Information Technology > QUESTIONS & ANSWERS > WGU Test Prep 3 OA C795 Questions and Answers (All)
WGU Test Prep 3 OA C795 Questions and Answers
Document Content and Description Below
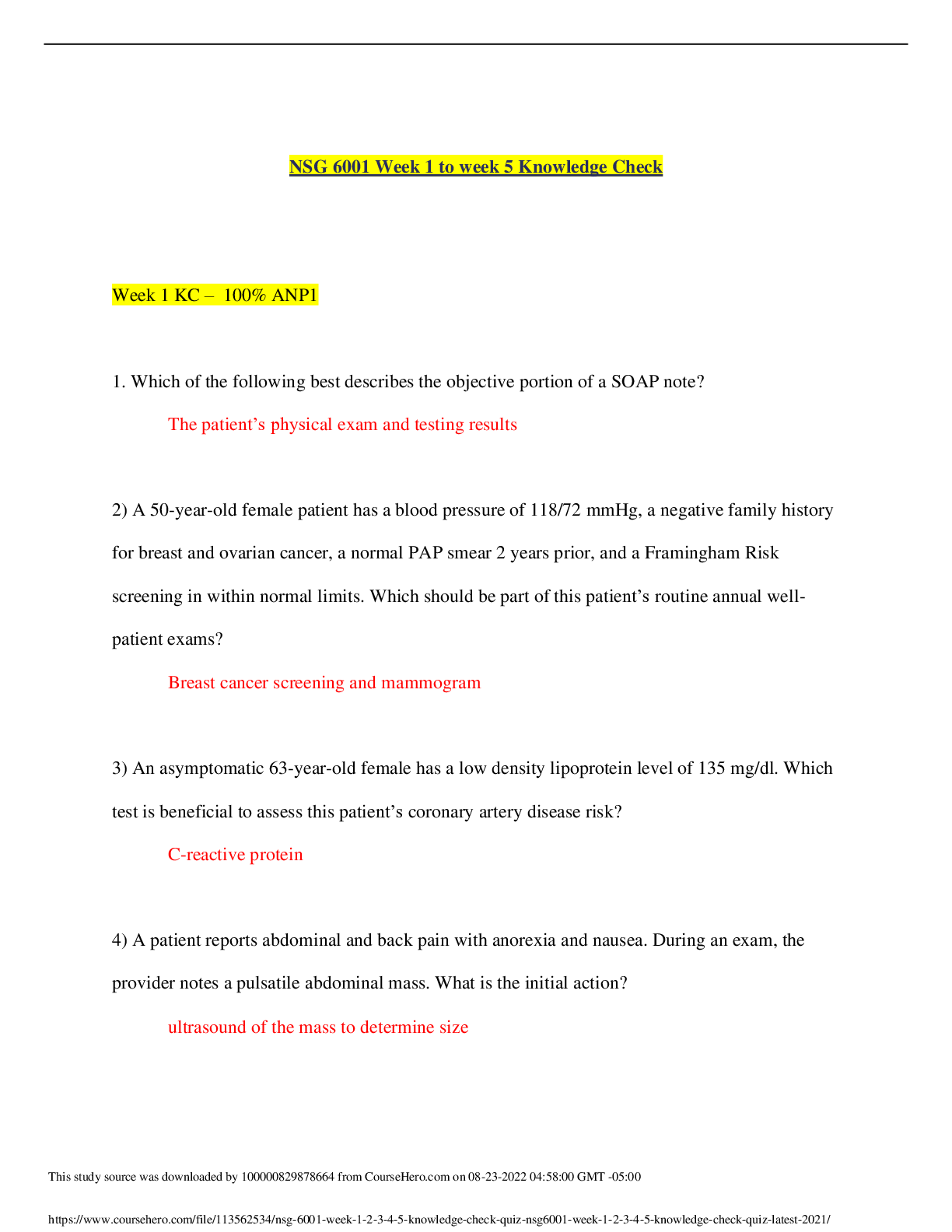
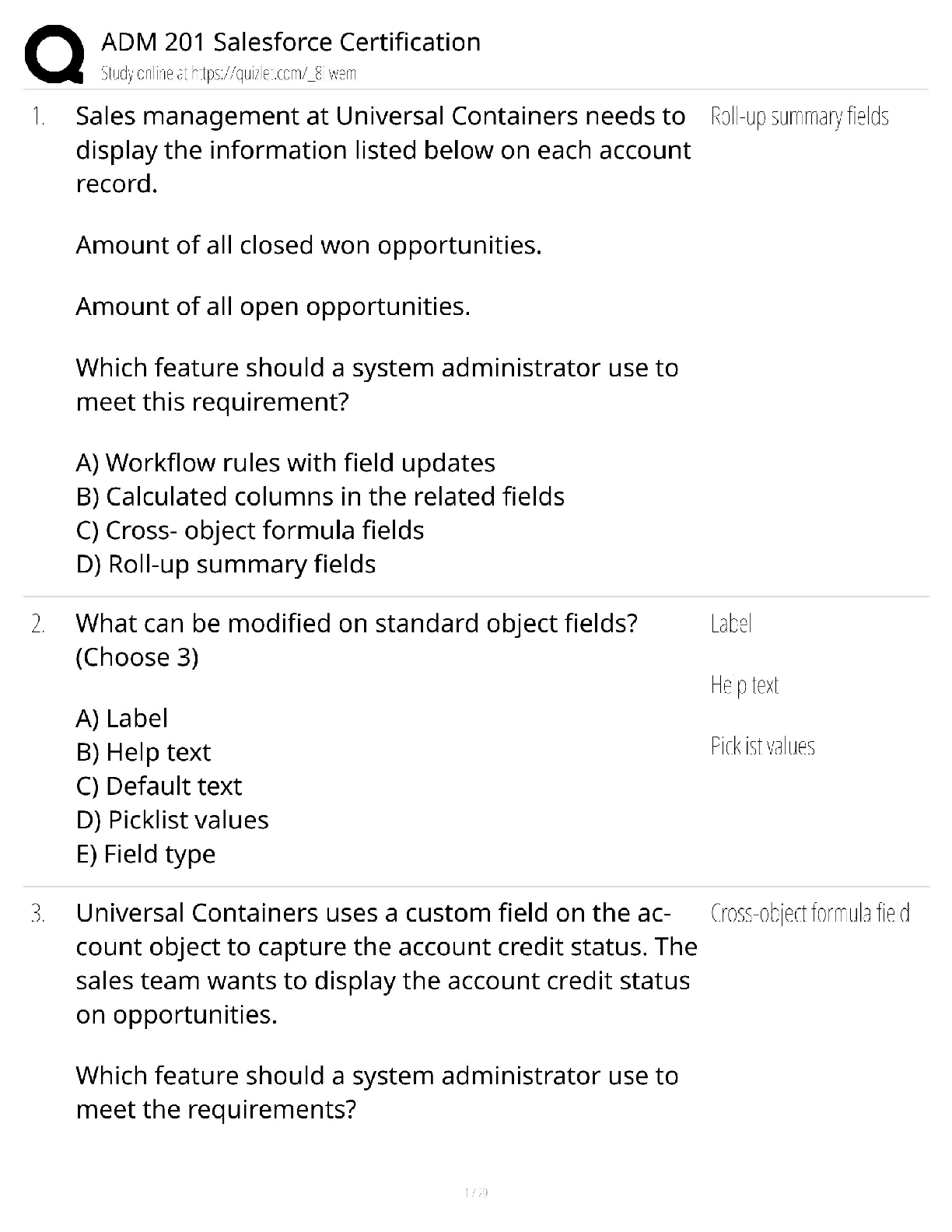
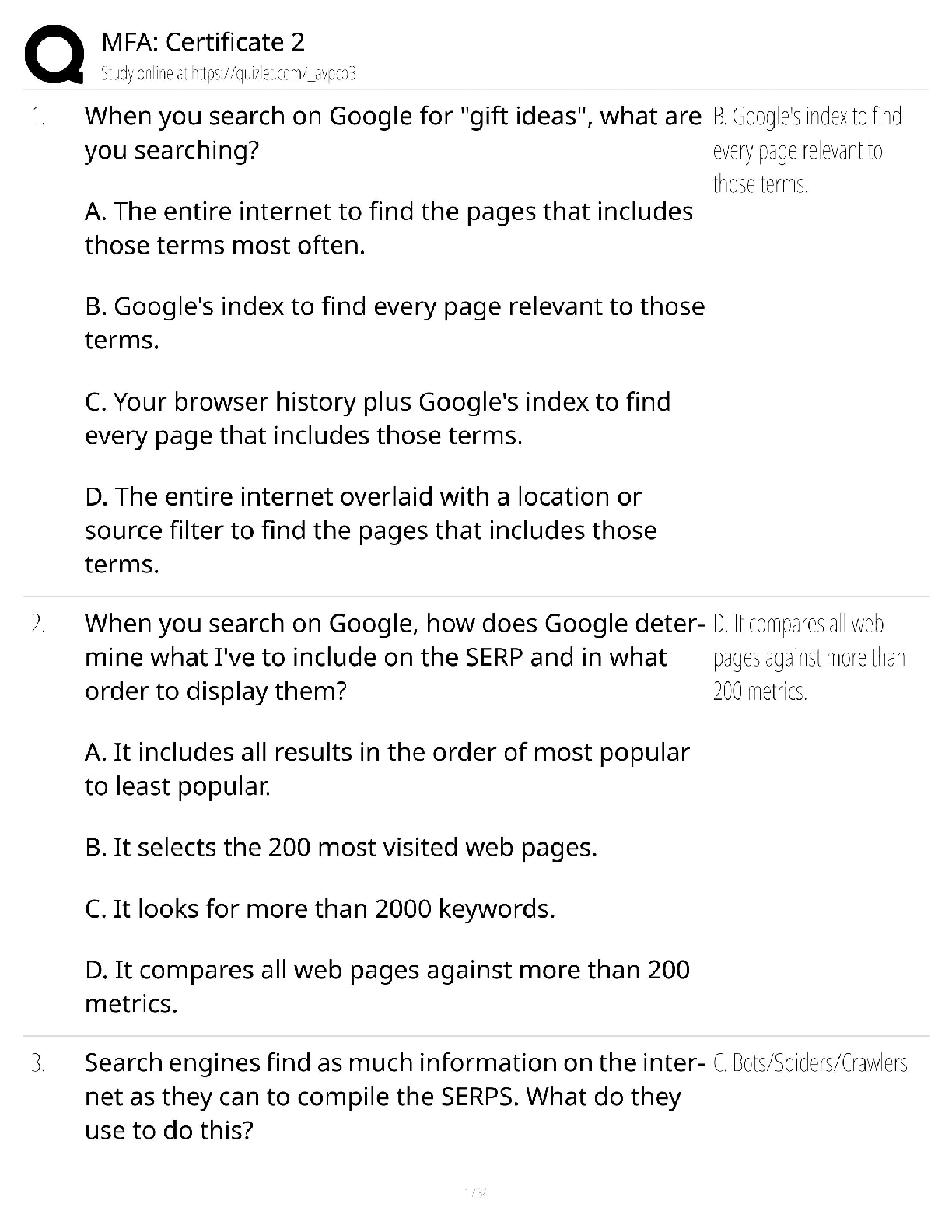
Question 1 :A security technician reports to you that a file server is experiencing unscheduled initial program loads (IPLs). Which statement BEST explains this problem? ---AnswerThe system is reboo ... ting. Because of the value of your company's data, your company has asked you to ensure data availability. You want to implement the techniques that can help to ensure data availability. Which mechanism(s) should you implement? auditing techniques data recovery techniques authentication techniques fault tolerance techniques access control techniques ---AnswerYou should implement data recovery and fault tolerance techniques to ensure data availability Question 3 :Which fault tolerant solution is the most expensive to implement? ---Answerclusters Question 4 :Your organization is implementing a new file server. You have been asked to implement a disk subsystem that is a failure-resistant disk system (FRDS). Which criterion should this system meet? ---AnswerIt protects against data loss due to disk drive failure. What is the term for RAID 1 implemented with a single hard disk controller? ---Answerdisk mirroring Question 6 :What is the term for providing fault tolerance by copying the contents of one hard drive to another? ---Answermirroring Your company has a backup solution that performs a full backup each Saturday evening and an incremental backup all other evenings. A vital system crashes on Monday morning. How many backups will need to be restored? ---Answertwo Question 8 : You need to protect data on computer networks from power spikes. What should you use? ---Answera surge suppressor Your organization implements a full/differential backup scheme. A full backup was completed two days ago. Yesterday, a differential backup was completed. Which files were backed up yesterday ---Answerall files in a backup set that were changed or created since the last full backup Question 10 :Which electronic backup solution backs up data in real time but transmits the data to an offsite facility in batches? ---Answerelectronic vaulting During the business impact analysis (BIA), the business continuity committee identifies a server that has a maximum tolerable downtime (MTD) of 48 hours. Into which maximum tolerable downtime (MTD) category should this system be placed? ---Answerimportant A critical system would need to be restored in under 24 hours. An urgent system would need to be restored within 24 hours. A normal system would need to be restored within 7 days. A nonessential system would need to be restored in 30 days. Question 12 :What is covered by the last step of a business continuity plan? ---Answerupdating the plan Question 13 :Your organization is considering leasing an off-site data center to provide facility recovery if a disaster occurs. Management wants to lease a cold site. What are some disadvantages of this type of site? expense recovery time administration time testing availability ---AnswerRecovery and testing availability Which site usually takes the longest to configure when needed? ---Answercold site Question 15 :Your organization is researching alternate computing facilities to ensure that the organization is able to function if the primary facility is destroyed. Which offsite facility is the most expensive to implement? ---Answerhot site Question 16 : You have been asked to work with a team to design your company's business continuity plan. The team has defined the scope of the business continuity plan. What is the next step? ---AnswerIdentify the key business areas. Question 17 : Which plan is written to attempt to prevent a disaster from impacting the organization and/or to lessen a disaster's impact? ---Answerbusiness continuity plan Question 18 :Which type of incident is NOT usually addressed in a contingency plan? ---Answera hurricane Question 19 :You are performing embedded device analysis on a GPS chip in a mobile phone. You perform cryptographic hashing, create checksums, and document all the evidence. Which phase of embedded device analysis are you performing? ---AnswerPreservation Question 20 :What occurs during the reconstitution phase of a recovery? ---Answeran organization transitions back to its original site OPEN Question 21 :Your organization has created an exhaustive disaster recovery plan. When should it be implemented? ---Answerwhen the company is in emergency mode Question 22 :During a recent natural disaster, the primary location for your organization was destroyed. To bring the alternate site online, you restored the most critical systems first. Now a new primary site is complete, and you need to ensure that the site is brought online in an orderly fashion. What should you do first? ---AnswerRestore the least critical functions to the new primary site. What are some of the areas for which employees must be trained so that they follow procedures when a disaster occurs? restoration procedures evacuation procedures investigation procedures communication procedures ---AnswerEmployees should be trained in restoration procedures, evacuation procedures, and communication procedures Which stipulation is usually NOT provided in an offsite vendor contract? ---Answerspecific location of the offsite facility Question 25 :While developing the business continuity plan, your team must create a plan that ensures that normal operation can be resumed in a timely manner. Which element is your team creating? ---Answerdisaster recovery plan Which business continuity plan element is primarily concerned with minimizing property damage and preventing loss of life? ---Answerdisaster recovery plan Question 27 :An earthquake damaged the building that houses your organization's data center. As a result, the alternate site in New Jersey must be configured and brought online. Which team should be responsible for this? ---Answerrestoration team Over the next weekend, your team is scheduled to perform tests that include shutting down the live site and bringing the alternate site up to full operation. Which test will be performed? ---Answerfull-interruption test Question 29 :The business continuity committee has developed the business impact analysis (BIA), identified the preventative controls that can be implemented, and developed the recovery strategies. Next, the committee should develop a contingency plan. Which teams should be included in this plan's development to aid in the execution of the final plan? restoration team damage assessment team salvage team risk management team incident response team ---AnswerThe teams that should be included in the contingency plan's development to aid in the execution of the final plan are the restoration, damage assessment, and salvage teams. Which backup facility is owned by the company and can be brought online relatively easily? ---Answerredundant site You need to ensure that all systems, networks, and major applications can be recovered. What should you create or perform? ---Answercontingency plan What is NOT an example of an operational control? ---Answera business continuity plan Question 33 :Which plan ensures that a vital corporate position is filled in the event it is vacated during a disaster? ---Answerexecutive succession plan Question 34 :Which term refers to the amount of time a company can tolerate the outage of a certain asset, entity, or service? ---Answermaximum tolerable downtime Question 35 :Which term is an estimate of the amount of time a piece of equipment will last and is usually determined by the equipment vendor or a third party? ---AnswerMTBF Mean time between failures (MTBF) is an estimate of the amount of time a piece of equipment will last and is usually determined by the equipment vendor or a third party. Question 36 :Which of the following business continuity exercises can be quite involved and should be performed annually? ---Answerdisaster simulation testing Question 37 :Recently, flooding damaged the building that houses your company's data center. Your team has been asked to determine which functions were affected by the flooding, and which functions are most critical. Which disaster recovery step are you performing? ---Answerdamage assessment According to the business continuity plan, this week your team must complete a test of specific systems to ensure their operation at alternate facilities. The results of the test must be compared with the live environment. Which test are you completing? ---Answerparallel test ___________a computer that is hacked when a malicious program is installed on it and remotely triggered ---AnswerBotnet - ________ is a software application that displays advertisements while the application is executing ---AnswerAdware - A ________ is a program that spreads itself through network connections ---AnswerWorm - _________a collection of programs that grants a hacker administrative access to a computer or network ---AnswerRootkit - Backdoor - a developer hook in a system or application that allows developers to circumvent normal authentication Logic bomb - a program that executes when a certain predefined event occurs Spyware - a program that monitors and tracks user activities Trojan horse - a program that infects a system under the guise of another legitimate program ---AnswerThe Different (4) types of malware Question 41 :Which of the following should be members of the Computer Security Incident Response Team (CSIRT)? IT department member Legal department member Public relations department member Management team member ---Answerall of the options Your organization has responded to a security incident. The breach has been contained, and all systems have been recovered. What should you do last as part of the incident response? ---Answerpost-mortem review Question 43 :Which statement is true of computer incident handling? ---AnswerInvestigation by the computer incident response team should involve a representative from the senior management. Recently, an employee of your organization made illegal copies of your organization's intellectual property. This is a direct violation of your organization's employment policies. You need to create an incident response team to investigate the crime. Who should NOT be a part of an incident response team? HR department a Public Relations department senior management Federal government Information Technology department ---Answera Public Relations department senior management Which statement is NOT a characteristic of a network-based intrusion detection system (NIDS)? ---AnswerAn NIDS analyzes encrypted information. Question 46 : Which statements regarding an audit trail are NOT true? An audit trail is a preventive control. An audit trail assists in intrusion detection. An audit trail does not record successful login attempts. An audit trail establishes accountability for access control. An audit trail is not reviewed as soon as an intrusion is detected. ---AnswerAn audit trail is a preventive control. An audit trail does not record successful login attempts. An audit trail is not reviewed as soon as an intrusion is detected. Which technologies are considered remote-sensing technologies? [Show More]
Last updated: 3 years ago
Preview 1 out of 11 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 10, 2022
Number of pages
11
Written in
All
Additional information
This document has been written for:
Uploaded
Aug 10, 2022
Downloads
0
Views
88








.png)