EXAM 3 BCIS 3610 UNT
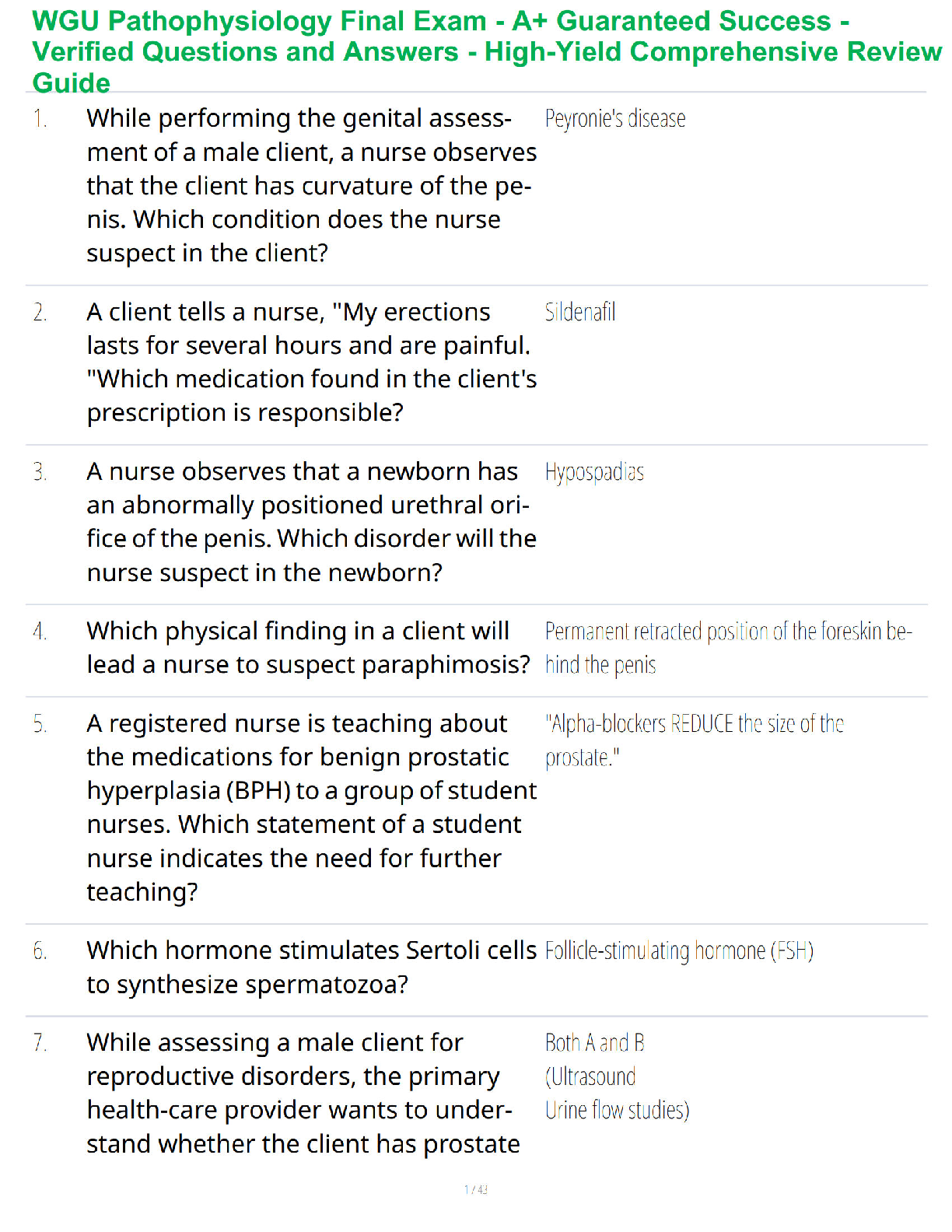
The more attributes there are in a sample data, the easier it is to build a model that fits the sample
data, but that is worthless as a predictor. Which of the following best explains this phenomen
...
EXAM 3 BCIS 3610 UNT
The more attributes there are in a sample data, the easier it is to build a model that fits the sample
data, but that is worthless as a predictor. Which of the following best explains this phenomenon?
- ✔✔the curse of dimensionality
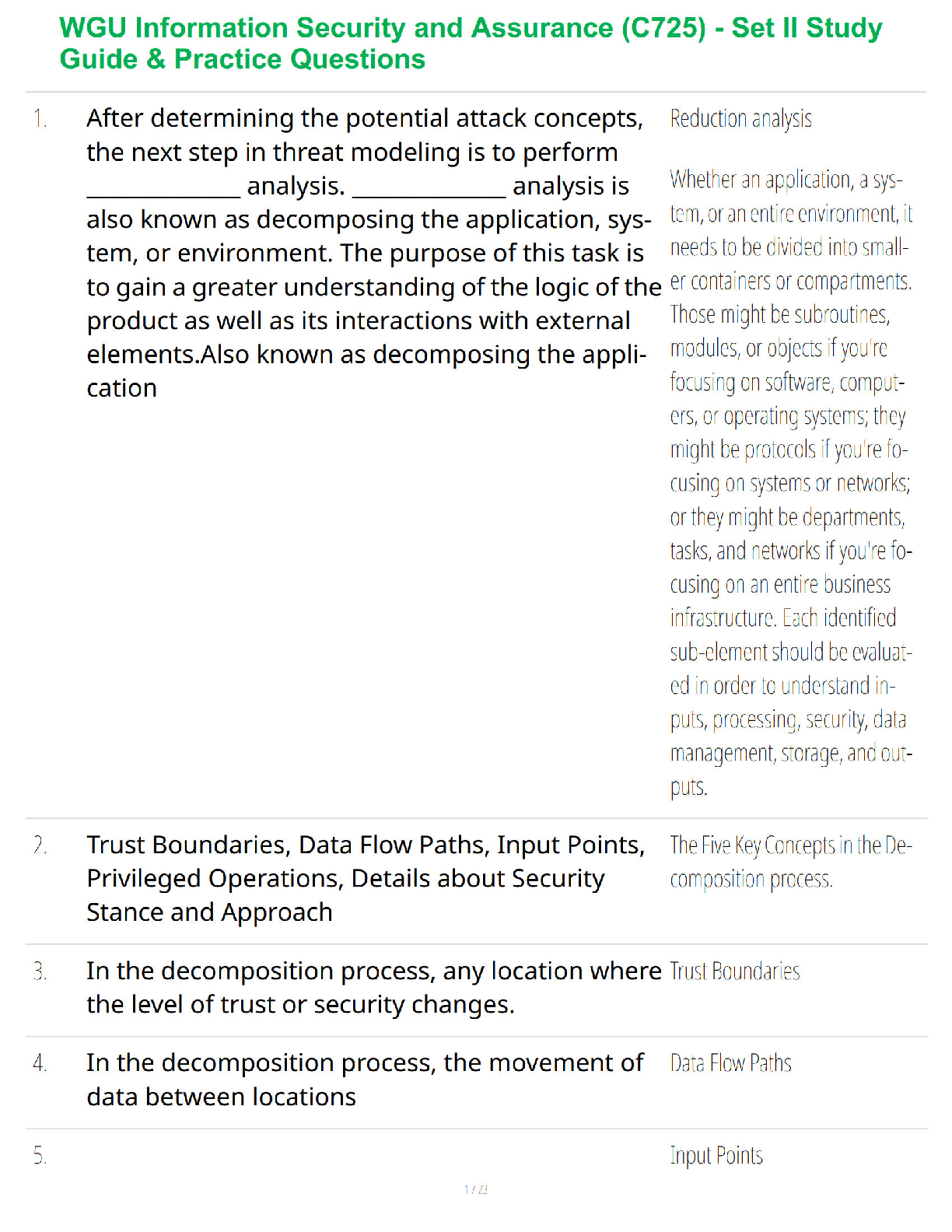
In the ________ phase, a BigData collection is broken into pieces and hundreds or thousands of
independent processors search these pieces for something of interest. - ✔✔map
________ refers to the level of detail represented by data. - ✔✔Granularity
What is the query language used in Hadoop? - ✔✔Pig
Which BI activity would a company be participating in if they were cataloging? - ✔✔data
acquisition
A ________ is a facility for managing an organization's business intelligence data. - ✔✔data
warehouse
Problematic data are termed ________. - ✔✔dirty data
The results generated in the map phase are combined in the ________ phase. - ✔✔reduce
Which of the following refers to data in the form of rows and columns? - ✔✔structured data
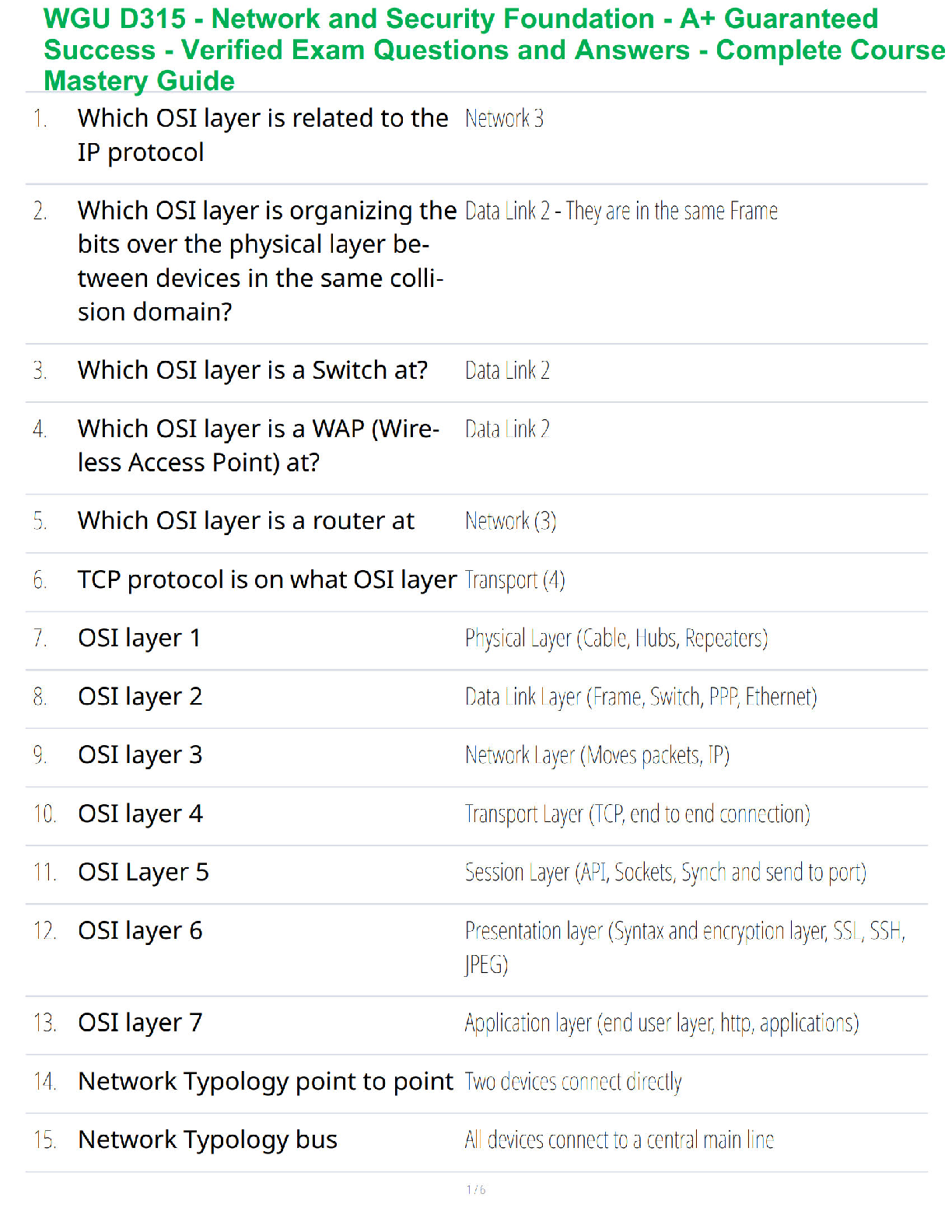
A person calls the Stark residence and pretends to represent a credit card company. He asks Mrs.
Stark to confirm her credit card number. This is an example of ________. - ✔✔pretexting
________ is a broad category of software that includes viruses, worms, Trojan horses, spyware,
and adware. - ✔✔Malware
The _________ can delete programs or data or even modify data in undetected ways. -
✔✔payload
Jack installed the incorrect security patch on the server. This is an example of what type of
security problem? - ✔✔faulty service
________ take computers with wireless connections through an area and search for unprotected
wireless networks. - ✔✔Wardrivers
The procedure of entrusting a party with a copy of an encryption key that can be used in case the
actual key is lost or destroyed is called ________. - ✔✔key escrow
A(n) ________ is a computer program that senses when another computer is attempting to scan a
disk or access a computer. - ✔✔intrusion detection system
The Grey-Sloan hospital was attached by a virus. The interns should check the ________ for
next steps. - ✔✔incident-response plan
________ are created by companies as false targets for computer criminals to attack. -
✔✔Honeypots
A(n) ________ is a measure that individuals or organizations take to block a threat from
obtaining an asset. - ✔✔safeguard
If a company's information systems (IS) related programs are not developed in-house, then the
development group of the IS department will be staffed primarily by ________. - ✔✔systems
analysts
In organizations that operate significant nonaccounting information systems, such as
manufacturers, a reporting arrangement wherein the chief information officer reports to the
________ is more common and effective. - ✔✔chief executive officer
In order to accomplish organizational goals and objectives, an organization's information
systems (IS) must be aligned with its ________. - ✔✔competitive strategy
A ________ monitors, maintains, fixes, and tunes computer networks. - ✔✔network
administrator
An organization that wishes to leverage the power of social media and elastic cloud opportunities
to help accomplish its goals and objectives should ideally turn to the ________ group within its
IT department for information. - ✔✔technology
Which of the following is a right of a user of information systems (IS)? - ✔✔contributing to
requirements for new system features and functions
________ refers to the leasing of hardware with preinstalled operating systems. - ✔✔Platform as
a service (PaaS)
Which of the following is a responsibility of an information systems (IS) user? - ✔✔following
security and backup procedures
The ________ evaluates new technologies, new ideas, and new capabilities and identifies those
that are most relevant to the organization. - ✔✔chief technology officer
Which of the following is a responsibility of a systems analyst? - ✔✔determining system
requirements
Which of the following statements is TRUE of systems development? - ✔✔It requires business
knowledge and an understanding of group dynamics.
Projects are said to be in analysis paralysis if so much time is spent ________. -
✔✔documenting the requirements
During design and implementation, a development team will be heavy with ________. -
✔✔programmers
Which of the following is a major concern for developers in a systems development life cycle
process? - ✔✔performing repetitive tasks of a completed phase
In a ________ installation, a new system runs alongside the old one until the new one has been
tested and is fully operational. - ✔✔parallel
The process of creating and maintaining information systems is called ________. - ✔✔systems
development
Procedures for a business information system are designed usually by ________. - ✔✔systems
analysts
Which of the following styles of system conversion shuts off the old system and starts a new
system? - ✔✔plunge installation
The first major task of the project team is to ________. - ✔✔plan the project
Which of the following is a fundamental category of business intelligence (BI) analysis? -
✔✔reporting
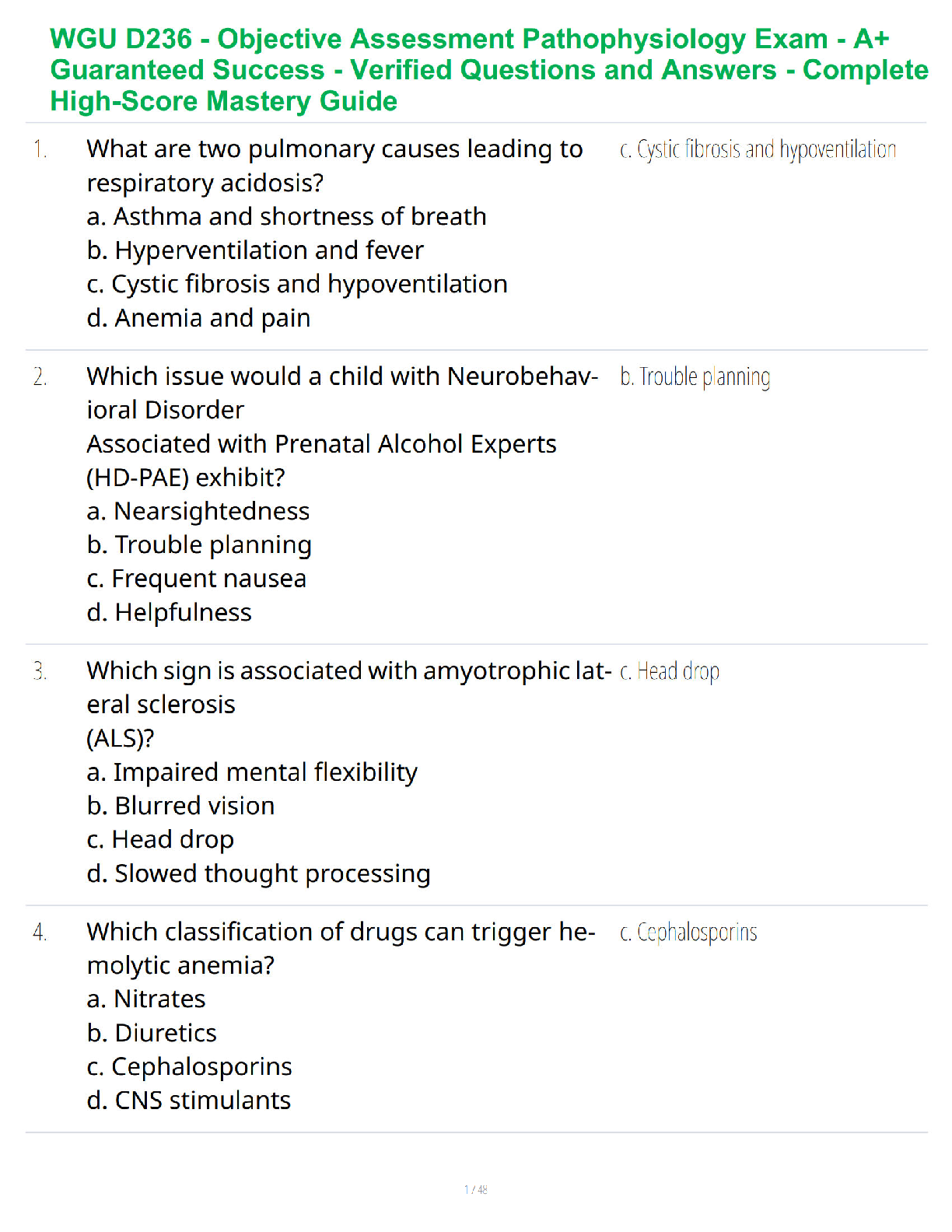
Which of the following problems is particularly common for data that have been gathered over
time? - ✔✔lack of consistency
Which of the following statements is TRUE of a data warehouse? - ✔✔A data warehouse is
larger than a data mart.
Which of the following statements is TRUE of unsupervised data mining? - ✔✔Analysts create
hypotheses only after performing an analysis.
In the ________ phase, a BigData collection is broken into pieces and hundreds or thousands of
independent processors search these pieces for something of interest. - ✔✔map
Which of the following occurs when millions of bogus service requests flood a Web server and
prevent it from servicing legitimate requests? - ✔✔denial of service
A(n) ________ examines the source address, destination address, and other data of a message
and determines whether to let that message pass. - ✔✔packet-filtering firewall
The _________ can delete programs or data or even modify data in undetected ways. -
✔✔payload
The Grey-Sloan hospital was attached by a virus. The interns should check the ________ for
next steps. - ✔✔incident-response plan
Which of the following is TRUE if the development group of a company's information systems
(IS) department is staffed primarily by programmers, test engineers, technical writers, and other
development personnel? - ✔✔The company develops programs in-house.
Which of the following is a responsibility of a systems analyst? - ✔✔determining system
requirements
Which of the following is TRUE of the alignment between information systems and
organizational strategies? - ✔✔Information systems must evolve with changes made in
organizational strategies.
Which of the following is an advantage of outsourcing information systems? - ✔✔It can be an
easy way to gain expertise otherwise not known.
Which of the following is a risk of outsourcing information systems? - ✔✔Vendors can gain
access to critical knowledge of the outsourcing company.
Which of the following statements is TRUE of systems development? - ✔✔It requires business
knowledge and an understanding of group dynamics.
According to Brooks' Law, which of the following is a consequence of adding more people to
late projects? - ✔✔The costs of training new people can overwhelm the benefits of their
contribution.
In the ________ phase of the systems development life cycle, developers use management's
statement of the system needs in order to develop a new information system. - ✔✔system
definition
Which of the following statements is TRUE of the composition of a development team over the
different phases of the systems development life cycle? - ✔✔During integrated testing and
conversion, the team will be augmented with business users.
During the ________ phase of the systems development life cycle process, developers construct,
install, and test the components of the information system. - ✔✔implementation
The budget was tight when the project entered the testing phase so Bob decided to implement the
________ for the new system. It was a disaster because the customer service agents could not log
in to their accounts. So the testing team had to come and reinstall the old system. - ✔✔plunge
installation method
[Show More]






.png)