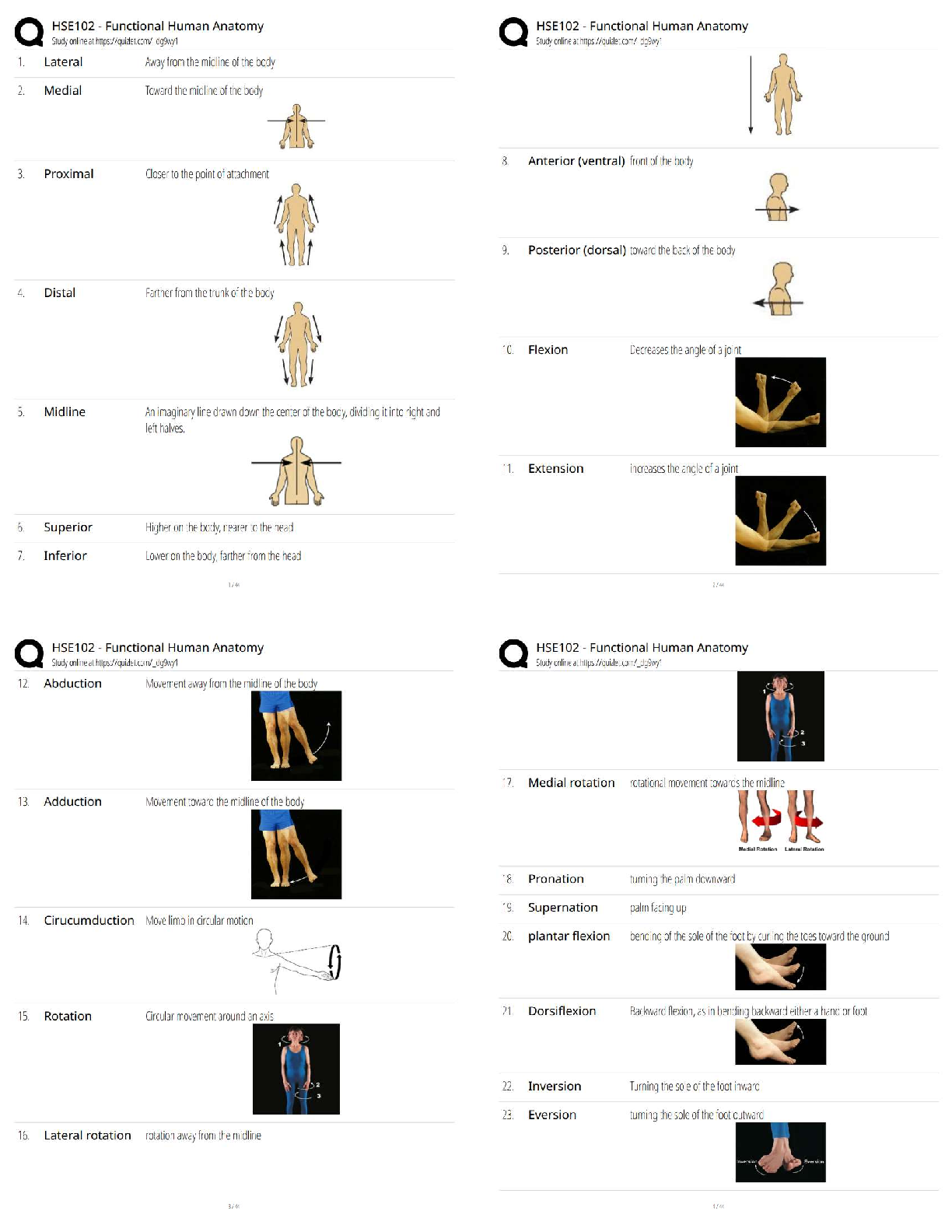
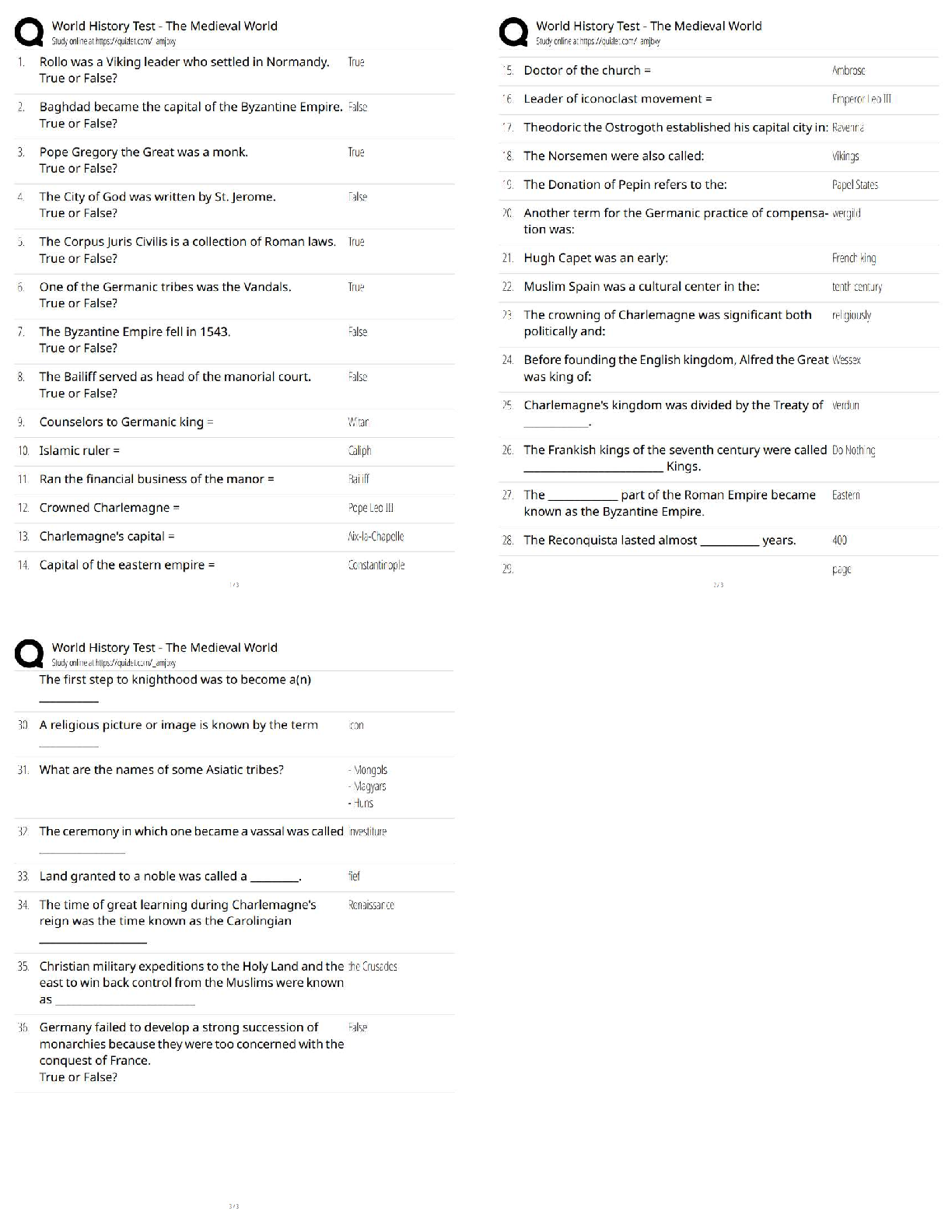
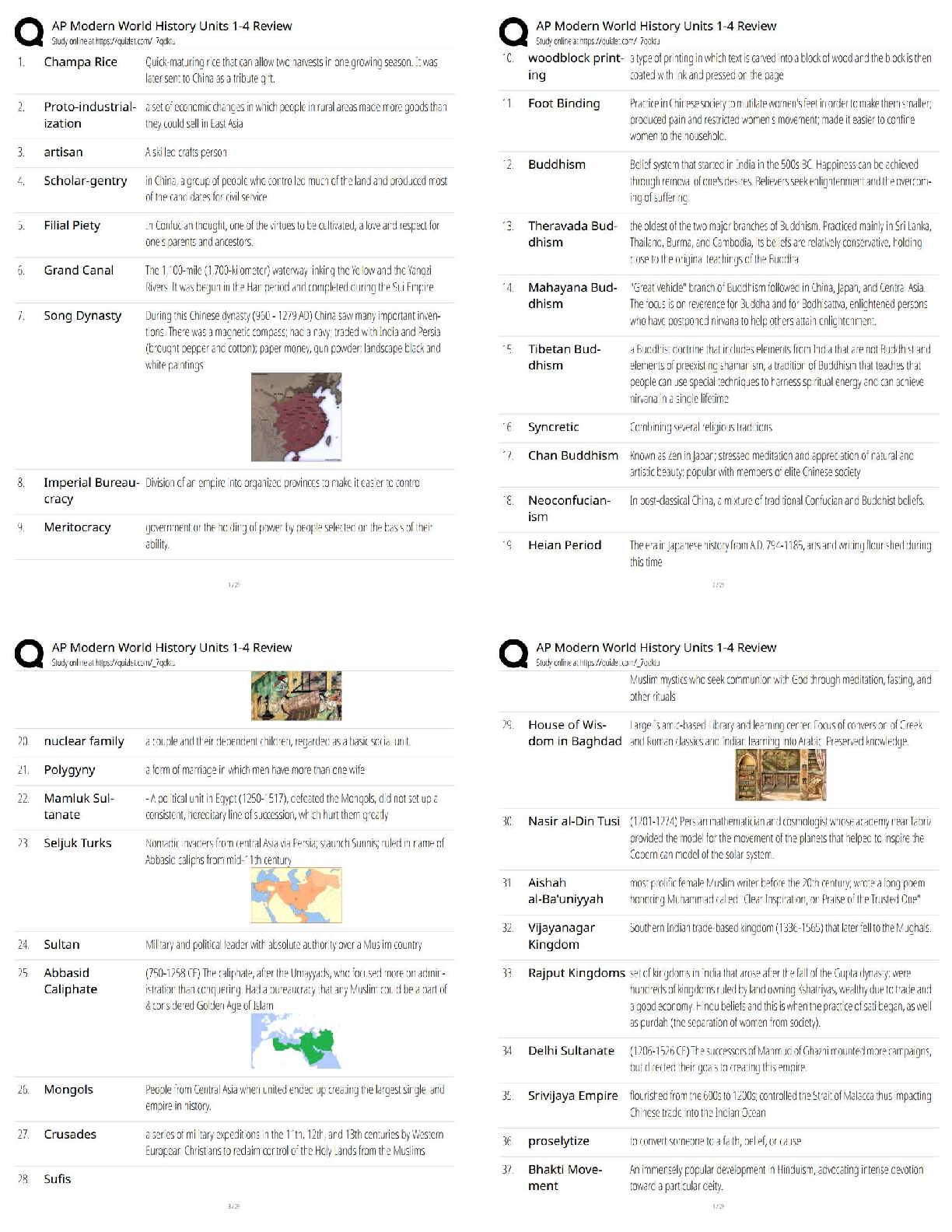
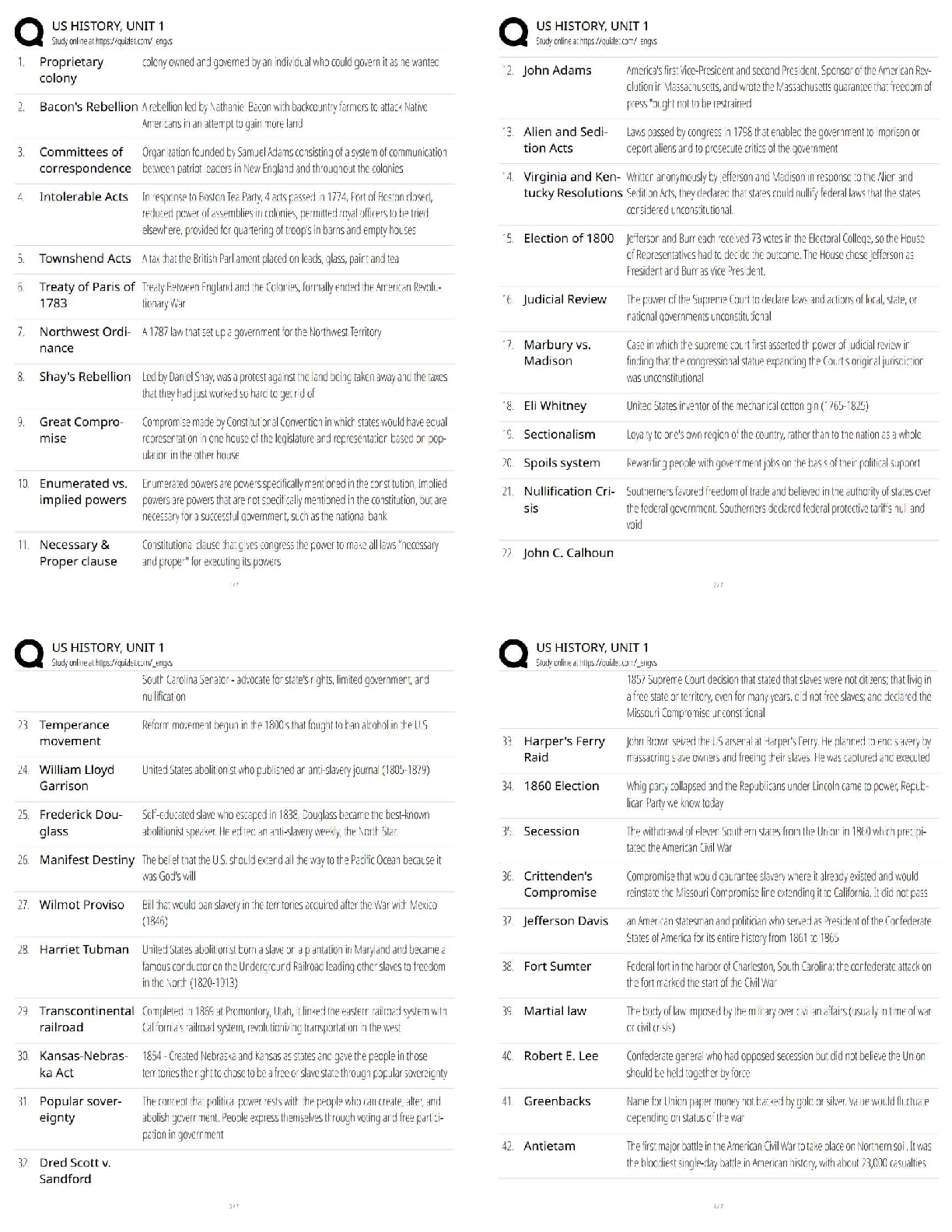
Computer Science > QUESTIONS & ANSWERS > PCNSA exam 144 Questions with 100% Correct Answers (All)
PCNSA exam 144 Questions with 100% Correct Answers
Document Content and Description Below
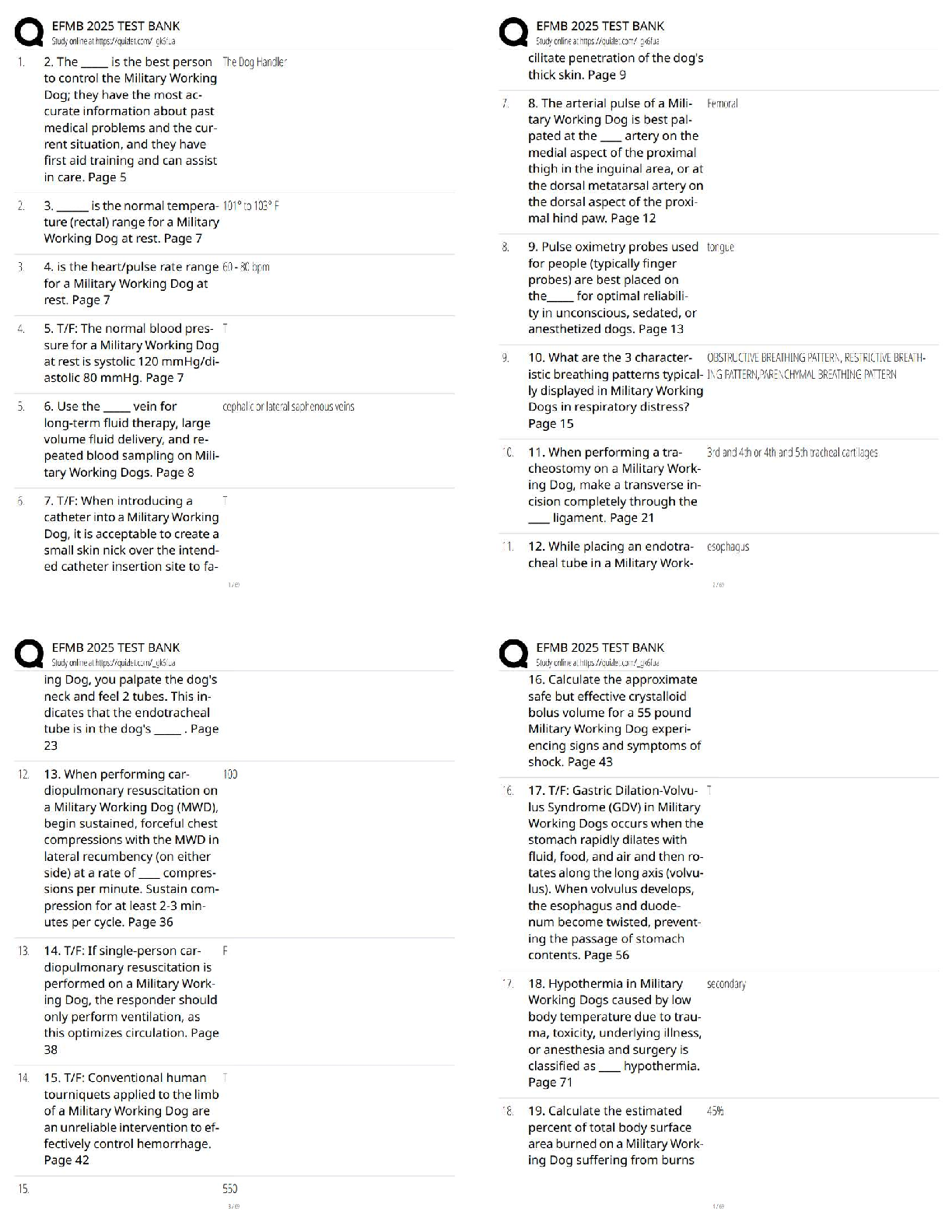
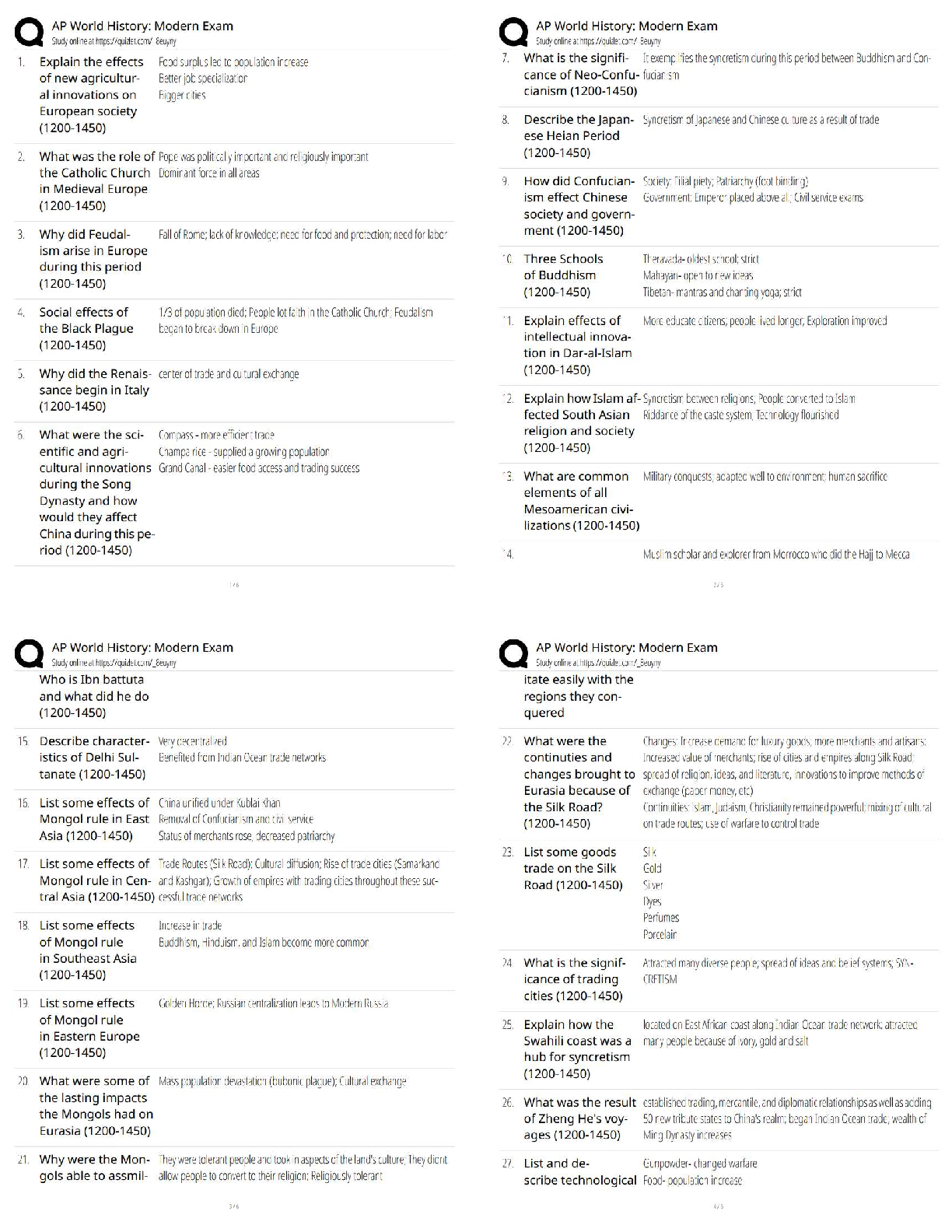
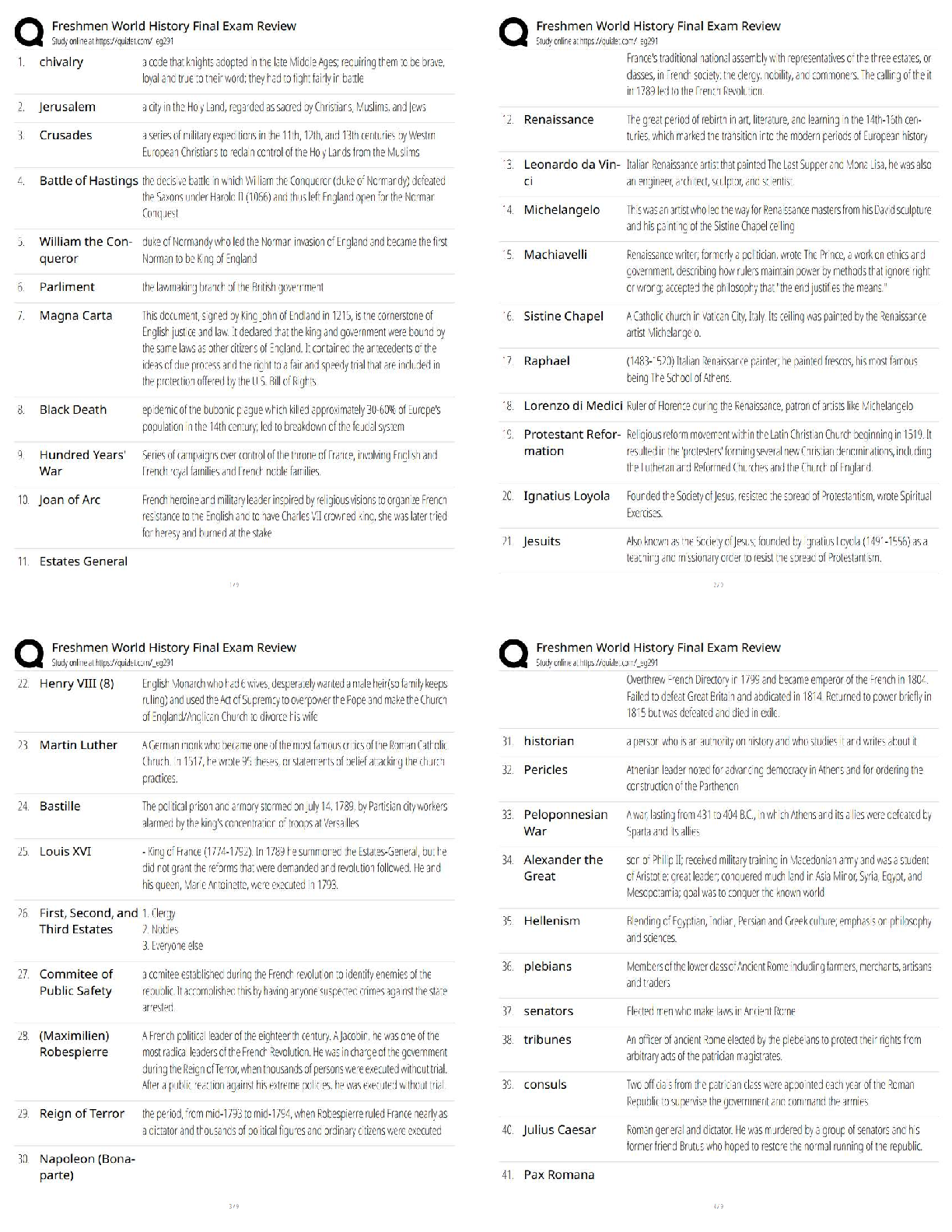
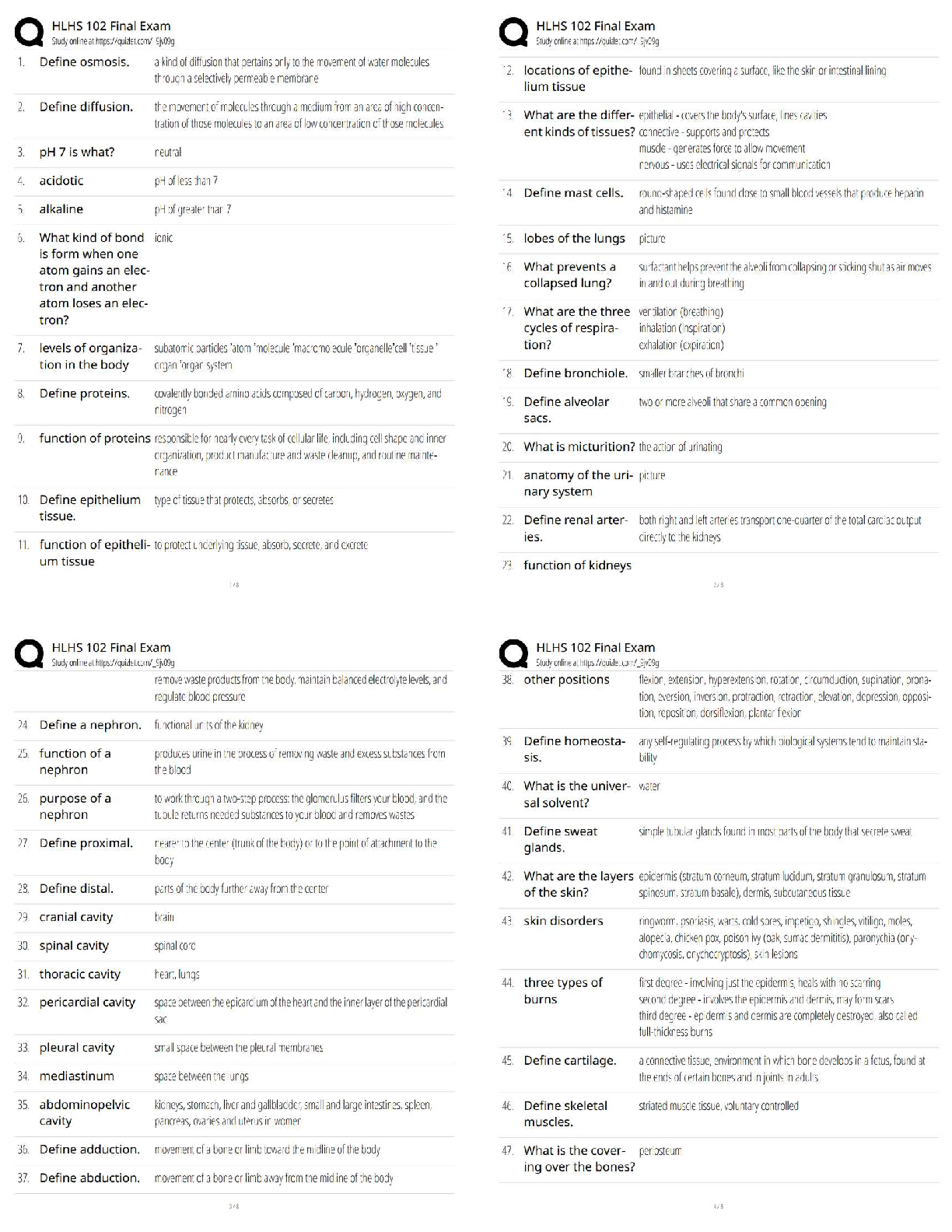
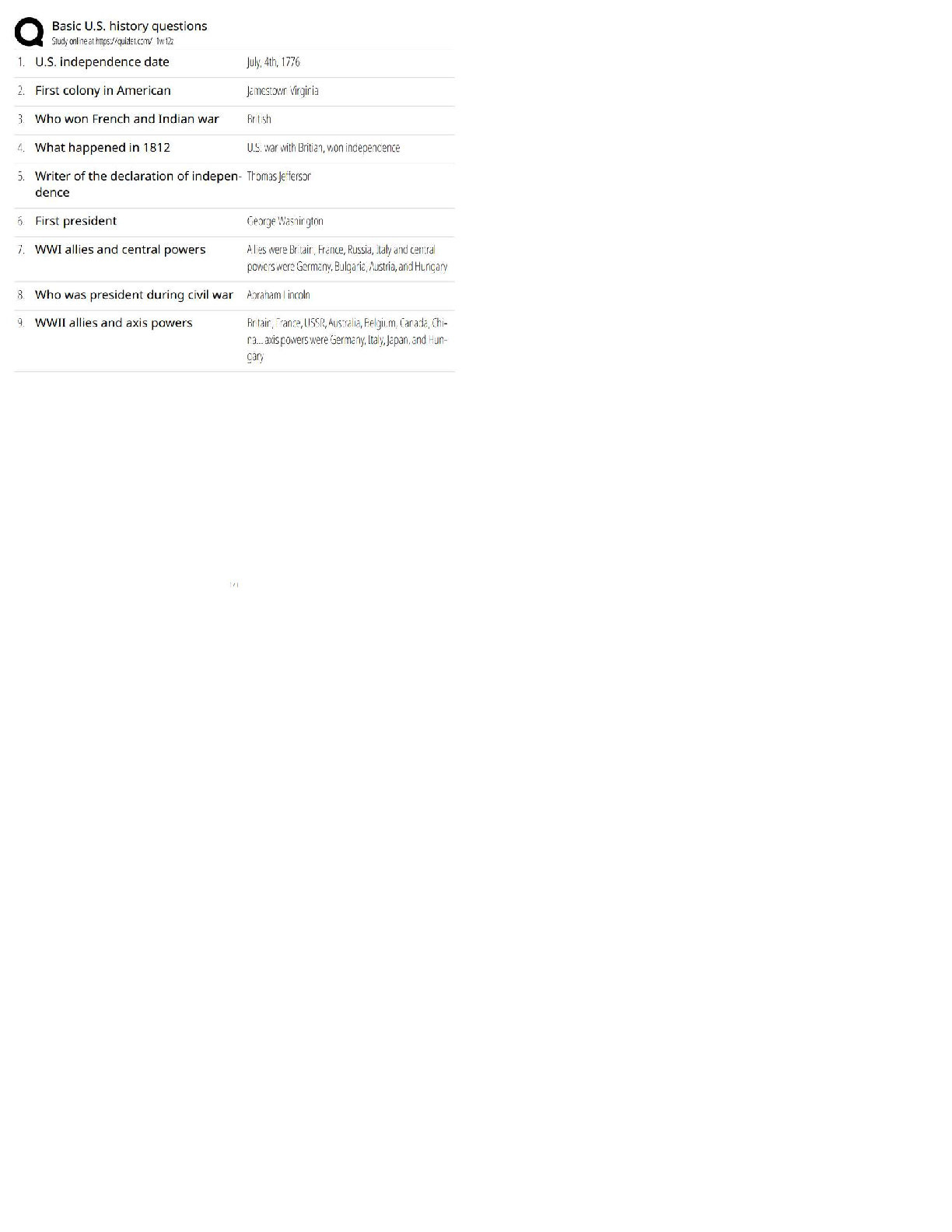
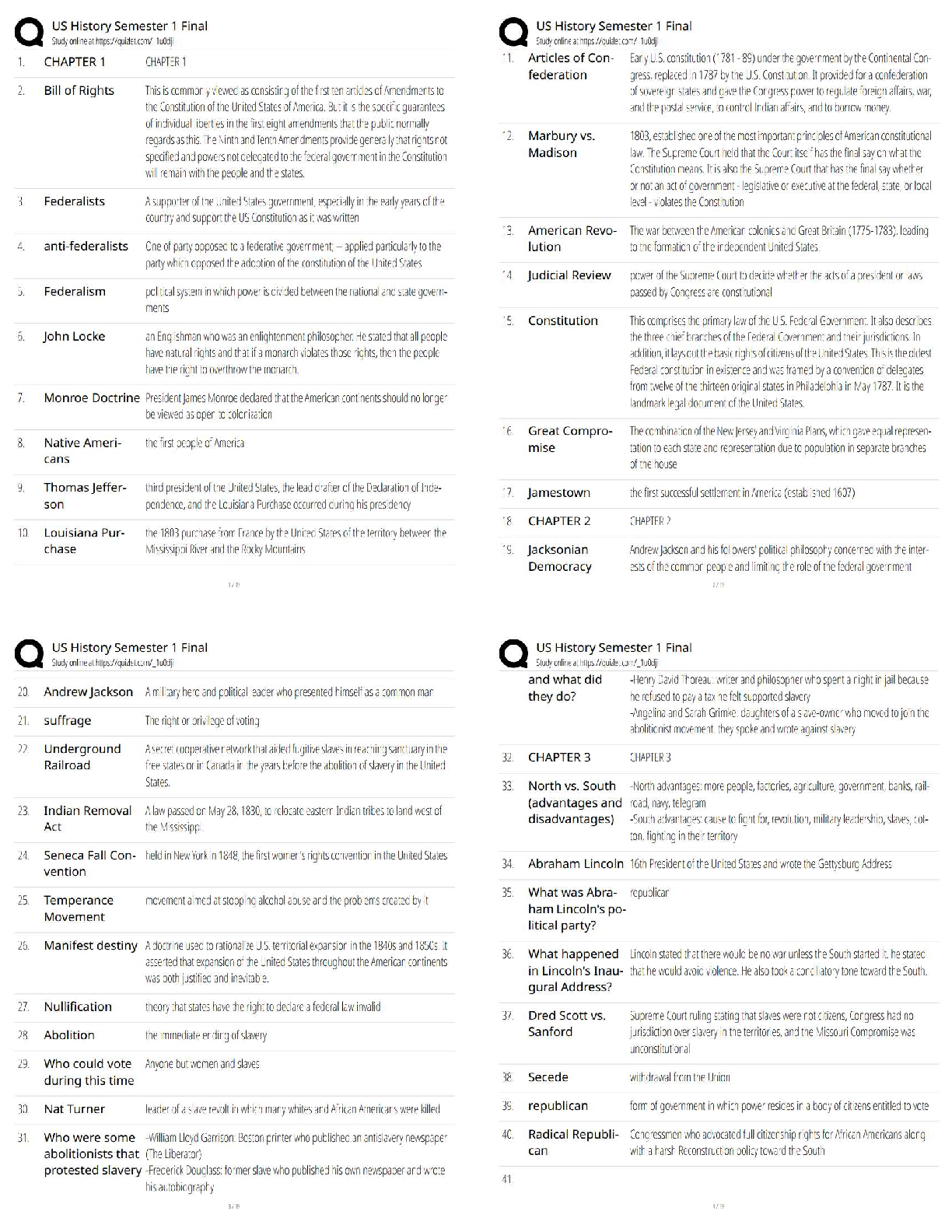
PCNSA exam 144 Questions with 100% Correct Answers Which firewall plane provides configuration, logging, and reporting functions on a separate processor? -Answer- Control plane A security admini ... strator has configured App-ID updates to be automatically downloaded and installed. The company is currently using an application identified byApp-ID as SuperApp_base.On a content update notice, Palo Alto Networks is adding new app signatures labeled SuperApp_chat and SuperApp_download, which will be deployed in 30 days.Based on the information, how is the SuperApp traffic affected after the 30 days have passed? -Answer- No impact because the firewall automatically adds the rules to the App-ID interface How many zones can an interface be assigned with a Palo Alto Networks firewall? -Answer- One Which two configuration settings shown are not the default? -Answer- Server Log Monitor Frequency (sec) Enable Session Which data-plane processor layer provides uniform matching for spyware and vulnerability exploits on a Palo Alto Networks Firewall? -Answer- Signature Matching Which option shows the attributes that are selectable when setting up application filters? -Answer- Category, Subcategory, Technology, Risk, and Characteristic Actions can be set for which two items in a URL filtering security profile? -Answer- Custom URL Categories PAN-DB URL Categories Which two statements are correct about App-ID content updates? -Answer- Existing security policy rules are not affected by application content updates After an application content update, new applications are automatically identified and classified Which User-ID mapping method should be used for an environment with clients that do not authenticate to Windows Active Directory? -Answer- Captive Portal An administrator needs to allow users to use their own office applications. How should the administrator configure the firewall to allow multiple applications in a dynamic environment? -Answer- Create an Application Group and add business-systems to it Which statement is true regarding a Best Practice Assessment? -Answer- It provides a percentage of adoption for each assessment data Complete the statement. A security profile can block or allow traffic. -Answer- after it is evaluated by a security policy that allows traffic When creating a Source NAT policy, which entry in the Translated Packet tab will display the options Dynamic IP and Port, Dynamic, Static IP, and None? -Answer- Translation Type Which interface does not require a MAC or IP address? -Answer- Virtual Wire A company moved its old port-based firewall to a new Palo Alto Networks NGFW 60 days ago. Which utility should the company use to identify out-of-date or unused rules on the firewall? -Answer- Rule Usage Filter > Hit Count > Unused in 90 days What are two differences between an implicit dependency and an explicit dependency in App-ID? -Answer- An implicit dependency does not require the dependent application to be added in the security policy An explicit dependency requires the dependent application to be added in the security policy Recently changes were made to the firewall to optimize the policies and the security team wants to see if those changes are helping.What is the quickest way to reset the hit counter to zero in all the security policy rules? -Answer- Use the Reset Rule Hit Counter > All Rules option Which two App-ID applications will need to be allowed to use Facebook-chat? -Answer- Facebook-base Facebook-chat Which User-ID agent would be appropriate in a network with multiple WAN links, limited network bandwidth, and limited firewall management plane resources? -Answer- Windows-based agent deployed on the internal network Your company requires positive username attribution of every IP address used by wireless devices to support a new compliance requirement. You must collect IP-to-user mappings as soon as possible with minimal downtime and minimal configuration changes to the wireless devices themselves. The wireless devices are from various manufactures.Given the scenario, choose the option for sending IP-to-user mappings to the NGFW. -Answer- syslog An administrator receives a global notification for a new malware that infects hosts. The infection will result in the infected host attempting to contact a command- and-control (C2) server. Which two security profile components will detect and prevent this threat after the firewall's signature database has been updated? -Answer- anti-spyware profile applied to outbound security policies URL filtering profile applied to outbound security policies In which stage of the Cyber-Attack Lifecycle would the attacker inject a PDF file within an email? -Answer- Weaponization Identify the correct order to configure the PAN-OS integrated USER-ID agent. 3. add the service account to monitor the server(s) 2. define the address of the servers to be monitored on the firewall 4. commit the configuration, and verify agent connection status 1. create a service account on the Domain Controller with sufficient permissions to execute the User- ID agent -Answer- 1-3-2-4 Users from the internal zone need to be allowed to Telnet into a server in the DMZ zone.Complete the security policy to ensure only Telnet is allowed.Security Policy: Source Zone: Internal to DMZ Zone __________services, Application default, and action = Allow -Answer- Application=Telnet [Show More]
Last updated: 3 years ago
Preview 1 out of 12 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Also available in bundle (1)
Click Below to Access Bundle(s)

PCNSA Bundled Exams with complete solutions
PCNSA Bundled Exams with complete solutions PCNSA 2022 Questions and Answers PNSCE - PAN-OS 10 Test Questions with Complete Answers PNSCE - Firewall 10.0: WildFire Versus Malware Exam Questions...
By Professor Lynne 3 years ago
$15
9
Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 05, 2022
Number of pages
12
Written in
All
Additional information
This document has been written for:
Uploaded
Sep 05, 2022
Downloads
0
Views
146