Questions and Verified Answers
$ 32

CyberRookie CSX Fundamentals - Section 6: Security Implications and adoption of evolving technology
$ 12
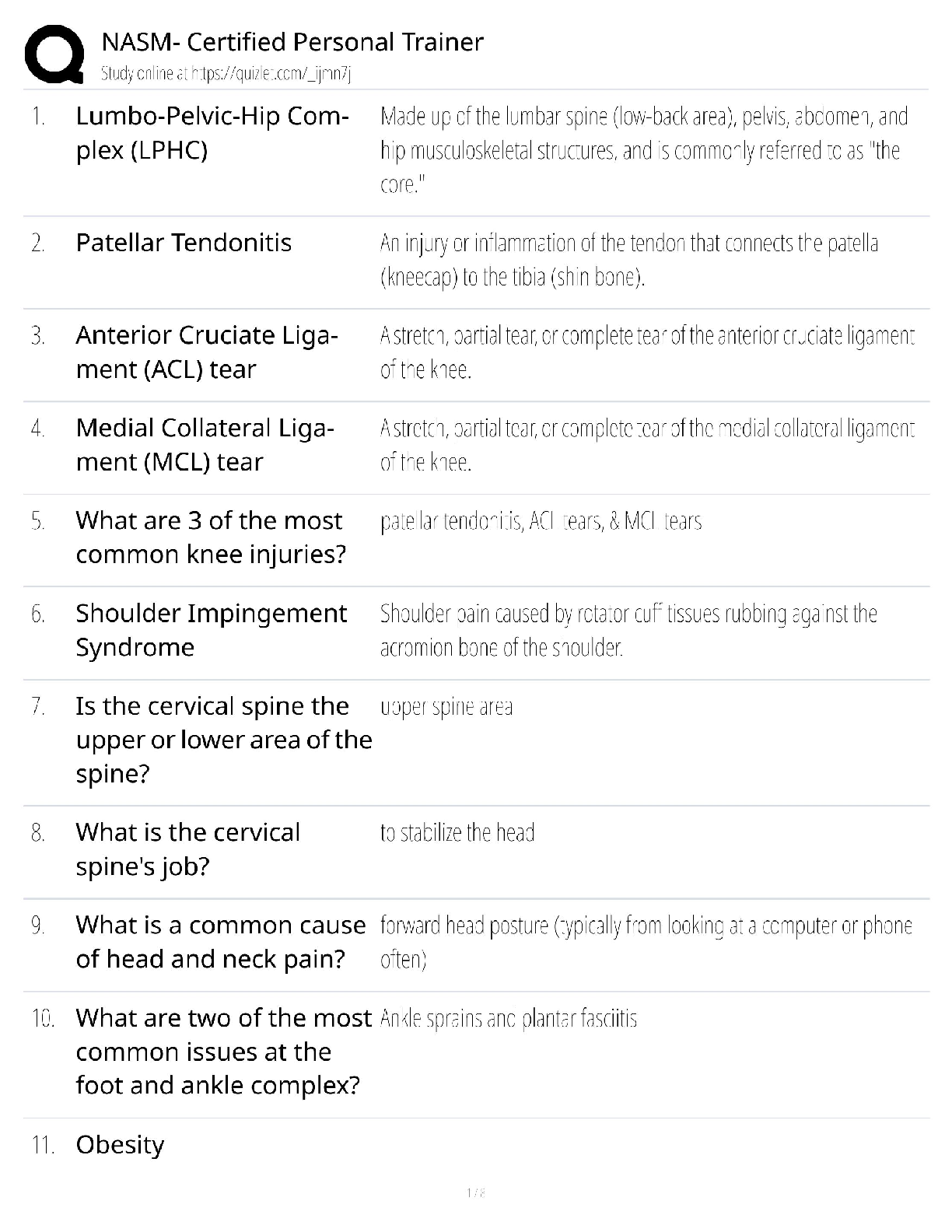
NASM Certified Personal Trainer (CPT) / Complete Exam Study Guide & Test Bank / 2025 OPT Model / Pass Guarantee
$ 19

BUS 372 Week 4 Assignment ( Cost Of Living ) - A Graded, Quality Work
$ 11

{NGN}ATI RN Comprehensive 2023!!!! ATI COMPREHENSIVE PREDICTOR VERSION 1 COMPLETE (150) QUESTIONS AND ANSWERS LATEST 2022/2023
$ 17

Information on writing a good thesis statement LATEST 2021/2022
$ 15

(5) 2021-2024 AORN PeriOp 101 Exam Qs&As Perioperative Assessment; Perioperative Safety: Patient Focus; Preoperative Skin Antisepsis; Positioning; Transmissible Infection Prevention
$ 13

Summary Week 1 Organizational Change Matrix AET/560 Organizational Change Matrix Complete the following matrix to analyze the human factors that influence organizational change. Write 1 or 2 complete sentences to explain your rationale for each facto
$ 7

RHIT EXAM PREP DOMAIN 1 PRACTICE QUESTIONS 2023 LATEST UPDATE
$ 12.5
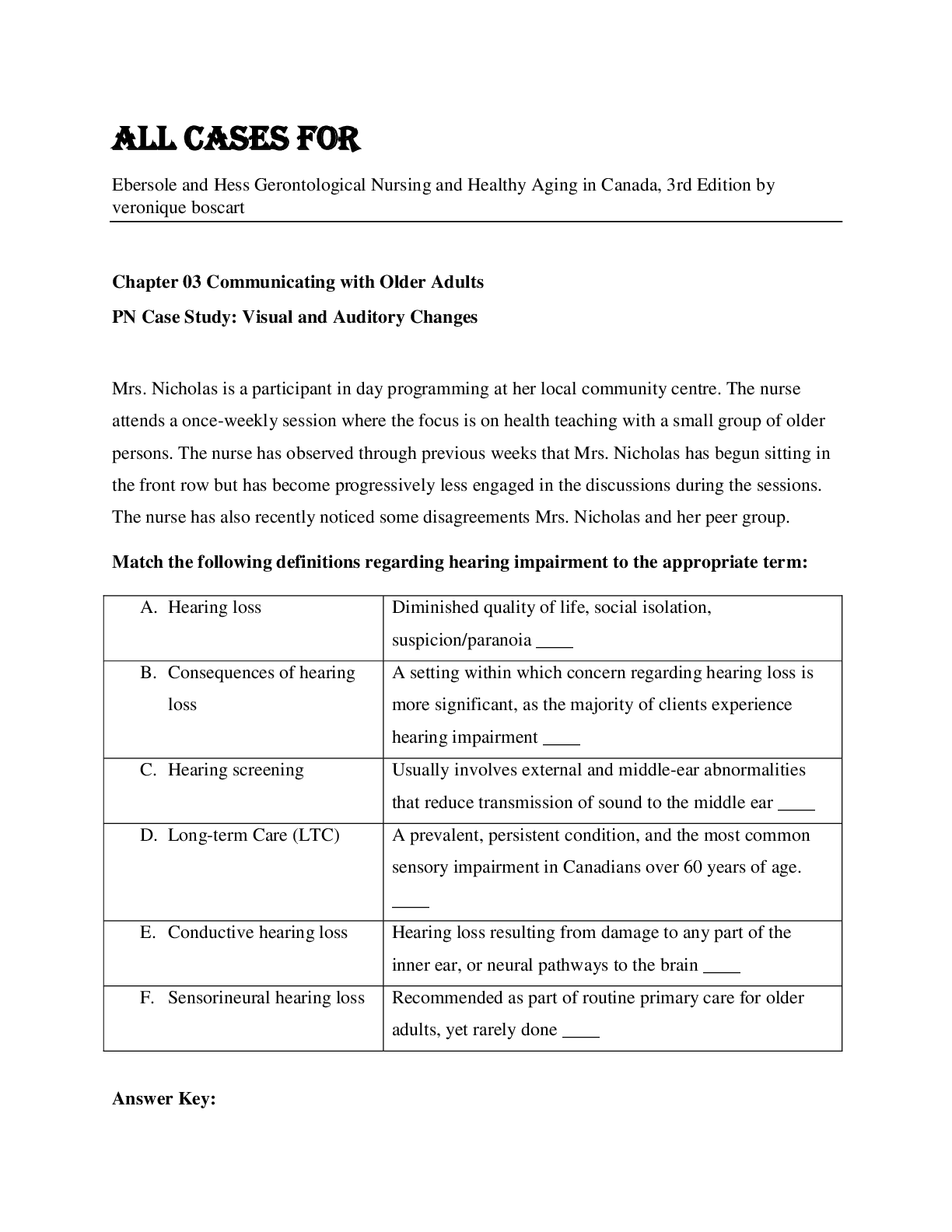
ALL CASES for Ebersole and Hess Gerontological Nursing and Healthy Aging in Canada, 3rd Edition by veronique boscart
$ 14

BSW3702 – Assessment 02: Practise Material (2025) University of South Africa | Social Work Theory, Case Analysis & Community Practice Grade A
$ 12

Solution Manual for Principles of Taxation for Business and Investment Planning 2024 27th Edition By Jones, Shelley, Callaghan, Kubick | All Chapters, 100% original verified
$ 22

Summary STR581 Week 1 Case Study.docx Wk1 Apply Case Study Analysis: "Case 6 Fixer Upper: Expanding the Magnolia Brand" STR/581 Wk1 Apply Case Study Analysis: "Case 6 Fixer Upper: Expanding the Magnolia Brand" Through a collection of busines
$ 4.5

CIPS L4M1 SAMPLE QUESTIONS AND ANSWERS RATED A.
$ 1

AP Physics Unit 3 Progress Check MCQ part A_Answered correctly, 22/23.
$ 8

CPPO Questions and Answers of the day 2023
$ 5.5

WGU Psychology c180 Questions and Answers Already Passed
$ 11

Business J204/02: Business 2: operations, finance and influences on business General Certificate of Secondary Education QUESTION PAPER for November 2020
$ 6.5

Social Studies 7-12 PACT Questions and Answers Rated A+
$ 20.5

accounting
$ 7
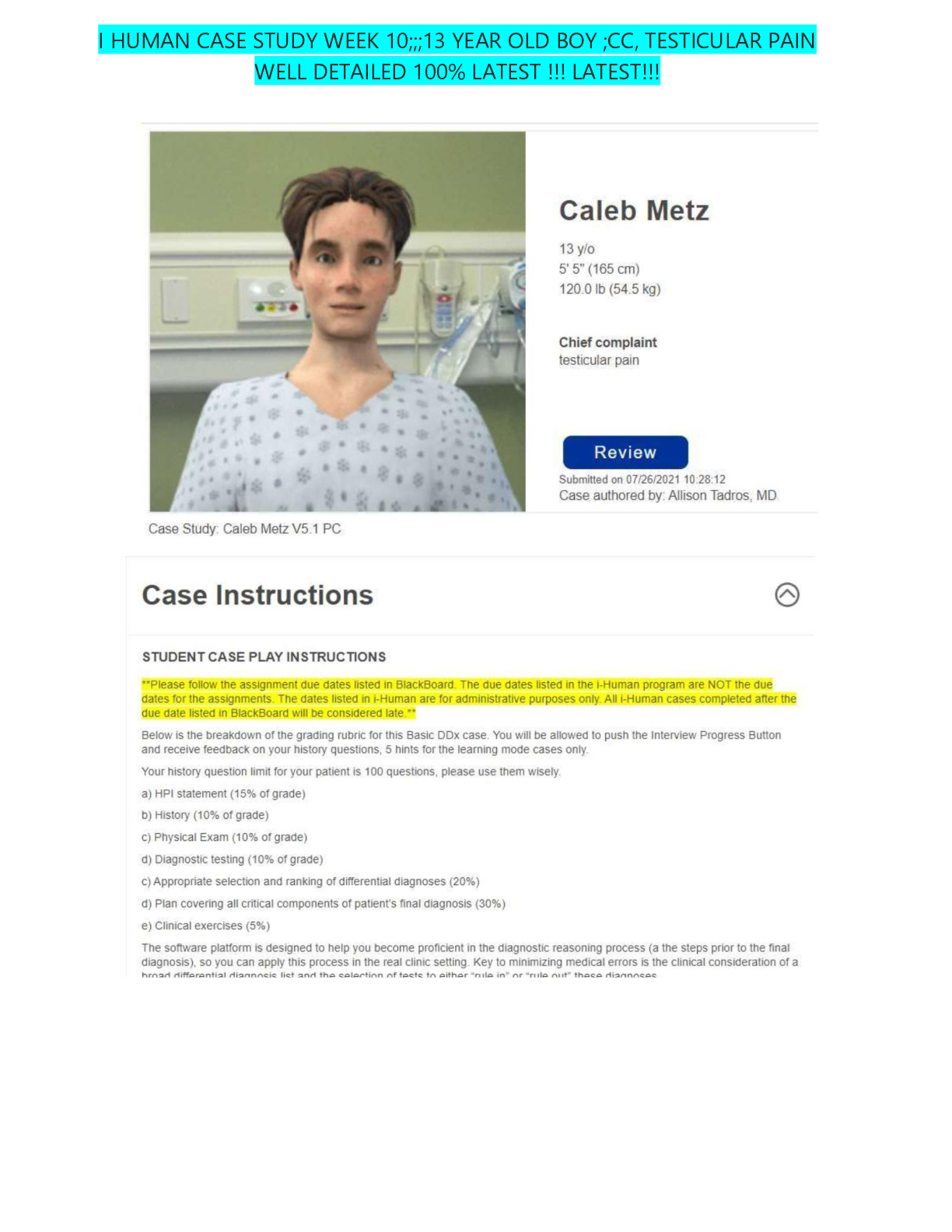
Caleb Metz, 3-Year-Old Boy With Testicular Pain (CLASS 6512) | iHuman Case Analysis Week #10 | Comprehensive Case Study With Testicular Pain | Includes HPI, PE, Differential Diagnosis, and Management Plan and EXPERT FEEDBACK
$ 24

Gray's Anatomy for Students, 5th Edition by Richard Drake, Wayne Vogl, Adam Mitchell SOLUTIONS MANUAL
$ 19

AQA A-level PHYSICS Paper 3 Section A June 2020 QP
$ 5

PICOT | PICO(T) To Prepare: Review the Resources and identify a clinical issue of interest that can form the basis of a clinical inquiry.
$ 10

AQA A-level PHYSICS Paper 2 Merged Question Paper + Mark Scheme 2025
$ 10.5

SOLUTION MANUAL FOR The Legal and Regulatory Environment of Business, 19th Edition By Marisa Pagnattaro, Daniel Cahoy, Julie Manning Magid, Peter Shedd Chapter 1-22
$ 26

Complete final business plan
$ 10

Solutions Manual For Macroeconomics, 8th Edition by Olivier Blanchard | All Chapters 1-24
$ 22
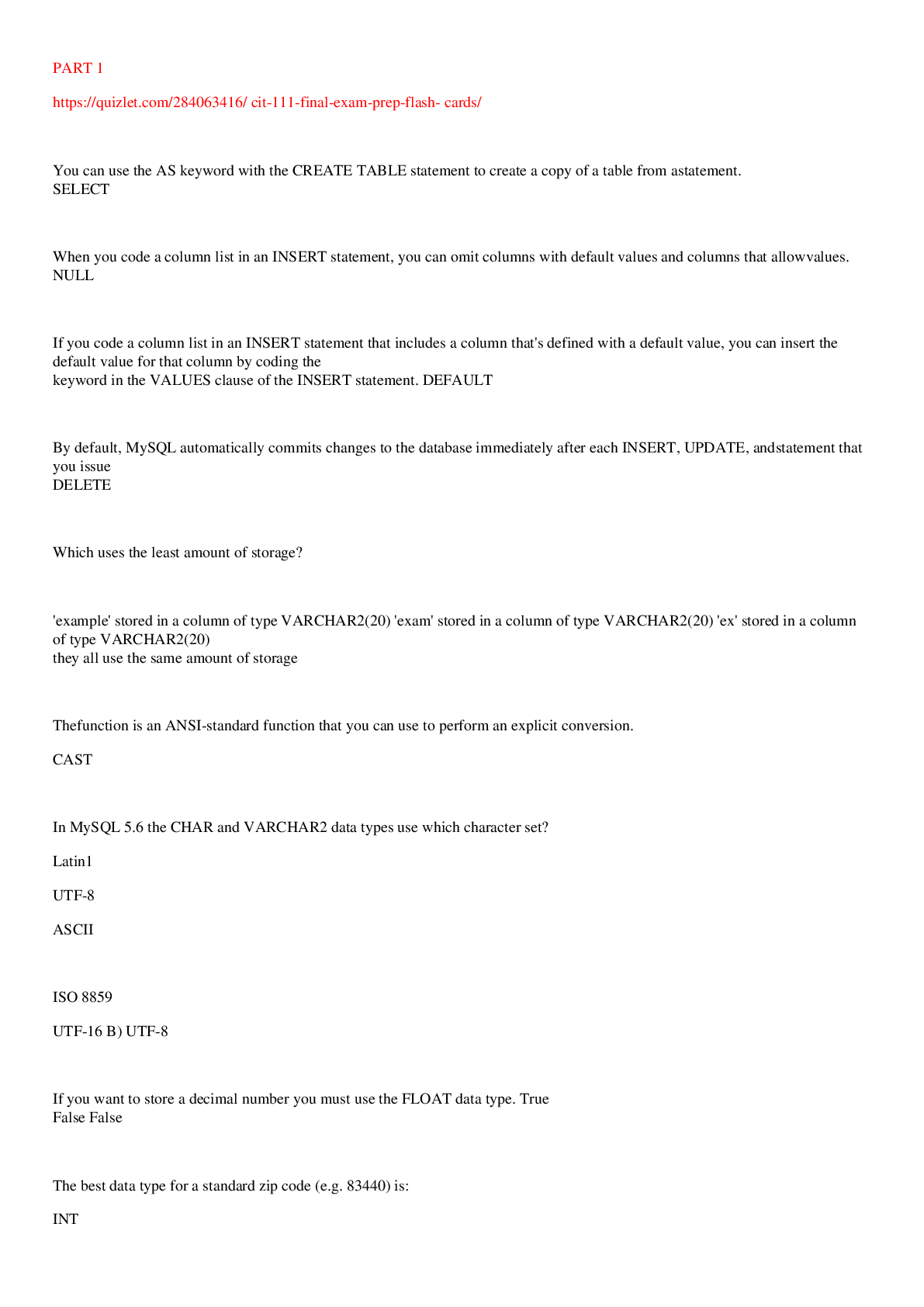
CIT 111 Final Exam Prep Flash Cards
$ 8

C12 - Business Law Case Analysis 4, Awad v. Ziriax - Ashworth College
$ 8

AQA June 2022 Question Paper A-level BUSINESS Paper 1 Business 1 7132/1
$ 7
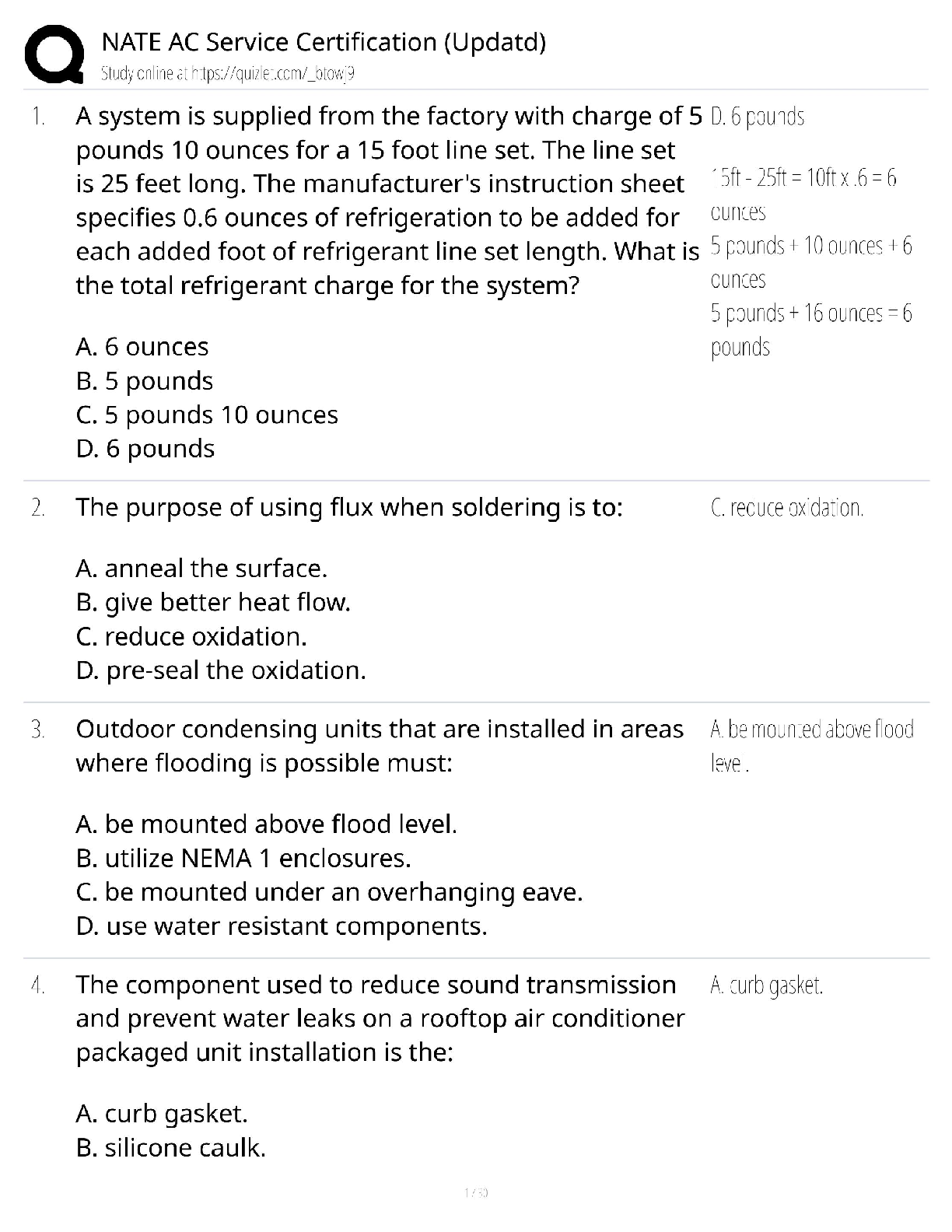
NATE AC Service Certification / Updated Study Guide & Practice Exam / Score 100% / 2025 HVAC Technician
$ 29.5

SOLUTIONS MANUAL Ordering and Payment Page: Make payment here, Provide the TITLE and You will receive your SPECIFIC Solutions Manual via email and/or download link. [ If you have any questions, please contact us.]
$ 30

Cornell UniversityHADM 4280Lec17-3210-F13-Spencer Levy Presentation
$ 13

The Digital Information Age An Introduction to Electrical Engineering 2nd Edition By Roman Kuc (SOLUTIONS MANUAL All Chapters, 100% Original Verified, A+ Grade)
$ 26

Security Strategy / Score 100% / New 2025 Update / CISSP, CISM Study Guide & Test Bank
$ 29

eBook [PDF] Advanced Engineering Mathematics and Analysis Vol 1 By Rami A. Maher
$ 30

GLO-BUS Decisions & Reports years 7/ GLOBUS Decisions & Reports years; Latest 2019/20 Complete Guide, Already Graded A.
$ 8.5

MRL3702-labour_law_notes_chapter_1 2020 /2021
$ 8
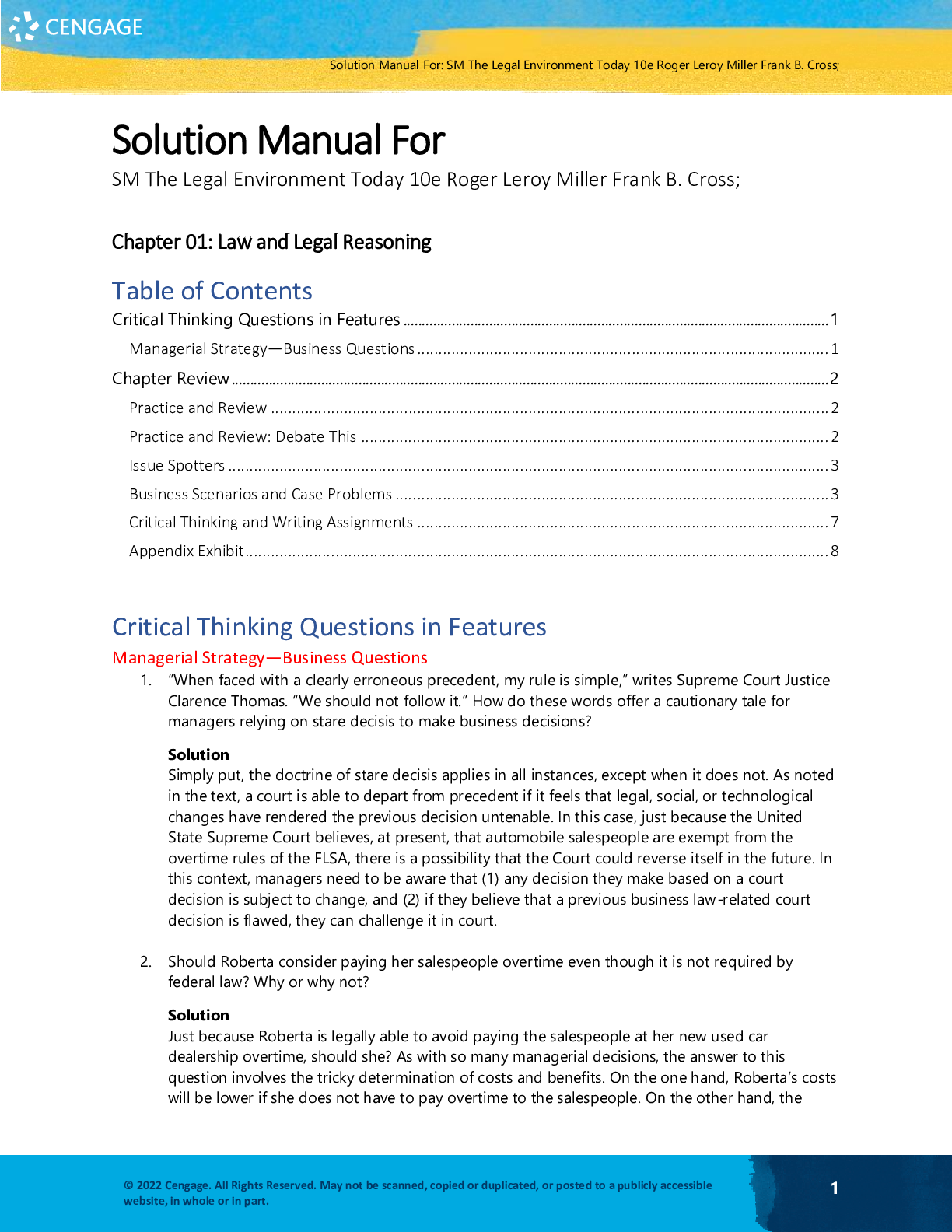
Solution Manual For The Legal Environment Today 10th Edition by Roger LeRoy MillerFrank B. Cross Chapter(1-24)
$ 19

COM 312 Exam 2 Study Guide 59 Questions with Verified Answers,100% CORRECT
$ 8.5

ATI RN COMPREHENSIVE EXIT EXAM (100% verified to get grade A+)
$ 9.5
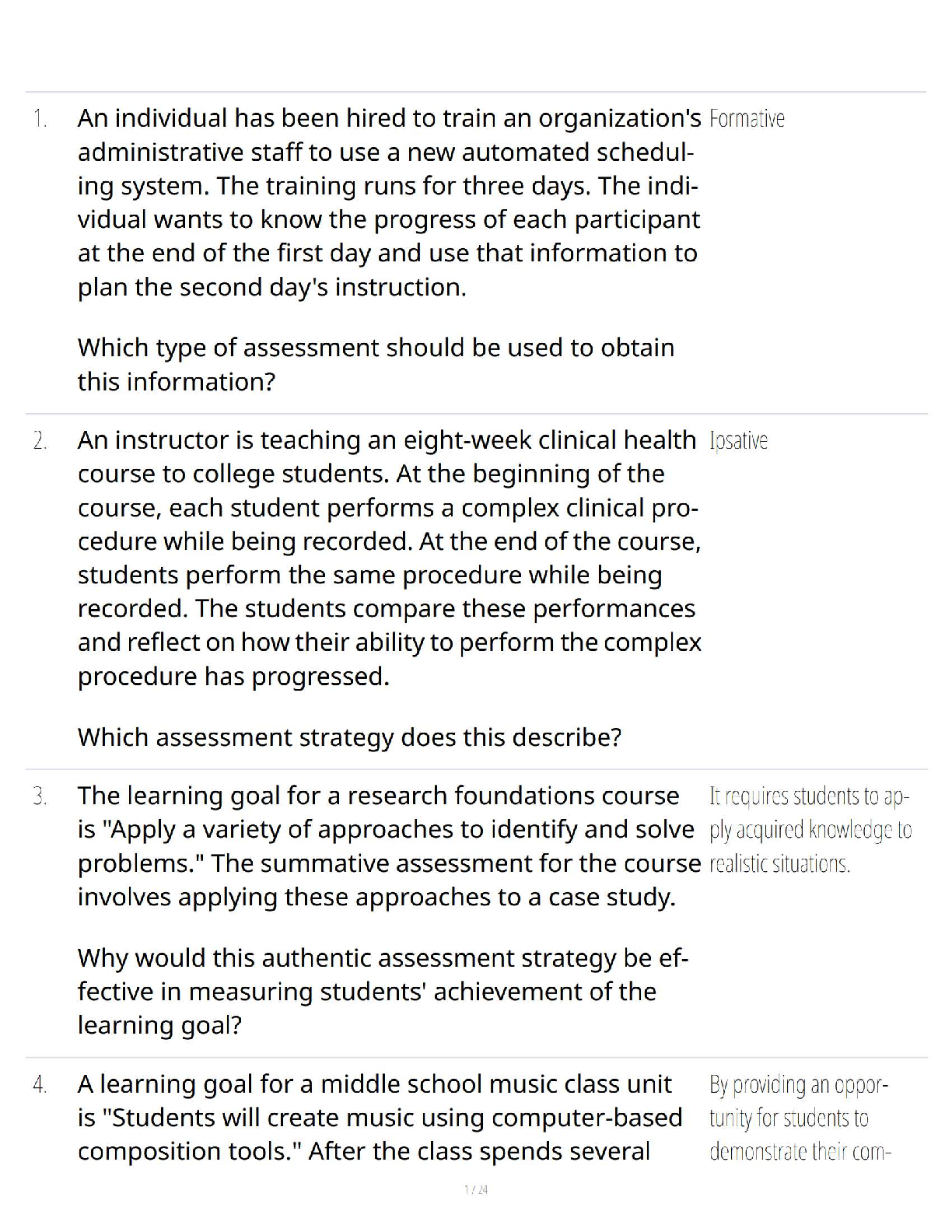
📊 D293 – Pre-Assessment | Assessment and Learning Analytics | Western Governors University | Verified Questions and Correct Answers | 100% Accurate | Grade A
$ 10.5

WGU D427 DATABASE MANAGEMENT APPLICATIONS EXAM PRE-ASSESSMENT AND OBJECTIVE ASSESMENT
$ 18

CPPO PREP EXAM WITH COMPLETE QUESTIONS AND ANSWERS
$ 8

📊 D293 – Cheat Sheet: Assessment and Learning Analytics | Western Governors University | Verified Concepts and Key Terms | 2025–2026 Edition
$ 10

Solution Manual For Fraud Examination 7th Edition by W. Steve AlbrechtChad O. AlbrechtConan C. AlbrechtMark F. Zimbelman Chapter 1-18
$ 19

TNCC test prep A. Questions and answers. Graded A+
$ 10

MB 101 Bloomberg Answers - Economic Indicators
$ 9

NURSING 4130 shadow health preeclampsia
$ 15

Exam (elaborations) s Introduction to Information Technology -IT Milestone 1.
$ 13

Hth 100 exam 4 with complete solutions 100 verified 2026
$ 6

MKT113 Final Project Part IProduct Overview| MKT113: Final Project Part IProduct Ov
$ 7

University of Texas, Dallas - OPRE 6362Slide Presentation.
$ 7

Physics for Scientists and Engineers with Modern Physics 10th Edition By Raymond Serway, John Jewett SOLUTIONS MANUAL
$ 20

Clinical Cases in Cardiology Atooshe Rohani Clinical Cases in Cardio-Oncology
$ 12

(Answered) LDR 535 Week 6 Apply Signature Assignment Change Management Presentation
$ 10
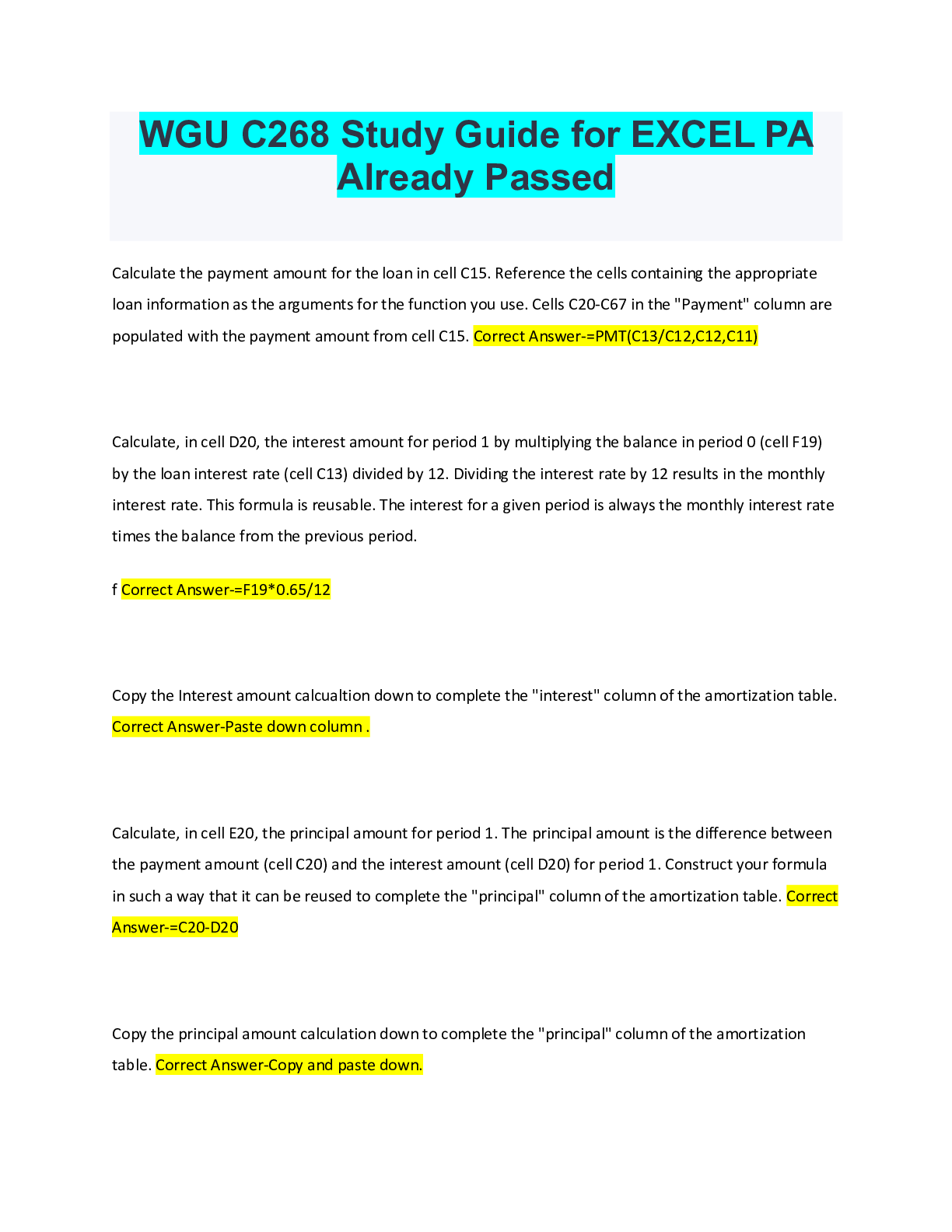
WGU C268 Study Guide for EXCEL PA Already Passed
$ 7

Advances in Anesthesiology (Volume 2) Anesthesia: A Topical Update - Thoracic, Cardiac, Neuro, ICU, and Interesting Cases
$ 12
.png)
Strayer University - HRM 530 COMPENSATION & BENEFITS PACKAGE POWERPOINT FINAL PRESENTATION
$ 15

Exam 12 November 2015, questions and answers Physics for Biomedicine (University of Melbourne) | Download for quality grades
$ 20

Clinical Cases in Dermatopathology Robert A. Norman
$ 12

BIS 320 Week 5 Individual Assignment, IT Strategic Project Presentation
$ 13

Clinical Cases in Dermatology Clinical Cases in Pruritus Shannon C. Trotter
$ 12

NRS 428; Community Teaching Plan: Teaching Experience Grand Canyon
$ 7

Solution Manual For On Cooking A Textbook of Culinary Fundamentals, 7th Edition By Sarah R. Labensky Alan M. Hause Priscilla A. Martel
$ 19
Week 3 - Project Coffee Shop - Scope Statement latest documents 2020
$ 8.5

PSI NJ Real Estate Exam Questions and Answers Latest Updates 2024














.png)