Information Technology > EXAM > Information Security Exam 1 | 90 Questions with 100% Correct Answers (All)
Information Security Exam 1 | 90 Questions with 100% Correct Answers
Document Content and Description Below
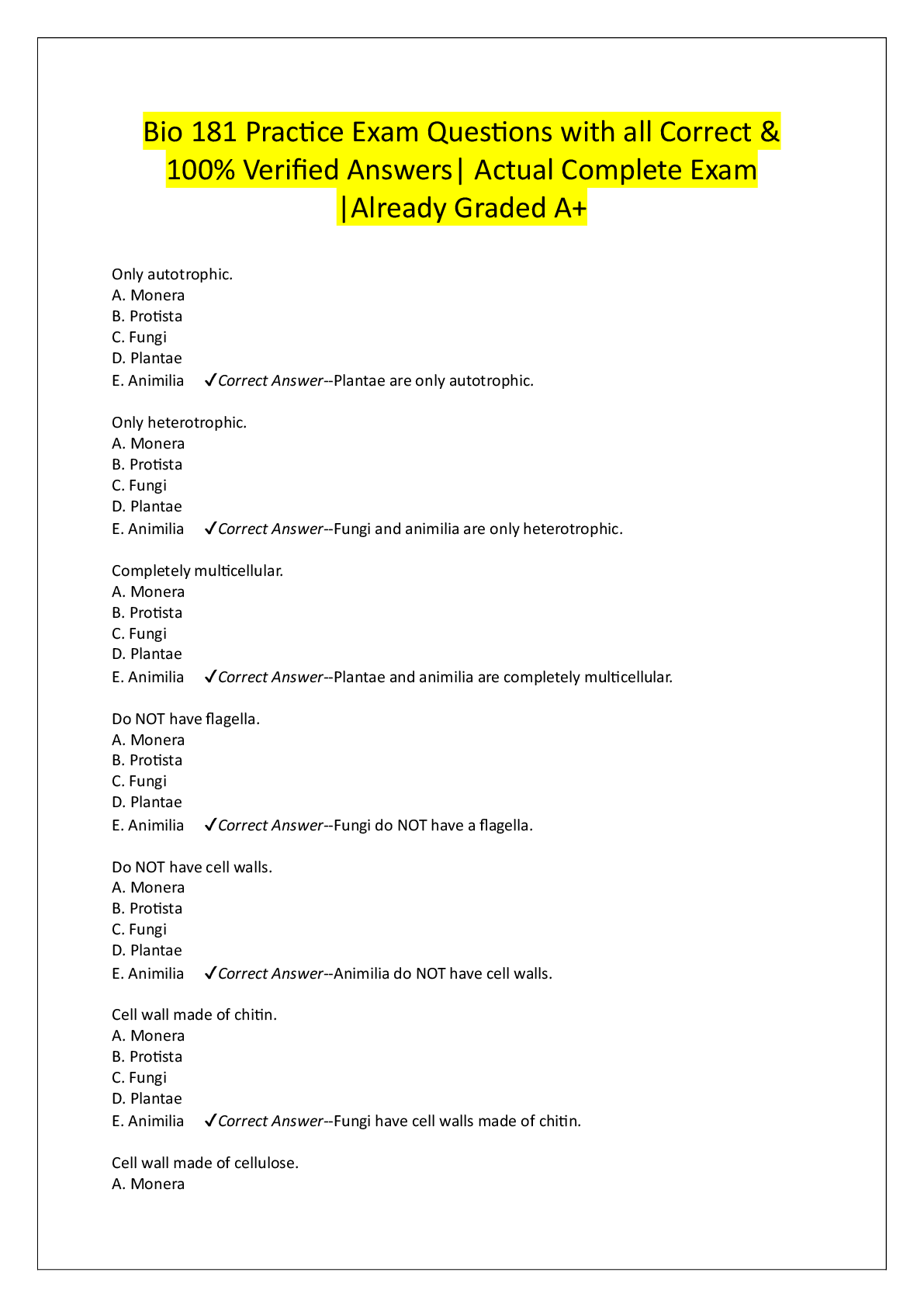
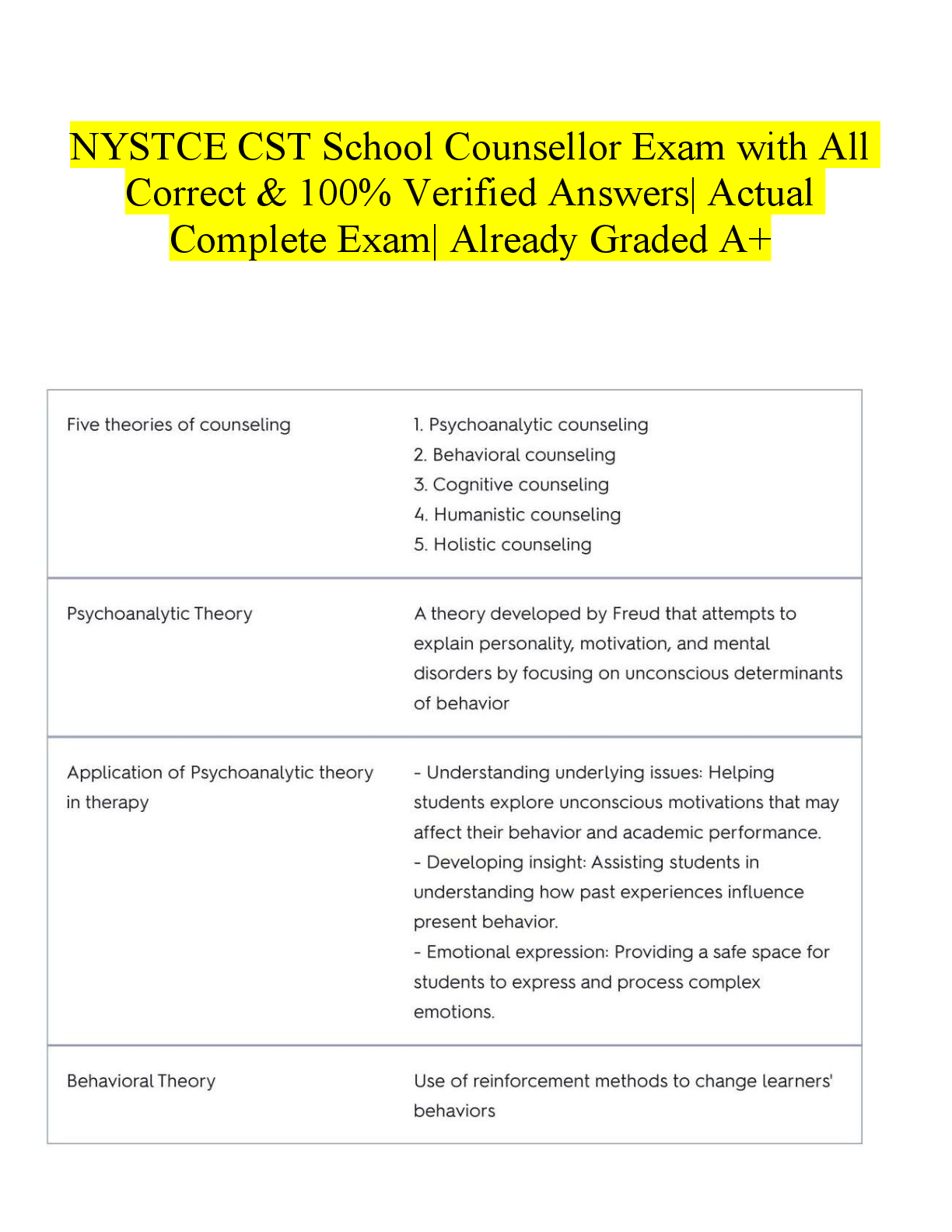
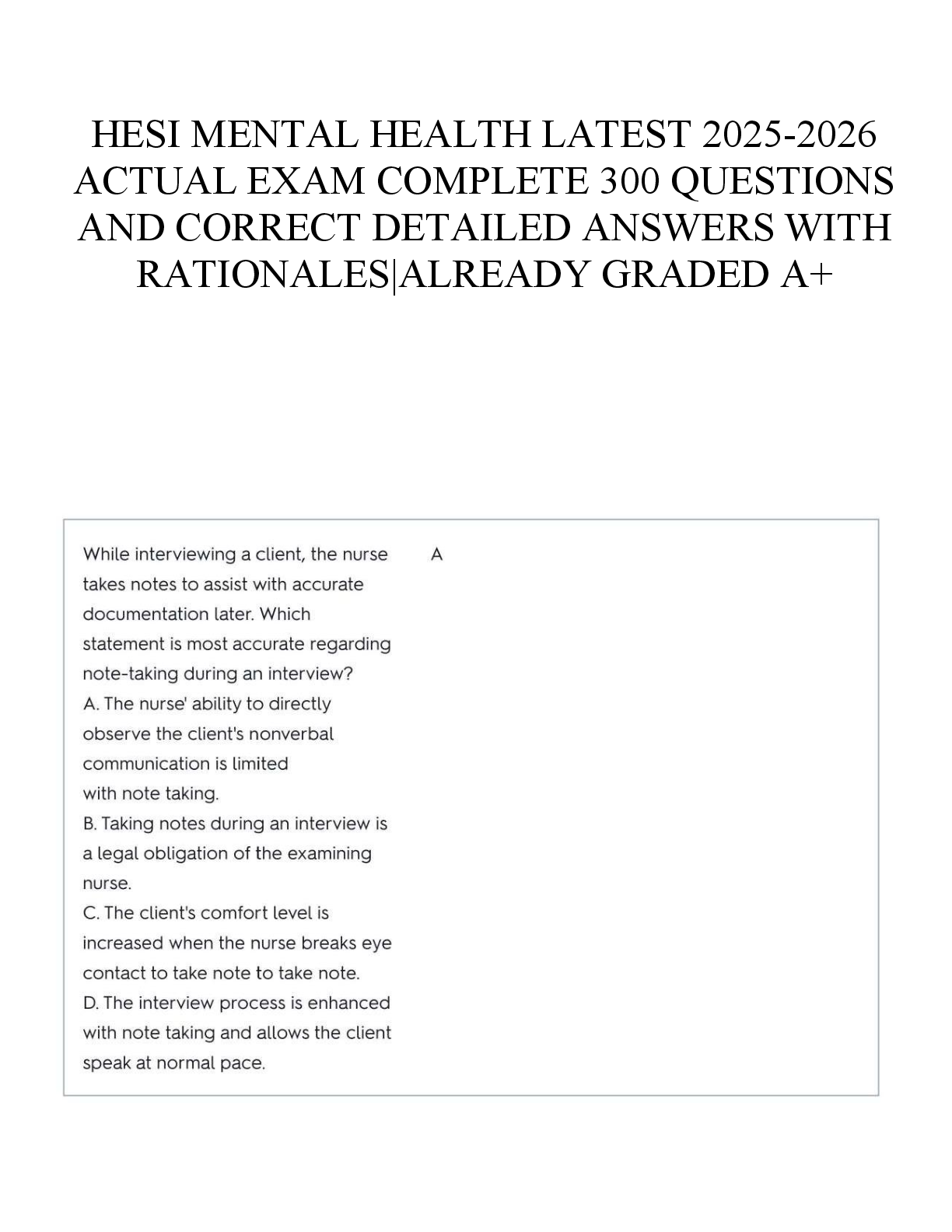
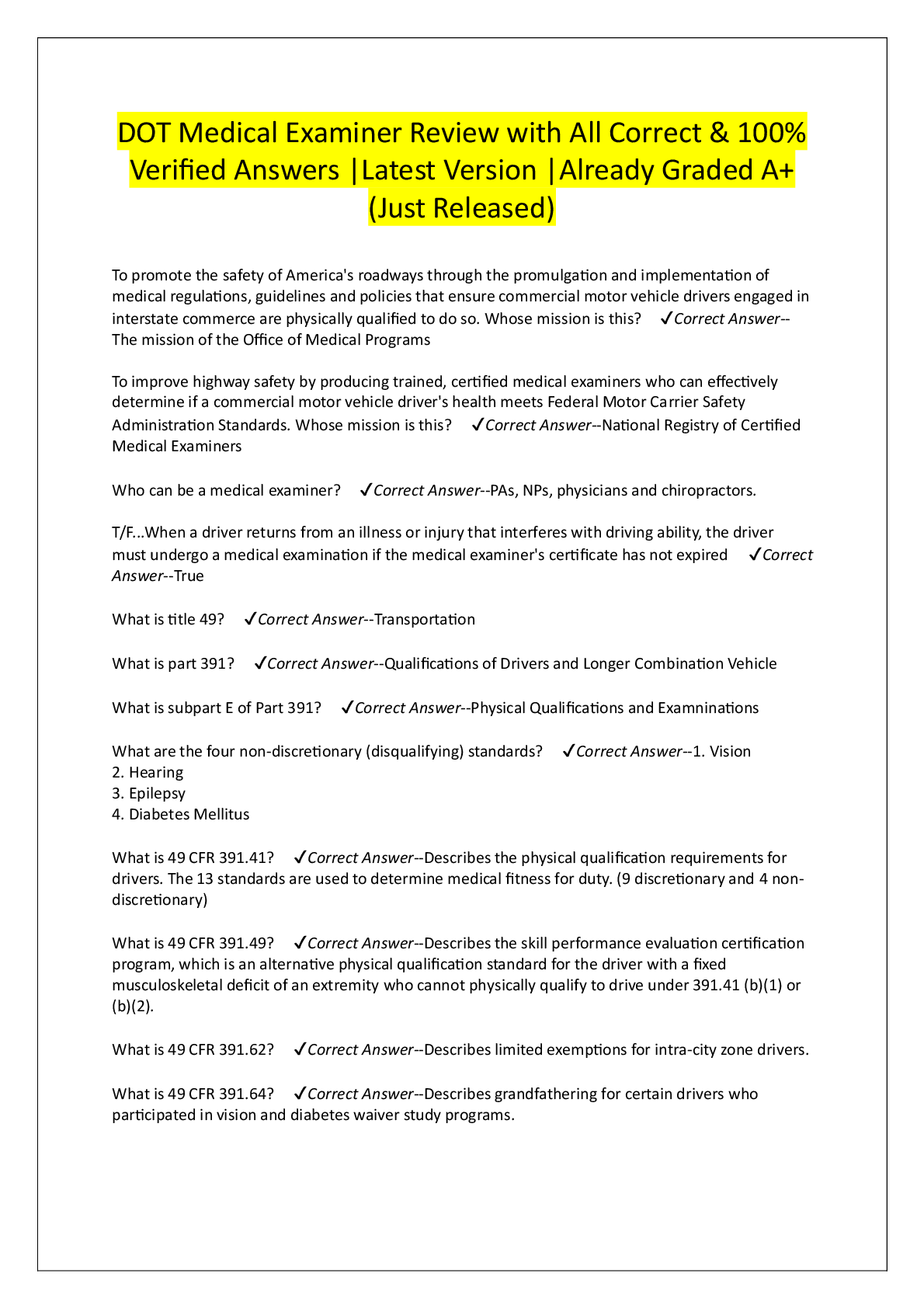
________ is the protection afforded to an automated information system in order to attain the applicable objectives of the integrity, availability, and confidentiality of information system resource ... s. - ✔✔Computer Security Confidentiality, Integrity, and Availability form what is often referred to as the _____ - ✔✔CIA Triad A loss of _________ is the disruption of access to or use of information or an information system. - ✔✔Availability In the United States, student grade information is an asset whose confidentiality is regulated by the __________. - ✔✔FERPA (Family Educational Rights and Privacy Act) A(n) _________ is a threat that is carried out and, if successful, leads to an undesirable violation of security, or threat consequence. - ✔✔Attack A(n) _________ is any means taken to deal with a security attack. - ✔✔Countermeasure Misappropriation and misuse are attacks that result in ________ threat consequence - ✔✔Usurpation The assets of a computer system can be categorized as hardware, software, communication lines and networks, and _________. - ✔✔Data Release of message contents and traffic analysis are two types of _________ attacks. - ✔✔Passive Replay, masquerade, modification of messages, and denial of service are example of _________ attacks - ✔✔Active Establishing, maintaining, and implementing plans for emergency response, backup operations, and post disaster recovery for organizational information systems to ensure the availability of critical information resources and continuity of operations in emergency situations is a __________ plan - ✔✔Contingency A(n) _________ assessment is periodically assessing the risk to organizational operations, organizational assets, and individuals, resulting from the operation of organizational information systems and the associated processing, storage, or transmission or organizational information. - ✔✔Risk [Show More]
Last updated: 3 years ago
Preview 1 out of 7 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$10.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Aug 09, 2022
Number of pages
7
Written in
All
Additional information
This document has been written for:
Uploaded
Aug 09, 2022
Downloads
0
Views
136