Information Technology > QUESTIONS & ANSWERS > AWS Key Questions with accurate answers. 100% verified/ 2022/2023. Rated A (All)
AWS Key Questions with accurate answers. 100% verified/ 2022/2023. Rated A
Document Content and Description Below
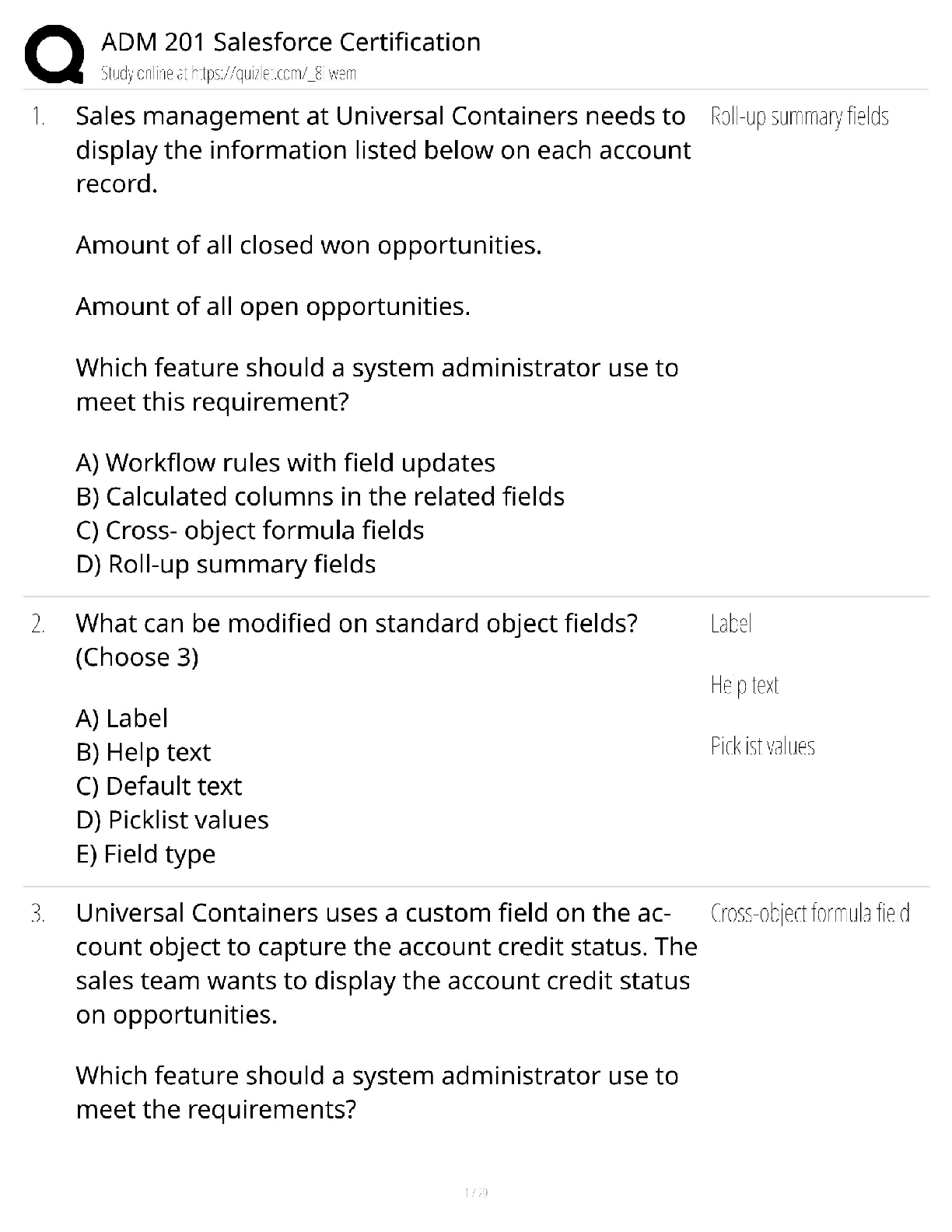
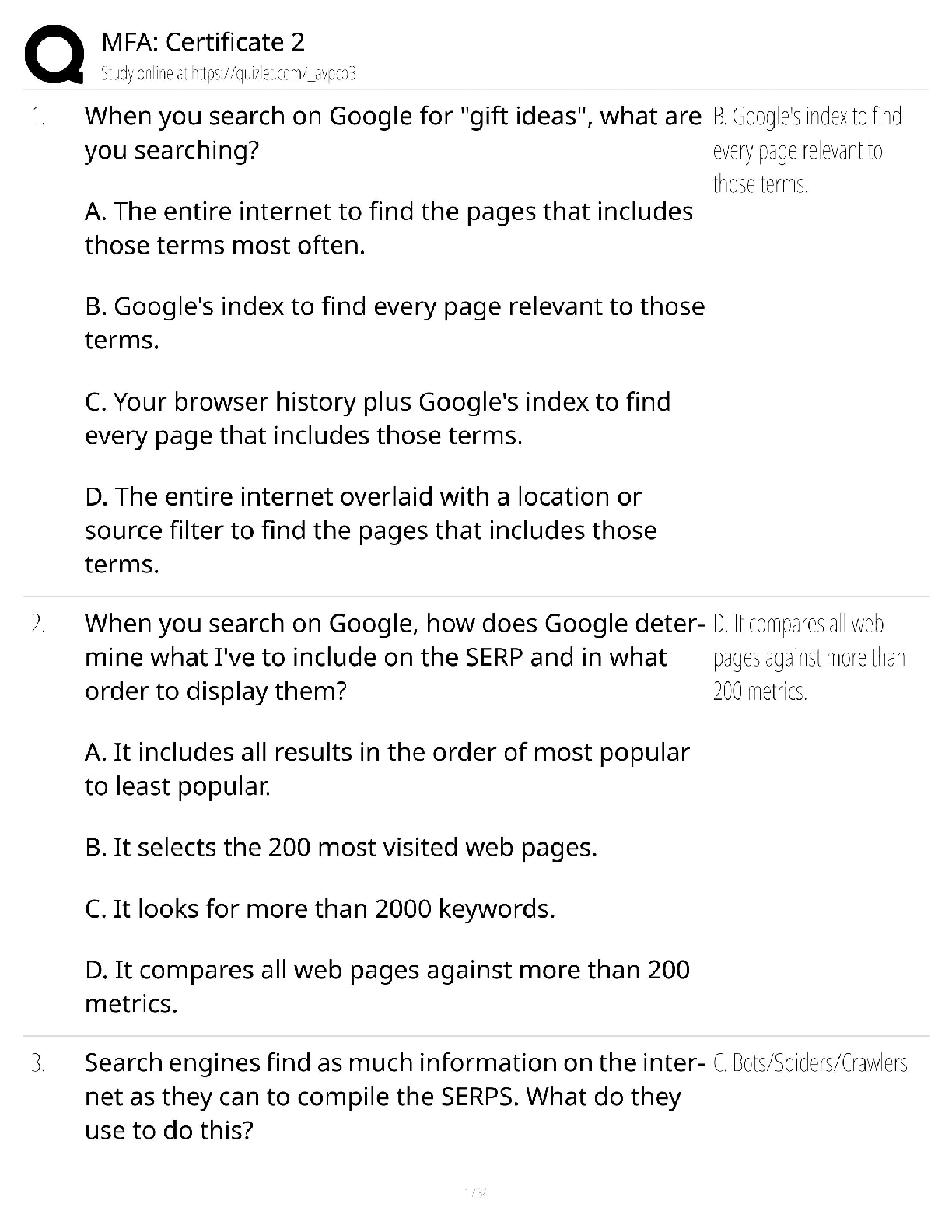
AWS Key Questions with accurate answers. 100% verified/ 2022/2023. Rated A Access Keys are digitally signed requests to AWS API's. Keys Pairs are used for sshing to EC2 instances, and for Cloud ... front signed urls. Amazon uses 1024 bit SSH-2 RSA keys. You can have them generated or upload your own. X509 certificates are only for SOAP requests to API's. - ✔✔What's the difference in Access Keys, Key Pairs, and X509 certificates? AWS allows you to have multiple sets of concurrent keys and certificates, allowing you to roatate them in and out. - ✔✔What features allow you to update your access keys and certificates with no impact to operations? Requires you to enter a six digit code in addition to username and password. Code is retrieved from either a hardware or virtual MFA device - likely an app running on a cell phone. Utiliza by adding the MFA requirement to an IAM policy, then attaching those policies to IAM users, groups, or resources that support ACL's like S3 buckets, SQS queues, and SNS topics. - ✔✔What is multifactor authentication (MFA)? Inspects your AWS environment and makes reommendations to save money, improve performance, or close security gaps. Looks for common errors like leaving certain ports open, public access to s3 buckets, not turning on cloudtrail, and not using MFA on root accounts. - ✔✔What's Trusted Adviser used for? Normally, each EC2 instance you launch is randomly assigned a public IP address in the amazon EC2 address space. VPC allows you to create an isolated portion of the AWS cloud and launch EC2 instances that have private address in the range of your choice (10.0.0.0, for instance) - ✔✔Why use a VPC EC2 instances running within a VPC inherit all of the security benefits of the VPC (guest os protection, protection against packet sniffing), but you must create security groups specifically for your Amazon VPC. amd Amazon EC2 security groups you have created will not work inside your Amazon VPC. - ✔✔What happens to EC2 security groups when used inside a amazon VPC? 1. Being able to change the security group after the instance is launched 2. Being able to specify any protocol with a standard number, rather than just TCP, UDP, or ICMP - ✔✔What benefits to VPC security groups give you that EC2 security groups do not? Inbound communication from other members of the same group, and outbound to any. - ✔✔What does the default VPC security group allow by default? Stateless traffic filters (must permit traffic in both directions) that apply to all inbound or outbound traffic from a subnet within a VPC. Ordered list, based on IP protocol, service port, and source destination IP - ✔✔How do network acl's work? It enables private connectivity between the Amazon VPC and another network. Networj traffic within each virtual private gateway is isolated from neteork traffic within all other virtual private gateways. You can establish VPN connections to the Virtual Private Gateway from gateway devices at your premises. Each connection is secured by a pre-shared key in conjunction with the IP of the customer gateway device. - ✔✔What's the function of a Virtual Private Gateway? An internet gateway may be attached to an Amazon VPC to enable direct connectivity to Amazon S3, other AWS services, and the internet. Each instance desiring this access must either have an elastic IP associated with it or route traffic through a NAT instance. Additionally, network routes are configured to direct traffic to the internet gateway. - ✔✔What's the function of an Internet Gateway? An Elastic IP address is a static IP address designed for dynamic cloud computing. An Elastic IP address is associated with your AWS account. With an Elastic IP address, you can mask the failure of an instance or software by rapidly remapping the address to another instance in your account. An Elastic IP address is a public IP address, which is reachable from the Internet. If your instance does not have a public IP address, you can associate an Elastic IP address with your instance to enable communication with the Internet - ✔✔What's the purpose of an elastic IP? If your Amazon EC2 instances are located inside a private subnet, you will not be able to connect to them remotely. To connect to your instances, you can set up bastion servers in the public subnet to act as proxies. For example, you can set up SSH port forwarders or RDP gateways in the public subnet to proxy the traffic going to your database servers from your own network - ✔✔What's the purpose of a bastion host? 1. A default subnet is created in each availability zone 2. An internet gateway is created and connected to your default VPC 3. A main route is created for your default VPC with a rule that sends all traffic destined for the internet to the internet gateway 4. A default security group is created and associated with your default VPC 5. A default ACL is created an associated with your default VPC 6. Default DHCP options set for your AWS account are associated with your default VPC - ✔✔What automatically happens for you when you launch a first time instance into EC2-VPC (also known as the default VPC)? 1. In the default VPC, instances will receive a public and a private IP automatically. In a normal VPC, will only get private 2. DNS names are enabled by default in the default VPC. Not in a normal VPC - ✔✔Some differences in launching EC2 instances in the default VPC vs a normal VPC Gives customers an easy way to distribute content to end users with low latency and high speed. Delivers dynamic, static, and streaming content using a glocal network of edge locations. Requests for data are automatically routed to the nearest edge location, so content is delivered with best possible performance. Optimized to work with S3, EC2, , ELB, and route 53. Can also work with non AWS orgin servers that store original versions of files. - ✔✔What's the purpose of cloudfront? You can enable the service's provate content feature. Has 2 components - one controls how content is delivered from edge locations to viewers on the internet, second controls how edge locations access objects in Amazon S3. Cloudfront also supports Geo Restriction, which restricts access to your content based on the geographic location of your viewers - ✔✔What are some of the ways that Cloudfront it secured? Cloudfront allows you to create one or more "Orgin Access Identities" and associate these with your distributions. When associated, the distribution will use that identity to retirve objects from S3. You can then ise S3's ACL feature, which limits access to the Orgin Access Identity so the original copy of the object is not publicly readable. - ✔✔How can you control access to the original copies of your S3 objects when using Cloudfront? The service uses a signed URL verification system. Create a public-private key pair, upload the public key to your account via the console, then configure the CloudFront distribution to indicate which accounts you would authorize to sign requests. Third, as you receive requests, you create policy documents indicating the conditions under which you want CloudFront to serve your content. Feature is optional. Without this feature, all content delivered will be publicly readable. - ✔✔How can you control who is able to download objects from Cloudfront edge locations? HTTPS is optional. By default, CloudFront will accept requests over both. You can configure CloudFront to require HTTPS, and you can even require it to allow HTTP for some objects but require HTTPS for others. - ✔✔By default, does CloudFront use HTTP or HTTPS? Allows you to provision a direct link between your internal network and an AWS region using a high throughput dedicated connection. You can then create virtual interfaces directly to the AWS cloud. You procure rackspace within the facility housing the Direct Connect location and deploy your equipement, then connect to to AWS Direct Connect using a cross connect. Use 802.1q vlans the partition the connection into multiple virtual interfaces. Using BGP and MD5 keys. - ✔✔What's the use case for Direct Connect? 1. IAM poilicies - Grant users within your own AWS account permission to access your Amazon S3 resources 2. ACL's - Give read or write access on buckets or objects to groups of users. Only used to grant other AWS accounts (not specific users) access to S3 resources 3. Bucket Policies - used to add or deny permissions across some or all of the objects within a single bucket. Policies can be attached to users, groups, or buckets. Can be used to grant access to users within your AWS account or other AWS accounts. - ✔✔3 ways to control access to objects and buckets in S3? A. It can be migrated across Availability Zones B. It is specific to an Amazon Machine Image (AMI) C. It can be applied to instances launched by Auto Scaling D. It is specific to an instance Type E. It can be used to lower Total Cost of Ownership (TCO) of a system You can have reserved instances migrated between availability zones, but not between regions. Reserved instances are tied to a specific instance type, but the size of that instance type can be changed. - ✔✔Which of the following are characteristics of a reserved instance? Choose 3 answers A. SQS guarantees the order of the messages. B. SQS synchronously provides transcoding output. C. SQS checks the health of the worker instances. D. SQS helps to facilitate horizontal scaling of encoding tasks. Answer D From SQS FAQ: During this whole workflow, a dedicated Amazon EC2 instance can constantly monitor the incoming queue and, based on the number of messages in the incoming queue, is able to dynamically adjust the number of transcoding Amazon EC2 instances to meet customers' response time requirements - ✔✔A company has a workflow that sends video files from their on-premise system to AWS for transcoding. They use EC2 worker instances that pull transcoding jobs from SQS. Why is SQS an appropriate service for this scenario? A. Create a load balancer, and register the Amazon EC2 instance with it B. Create a CloudFront distribution, and configure the Amazon EC2 instance as the origin C. Create an Auto Scaling group from the instance using the CreateAutoScalingGroup action D. Create a launch configuration from the instance using the CreateLaunchConfiguration action - ✔✔You have a content management system running on an Amazon EC2 instance that is approaching 100% CPU utilization. Which option will reduce load on the Amazon EC2 instance? True - ✔✔When creating an RDS instance you can select which availability zone in which to deploy your instance? The customer gateway is the appliance at your end of the VPN connection. (The device on the AWS side of the VPN connection is the virtual private gateway.) You must provide the Internet-routable IP address of the customer gateway's external interface. http://docs.aws.amazon.com/cli/latest/reference/ec2/create-customer-gateway.html - ✔✔What action is required to establish an Amazon VPC VPN Connection between an on-premise data center and an Amazon VPC Virtual Private Gateway? Empherial ports - ✔✔An instance running a webserver is launched in a VPC subnet. A security group and a NACL are configured to allow inbound port 80. What should be done to make web server accessible by everyone? 6 .. Three public subnets and Three private subnets - ✔✔You have been tasked with creating a VPC network topology for your company. The VPC network must support both Internet-facing applications and internally-facing applications accessed only over VPN. Both Internet-facing and internally-facing applications must be able to leverage at least three AZs for high availability. At a minimum, how many subnets must you create within your VPC to accommodate these requirements? a. Use Cloudfront to serve images b. Restrict access to those websites in the bucket policy c. Use glacier to store images d. Restrict access to those websites in the IAM policy e. Remove the public URL link from the object in S3 - ✔✔You have a photo selling website where you have a library of photos on S3. You noticed that there are some websites that are showing the link to your S3 photos. How do you restrict sites like these using your S3 photos link: A. Setting up a federation proxy or identity provider B. Using AWS Security Token Service to generate temporary tokens C. Tagging each folder in the bucket D. Configuring IAM role E. Setting up a matching IAM user for every user in your corporate directory that needs access to a folder in the bucket - ✔✔Your fortune 500 company has under taken a TCO analysis evaluating the use of Amazon S3 versus acquiring more hardware The outcome was that ail employees would be granted access to use Amazon S3 for storage of their personal documents. Which of the following will you need to consider so you can set up a solution that incorporates single sign-on from your corporate AD or LDAP directory and restricts access for each user to a designated user folder in a bucket? (Choose 3 Answers) A. SecurityGroupInboundRule:Protocol-TCP.PortRange-22,Source72.34.51.100/32 B.Network ACL Inbound Rule: Protocol - TDP, Port Range - 22, Source 72.34.51.100/32 - ✔✔Q: You are tasked with setting up a Linux bastion host for access to Amazon EC2 instances running in your VPC. Only clients connecting from the corporate external public IP address 72.34.51.100 should have SSH access to the host. Which option will meet the customer requirement? A. Amazon Glacier multipart upload B. AWS Storage Gateway C. VM Import/Export D. AWS Import/Export - ✔✔You are working with a customer who has 10 TB of archival data that they want to migrate to Amazon Glacier. The customer has a 1-Mbps connection to the Internet. Which service or feature provides the fastest method of getting the data into Amazon Glacier? A. Enable enhanced networking B. Use Amazon S3 multipart upload C. Leveraging Amazon CloudFront, use the HTTP POST method to reduce latency. D. Use Amazon Elastic Block Store Provisioned IOPs and use an Amazon EBS-optimized instance - ✔✔You have an application running on an Amazon Elastic Compute Cloud instance, that uploads 5 GB video objects to Amazon Simple Storage Service (S3). Video uploads are taking longer than expected, resulting in poor application performance. Which method will help improve performance of your application? A. Establish a hardware VPN over the internet between VPC-2 ana the on-premises network. B. Establish a hardware VPN over the internet between VPC-1 and the on-premises network. C. Establish a new AWS Direct Connect connection and private virtual interface in the same region as VPC-2. D. Establish a new AWS Direct Connect connection and private virtual interface in a different AWS region than VPC-1. [Show More]
Last updated: 3 years ago
Preview 1 out of 29 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

AWS bUNDLE. ALL EXAMINABLE QUESTIONS WITH ANSWERS. PASS EASY.
ALL AWS PAPERS. QUESTIONS WITH ANSWERS. RATED A
By Topmark 3 years ago
$32
28
Reviews( 0 )
$12.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Oct 13, 2022
Number of pages
29
Written in
All
Additional information
This document has been written for:
Uploaded
Oct 13, 2022
Downloads
0
Views
156