Military Science > QUESTIONS & ANSWERS > Counterintelligence Awareness and reporting pretest questions and answers 100% pass (All)
Counterintelligence Awareness and reporting pretest questions and answers 100% pass
Document Content and Description Below
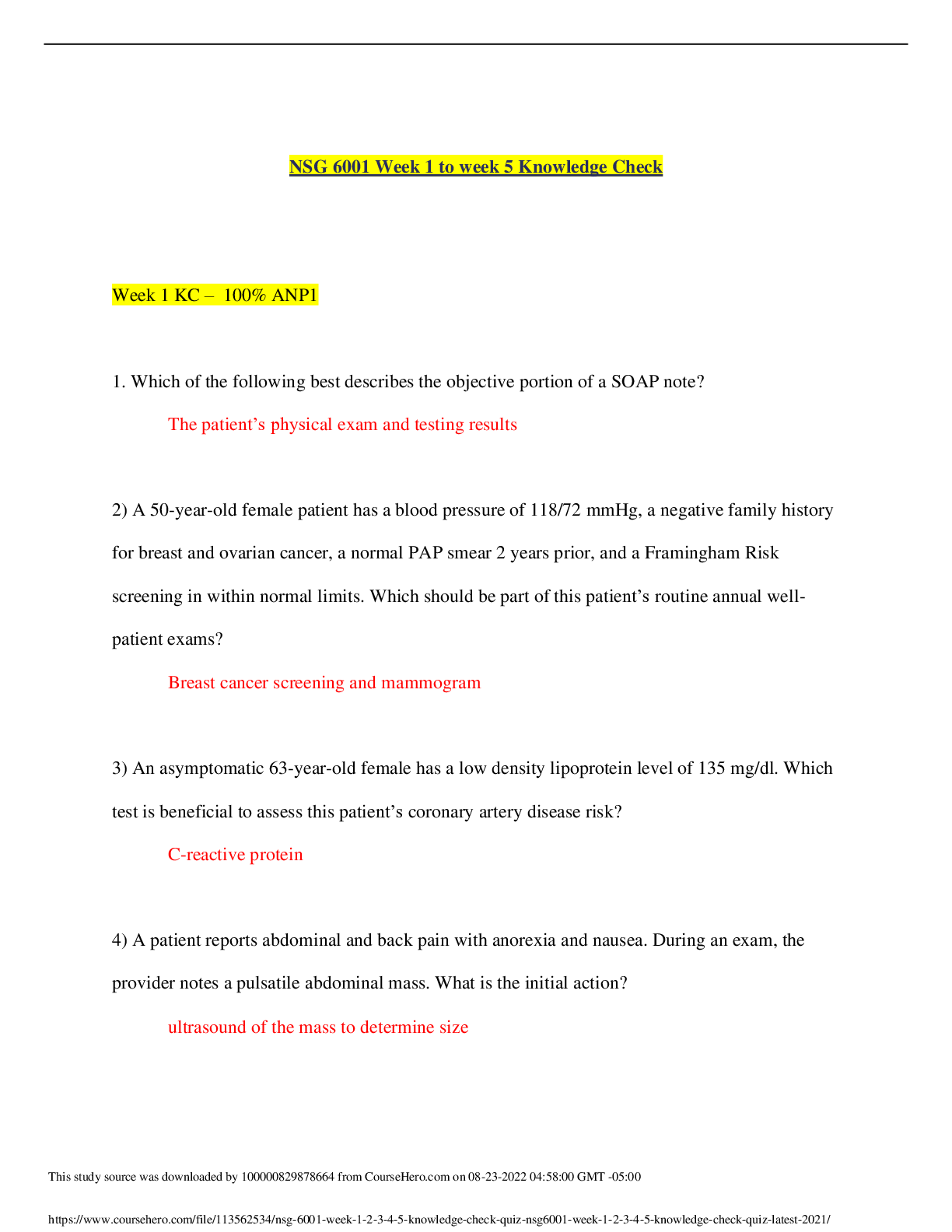
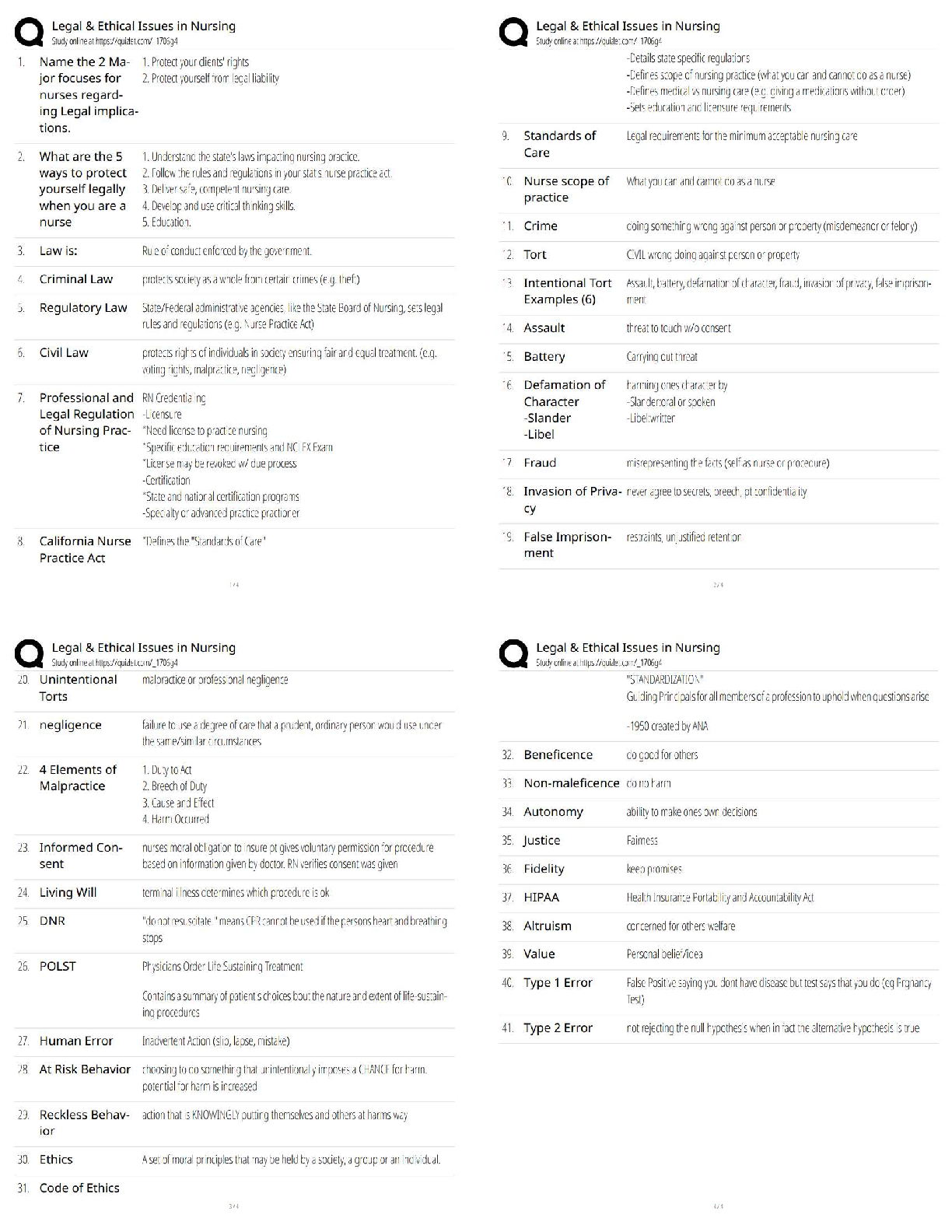
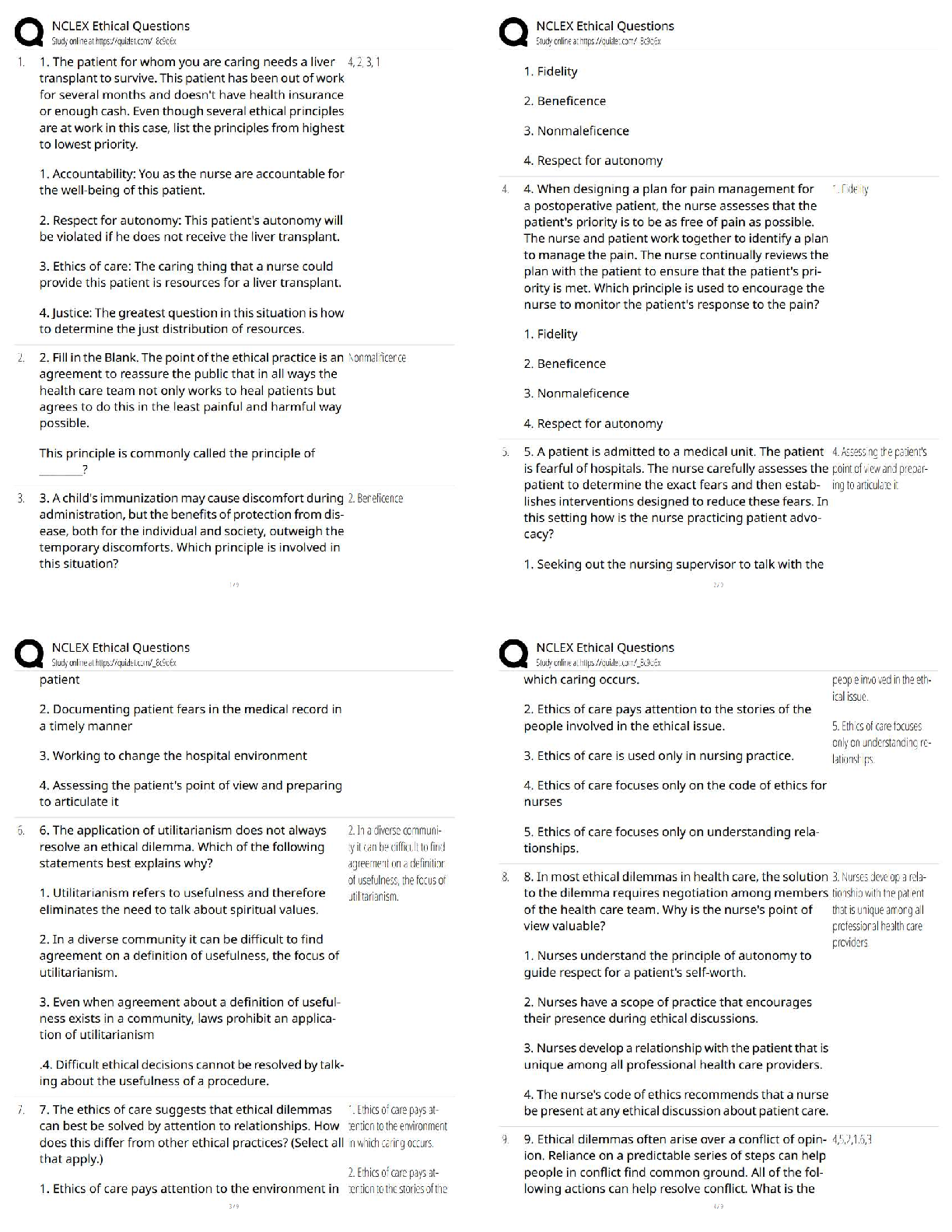
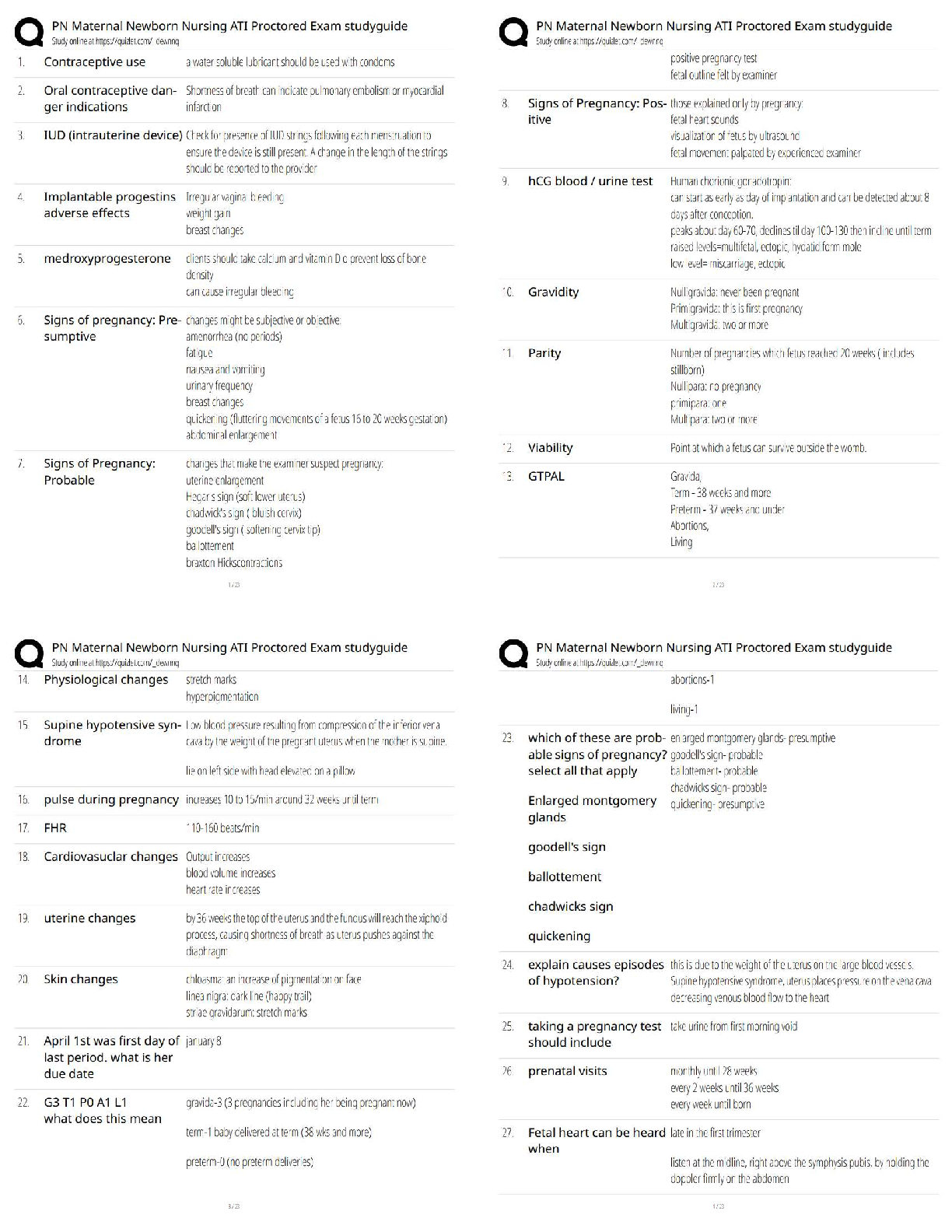
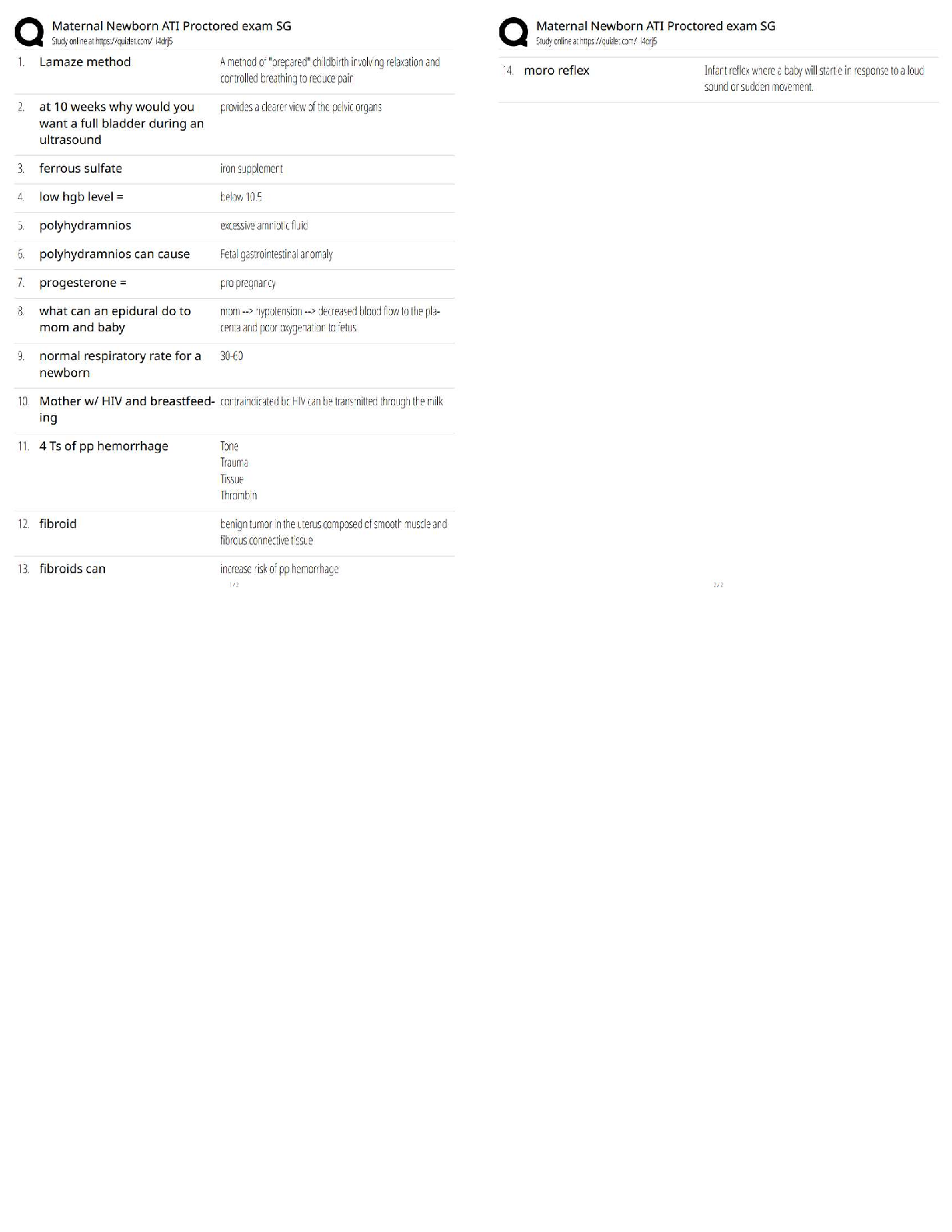
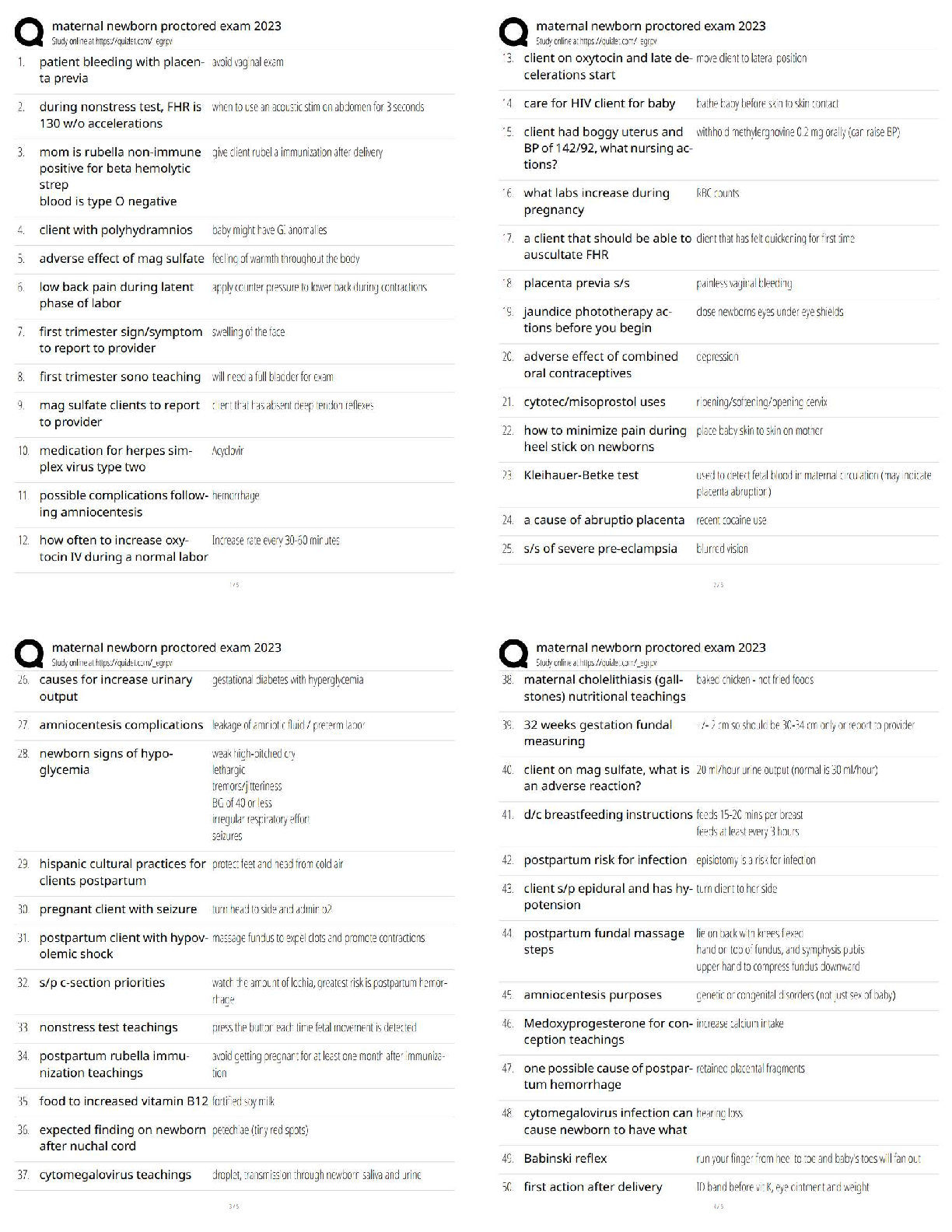
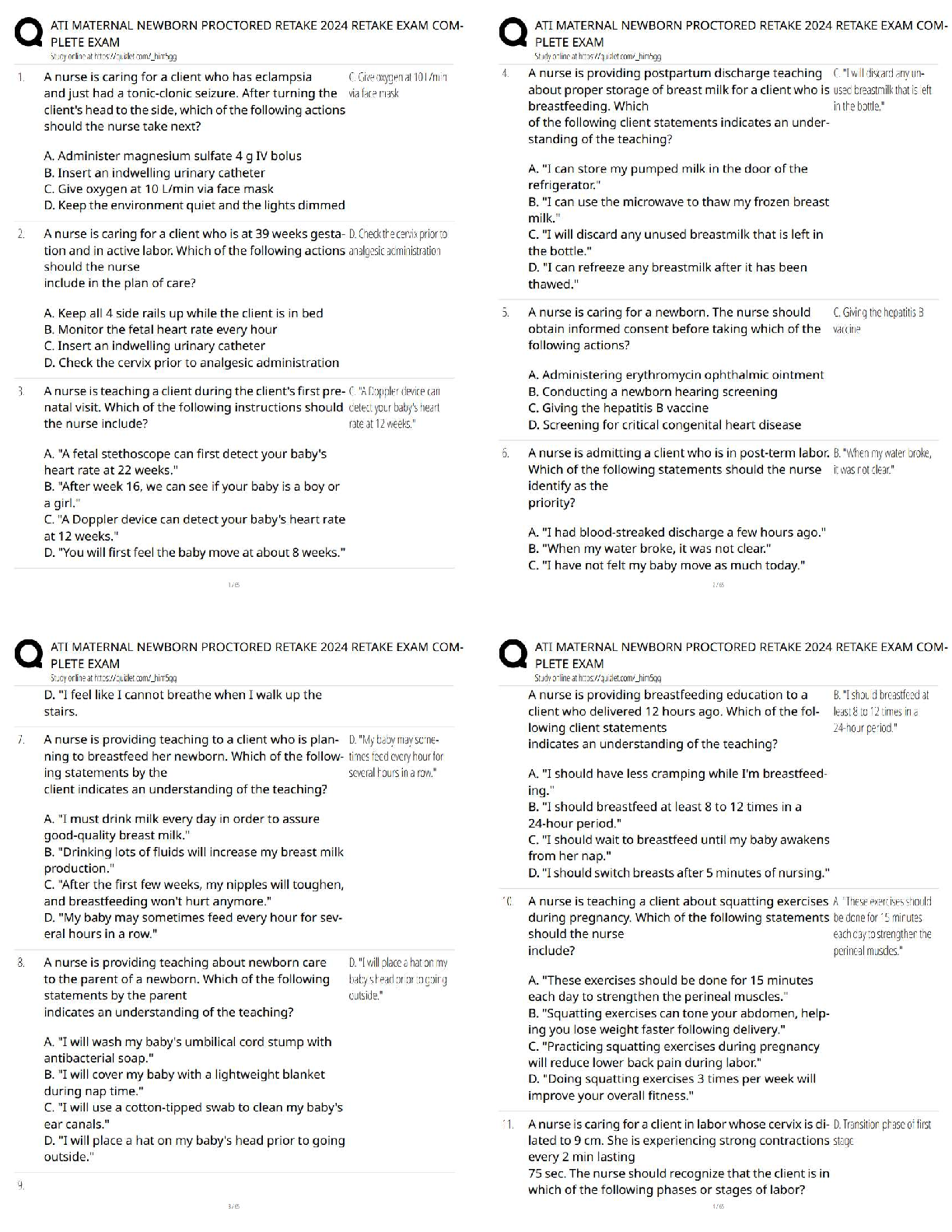
Counterintelligence Awareness and reporting pretest questions and answers 100% pass Select all that apply. Counterintelligence (CI) pre- and post-foreign travel briefs support you by providing (Co ... urse Introduction, Page 3) ✔✔Information on local and regional threat environments (correct) Travel area intelligence and security practices and procedures (correct) Reportable activity guidelines (correct) Defensive actions needed to defeat threats (correct) 2) Communicating information about the national defense to injure the U.S. or give advantage to a foreign nation is called (Lesson 1: Foreign Intelligence Entities (FIE), Page 4) ✔✔Espionage (correct) 3) It is acceptable to discuss sensitive information such as travel plans in taxis, buses, or other public transportation while traveling in foreign countries. (Lesson 4: Traveling in a Foreign Country, Page 3) ✔✔False (correct) Terrorist organizations are considered Foreign Intelligence Entities by the U.S. (Lesson 1: Foreign Intelligence Entities, Page 1) ✔✔True (correct) ) Unclassified information can be collected to produce information that, when put together, would be considered classified. (Lesson 1: Foreign Intelligence Entities, Page 3) ✔✔true All requests to transport media back to the U.S. on behalf of a foreign country must be reported to your Counterintelligence representative. (Lesson 5: Reporting Requirements, Page 1) ✔✔true Foreign adversary use of social networking services causes which of the following concerns? (Select the best answer) (Lesson 3: Internet and Social Networking Services, Page 3) ✔✔All of the answers are correct (correct) Risk of exposure is low because cyber operations can be carried out remotely and with a high degree of anonymity Foreign adversaries can conduct cyber operations to collect intelligence or degrade the effectiveness of our technologies Cyber operations can be conducted relatively cheaply and easily, offering high returns with a low degree of risk 8) Human intelligence (HUMINT) targeting methods include which of the following? Select all that apply. (Lesson 1: Foreign Intelligence Entities, Page 8) ✔✔Relationship building (correct) Cold Pitching (correct) Passive collection (correct) Elicitation (correct) 9) A foreign power activity or knowledge that is inconsistent with the expected norms that suggest prior foreign knowledge of U.S national security information, processes or capabilities is defined as (Lesson 1: Foreign Intelligence Entities, Page 10) ✔✔Anomaly What percentage of information collected is unclassified? (Lesson 1: Foreign Intelligence Entities, Page 3 ✔✔80-85% ) Impairment of a Signals Intelligence collection platform or an unexplained compromise of U.S. Intelligence Operations are examples of (Lesson 1: Foreign Intelligence Entities, Page 10) ✔✔anomaly The Internet and social networking services have allowed (Lesson 3: Internet and Social Networking Services, Page 2) ✔✔Relative anonymity and safety for hackers Information about an individual to be obtained which allow the FIE to understand their targets weaknesses, like and dislikes before their first meeting Organizations to oversee operations more gl [Show More]
Last updated: 3 years ago
Preview 1 out of 4 pages
.png)
Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$7.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 25, 2022
Number of pages
4
Written in
All
Additional information
This document has been written for:
Uploaded
Aug 25, 2022
Downloads
0
Views
201








.png)