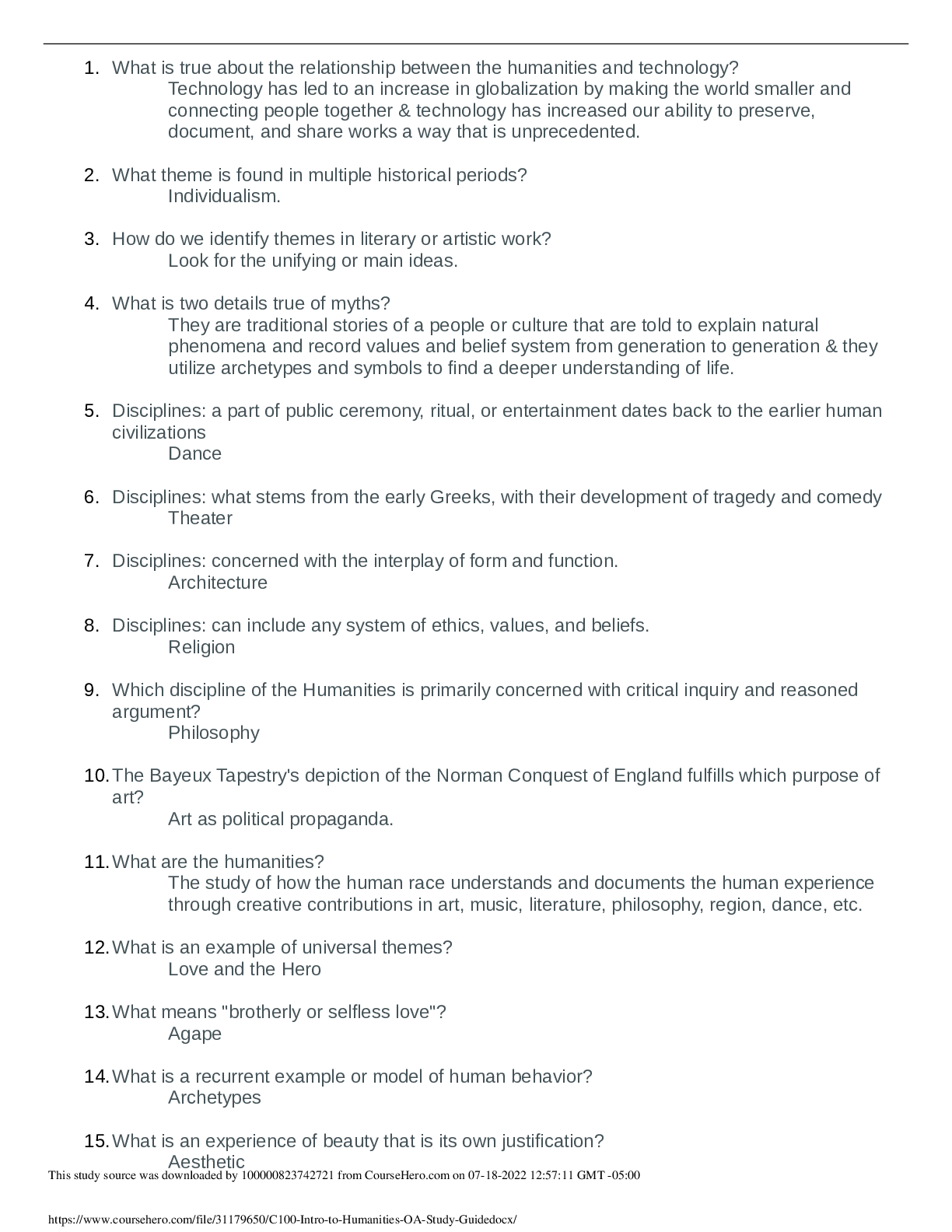
Chamberlain College of Nursing NR 503 Portfolio Part 2
$ 15

Test Bank for Financial Accounting, 11th Edition by Robert Libby, Patricia Libby & Frank Hodge | ISBN: 9781265083922 | Complete Verified Chapters 1-13 | Downloadable PDF
$ 20

Shadow Health- Brian Foster- Focused Exam: Chest Pain 1 Shadow Health- Brian Foster- Focused Exam: Chest Pain
$ 12

HESI RN NEW EXIT EXAM LATEST SOLUTION AND GUIDE.
$ 14

Anatomy & Physiology I with Lab Questions
$ 18

2.1.8 Lab 11: The Effects of Temperature and Particle Size Lab Assignment AP Chemistry Sem 2
$ 9

eBook [PDF] Pedagogical Encounters in the Post-Anthropocene (Volume 1) Childhood, Environment, Indigeneity 1st Edition By Jan Jagodzinski
$ 29

eBook Systems Engineering Analysis, Modeling and Simulation of Systems 1st Edition By Emmanuel Hygounenc
$ 29

ATI COMPREHENSIVE C. COMPREHESIVE
$ 25

SAT QAS - PAST May International PAPER
$ 10

eBook ISE [PDF] Essentials of Athletic Injury Management 12th Edition By William Prentice
$ 30

Test Bank - Medical-Surgical Nursing: Concepts for Interprofessional Collaborative Care 9e
$ 17.5
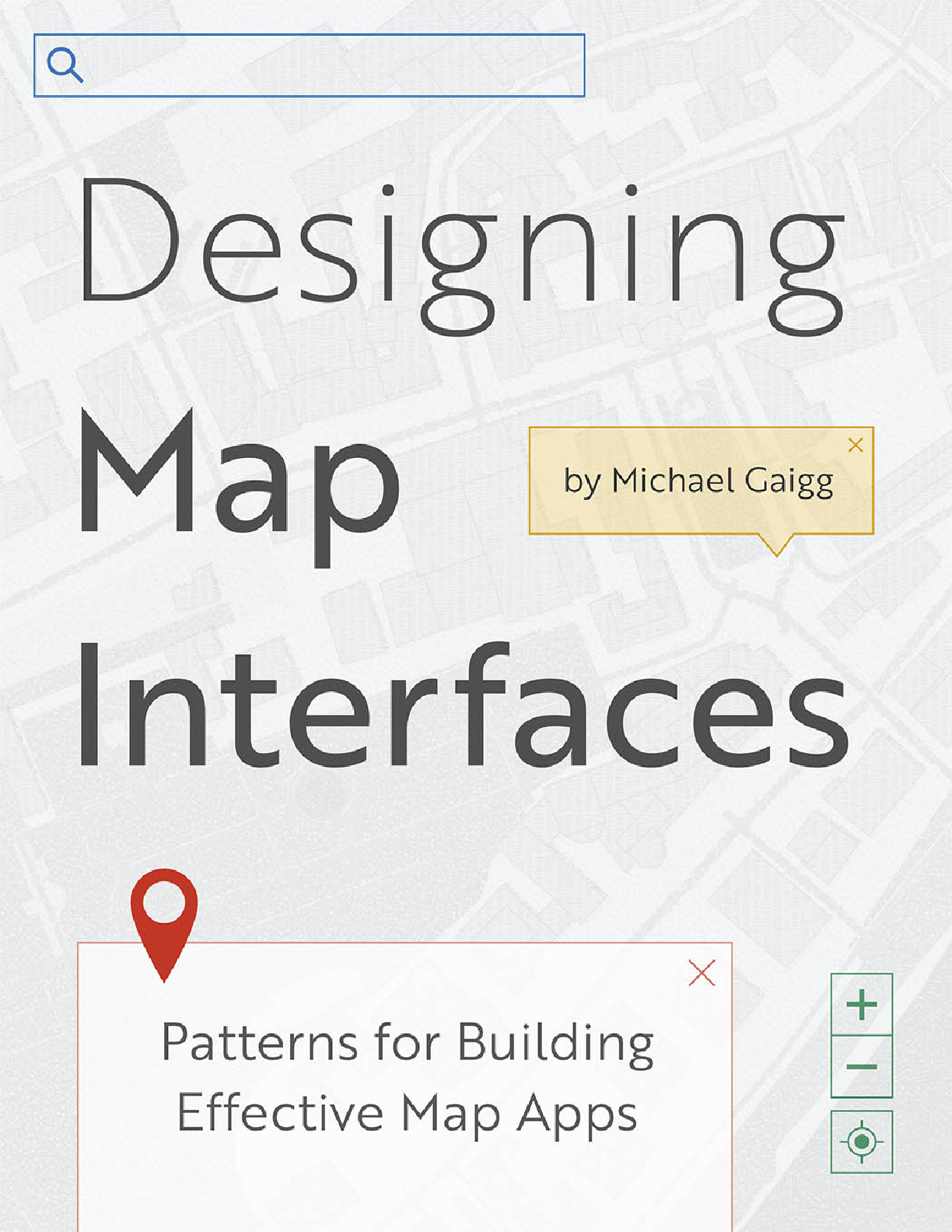
eBook Designing Map Interfaces Patterns for Building Effective Map Apps By Michael Gaigg
$ 29

NUR 513 Topic 6 - Discussion Question 2
$ 5

NR 601 Week 2 Polypharmacy Discussion
$ 5

TEXAS ESL CERTIFICATION EXAM 2023-2024 ACTUAL EXAM 300 QUESTIONS AND CORRECT DETAILED ANSWERS
$ 18
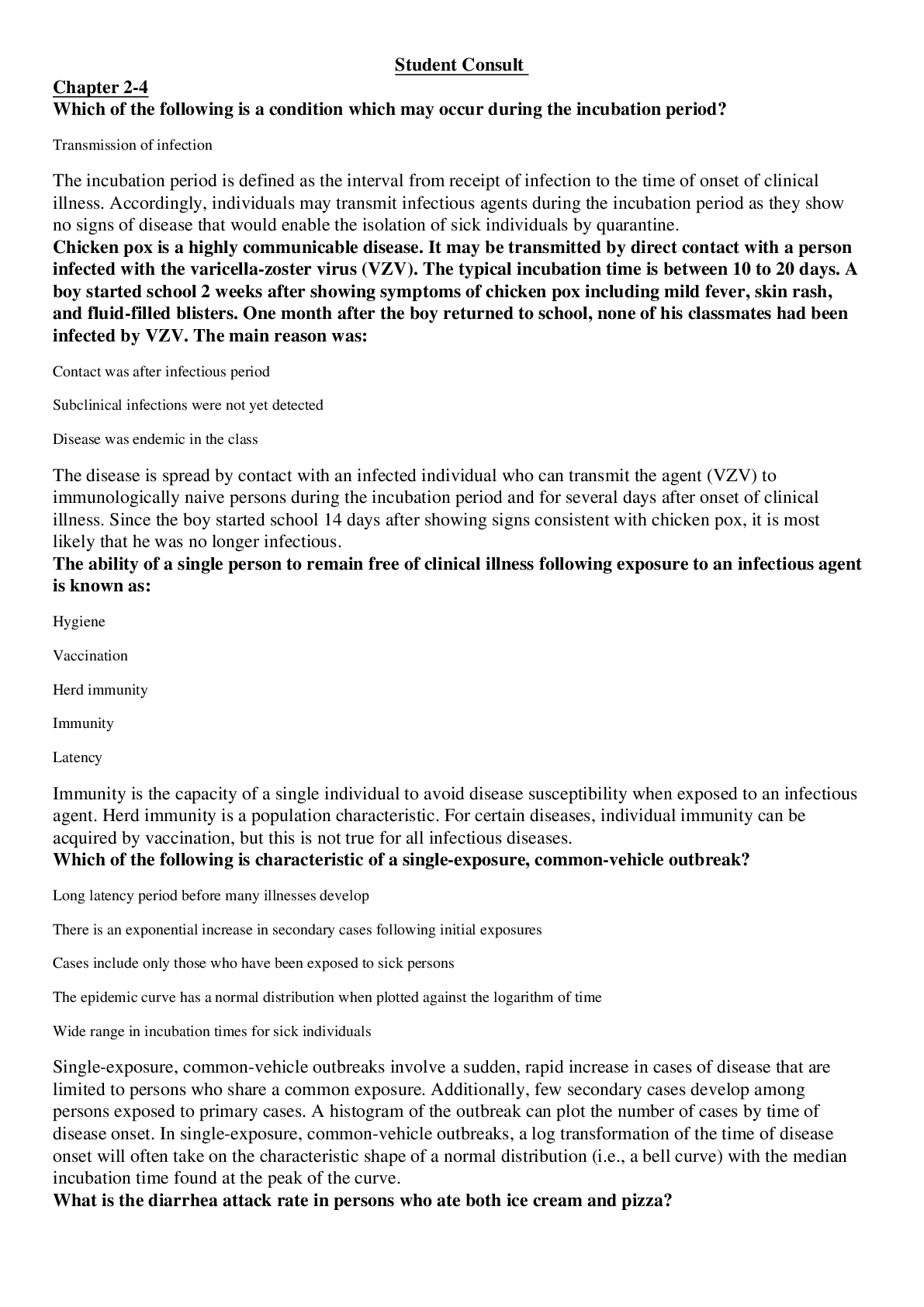
NR 503 Epi Midterm_Final SG .
$ 47.5

eBook EPUB [PDF] Orthopaedic Basic Science Foundations of Clinical Practice 5th Edition By Roy Aaron
$ 30
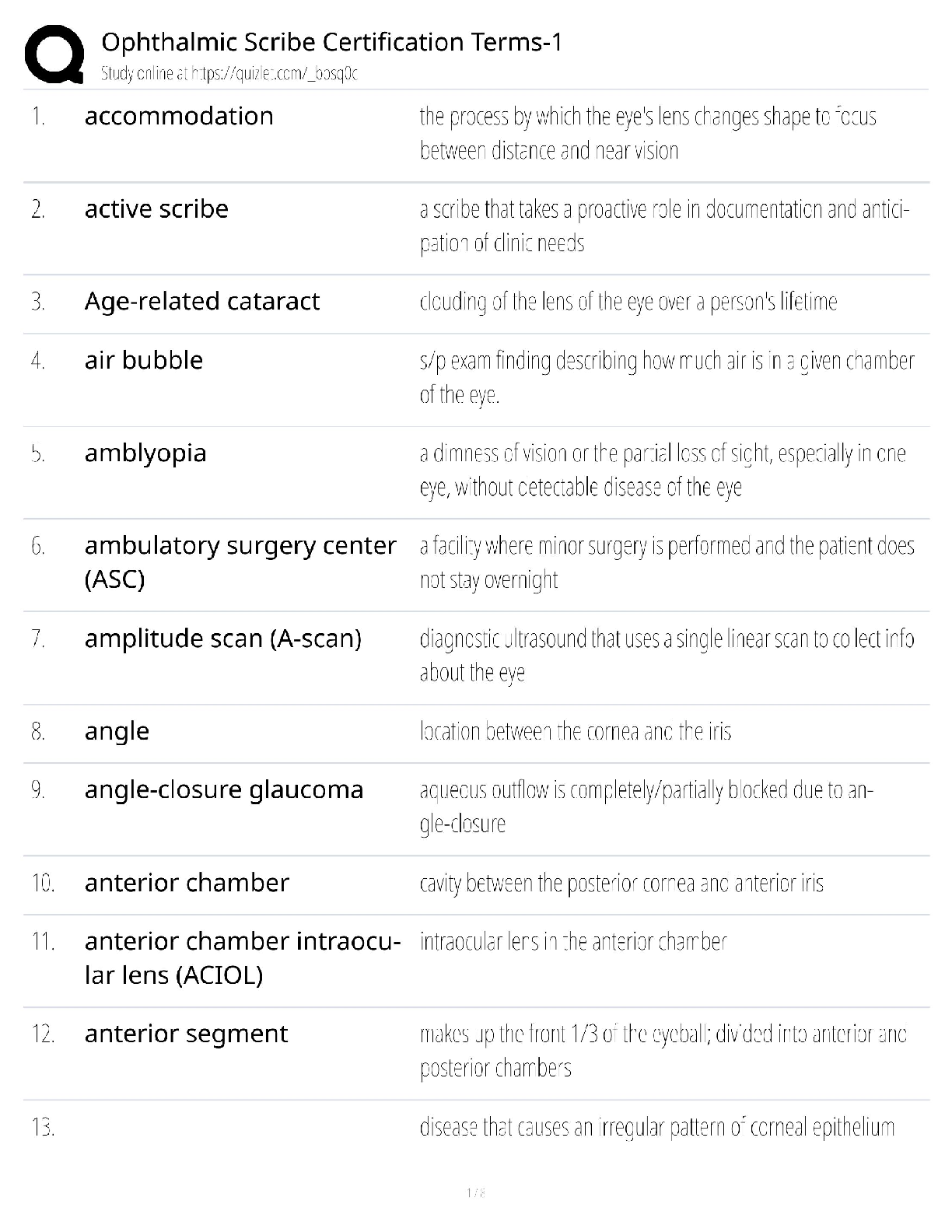
Ophthalmic Scribe Certification Terms / 2024 Exam Glossary / Eye Anatomy & EHR Abbreviations
$ 13.5
Summary NR 601 WEEK 6 QUIZ REVIEW
$ 18

JWMI 530 Financial Management I Knowledge Check 2 Quiz, 2019/20 Complete Solution Guide.
$ 9

Test Bank for Pharmacology A Patient Centered Nursing Process Approach 10th Ed by Linda
$ 12

Test Bank For General, Organic, and Biological Chemistry 4th Edition By Laura Frost, Todd Deal (All Chapters 100% Original Verified A+ Grade)
$ 22

NURSING NR 326 MENTAL-HEALTH-EXAM-1 test preparation study notes
$ 14.5
.png)
NR 360 Unit 8 Discussion Topic: Team Presentation/COMPLETE SOLUTION
$ 12.5

eBook Special Electrical Machinery 1st Edition By Jigneshkumar P. Desai
$ 29

Information Technology Project Management 5th Edition Jack Marchewka | Solutions Manual
$ 23

SAT Practice_Test_6_Answers_and_Explanations
$ 11
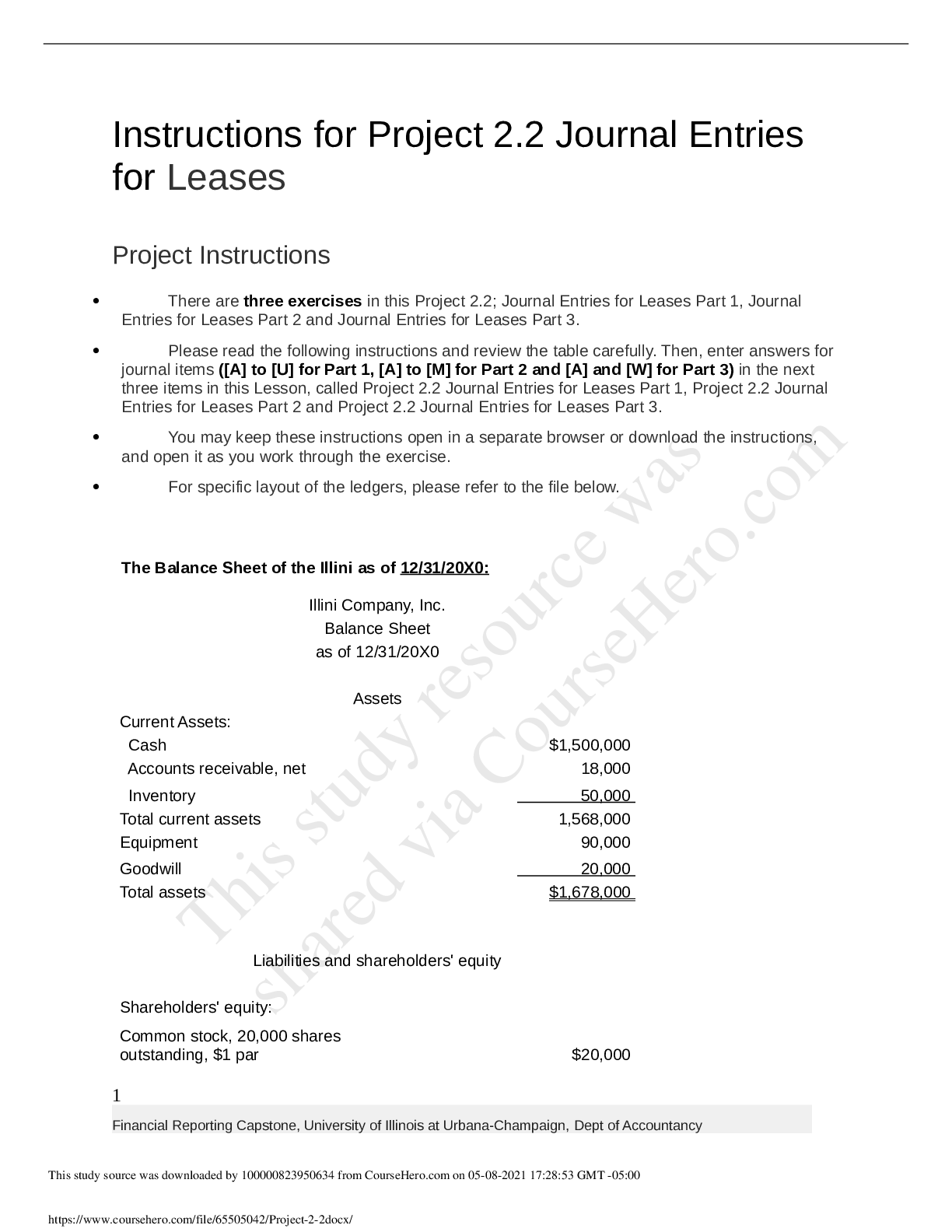
University of Illinois, Chicago ACTG MISC Project-2-2.
$ 7
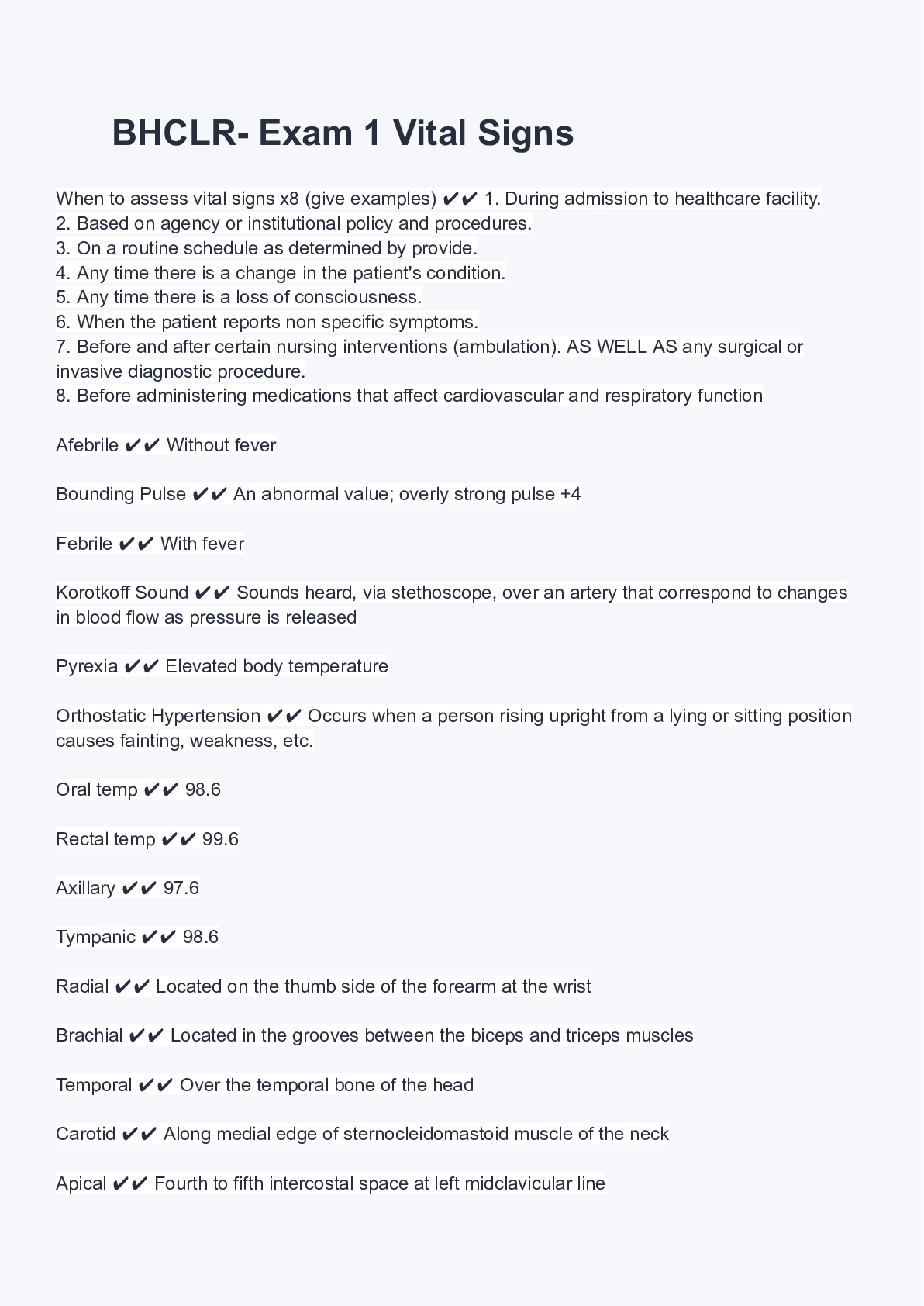
BHCLR- Exam 1 Vital Signs (1)
$ 7

NCLEX Therapeutic Communication Practice Questions – A+ Guaranteed Success with Verified Questions and Answers
$ 31
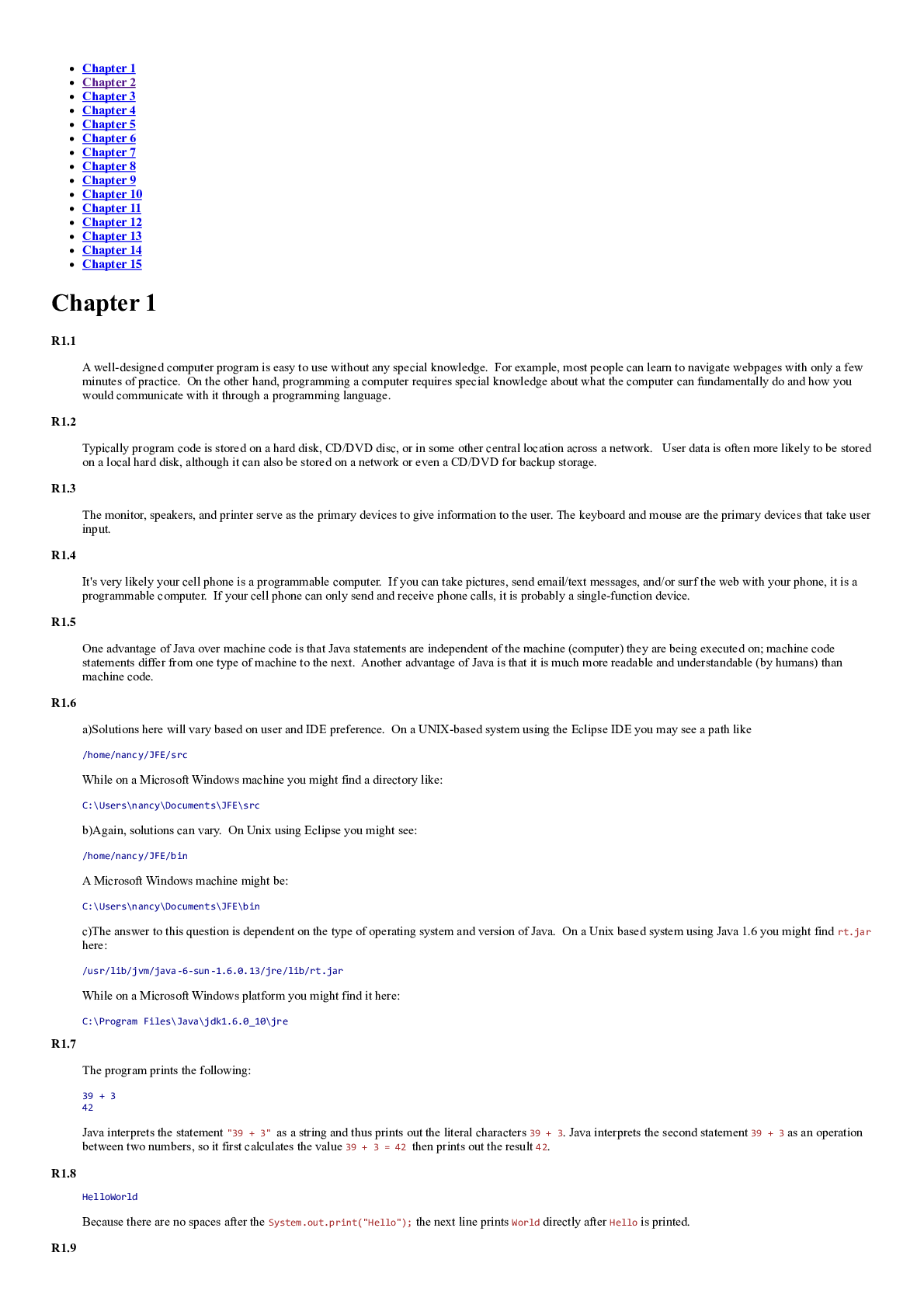
Brief Java Early Objects, 9e Cay Horstmann (Solution Manual)
$ 25

[eTextBook] [PDF] eDiscovery for the Legal Professional, 1st Edition By Christine E. Broucek
$ 24

(D403) HLTH 3330 FA Readiness Exam 2024 (Understanding Substance Abuse & Addiction)
$ 11

HS 499 PUBLIC HEALTH Kurious Hudson HS 499 Unit 8 Assignment Part 1
$ 15

NR 566 wk 6 study guide .docx. Comprehensive sheet
$ 5

NURS 6531N WEEK 1 ASSIGNMENT 2021 | Already Graded A+ | Walden University
$ 8

MEDICAL TERMINOLOGY & CLINICAL ASSESSMENT MASTERY: THE ULTIMATE 2026 STUDY GUIDE FOR HEALTHCARE STUDENTS AND EXAM SUCCESS
$ 13.5

Pierra Flack - Gizmo Equilibrium and Concentration
$ 11.5
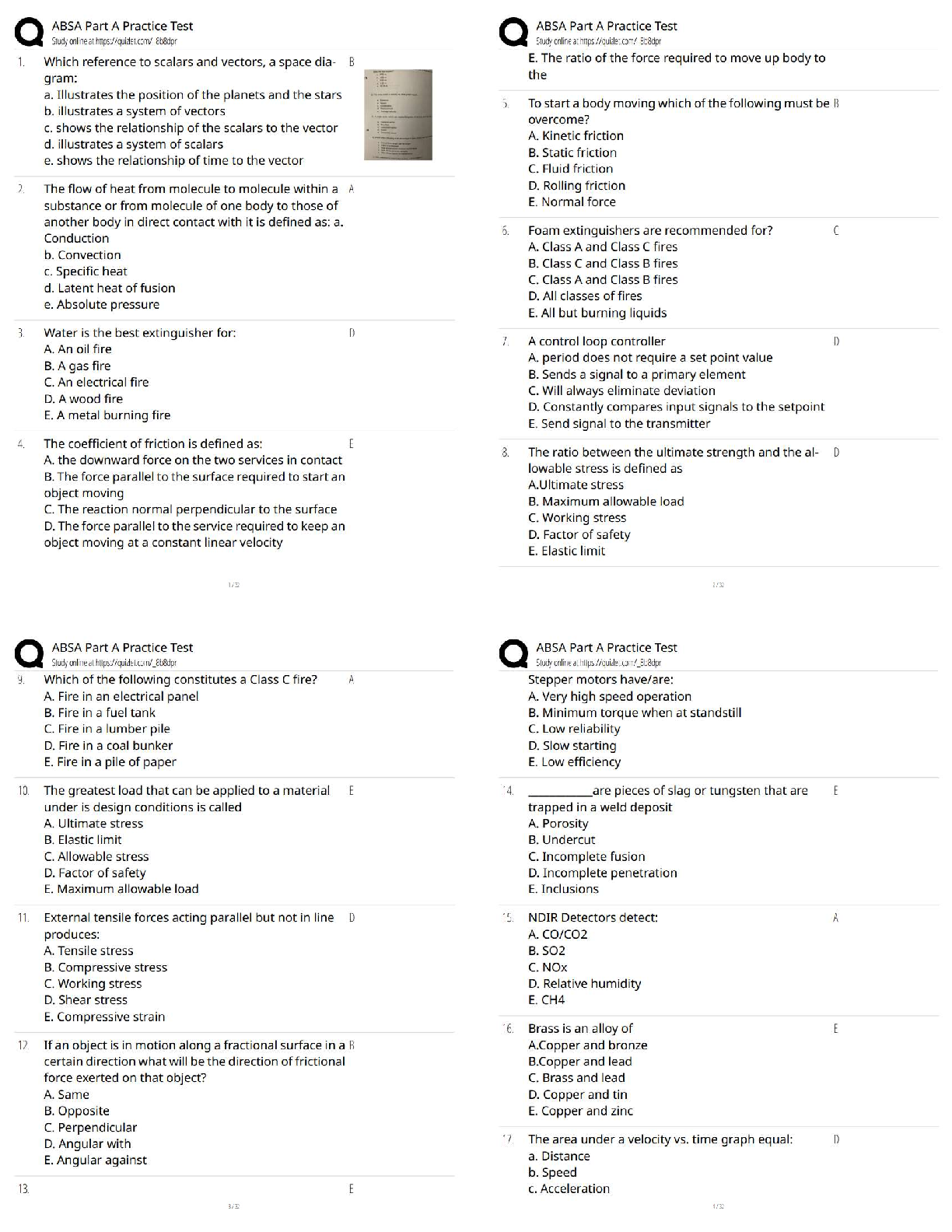
ABSA Part A Practice Test / Surgical Assistant Certification Exam Prep / CSFA & SA-C Review / Score 100% | 2026 Updated
$ 12

PSYC 324 Exam 3
$ 8

Defense Acquisition University CLC 222 | CLC222 Lesson 4 Answers.
$ 10
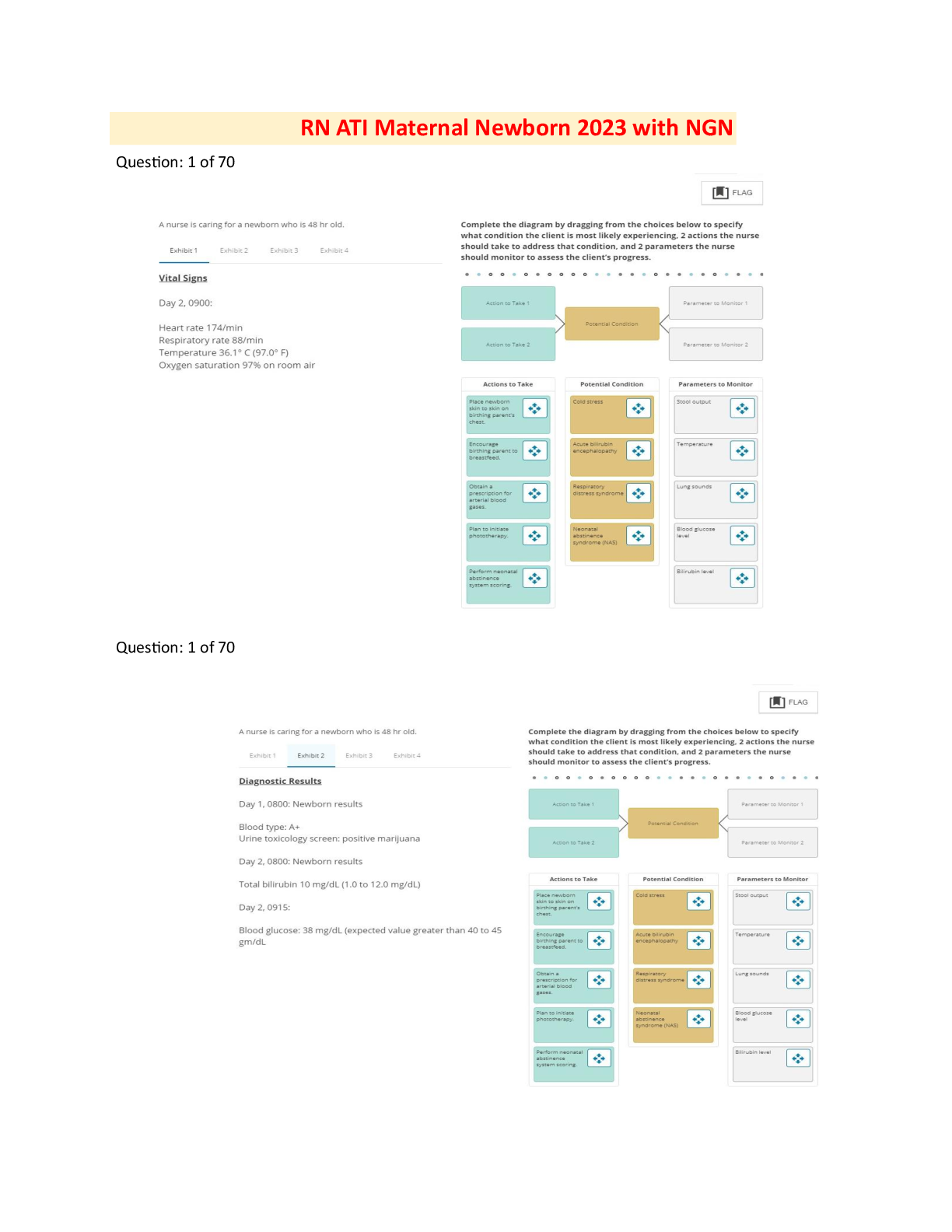
2025 NGN ATI RN Maternal Newborn (OB) Exam Bundle | 2023 Predictor, Complete Set | 70 Screenshot Questions Each | Verified Rationalized Answers
$ 75

Hesi A2 Reading
$ 10

Week 1 NDOC Exam (Latest 2026 2027 Update) Verified Questions Correct Answers Grade A 100 Guarantee Pass
$ 18

[eBook] [PDF] A Pen And Paper Introduction To Statistics 1st Edition By Antonio Marco
$ 25

Introduction to Psychology PSYC_1051_2020. Seneca College GNED 1106
$ 7
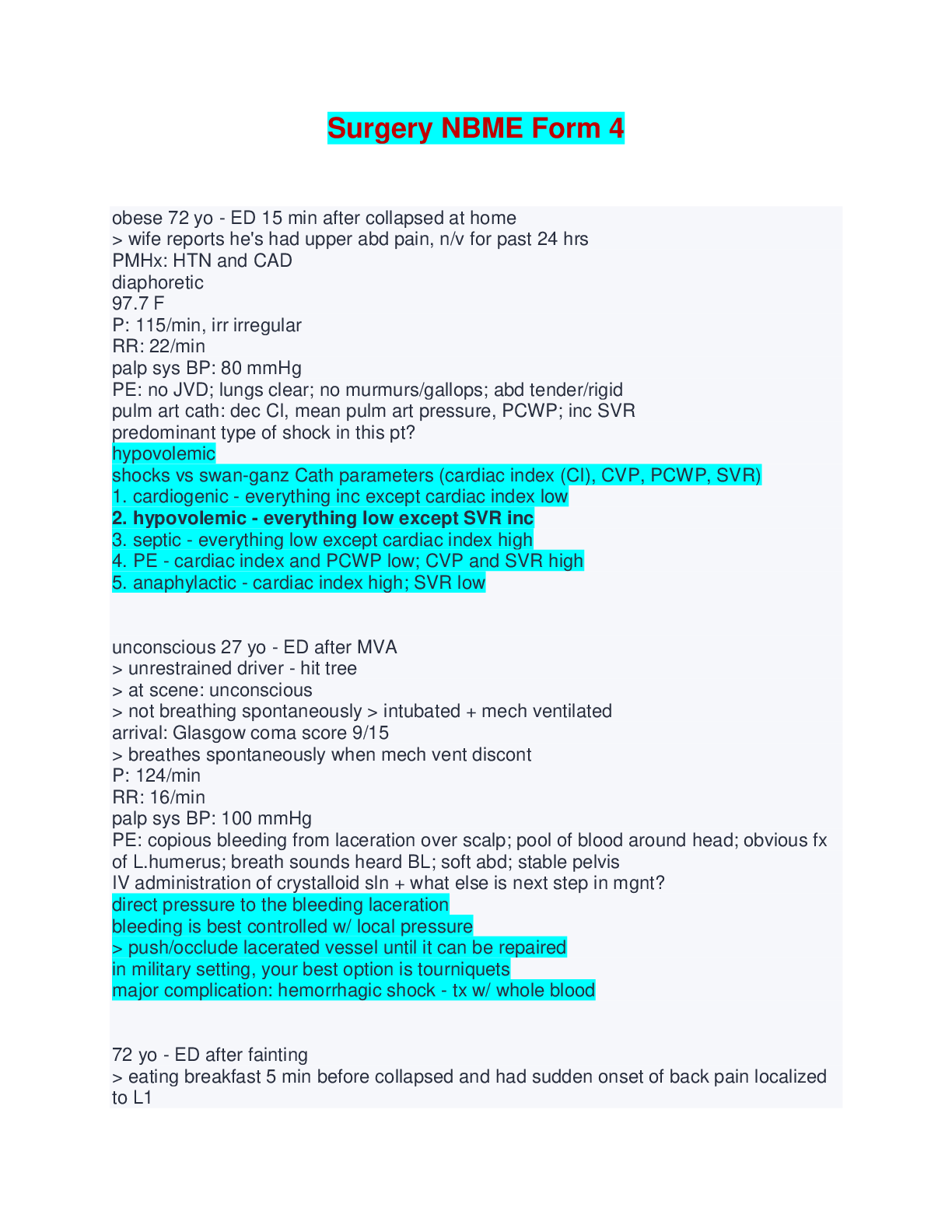
Surgery NBME Form 4 - Questions and Answers
$ 16
WEEK 7 CLASS 6531 IHUMAN CASE STUDY FOR A 25 YEARS OLD FEMALE PRESENTING LOOSE STOOL
$ 33
.png)
A+ ACT Math Practice Test 1 (60 Question Full Test and Review Question Solution)
$ 24

Summarized guide on Understanding Medical Surgical Nursing 6th Edition - GUARANTEED 100% SCORE
$ 16

NCLEX-RN 2025 Success Guide – 300 Priority-Based Practice Questions with Expert Rationales (NGN Included)
$ 17

RN Pharmacology for Nursing ebook REVIEW MODULE EDITION ,2021 LATEST
$ 24

POLICIES & PRACTICE STANDARDS.STATE NURSE PRACTICE ACT POLICIES & PRACTICE STANDARS.
$ 20.5

DTS Basic - DTS Travel Documents _ DTS 101 | Questions with Complete Solutions
$ 6

NR 439 Week 1 Graded Discussion Topic; Introduction to Evidence-based Practice.
$ 5.5

eBook (scan copy) Teaching Toward Solutions, A Solution Focused Guide to Improving Student Behavior, Grades, Parental Support and Staff Morale 2nd Edition by Linda Metcalf, Ryan Metcalf
$ 29

2015-Test Bank-LeMoneBurkeBauldoffGubrud-Medical-Surgical Nursing 6th Edition PII
$ 12

2024 HESI RN LEADERSHIP EXIT EXAM 7 LATEST VERSIONS AND 3 PRACTICE EXAM EACH EXAM CONTAINS 55 QUESTIONS AND CORRECT DETAILED ANSWERS
$ 27.5
.png)
rmy OPSEC level 1 2022 Exam Questions - Answered (Newcomers & Refresher)
$ 10
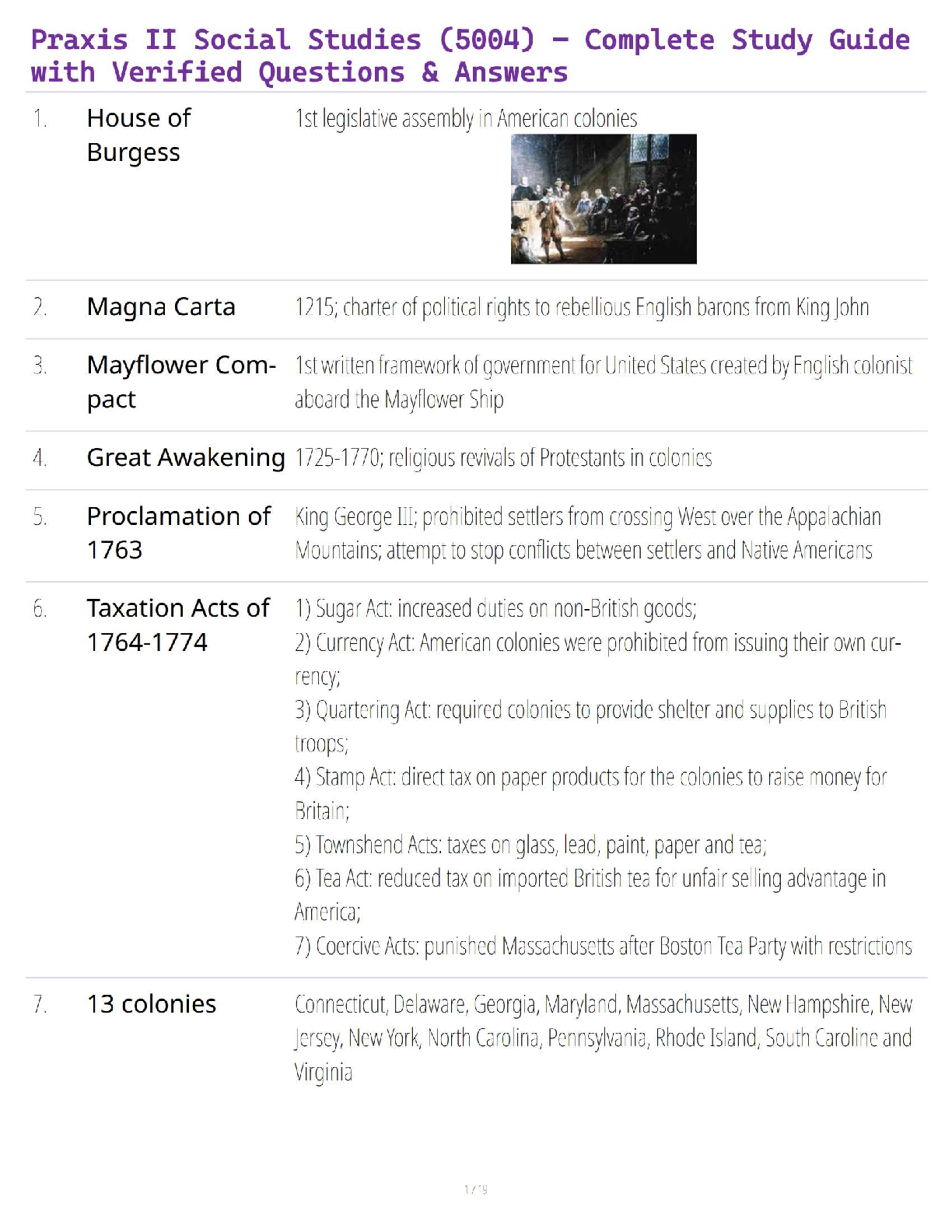
Praxis II Social Studies (5004) – Complete Study Guide with Verified Questions & Answers