Computer Science > EXAM > CEH Master 2022 EXAM QUESTIONS AND ANSWERS| GRADED A+ (All)
CEH Master 2022 EXAM QUESTIONS AND ANSWERS| GRADED A+
Document Content and Description Below
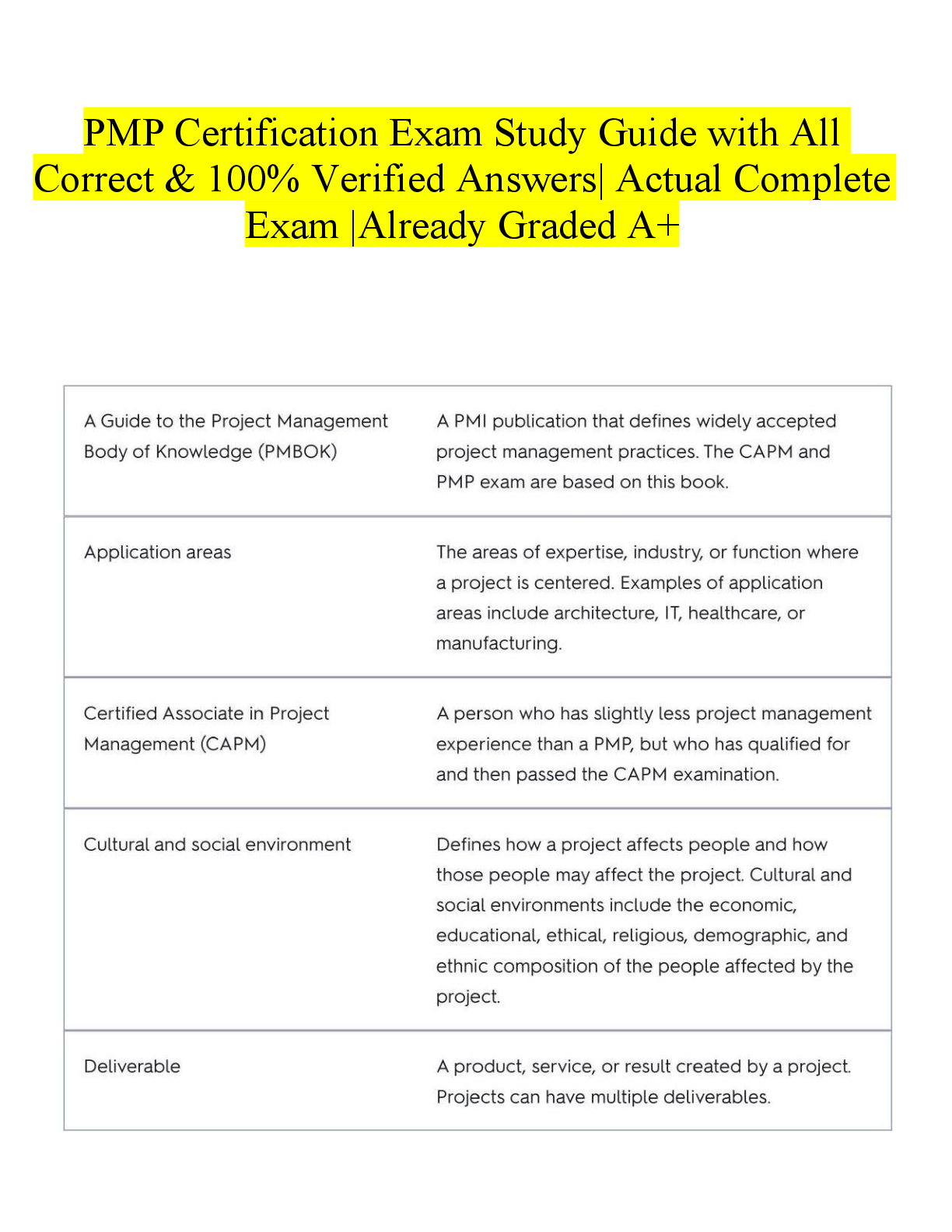
CEH Master 2022 EXAM ISO 27001 Correct Answer: Considered the Governance standard, based on BS 7799. Defines a standard for creating an IS Management System. Focuses on Security Governance. ... ISO 27002 Correct Answer: Considered the security controls standard, based on BS 7799. Recommends security controls based on industry best practices Focuses on Security Objectives Cain & Able can do....? Correct Answer: record and extract VOIP conversations Capture/decrypt RDP traffic Collect and prepare server certs for MITM attacks Perform ARP poisoning start/stop/pause/continue remote windows services detect 802.11 WLANs reveal passwords in text boxes enumerate netwoks and extract SIDs Retinal Scan Correct Answer: Most likely to reveal private health info about a user and considered to be invasive Windows XP and 7 respond to pings sent to network or broadcast addresses by default? Correct Answer: NO. Windows "NET" command can do...? Correct Answer: manage services manage user accounts connect to a remote resource manage a printer que manage a shared resource Metamorphic virus Correct Answer: Rewrites itself every time they infect a new file Microsoft Secure Development Lifecycle Correct Answer: 1. Training 2. Requirements 3. Design 4. Implementation 5. Verification 6. Release 7. Response HTTP PUT method should be considered a RISK Correct Answer: Allows clients to update files on a webserver Worms and BOTs can propagate without human interaction Correct Answer: What tool do you use to perform Blackjacking? Correct Answer: BBProxy Known plaintext attack Correct Answer: Attack has both plaintext and cipher text COBIT (Control Objects for Information Related Technology) Correct Answer: Four domains: -Planning and Organization -Acquisition and implementation -Delivery and support -Monitoring and Evaluation ITIL Correct Answer: Developed by CCTA for UK Gov ITIL Standardizes IT management procedures Five main categories -Service strategy -Service design -Service transition -Service operation -Continual service improvement Windows NT 4.0 SP4 uses _____ for hashing Correct Answer: MD5 Kismet Correct Answer: Runs on Linux and OS X Supports monitor mode and 802.11n Can be used as an IDS NetSumbler Correct Answer: Can only be installed on windows Does not detect 802.11n detects 802.11a,b,g does not support monitor mode ARP spoofing takes advantage of _________ relationship Correct Answer: TRUST SC Query only shows ________ services on a windows machine Correct Answer: ACTIVE 802.1X uses ____________ to establish port-based network access control Correct Answer: EAP (Extensible Authentication Protocol) Directive security control Correct Answer: AKA procedural controls used to define appropriate use & behavoir Deterrent security control Correct Answer: Used to dissuade or deter attacks Preventative security control Correct Answer: Used to stop attacks by preventing users from performing specific actions Compensating security control Correct Answer: Used to supplement directive controls Detective security control Correct Answer: Used to monitor and/or send alerts about activity Corrective Correct Answer: Used to repair damage caused by malicious events Recovery Correct Answer: Used to restore system to a normal state after attack Application firewalls (what layer?) Correct Answer: Operate at layer 7 Circuit firewalls (what layer?) Correct Answer: Operate at layer 5 Packet filter firewall (what layer?) Correct Answer: Operate at layer 3 Stateful multilayer firewall Correct Answer: Combine quality of all other firewalls Operate at multiple layers Hinfo shows what? (DNS record) Correct Answer: CPU type OS Type OSSTMM defines three types of compliance.... Correct Answer: Legislative (SOX, HIPPA) Contractual (PCI) Standards-based (ITIL, ISO, OSSTM) WPA uses _________ to ensure integrity & protect against MITM attacks? Correct Answer: MIC (Message Integrity Checks) Metagoofil switches Correct Answer: -f writes all links to a date-time stamped file -t recognizes all which will search all 17576 three letter file extensions -e allows you to specify time delay between searches -r specifies the number of threads to use when downloading files PCI DSS Requirement 11 requires an organization does? Correct Answer: "Regularly test systems and processes" aka perform vulnerability assessments WPA2 uses _______ cipher instead of ________ cipher. Correct Answer: Uses block cipher instead of stream cipher What is libwhisker? Correct Answer: Pearl module that supports IDS evasion Nikto uses libwhisker OWASP 2013 Top 6 Correct Answer: 1. Injections 2. Broken Auth 3. XSS 4. Insecure Direct Object References 5. Security misconfig 6. Sensitive Data Exposure ESP is used with what? Correct Answer: IPSec uses ESP during tunneling mode; it encrypts the entire packet; aka TUNNEL MODE [Show More]
Last updated: 3 years ago
Preview 1 out of 48 pages

Buy this document to get the full access instantly
Instant Download Access after purchase
Buy NowInstant download
We Accept:

Reviews( 0 )
$14.00
Can't find what you want? Try our AI powered Search
Document information
Connected school, study & course
About the document
Uploaded On
Jul 14, 2022
Number of pages
48
Written in
All
Additional information
This document has been written for:
Uploaded
Jul 14, 2022
Downloads
0
Views
493