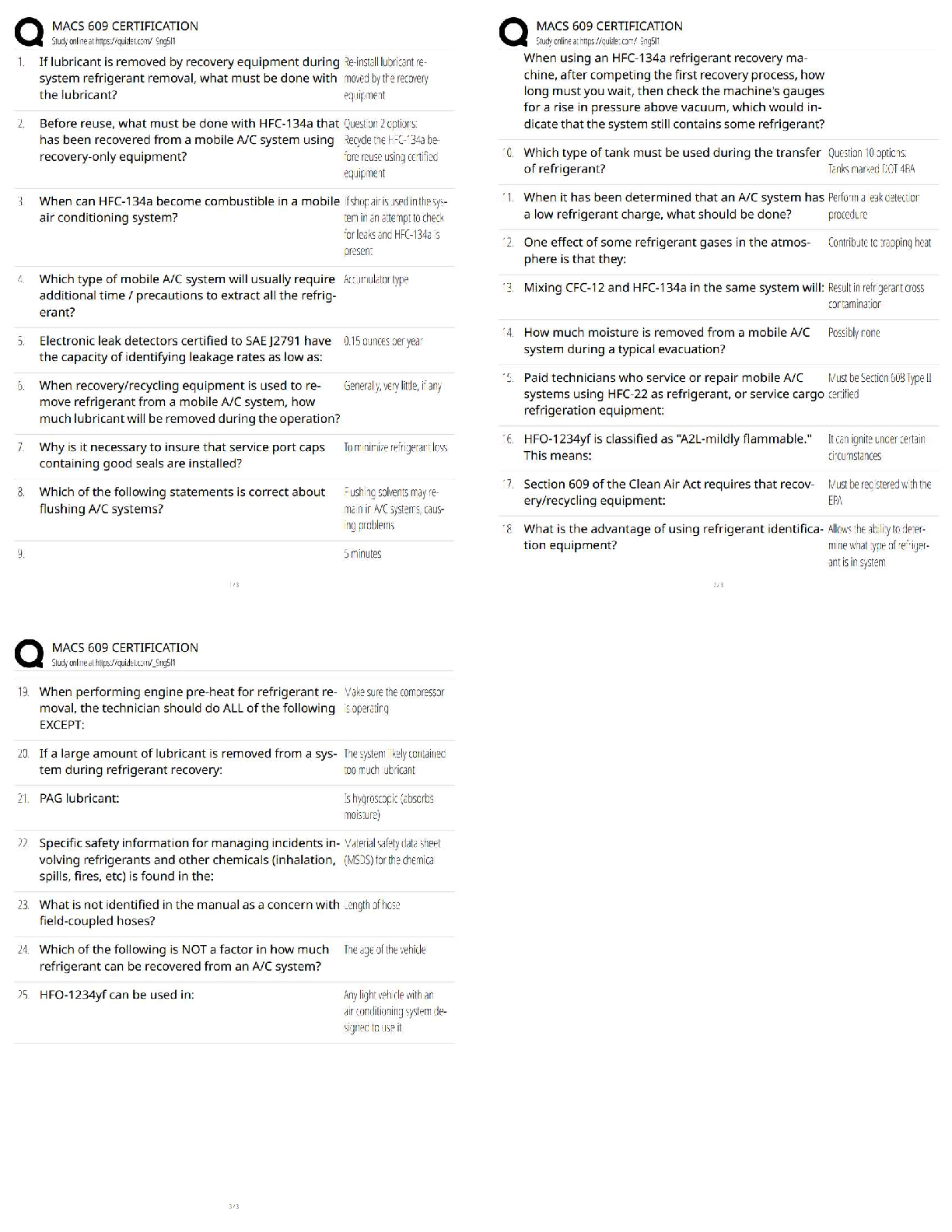
MACS 609 Certification / Score 100% / New Version / 2025 Update / Study Guide & Test Bank
$ 10.5

OCR A LEVEL JUNE 2022 FURTHER MATHS B -STATISTICS MINOR - QUESTION PAPER
Telecommunication and Information Technology > QUESTIONS & ANSWERS > University of the Cumberlands EMISS ISOL532 Telecommunications and network security. Lab 9 Assessmen (All)
QUESTION 1 1. A well-designed malicious email campaign can expect __________ responses, or click-throughs, as a legitimate commercial email campaign. far more somewhat more about the same number ... of fewer 5.00000 points QUESTION 2 1. In the scenario in the lab, Kitty Kat (KK) was able to access the Marina and Rita’s Cupcakes’ __________ via the VPN, which was set-up for Marina’s convenience to use a pre-stored password and automatic sign-in. email Facebook page Website Internet history 5.00000 points QUESTION 3 1. In the scenario in the lab, Kitty Kat (KK) was able to open the VPN and download the email of key employees after sending an email to the employees asking them to: send copies of their email history. reset their VPN passwords. delete their VPN accounts. establish new email accounts. 5.00000 points QUESTION 4 1. In the scenario in the lab, Marina and Rita’s Cupcakes used the __________, which stores copies of all emails on the server. Bitcoin account VPN password VPN protocol IMAP protocol 5.00000 points QUESTION 5 1. In the scenario in the lab, Marina neglected to use a(n) __________ on her smartphone, which meant that anyone could gain immediate access to her contacts and other private information. VPN pass key screen lock IMAP protocol 5.00000 points QUESTION 6 1. Instead of relying just on a user ID and password systems, VPN access can be protected by tokens like SecurID and other __________ methods. multi-factor authentication multi-use password uniform authentication universal password 5.00000 points QUESTION 7 1. Social engineering and reverse social engineering are used to gain access by: pretending to be a legitimate user. applying technical prowess. unleashing a brute-force attack. using outdated passwords and credentials. 5.00000 points QUESTION 8 1. The hidden part of the Internet where one can buy just about any product or service, pay in a currency called “bitcoins,” and transact business anonymously is referred to as the: spudnet. darknet. blacknet. webmark et. 5.00000 points QUESTION 9 1. What type of emails are used to either get credentials that make breaking into or using a VPN easier, or are designed to ask users to do things like send money, disclose VPN credentials, or change passwords? Spear phishing VPN phishing Password phishing Password noodling 5.00000 points QUESTION 10 1. Which of the following refers to a website that was a black market for drugs, weapons, and killers for hire? Darknet Black Road Silk Road The Club 5.00000 points QUESTION 11 1. Which of the following statements is true regarding Kitty Kat (KK) in the fictitious scenario used in the lab? KK began her work with an Internet search to find information about the target company and its owners. KK obtained the employees’ travel itinerary from the article in Cincinnati Journal. KK and her accomplices did not commit any type of crime at the airport. KK’s efforts were unsuccessful at obtaining valuable information about the target company. 5.00000 points QUESTION 12 1. Which of the following statements is true regarding a properly configured Virtual Private Network (VPN) that uses IPSec and adheres closely to best practices, such as strong authentication, network segmentation, device validation, posture assessment, etc.? This VPN will not protect information while it is in transit from one location to the other. Actually “breaking” into a VPN tunnel such as this one will take significant technical prowess. This VPN security will be impenetrable by less technically savvy cybercriminals, hackers, and others. This VPN will be immune to social engineering and reverse social engineering techniques. 5.00000 points QUESTION 13 1. Which of the following statements is true regarding creating a successful spam email campaign? The sender’s identity has to be a person or entity that is unknown or unfamiliar to the recipient. Most spam campaigns use an actual sender email address, rather than a temporary one. The decision to use a real or false sender address depends on whether or not the spammer wishes the recipient to ultimately delete the email. When the sender is a known contact of the target, using the sender’s actual email address increases the appearance that the email is proper. 5.00000 points QUESTION 14 1. Which of the following statements is true regarding phishing? Phishing emails are spam emails that rely on the recipient remaining passive and inactive. Phishing emails that are general in nature, rather than targeted to a specific audience, are called spear phishing emails. Spear phishing emails use social engineering techniques to appeal to the target. Neither phishing nor spear phishing emails are very effective. 5.00000 points QUESTION 15 1. Which of the following statements is true regarding social engineering? Social engineering is when an attacker attempts to take advantage of a weakness in a network, device, or application. Security professionals consider social engineering a highly sophisticated “technical” form of attack. Social engineering will never be as effective as a traditional technical attack. Hackers, cybercriminals, or cyberterrorists often save time and achieve what they could not otherwise by simply asking. 5.00000 points QUESTION 16 1. Which of the following statements is true regarding spam emails? Regardless of the purpose of the campaign, there is only a single type of spam email that can be sent. A good spam email can be considered a valid part of a legitimate marketing campaign. The effectiveness of a spam email has nothing to do with the relationship between the sender and receiver. A spam email can be part of a larger campaign of deception, or it can be the entire campaign. 5.00000 points QUESTION 17 1. Which of the following statements is true regarding the body (or content) of a spam email? The body of the email is generally not very important to the effectiveness of a spam email campaign. The body of the email depends entirely on the objectives and goals of the recipient. If the intent of the campaign is to verify that the email account is active, the recipient only has to open the email, not read the content. If the intent of the campaign is to encourage the recipient to do something, then the body is not very important. 5.00000 points QUESTION 18 1. Which of the following statements is true regarding the emails that were collected from Marina and Rita’s Cupcakes’ key employees? The emails were password protected and unable to be read. The emails included very little useful information. The emails included only personal information such as information about relationships and gossip. The emails included both professional and personal information that could be exploited. 5.00000 points QUESTION 19 1. Which of the following steps can make VPN access more secure? Assure Perfect Forward Secrecy during IKE key exchange. Allow access only from specific MAC addresses and specific MAC/IP address pairs. Use foreign words as passwords. Change password letters to numbers, such as all Ls to 7s and all Os to 0s. 5.00000 points QUESTION 20 1. Which of the following strengthens access procedures and makes a VPN more secure? Make sure that all parameters for the VPN are identical, regardless of the type of information being protected. Make sure that all parameters for the VPN are applied uniformly. Make sure that configuration procedures are not reviewed or changed once they are in place. Do not use devices that generate one-time use passwords or parts of passwords [Show More]
Last updated: 3 years ago
Preview 1 out of 6 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:


University of the Cumberlands EMISS ISOL532 Telecommunications and network security. Chapter 1 and 2 Exam. 30 Q&A University of the Cumberlands EMISS ISOL532 Telecommunications and network security...
By Kirsch 3 years ago
$69
23
Can't find what you want? Try our AI powered Search
Connected school, study & course
About the document
Uploaded On
Aug 09, 2022
Number of pages
6
Written in
All
This document has been written for:
Uploaded
Aug 09, 2022
Downloads
0
Views
133
Scholarfriends.com Online Platform by Browsegrades Inc. 651N South Broad St, Middletown DE. United States.
We're available through e-mail, Twitter, Facebook, and live chat.
FAQ
Questions? Leave a message!
Copyright © Scholarfriends · High quality services·