CIPP/US test Questions & Answers
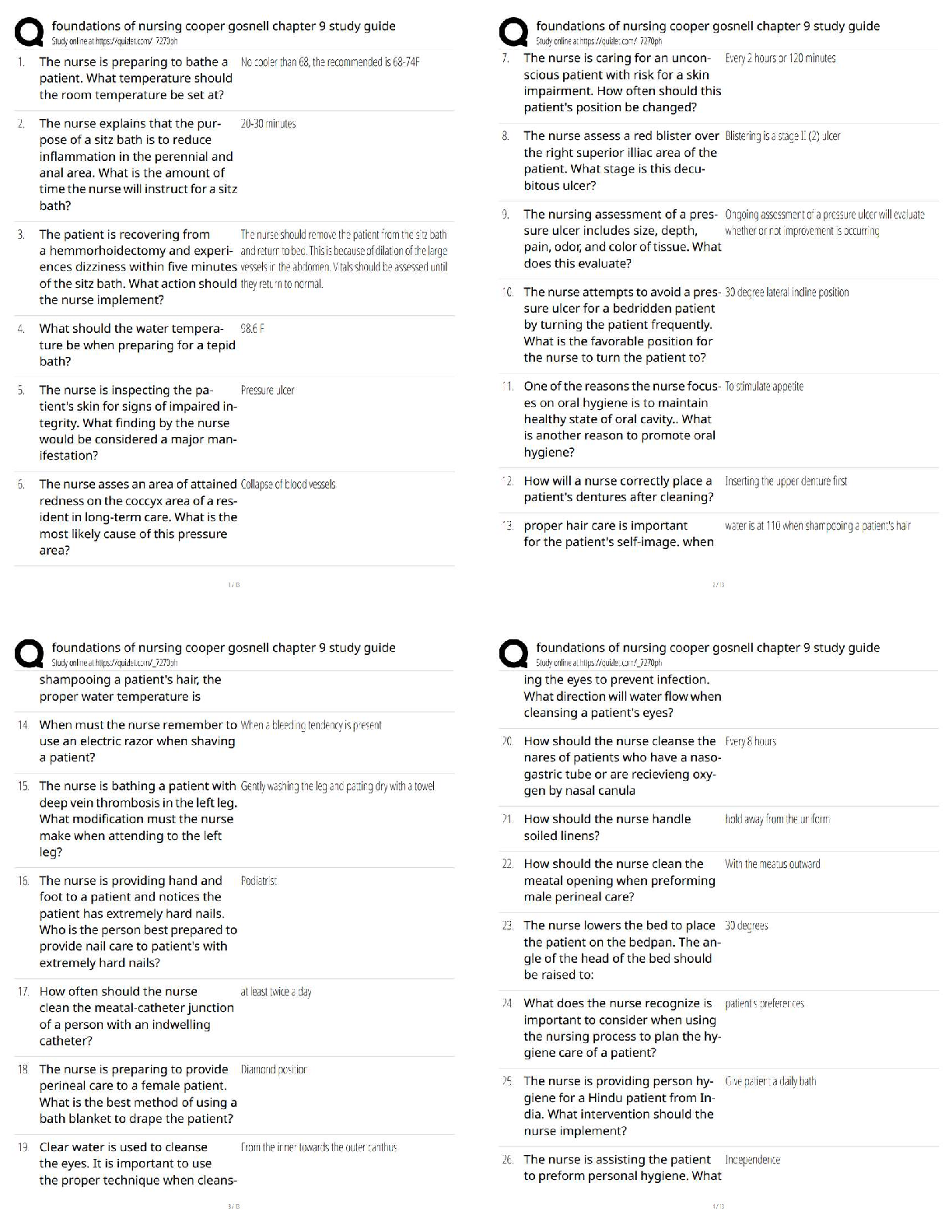
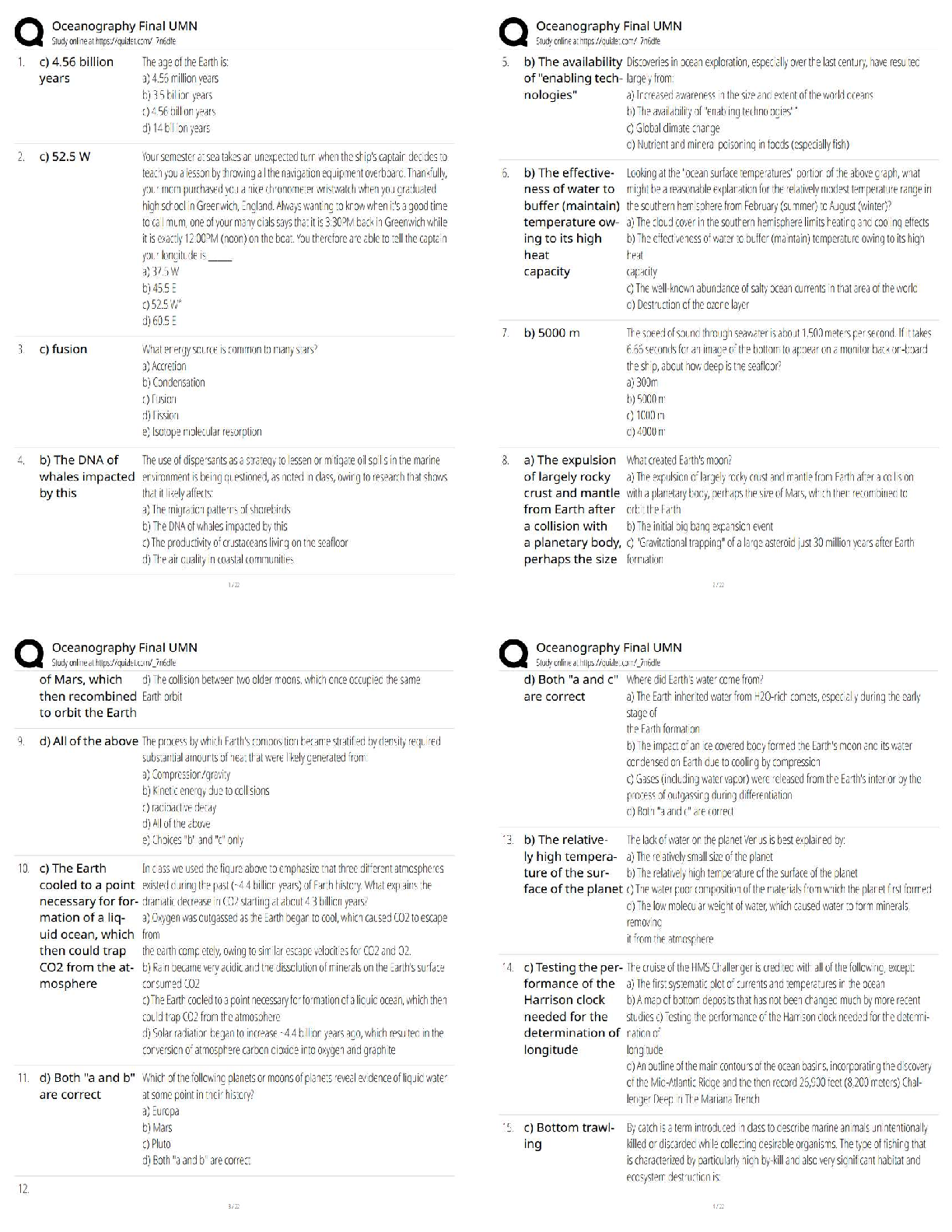
Data confidentiality, Data Availability, and what other attribute comprise the three key attributes
of information auditing and monitoring? - ANS - Data integrity.
What is a first-part
...
CIPP/US test Questions & Answers
Data confidentiality, Data Availability, and what other attribute comprise the three key attributes
of information auditing and monitoring? - ANS - Data integrity.
What is a first-party cookie? - ANS - A cookie that is set and read by the web server hosting the
website the user is visiting.
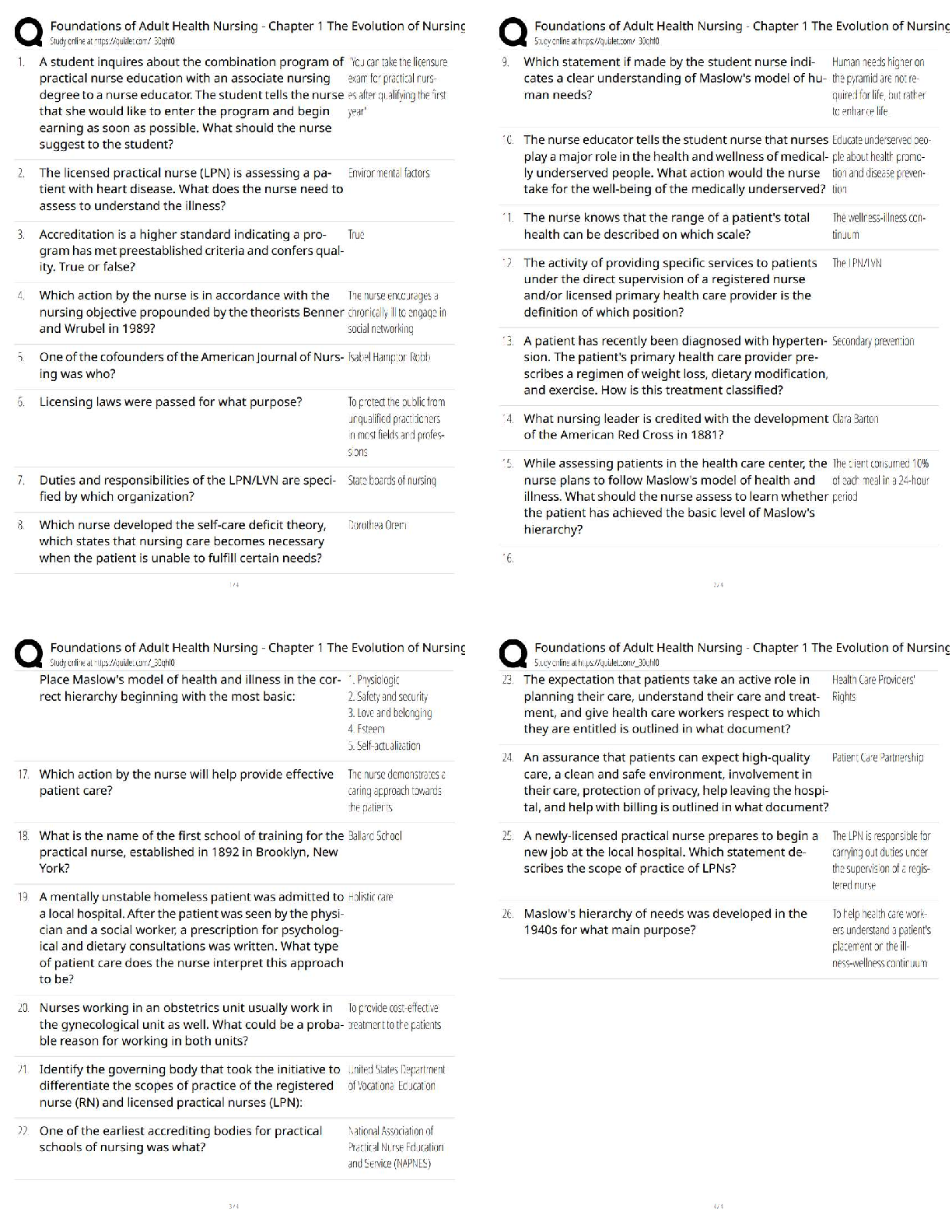
All of the following are considered acceptable methods for U.S.-based multinational
transportation companies to achieve compliance with the EU Data Protection Directive except -
ANS - Global consent.
Which condition must be met to satisfy the Right to Financial Privacy Act requirements for
disclosure of individual records by financial institutions? - ANS - The financial records are
reasonably described.
All of the following are considered acceptable reasons for sharing records of U.S. employees
with third parties without obtaining the consent of the employees except - ANS - test marketing
the company's new products.
According to the EU Data Protection Dirctive, what three elements are essential chracteristics of
consent? - ANS - A freely-given, specific and informed indication.
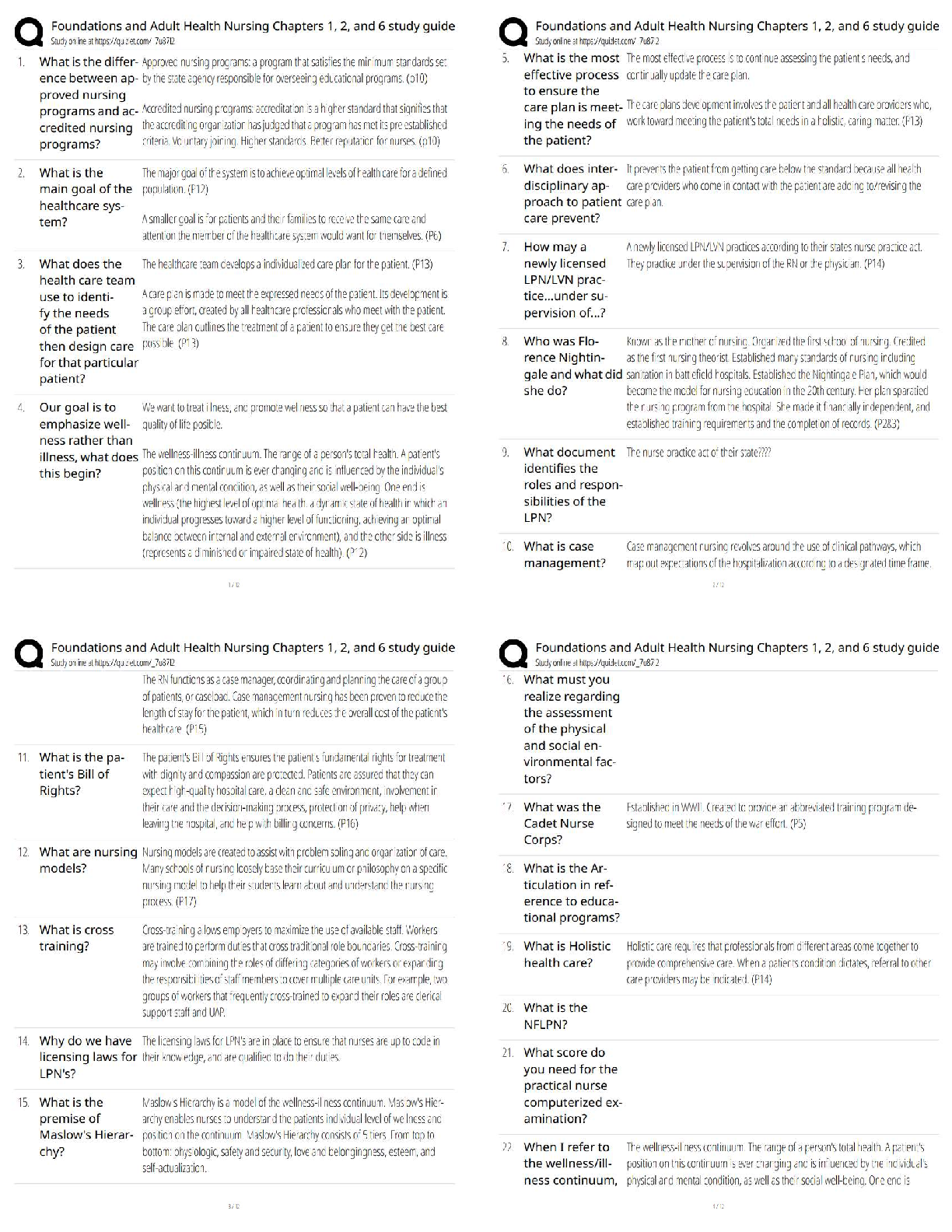
Two of the four categories of data protection and privacy law and practices are informational
privacy and - ANS - Territorial privacy
All of the following are valid privacy protection procedures when terminating an employee who
has access to sensitive personal information except - ANS - asking the employee to sign the
privacy policy immediately before conducting the exit interview.
Which of these elements may be considered personal information? - ANS - Information about a
company's leads or prospects.
Safe Harbor violations are enforced by the Federal Trade Commission and what other
government department? - ANS - The U.S Department of Transportation.
What changes did the FISA Amendments Act of 2008 make to the original Foreign Intelligence
Surveillance Act of 1978? - ANS - Legal authorization of some new surveillance practices.
What is the basis of common law? - ANS - Social customs and expectations.
Which country had opted NOT to join the European Economic Area but passed its own omnibus
privacy legislation? - ANS - Switzerland.
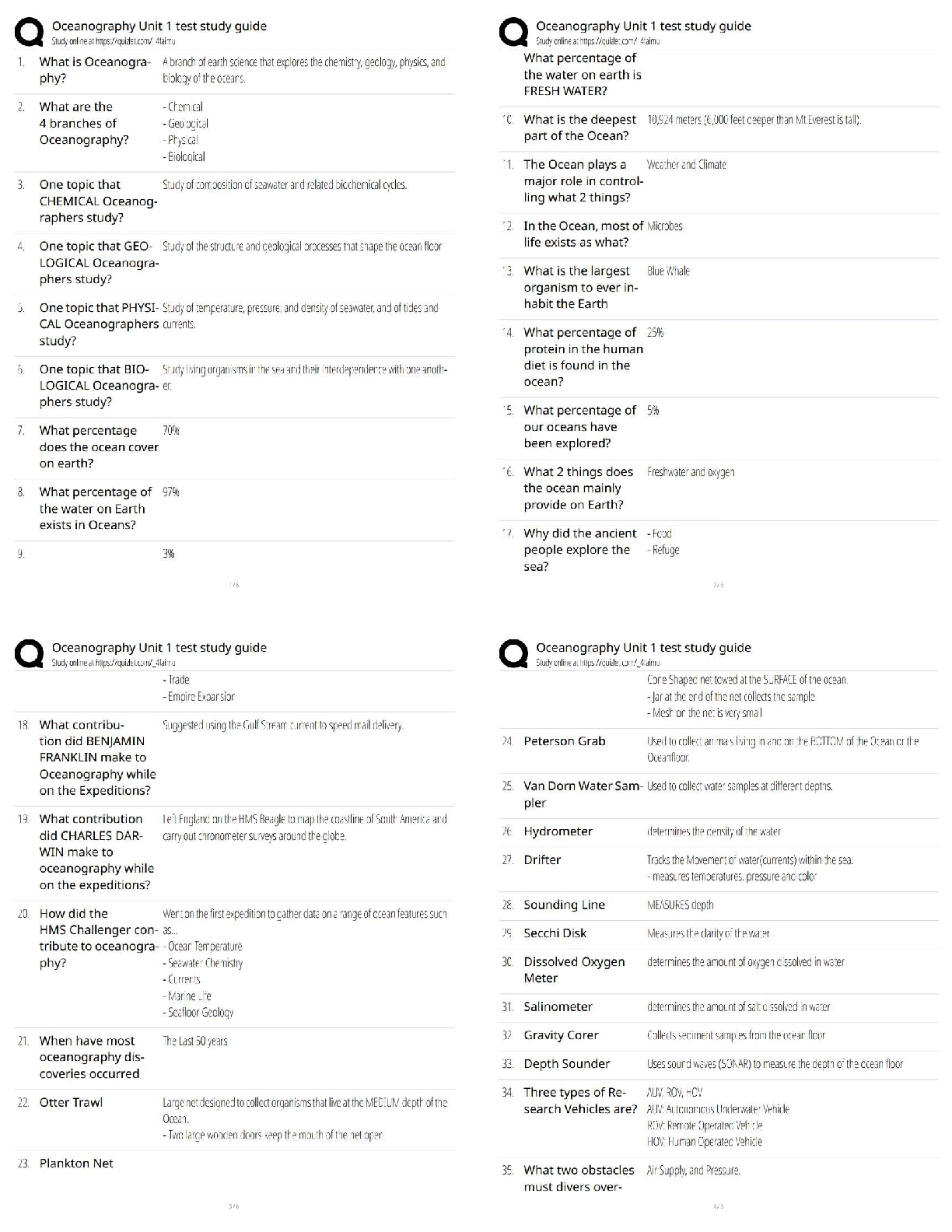
What is NOT a privacy risk raised by the use of smart grid technology? - ANS - Energy use
could increase due to continuous monitoring by energy companies.
What kind of information security control is an incident response procedure - ANS -
Administrative control.
Which characteristic completes the following list of the five essential characteristics of cloud
computing: on-demand self-service, broad network access, measured service, rapid elasticity and
- ANS - Resource pooling.
Effective security risk management balances the potential for loss with what cost? - ANS - The
cost of security protection and management.
Which model is used for privacy protection in the European Union? - ANS - Comprehensive
model.
Which of the following examples best illustrates the concept of "consumer report" for preemployment screening as defined under the U.S. Fair Credit Reporting Act - ANS - Driving
history obtained from an information aggregator.
In "phishing" which practices are used to collect personal information? - ANS - Fake e-mails
contain links to websites that only appear to be genuine and request personal information.
What is provided in Article 8 of the European Convention for the Protection of Human Rights
and Fundamental Freedoms? - ANS - The right to respect for an individual's privacy and family
life.
Which two actions are required under the Fair Credit Reporting Act in order for an employer to
obtain a consumer report on a job applicant? - ANS - Obtain applicant's written consent and
provide applicant with a copy of the credit report before taking an adverse action.
The use of personal information should follow what primary principle? - ANS - Personal
information should be limited to the purposes identified in the notice.
What is NOT a best practice for organizations managing a social media page? - ANS - Support
anonymous positive posts by employees on the organization's social media page to help offset
negative posts by customers.
All of the following are considered acceptable lines of questioning by U.S. employers to
applicants in the preemployment process except - ANS - questions on whether an applicant has
applied for or received worker's compensation.
For an employer to monitor or intercept electronic mail, which U.S. state requires daily
electronic notice? - ANS - Delaware
Use of a smart card would be identified as what type of safeguard - ANS - Two-factor
authentication.
Some states have security breach notification requirements. For those that do, what general
information must the breach-of-personally-identifiable-information notification letter to the
individual include? - ANS - A brief description of the incident, the type of information involved,
and a toll-free number for answers to questions.
Which statement is considered a best practice regarding information security governance? - ANS
- Ultimately, security is about people.
What is one reason consent decrees are posted publically on the FTC website? - ANS - To
provide guidance about what practices the FTC finds inappropriate.
What does the "red flags rule" require of financial institut
[Show More]
.png)
.png)


















.png)