Information Technology > QUESTIONS & ANSWERS > WGU C839-Practice test Questions and Answers Already Passed (All)
WGU C839-Practice test Questions and Answers Already Passed
Document Content and Description Below
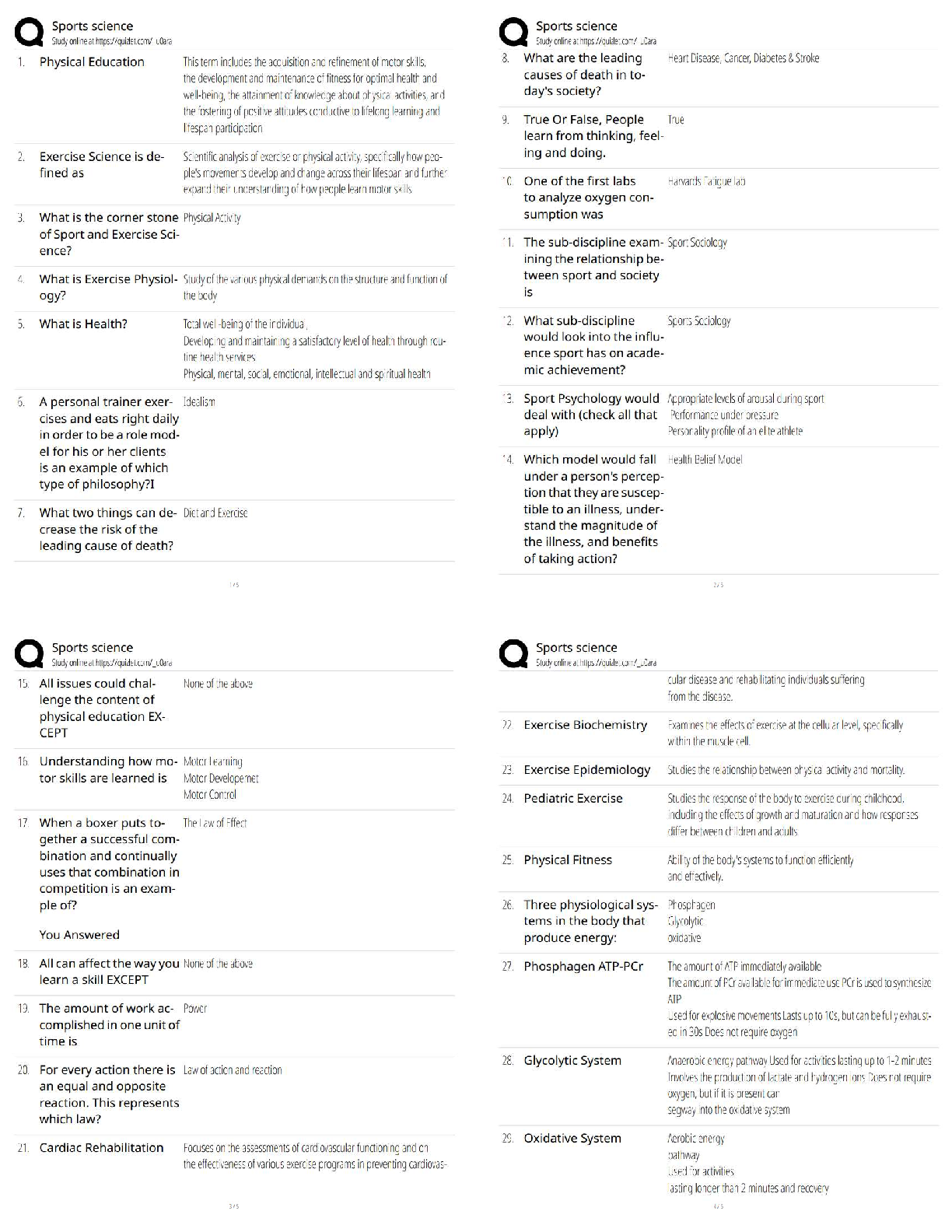
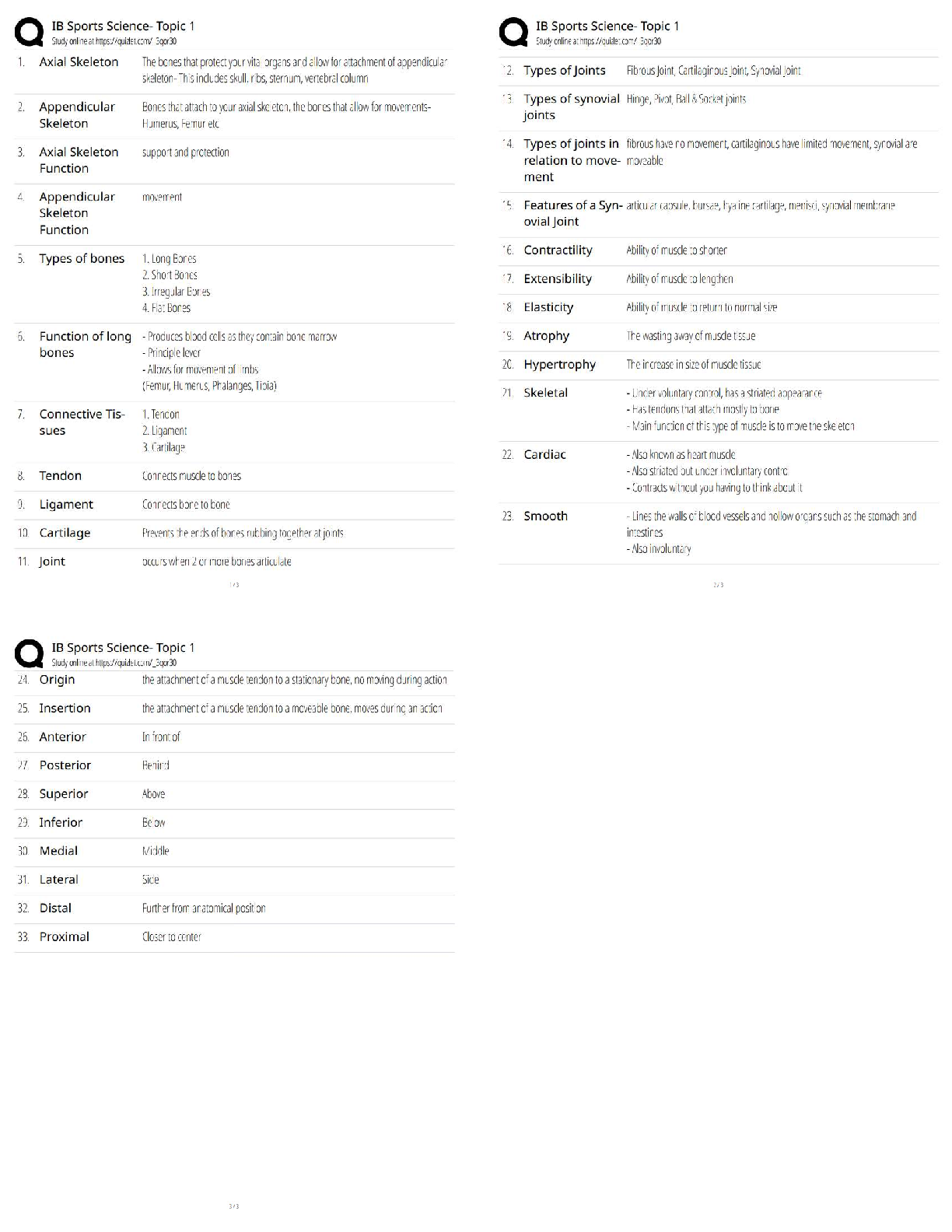
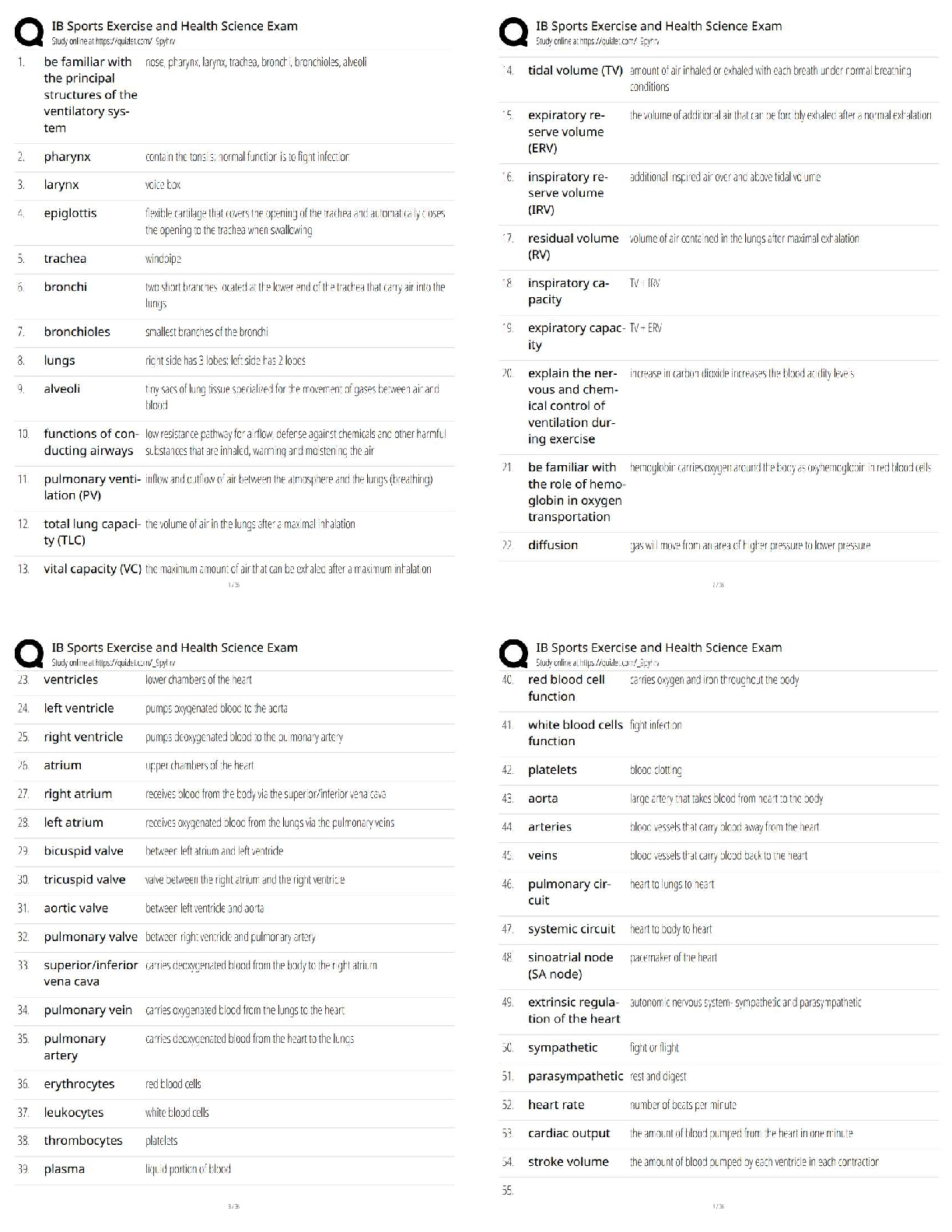
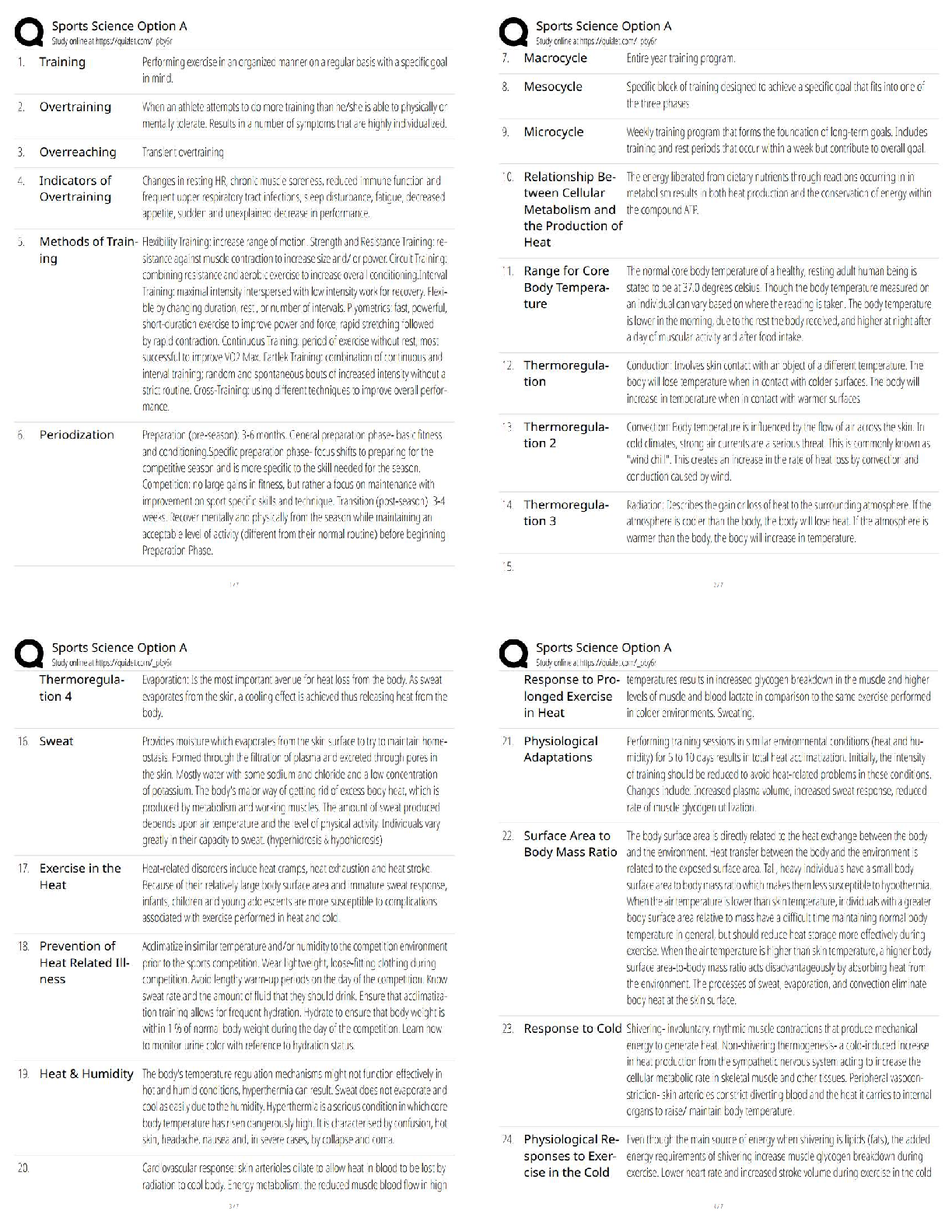
What term from the list below best describes a data concealment for covert communication that makes use of LSB replacement? -Crypanalysis -Stegnalysis -Steganography -Whitening ✔✔Steganograph ... y Which block cipher below uses a block size of 128 bits and key sizes up to 256 bits? -DES -Blowfish -TwoFish -Tiger ✔✔TwoFish Symmetric encryptionm is expressed mathematically as : - C=E(k,p) - P= E(k,c) - Me % n - y^2 = x^3 + Ax +B ✔✔C = E (k,p) Name all the Hashing algorithms ✔✔- Tiger - SHA256 - Fork256 - SHA1 - Gost [Show More]
Last updated: 3 years ago
Preview 1 out of 20 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$9.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Oct 12, 2022
Number of pages
20
Written in
All
Additional information
This document has been written for:
Uploaded
Oct 12, 2022
Downloads
0
Views
47



.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)
.png)