Information Technology > QUESTIONS & ANSWERS > MTA 98-366 Exam Questions with accurate answers. 100% predictor questions. Rated A+ (All)
MTA 98-366 Exam Questions with accurate answers. 100% predictor questions. Rated A+
Document Content and Description Below
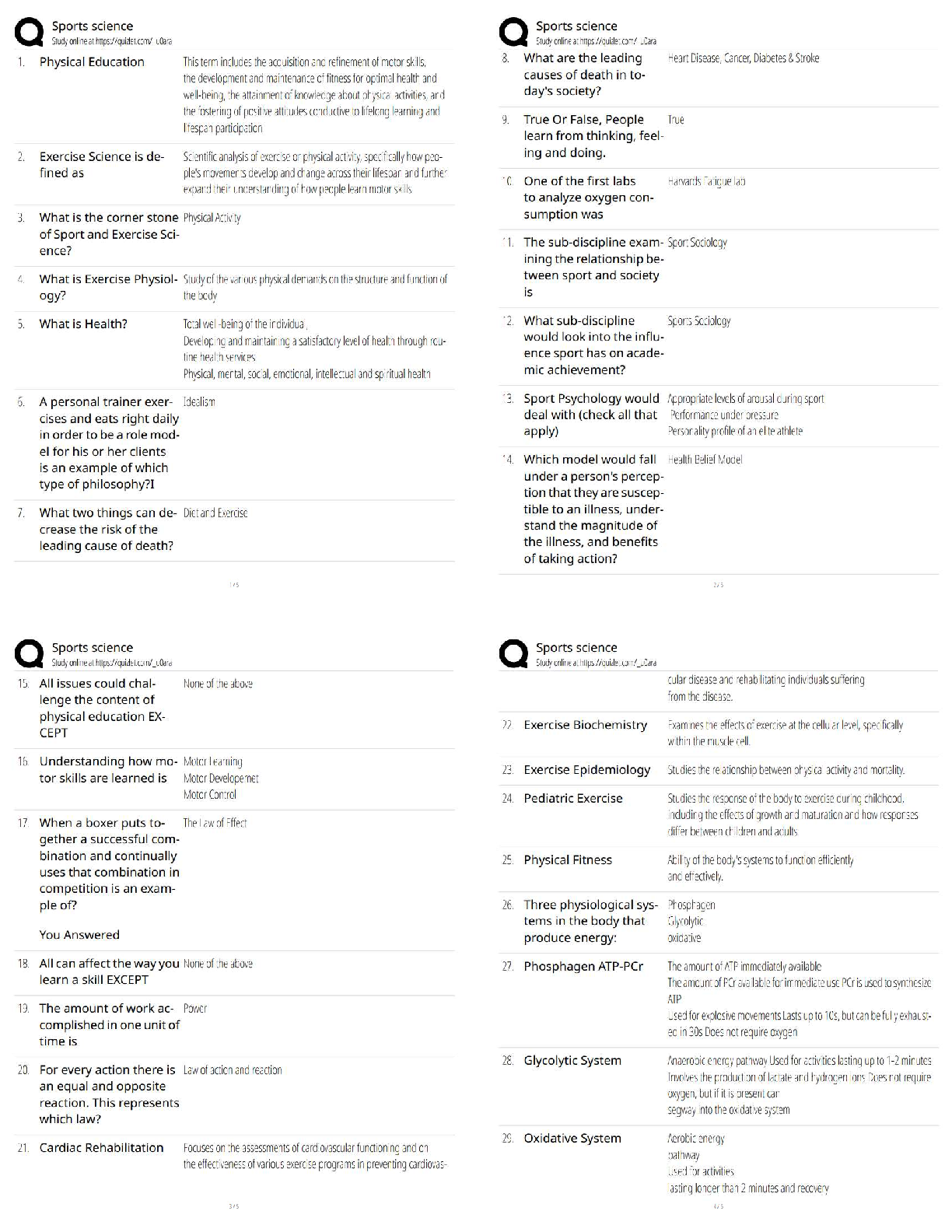
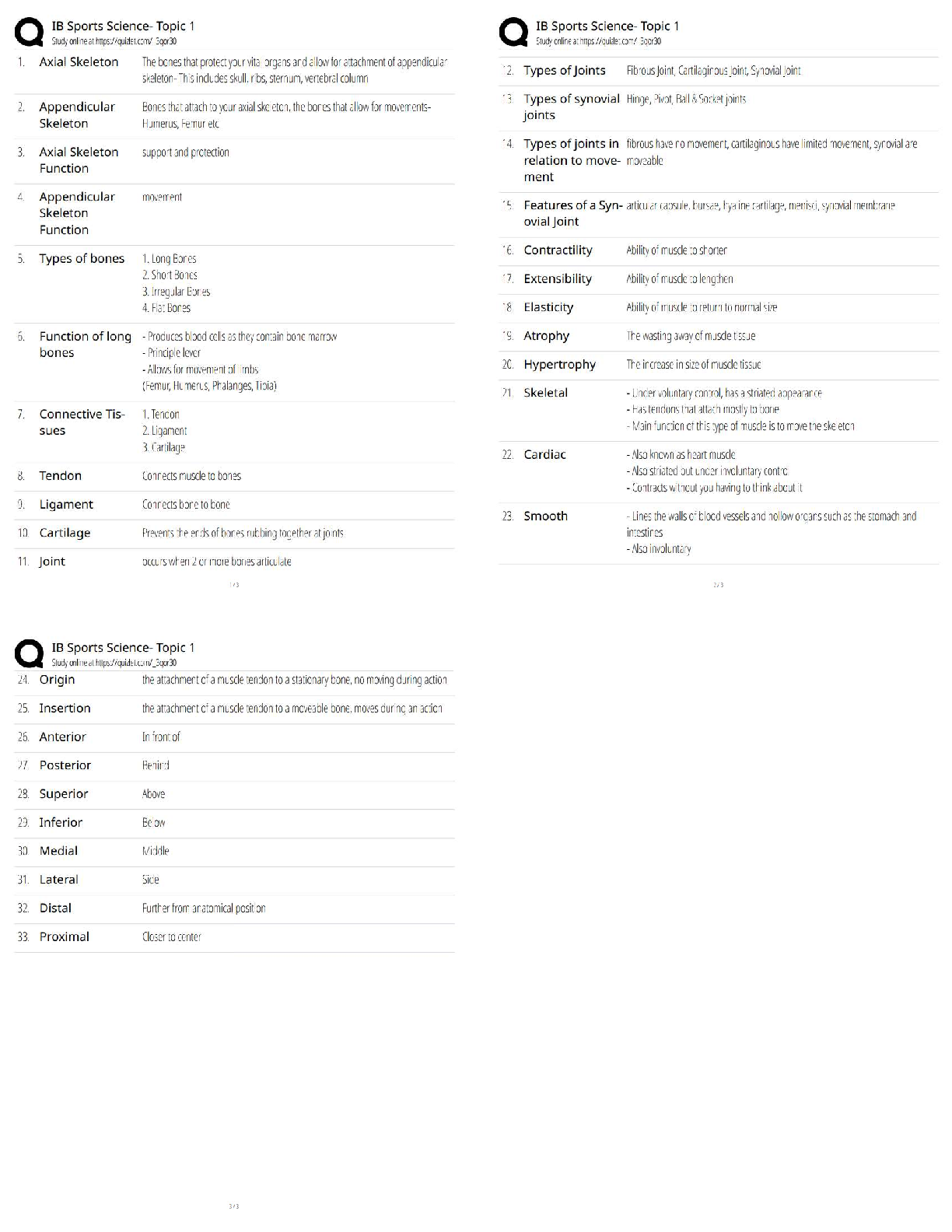
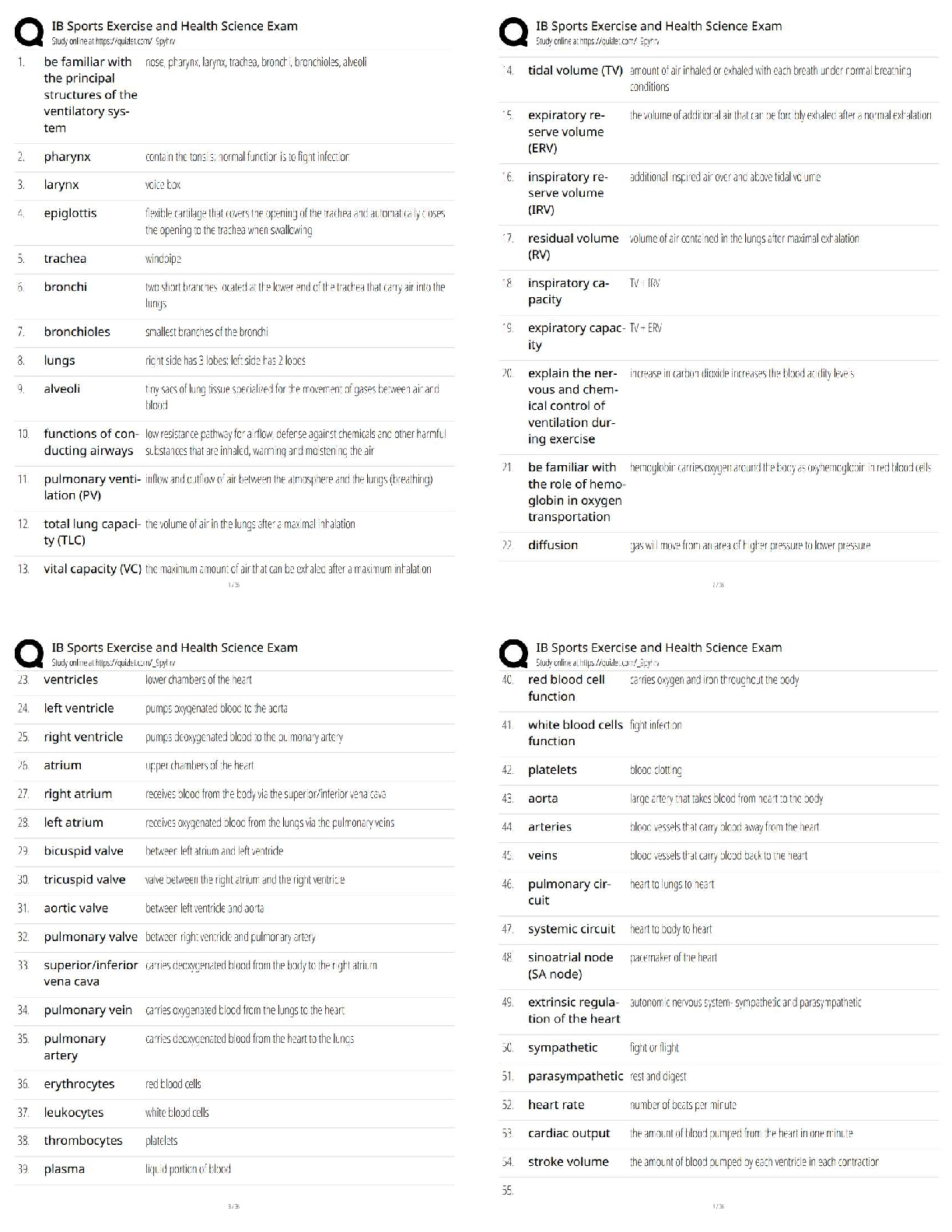
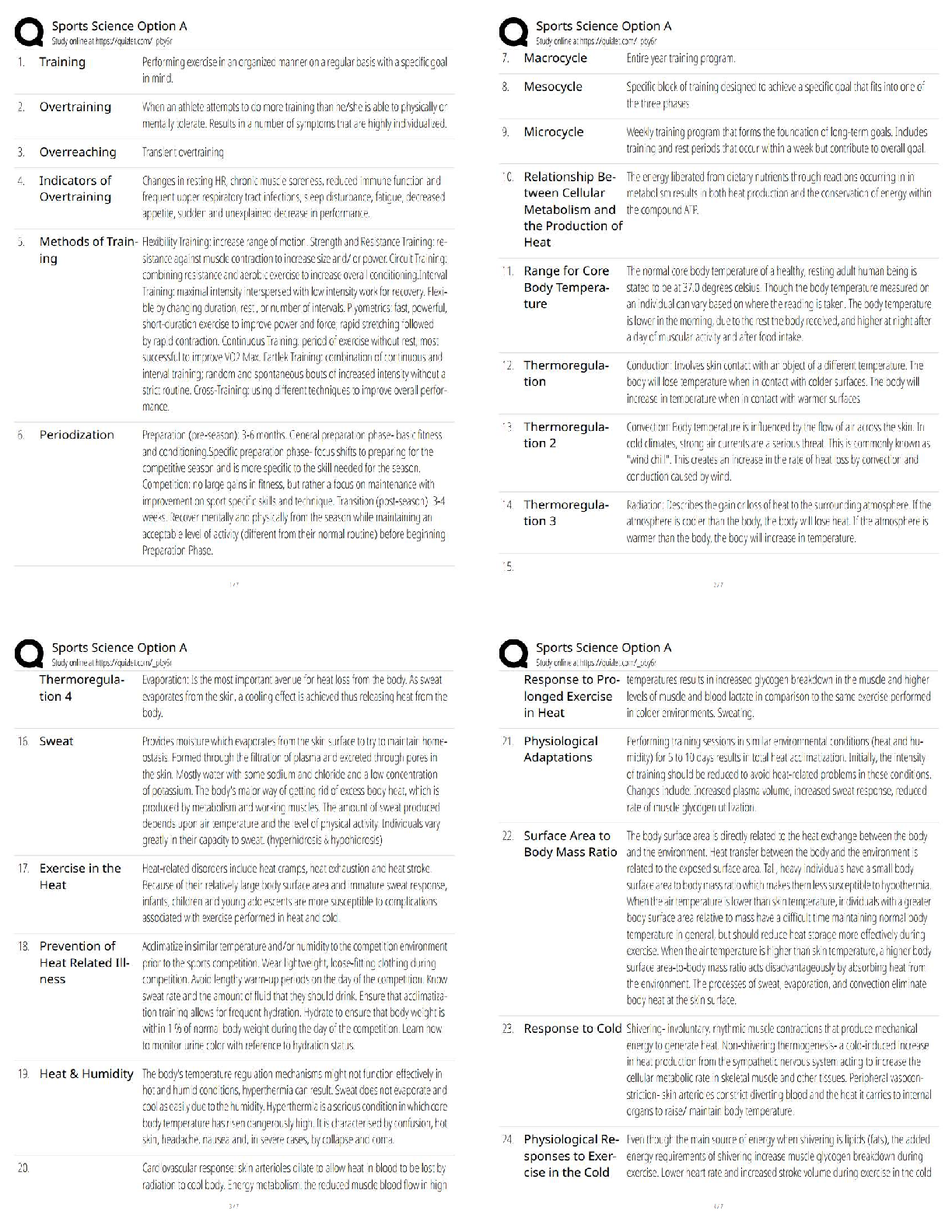
MTA 98-366 Exam What is the most common central device used today to connect computers to a network? A. Hub B. Switch C. SOHO Router D. VPN router - ✔✔B. Switch What is the most common adap ... ter or connector used to connect a computer to a wired network? A. RG6 B. RG45 C. RJ45 D. RJ8 - ✔✔C. RJ45 Which of the following does a switch use for increased performance? A. simplex B. half duplex C. Full duplex D. sliding duplex - ✔✔C. Full Duplex What do you use to isolate a group of computers within your organization? A. WLAN B. WAN C. VLAN D. Internet - ✔✔C. VLAN (Virtual Local Area Network What do you use to create VLANs? A. router B. switch C. firewall D. proxy server - ✔✔B. Switch What zone is used to publish external websites for an organization? A. intranet B. exanet C. internetwork D. DMZ - ✔✔D. DMZ (Demilitarized Zone)Which topology is the most redundant and the most expensive? A. Star B. Ring C. Mesh D. Bus - ✔✔C. Mesh What standard describes CSMA/CD? A. 801.2 B. 802.3 C. 802.5 D. 802.11 - ✔✔B. 802.3 What mechanism do wireless networks use to access the network? A. CSMA/CD B. CSMA/CA C. token passing D. polling - ✔✔B. CSMA/CA (Carrier Sense Multiple Access with Collision Avoidance) What model promises the most processing power? A. centralized computing B. distributive computing C. switching computing D. dumb computing - ✔✔B. Distributive computing Which model users a central database for authentication? A. peer-to-peer B. workgroup C. Client/server D. distributive - ✔✔C. client/server What type of server does Active Director run on? A. File server B. Print server C. database server D. network controller - ✔✔D. network controller Which model has each host have their own security database? A. peer-to-peerB. client/server C.distributive D. sliding - ✔✔A. peer-to-peer What type of communication is sent to a single designated host? A. unicast B. broadcast C. multicast D. anycast - ✔✔A. unicast What is used to uniquely identify a host on a TCP/IP network? A. IP address B. MAC address C. bit pattern D. router name - ✔✔A. IP address A_______ is a single computer or device that connects to a TCP/IP network. A. Host B. Node C. Access Point D. Laptop - ✔✔A and/or B. Host and Node are the same thing. What is the central device used in a wireless LAN? A. Wireless Access Point B. CS/CDM Connector C. Wireless Switch D. MDU - ✔✔A. Wireless Access Point What command do you use to test the TCP/IP stack on a computer? A. Ping localhost B. Ping 127.0.0.1 C. Ping Loopback D. ipconfig /renew - ✔✔A, B, and/or C. All three commands will ping the local network adapter You need to divide a network into the three subnets. Which device should you use? A. Router B. Hub C. SegmenterD. Bridge - ✔✔A. router Connecting to a private Network address from a public network requires: A. Dynamic Host Configuration Protocal (DHCP) B. Network Access Protection (NAP) C. Dynamic Domain Name System (DDNS) D. Network Address Translation (NAT) - ✔✔D. Network Address Translation (NAT) What model is used to describe how data communication occurs between hosts? A. server-centric model B. workgroup model C. peer-to-peer model D. OSI reference Model - ✔✔D. OSI Reference Model (Open Systems Interconnection model ) Which layer in the OSI model to MAC addresses and switches use? A. Physical B. Data Link C. Network D. Transport - ✔✔B. Data Link Which layer in the OSI model covers routing between networks? A. Physical B. Data Link C. Network D. Transport - ✔✔C. Network Which layer in the OSI model is used to verify that data was delivered without error? A. Physical B. Data Llink C. Network D. Transport - ✔✔C. Network Which layer of the OSI model covers HTTP, FTP, and RDC? A. Physical B. Sesion C. Application D. Presentation - ✔✔C. ApplicationWhich layer of the OSI model is used to create a connection so that a host can transfer files? A. Physical B. Session C. Application D. Presentation - ✔✔B. Session Which layer of the OSI model inclused VLANs? A. Physical B. Data Link C. Network D. Transport - ✔✔B. Data Link Which protocol do you use as the transport protocol for a video application? A. TCP B. UDP C. FTP D. RDC - ✔✔B. UDP Which port categories include inpoint ports of HTTP, HTTPS, FTP, and DNS? A. well-known ports B. registered ports C. dynamic ports D. private ports - ✔✔A. Well-known ports Which layer in the OSI model is responsible for logging on and off? A. Physical B. Session C. Application D. Presentation - ✔✔B. Session What layer in the OSI model is used to encrypt data? A. Physical B. Session C. Application D. Presentation - ✔✔D. Presentation Which layer in the OSI model includes the cable and network adapters? A. PhysicalB. Session C. Application D. Presentation - ✔✔A. Physical How many layers does the TCP/IP model have? A. 3 B. 4 C. 6 D. 7 - ✔✔B. 4 Which layer in the OSI model is included in the TCP/IP model? A. Physical B. Data Link C. Transport D. Application - ✔✔C. Transport Which protocol is used to translate IP addresses to MAC addresses? A. RARP B. ARP C. DNS D. WINS - ✔✔B. ARP (Address Resolution Protocol) What parts are defined above 49,152? A. well-known ports B. registered ports C. dynamic ports D. sliding ports - ✔✔C. dynamic ports A layer 3 switch is similar to a _____. A. Router B. Repeater C. Hub D. Patch Panel - ✔✔A. Router TCP/IP and IPX/SPX are know as _________stacks. A. protocols B. Services C. Layers D. Lenses - ✔✔A. ProtocolsWhat is the advantage of UDP over TCP? A. Less overhead - Faster performance B. Older - Larger pool of compatible hardware C. TCP is not IPv6 compatible, UDP is D. UDP can operate in layer 4 - ✔✔A. Less overhead - faster performance What the the seven layers found in the OSI model, in order? A. Physical - Data Link - Network - Transport - Session - Presentation - Application B. Physical - Data Link - Network - Transport - Session - Application - Presentation C. Physical - Data Link - Transport - Network - Session - Application - Presentation D. Physical - Data Link - Transport - Session - Presentation - Application - ✔✔A. Physical - Data Link - Network - Transport - Session - Presentation - Application What is the maximum speed supported by 802.11b? A. 1 Mbps B. 10 Mbps C. 11 Mbps D. 54 Mbps - ✔✔C. 11 Mbps One reason to incorporate VLANs in the network is to: A. Reduce the number of broadcast domains B. Increase the number of available Media Access Control (MAC) Addresses C. Increase the number of available IP addresses D. Reduce the number of nodes in a broadcast domain - ✔✔D. Reduce the number of nodes in a broadcast domain. What is the minimum cabling requirement for 100BaseTx network? A. Category 3. UTP cable B. Category 5 UTP cable C. Category 6 UTP cable D. Multimode fiber cable - ✔✔B. Category 5 UTP cable A router's static route is set by the: A. Next upstream router B. Routing Protocol C. Adjacent Network D. Network Administrator - ✔✔D. Network Administrator What type of record does DNS use to find a mail service?A. Host (A) DNS record B. Canonical (CNAME) DNS record C.Service (SRV) DNS record D. Mail Exchanger (MX) DNS record - ✔✔D. Mail Exchanger (MX) DNS record How many bits are there in an Internet Protocol version 6 (IPv6) address? A. 32 B. 64 C. 128 D. 256 - ✔✔C. 128 bits In which OSI layer does routing occur? A. Physical B. Network C. Data Link D. Transport - ✔✔B. Network The query protocol used to locate resources on a network is: A. Tracert B. Telnet C. Lightweight Directory Access Protocol (LDAP) D. User Datagram Protocol (UDP) - ✔✔C. Lightweight Directory Access Protocol (LDAP) What is the most common cable used today? A. UTP B. STP C. Coaxial D. Fiber - ✔✔A. UTP (Unshielded Twisted Pair) If you are making a crossover cable and one end is 568A, what should the other end be? A. 568A B. 568B C. 568C D. BOGB - ✔✔B. 568B If you want to connect a computer directly to another computer without using a switch, you use a _______.A. straight-through cable B. crossover cable C. laplink cable D. rollover cable - ✔✔b. Crossover cable You need to connect a twisted pair cable to the back of a patch panel. What tool should you use? A. punch-down tool B. zip tool C. wire wedge D. soldering iron - ✔✔A. punch-down tool What is the minimum category of twisted-pair cable you need to support 100 Mbps? A. Category 3 B. Category 5 C. Category 5e D. Category 6 - ✔✔B. Category 5 When you pick up your wireless phone, your computer drops network connectivity. What could be the cause of the problem? A. EMI B. RFI C. network adapter failure D. cable failure - ✔✔B. RFI (Radio Frequency Interference) You are setting up a network within a warehouse using Cat 6 UTP. However, parts of the network are down because of the heavy machinery used. What cable type should you use? A. STP B. Coaxial C. fiber D. Plenum-rated - ✔✔C. fiber What do you call it when electrical signals jump to another set of wires? A. EMI B. RFI C. crosstalk D. jump it is - ✔✔C. Crosstalk What type of cable should be used as part of a fire code for a building?A. STP B. PVC C. Heat protected D. plenum-rated - ✔✔D. Plenum rated Which of the following is not a fiber connector? A. FC B. LC C. RJ45 D. MT-RJ - ✔✔C. RJ45 [Show More]
Last updated: 3 years ago
Preview 1 out of 29 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$8.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 10, 2022
Number of pages
29
Written in
All
Seller

Reviews Received
Additional information
This document has been written for:
Uploaded
Sep 10, 2022
Downloads
0
Views
153