Information Technology > QUESTIONS & ANSWERS > CySA Exam Questions with Answers, 100% Accurate answers. Graded A (All)
CySA Exam Questions with Answers, 100% Accurate answers. Graded A
Document Content and Description Below
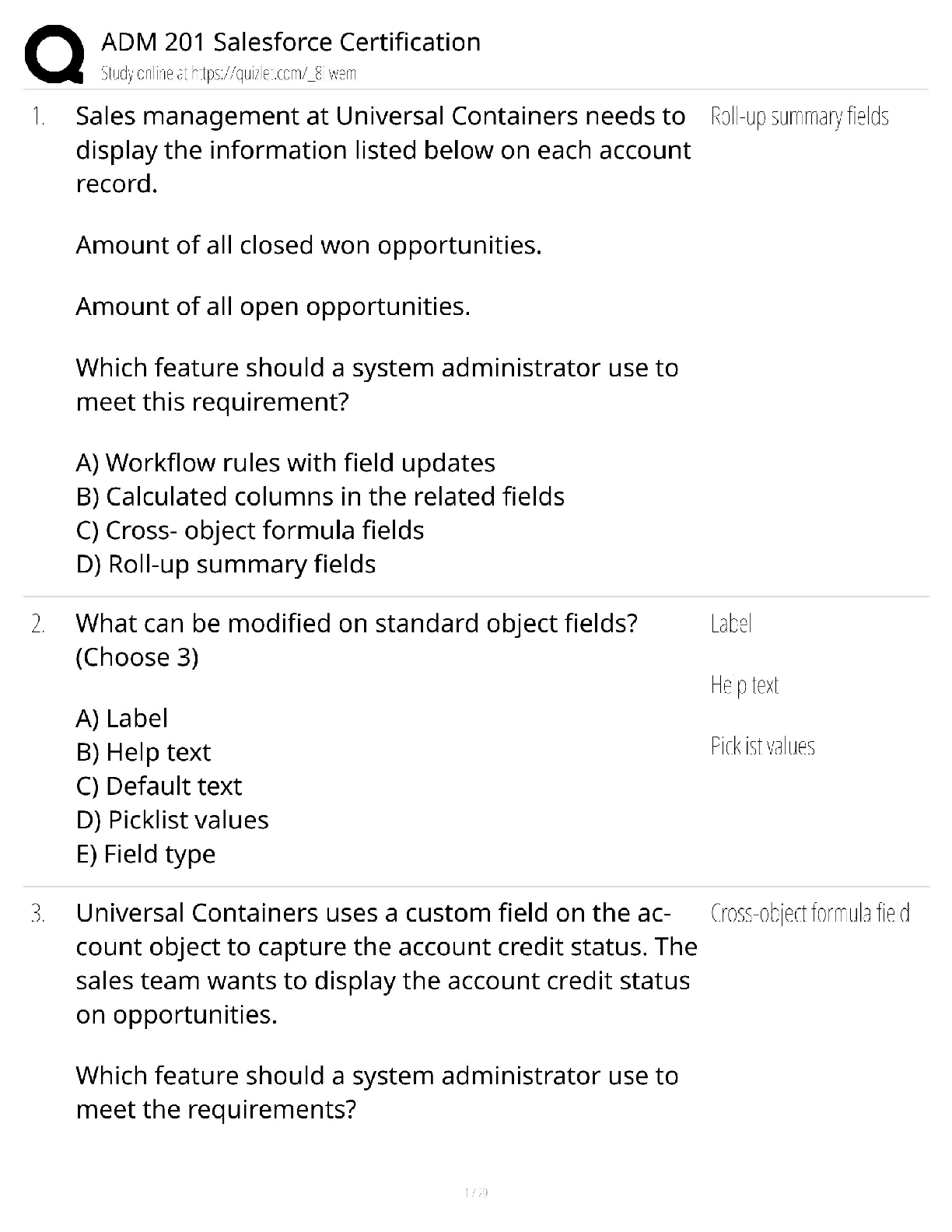
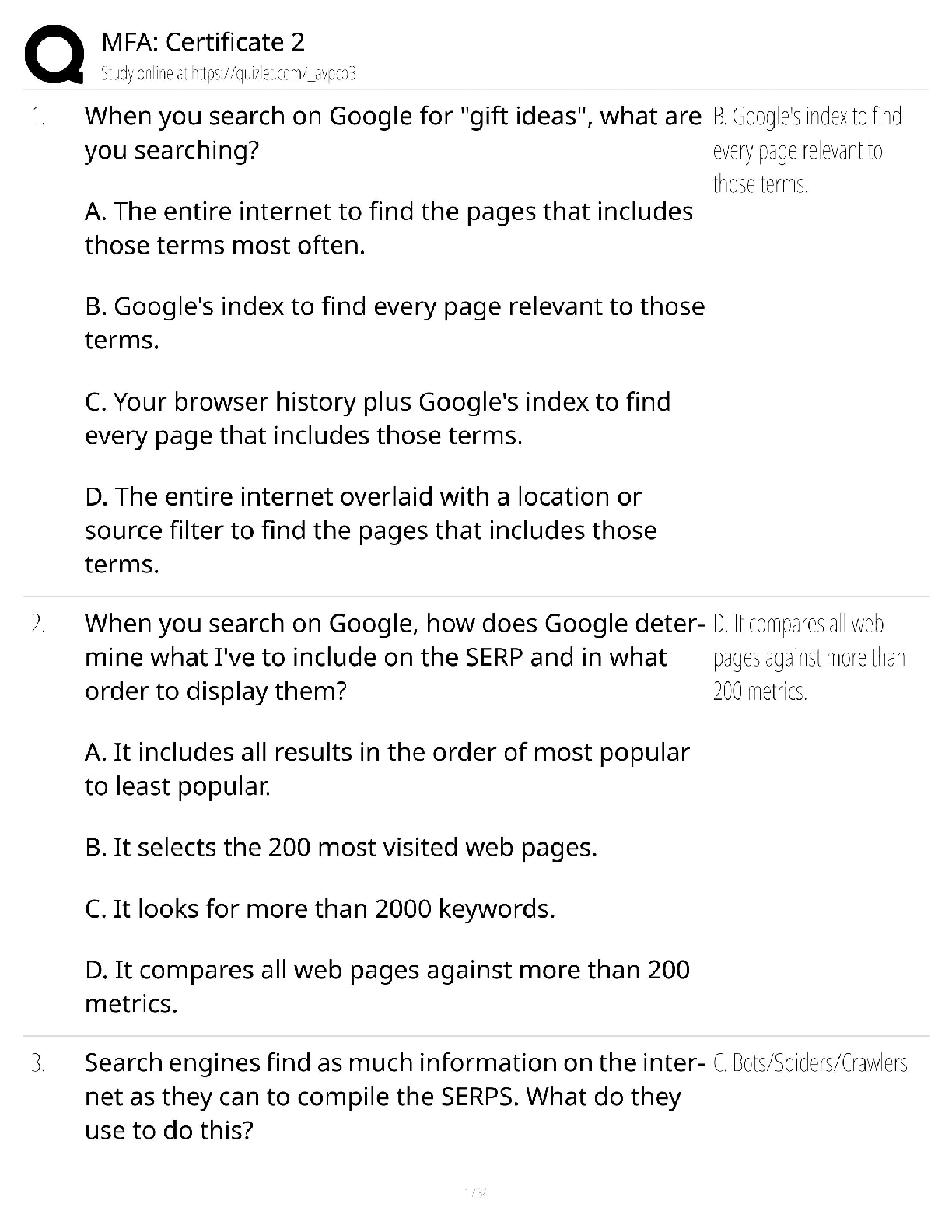
CySA Exam Questions with Answers Which one of the following objectives is not one of the three main objectives that information security professionals must achieve to protect their organizations aga ... inst cybersecurity threats? -Answer- nonrepudiation Tommy is assessing the security database servers in his datacenter and realizes that one of them is missing a critical Oracle security patch. What type of situation has Tommy detected? -Answer- vulnerability Ben is preparing to conduct a cybersecurity risk assessment for his organization. If he chooses to follow the standard process proposed by NIST, which one of the following steps would come first? -Answer- Identify threats Cindy is conducting a cybersecurity risk assessment and is considering the impact that a failure of her city's power grid might have on the organization. What type of threat is she considering? -Answer- environmental Which one of the following categories of threat requires that cybersecurity analysts consider the capability, intent and targeting of the threat source? -Answer- adversarial Vincent is responding to a security incident that compromised one of his organization's web servers. He does not believe that the attackers modified or stole any information, but they did disrupt access to the organization's website. What cybersecurity objective did this attack violate? -Answer- availability Which one of the following is an example of an operational security control? -Answerpenetration tests Encryption software, network firewalls, and antivirus software are all examples of _________________ security controls. -Answer- technical Paul recently completed a risk assessment and determined that his network was vulnerable to hackers connecting to open ports on servers. He implemented a network firewall to reduce the likelihood of a successful attack. What risk management strategy did Paul choose to pursue? -Answer- risk mitigation Robert's organization has a BYOD policy, and he would like to ensure that devices connected to the network under this policy have current antivirus software. What technology can best assist him with this goal? -Answer- network access control When performing 802.1x authentication, what protocol does the authenticator use to communicate with the authentication server? -Answer- RADIUSJuan is configuring a new device that will join his organization's wireless network. The wireless network uses 802.1x authentication. What type of agent must be running on the device for it to join this network? -Answer- 802.1x supplicant Rick is preparing a firewall rule that will allow network traffic from external systems to a web server running the HTTPS protocol. What TCP port must he allow to pass through the firewall? -Answer- 443 What type of firewall provides the greatest degree of contextual information and can include information about users and applications in its decision-making process? - Answer- Next Generation Firewalls Wayne is configuring a jump box server that system administrators will connect to from their laptops. Which port should definitely not be open on the jump box? -Answer- 23 Tom would like to deploy consistent security settings to all of his Windows settings simultaneously. What technology can he use to achieve this goal? -Answer- group policy object During what phase of a penetration test should the testers obtain written authorization to conduct the test? -Answer- planning Which step occurs first during the attack phase of a penetration test? -Answer- gaining access Barry is participating in a cybersecurity wargame exercise. His role is to attempt to break into adversary systems. What team is he on? -Answer- red Which one of the following techniques might be used to automatically detect and block malicious software that does not match known malware signatures? -Answersandboxing Kevin would like to implement a specialized firewall that can protect against SQL injection, cross-site scripting, and similar attacks. What technology should he choose? - Answer- WAF What method is used to replicate DNS information for DNS servers but is also a tempting exploit target for attackers? -Answer- zone transfers ____________ is a suite of DNS security specifications. -Answer- DNSSEC What flag does nmap use to enable operating system identification? -Answer- -o What command line tool can be used to determine the path that traffic takes to a remote system? -Answer- tracerouteTraceroute is a command-line tool that uses __________ to trace the route that a packet takes to a host. -Answer- ICMP What type of data can frequently be gathered from images taken on smartphones? - Answer- EXIF EXIF or Exchangeable Image Format data often includes ________________, allowing the images to be mapped and identified to a specific device or type of camera. -Answerlocation and camera data Which Cisco log level is the most critical? -Answer- 0 Which Cisco log level is used for debugging information and is at the bottom of the scale? -Answer- 7 During passive intelligence gathering, you are able to run netstat on a workstation located at your target's headquarters. What information would you not be able to find using netstat on a Windows system? -Answer- Active IPX connections Active TCP connections and the executables that are associated with them, and route table information are all available via ____________. -Answer- Netstat Which type of Windows log is most likely to contain information about a file being deleted? -Answer- security logs What organization manages the global IP address space? -Answer- IANA Before Ben sends a Word document, he uses the built-in Document Inspector to verify that the file does not contain hidden content. What is this process called? -Answermetadata purging What type of analysis is best suited to identify a previously unknown malware package operating on a compromised system? -Answer- heuristic analysis Which of the following is not a common DNS anti-harvesting technique? -Answerregistering manually CAPTCHAs, rate limiting, and blacklisting systems or networks that are gathering data are all common ___________ techniques. -Answer- anti-DNS harvesting The __________ flag indicates a zone transfer in both the dig and host utilities. - Answer- axfr Which of the following is not a reason that penetration testers often perform packet capture while conducting port and vulnerability scanning? -Answer- plausible deniabilityA ____________ is often used to document work, including the time that a given scan or process occurred, and it can also be used to provide additional data for further analysis. -Answer- packet capture What process uses information such as the way that a system's TCP stack responds to queries, what TCP options it supports, and the initial window size it uses? -Answer- OS detection What tool would you use to capture IP traffic information to provide flow and volume information about a network? -Answer- netflow __________ provides information about local connections, which applications have made them, and other useful local system information. -Answer- netstat What method used to replicate DNS information between DNS servers can also be used to gather large amounts of information about an organization's systems? -Answerzone transfer Selah believes that an organization she is penetration testing may have exposed information about their systems on their website in the past. What site might help her find an older copy of their website? -Answer- The Internet Archive During an information gathering exercise, Chris is asked to find out detailed personal information about his target's employees. What is frequently the best place to find this information? -Answer- social media Which lookup tool provides information about a domain's registrar and physical location? -Answer- Whois ____________ will provide IP address or hostname information. -Answer- nslookup __________ will provide IPv4 and IPv6 information as well as email service information. -Answer- host ___________ attempts to identify the path to a remote host as well as the systems along the route. -Answer- traceroute What federal law requires the use of vulnerability scanning on information systems operated by federal government agencies? -Answer- FISMA Gary is the system administrator for a federal agency and is responsible for a variety of information systems. Which systems must be covered by vulnerability scanning programs? -Answer- high-, moderate-, and low-impact systems What tool can administrators use to help identify the systems present on a network prior to conducting vulnerability scans? -Answer- asset inventoryThe asset inventory supplements automated tools with other information to detect systems present on a network. The asset inventory provides critical information for __________________. -Answer- vulnerability scans Tonya is configuring vulnerability scans for a system that is subject to the PCI DSS compliance standard. What is the minimum frequency with which she must conduct scans? -Answer- quarterly Which is not an example of a vulnerability scanning tool? -Answer- snort QualysGuard, Nessus, and OpenVAS are all examples of ___________________. - Answer- vulnerability scanning tools Bethany is the vulnerability management specialist for a large retail organization. She completed her last PCI DSS compliance scan in March. In April, the organization upgraded their point-of-sale system, and Bethany is preparing to conduct new scans. When must she complete the new scan? -Answer- immediately Renee is configuring her vulnerability management solution to perform credentialed scans of servers on her network. What type of account should she provide to the scanners? -Answer- read only Jason is writing a report about a potential security vulnerability in a software product and wishes to use standardized product names to ensure that other security analysts understand the report. Which SCAP component can Jason turn to for assistance? - Answer- common product enumeration Common Product Enumeration (CPE) is a ________________ component that provides standardized nomenclature for product names and versions. -Answer- SCAP Bill would like to run an internal vulnerability scan on a system for PCI DSS compliance purposes. Who is authorized to complete one of these scans? -Answer- any qualified individual Which type of organization is the most likely to face a regulatory requirement to conduct vulnerability scans? -Answer- government agency What minimum level of impact must a system have under FISMA before the organization is required to determine what information about the system is discoverable by adversaries? -Answer- high What term describes an organization's willingness to tolerate risk in their computing environment? -Answer- risk appetiteIf an organization is extremely ____________, it may choose to conduct scans more frequently to minimize the amount of time between when a vulnerability comes into existence and when it is detected by a scan. -Answer- risk averse Which one of the following factors is least likely to impact vulnerability scanning schedules? -Answer- staff availability Barry placed all of his organization's credit card processing systems on an isolated network dedicated to card processing. He has implemented appropriate segmentation controls to limit the scope of PCI DSS to those systems through the use of VLANs and firewalls. When Barry goes to conduct vulnerability scans for PCI DSS compliance purposes, what systems must he scan? -Answer- systems on the isolated network Ryan is planning to conduct a vulnerability scan of a business critical system using dangerous plug-ins. What would be the best approach for the critical scan? -Answerrun the scan in a test environment Which one of the following activities is not part of the vulnerability management life cycle? -Answer- reporting Detection, remediation, and testing are the three life-cycle phases for ____________. - Answer- vulnerability management What approach to vulnerability scanning incorporates information from agents running on the target servers? -Answer- continuous monitoring Continuous monitoring incorporates data from agent-based approaches to vulnerability detection and reports security-related configuration changes to the _______________ platform as soon as they occur, providing the ability to analyze those changes for potential vulnerabilities. -Answer- vulnerability management Brian is seeking to determine the appropriate impact categorization for a federal information system as he plans the vulnerability scanning controls for that system. After consulting management, he discovers that the system contains information that, if disclosed improperly, would have a serious adverse impact on the organization. How should this system be categorized? -Answer- moderate impact Jessica is reading reports from vulnerability scans run by a different part of her organization using different products. She is responsible for assigning remediation resources and is having difficulty prioritizing issues from different sources. What SCAP component can help Jessica with this task? -Answer- CVSS The Common Vulnerability Scoring Systems (CVSS) provides a standardized approach for measuring and describing the severity of ___________. -Answer- security vulnerabilitiesSarah would like to run an external vulnerability scan on a system for PCI DSS compliance purposes. Who is authorized to complete one of the scans? -Answer- an approved scanning vendor Tom is reviewing a vulnerability scan report and finds that one of the servers on his network suffers from an internal IP address disclosure vulnerability. What protocol is likely in use on this network that resulted in this vulnerability? -Answer- Network Access Translation (NAT) A network uses Network Access Translation (NAT) to map public and private IP addresses but a ______________ inadvertently discloses its private IP address to remote systems. -Answer- server Which one of the CVSS metrics would contain information about the number of times that an attacker must successfully authenticate to execute an attack? -AnswerAuthentication (Au) The Authentication metric describes the authentication hurdles an attacker would need to clear to ___________ a vulnerability. -Answer- exploit Which one of the following values for the CVSS access complexity metric would indicate that the specified attack is simplest to exploit? -Answer- low A _____________ access complexity of "low" indicates that exploiting the vulnerability does not require any specialized conditions. -Answer- CVSS Which one of the following values for the confidentiality, integrity, or availability CVSS metric would indicate the potential for total compromise of a system? -Answer- complete (C) What is the most recent version of CVSS that is currently available? -Answer- 3.0 Which one of the following metrics is not included in the calculation of CVSS exploitability score? -Answer- vulnerability age The __________________ is computed using the access vector, access complexity, and authentication metrics. -Answer- CVSS exploitability score Kevin recently identified a new security vulnerability and computed its CVSS base score as 6.5. Which risk would this vulnerability fall into? -Answer- high __________________ with a CVSS score higher than 6.0 but less than 10.0 fall into the high risk category. -Answer- VulnerabilitiesTara recently analyzed the results of a vulnerability scan report and found that a vulnerability reported by the scanner did not exist because the system was actually patched as specified. What type of error occurred. -Answer- false positive Which one of the following is not a common source of information that may be correlated with vulnerability scan results? -Answer- database tables Logs, SIEM reports, and configuration management systems are likely to contain information relevant to assessing a __________________. -Answer- vulnerability scan report Which one of the following operating systems' support has be [Show More]
Last updated: 3 years ago
Preview 1 out of 46 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$8.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 23, 2022
Number of pages
46
Written in
All
Seller

Reviews Received
Additional information
This document has been written for:
Uploaded
Sep 23, 2022
Downloads
0
Views
159