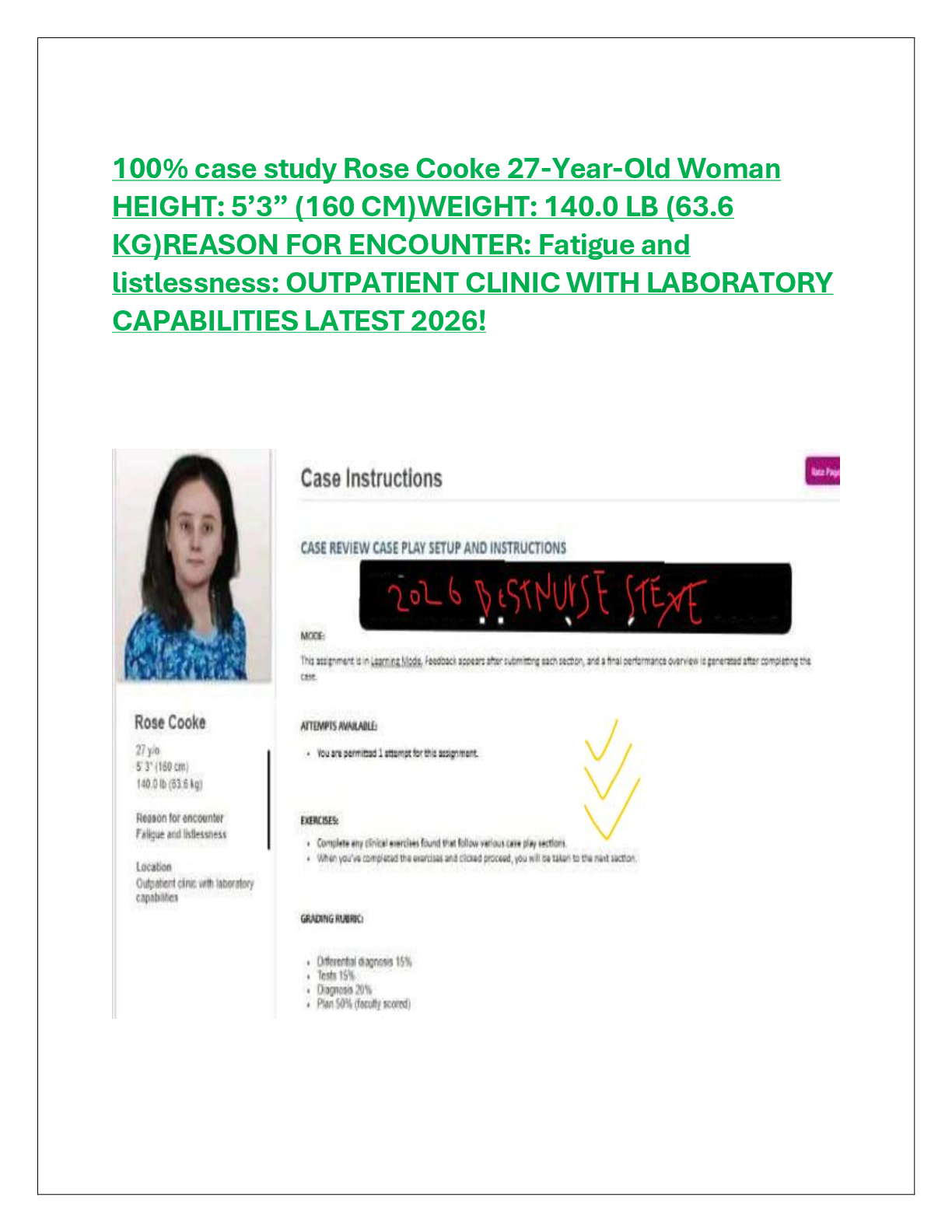
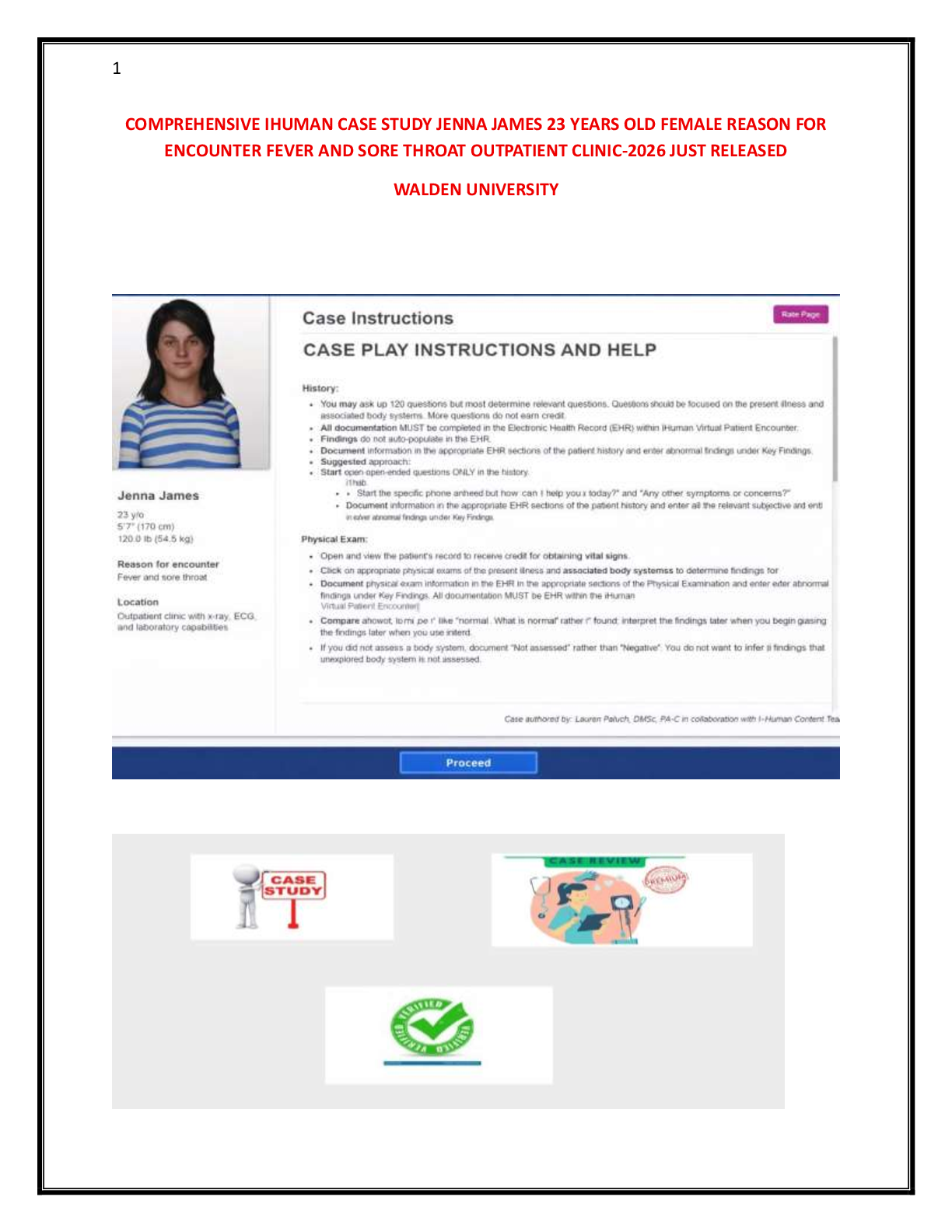
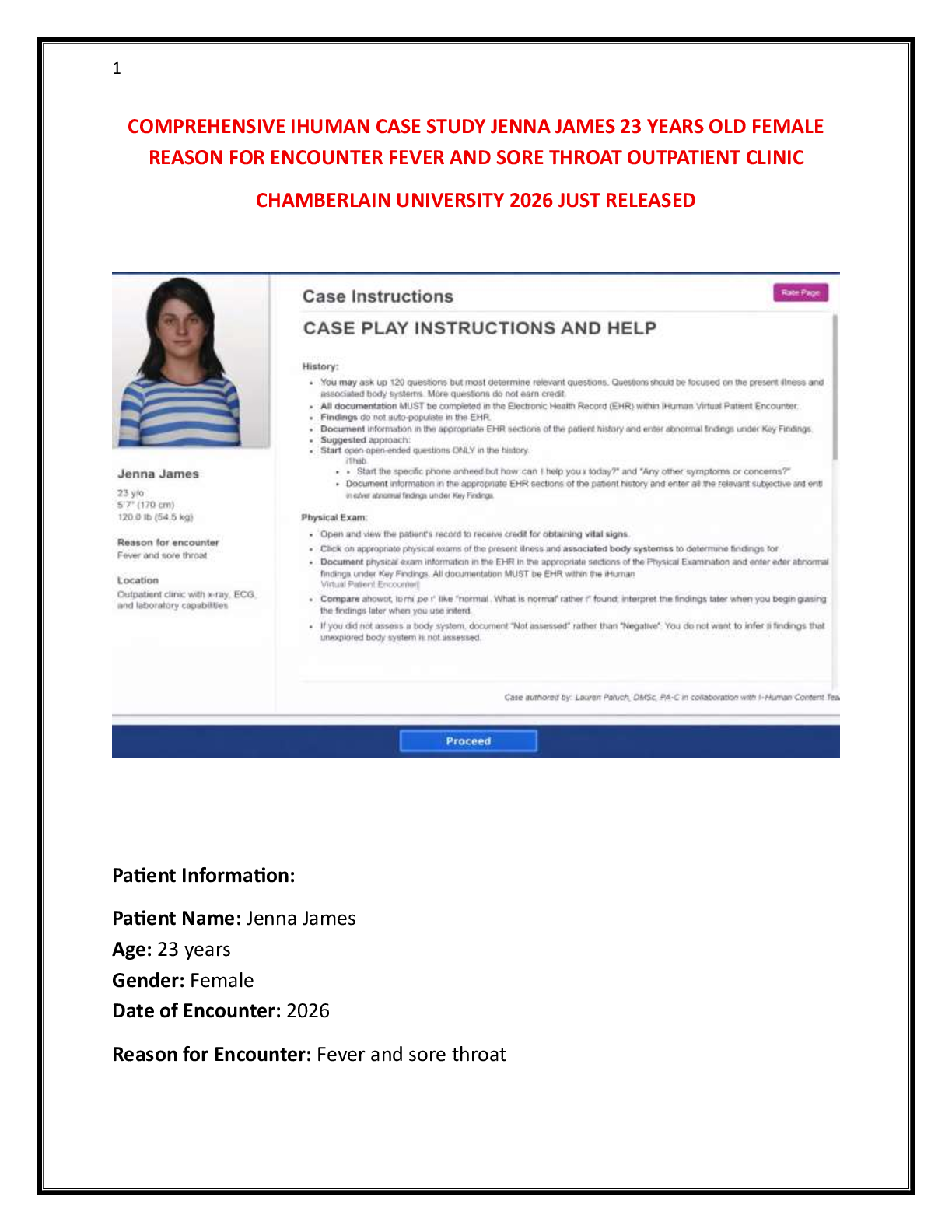
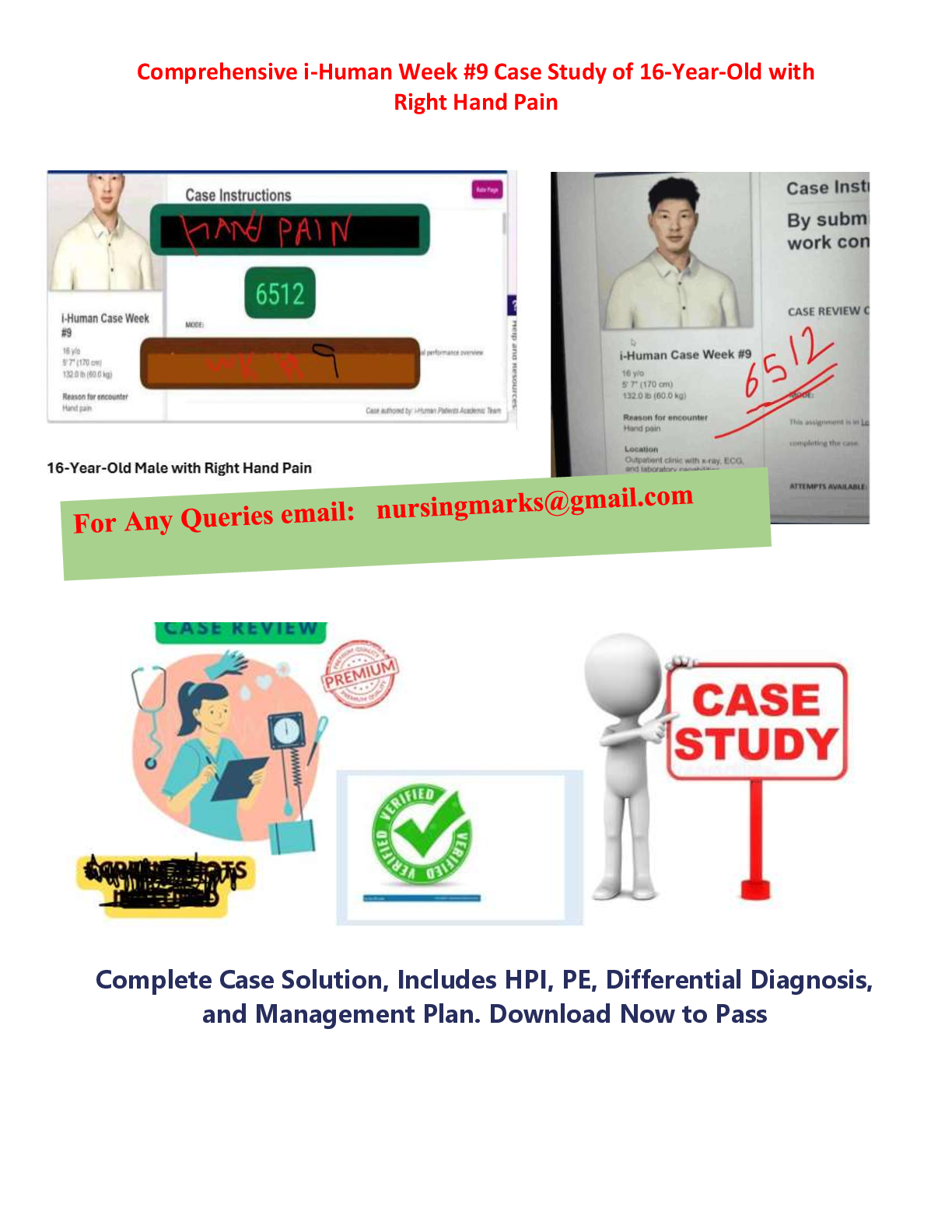
NHA Phlebotomy Certification Exam Key Concepts & Procedures / Score 100% / New 2025 Update / Complete Study Guide
$ 20.5

MLS ASCP EXAM 2025/2026
$ 23

Responsible Serving of Alcohol Exam 49 Questions with Answer,100% CORRECT
$ 8

Test Bank For Medical Terminology For Health Professions, Spiral Bound Version 9th Edition Author-Ann Ehrlich, Carol Schroeder, Laura Ehrlich, Katrina Schroeder Chapter 1-15 Newest Version
$ 20

PMHNP CERTIFICATION EXAM TESTBANK 2023 1818
$ 14
.png)
The Offensive Movie Cliche That Won't Die Rhode Island College FYW 100
$ 4

Safety and Infection Control NCLEX Questions and Answers
$ 7

Certified Medication Aide Exam 1
$ 5

Facilities Design, 5e by Sunderesh Heragu (Solutions Manual)
$ 25
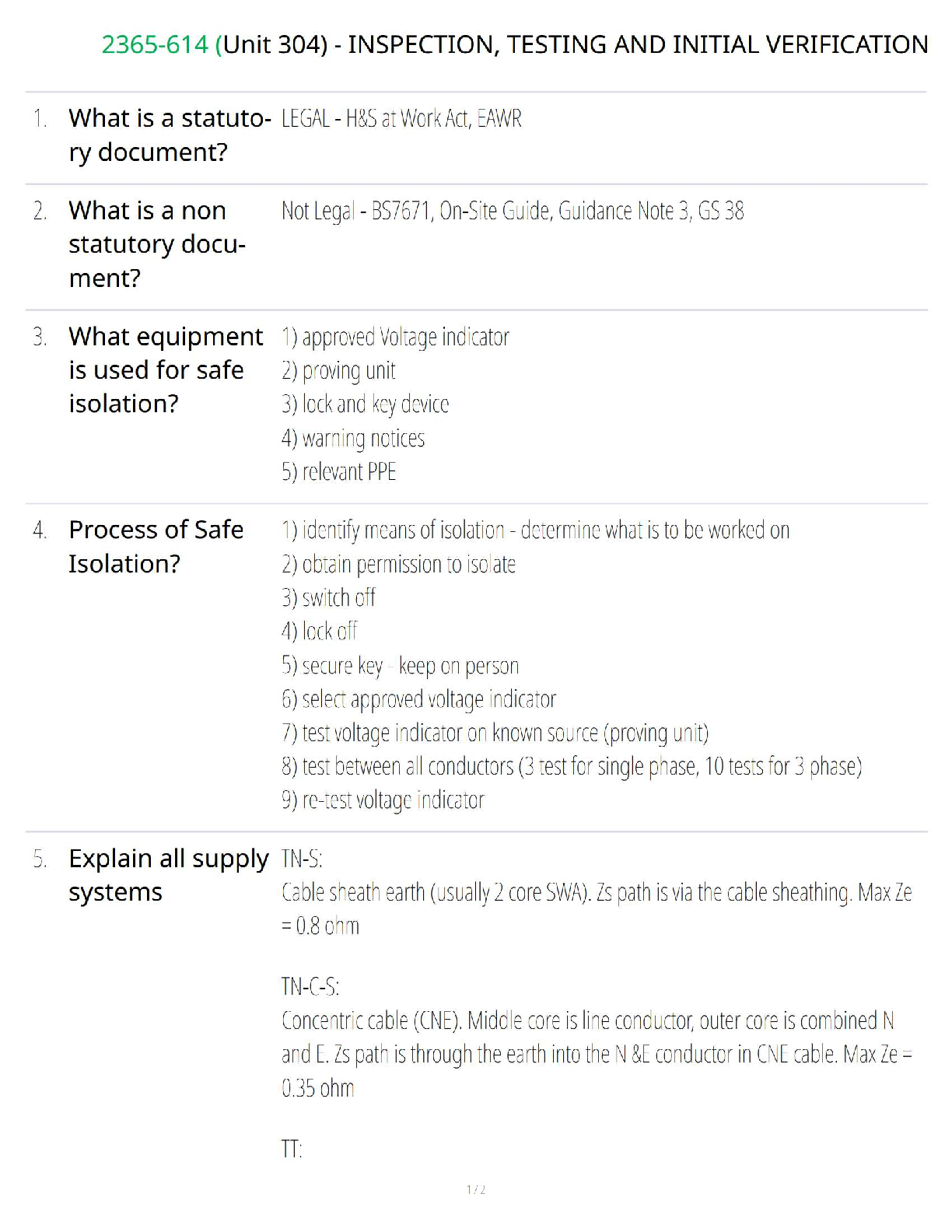
🔧 2365-614 (Unit 304) – Inspection, Testing and Initial Verification Study Guide Verified Assessment Tasks Electrical Installation Principles Grade A
$ 8.5
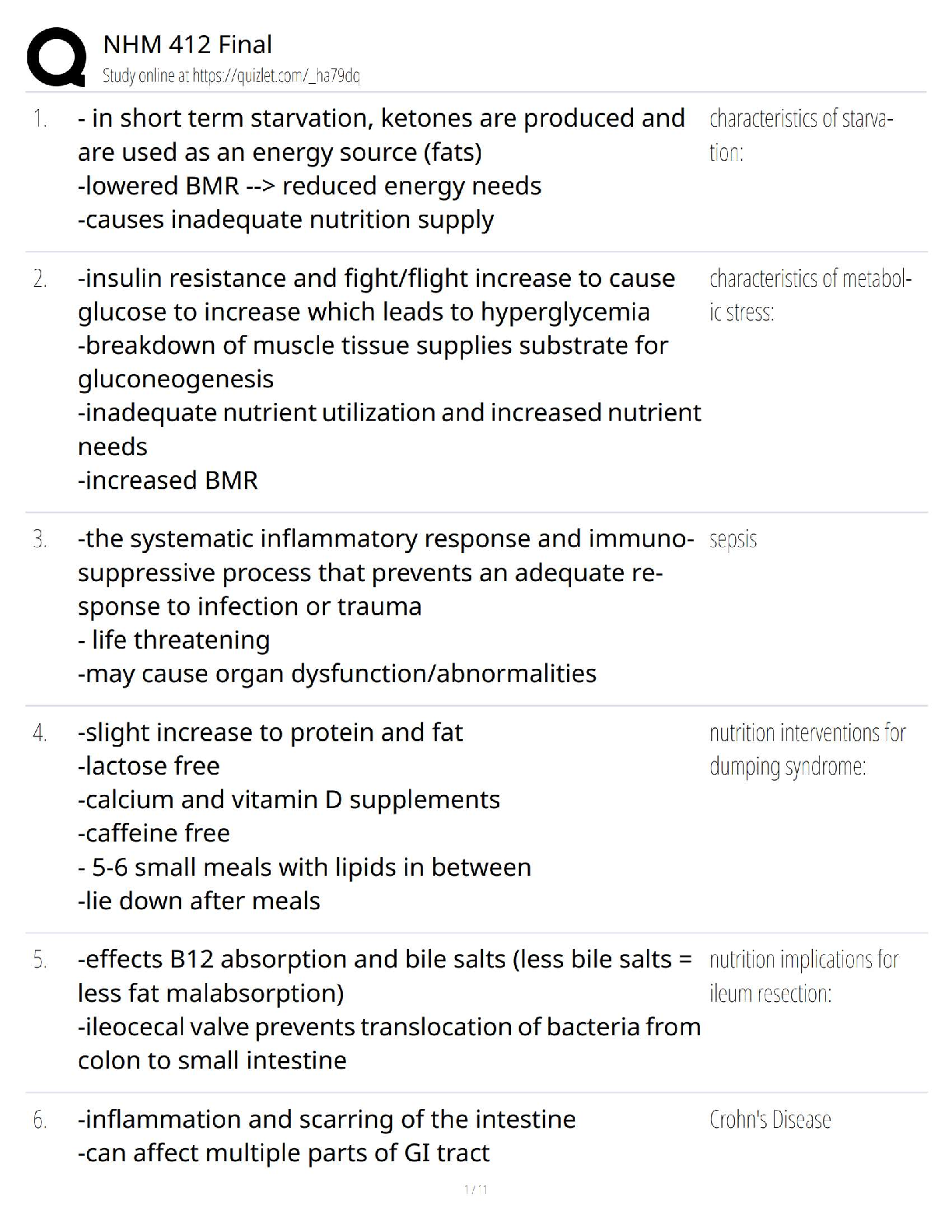
NHM 412 Final
$ 10

DISASTER MANAGEMENT CYCLE
$ 5

CLG 0010 DoD Government wide Commercial Card Exam Questions and answers. Rated A+
$ 7

EDEXCEL A LEVEL JUNE 2022 ENGLISH LANGUAGE QUESTION PAPER 3
$ 1

2023 NFHS Baseball Part I Test (WIAA) All Questions and Answers Complete
$ 11
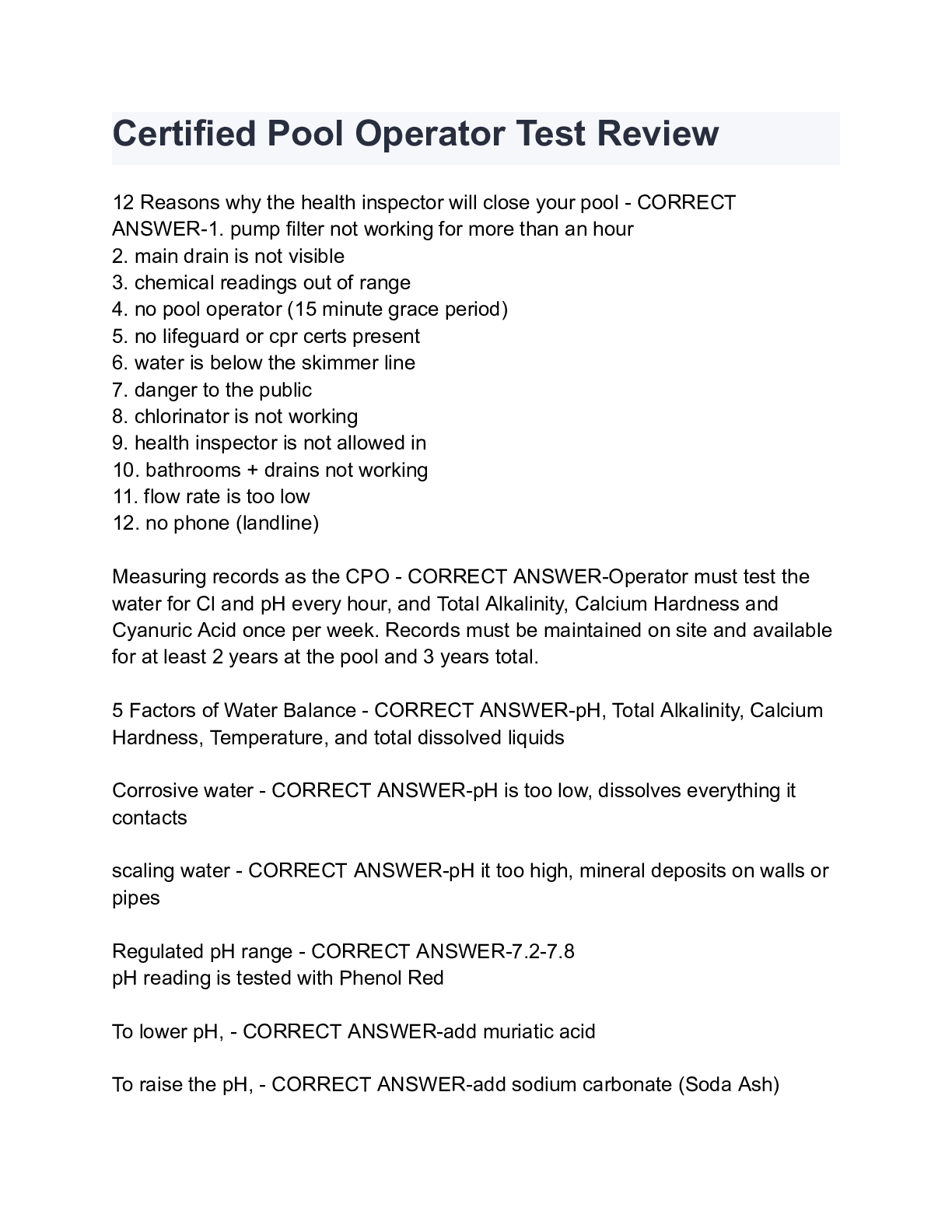
Certified Pool Operator Test Review
$ 7
 with complete Questions and Answers.png)
OCI Architect Associate (1Z0-1072) with complete Questions and Answers
$ 8.5

OCR A Level Drama and Theatre H459/43 Deconstructing Texts for Performance Earthquakes in London QUESTION PAPER Tuesday 21 June 2022 – Morning
$ 7

Pearson BTEC Level 1/Level 2 First Award Children’s Play, Learning and Development UNIT 1: Patterns of Child Development QUESTION PAPER 2022
$ 8
.png)
Module Report ;Real Life RN Nursing Care of Children 2.0: Gastroenteritis and Dehydration
$ 10

HESI A2 – GRAMMAR STUDY GUIDE 2022
$ 10
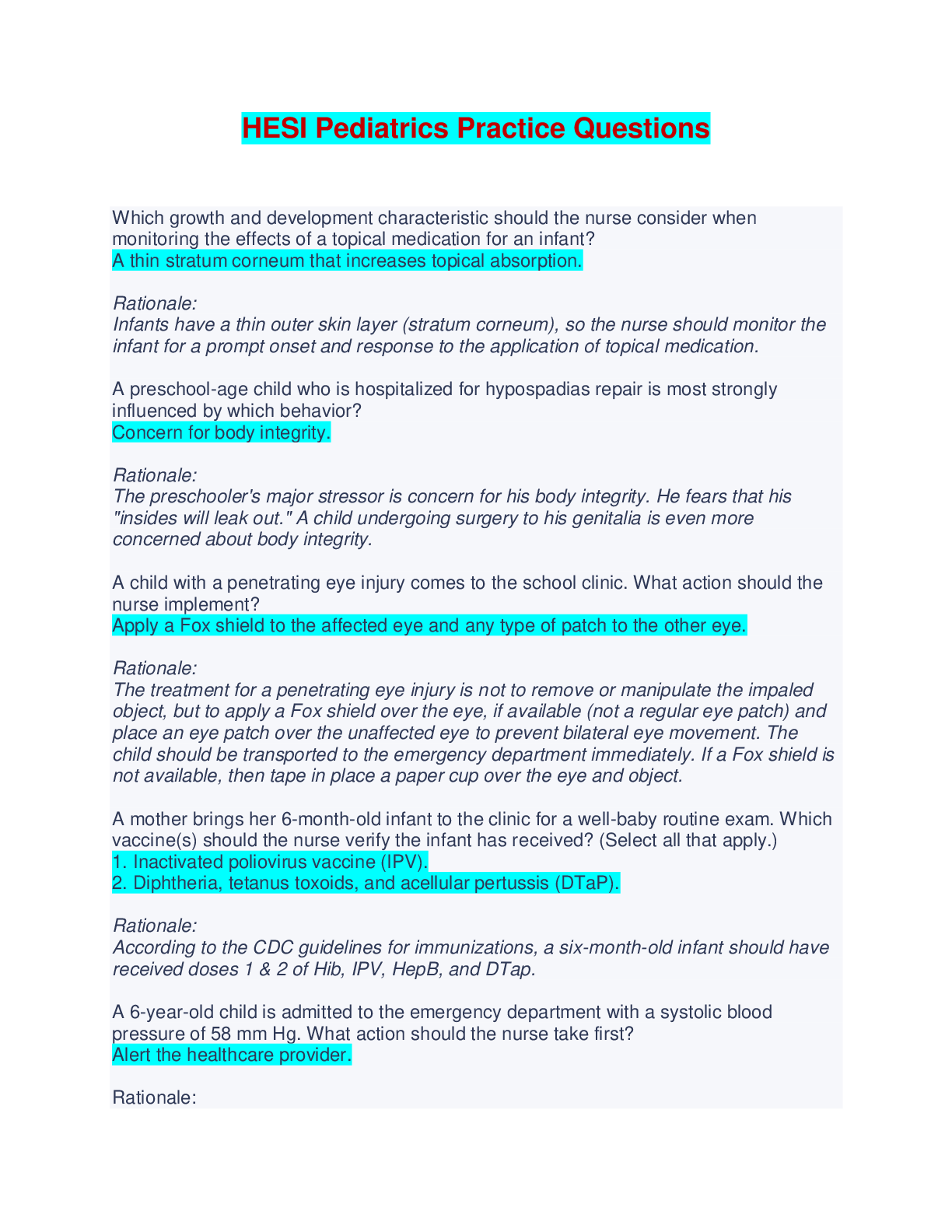
HESI Pediatrics Practice Questions - Answered with Rationales
$ 20

captains career course amedd Exam Questions and Answers 2023
$ 10

Review > 12.1-12.2_Lesson Review 1. How does a stretching warm-up differ from a flexibility (stretching) workout? 2. What is flexibility, and what factors influence it? 3. What are the benefits of good flexibility? 4. What are the types of flexibility exercises, and what is the FIT formula for each?
$ 4

PRACTICE EXAM FIREFIGHTER With Complete Solutions
$ 10

NURSING CARE PLAN
$ 10

ATLS_POST_TEST_EXAM,_ACTUAL_EXAM_ALL_QUESTIONS_AND_100_CORRECT_ANSWERS
$ 15

Fire Fighter 1 Study Guide (286 Questions with 100% Correct Answers)
$ 10

Breast Feeding Initiation Rate Across Western Countries Does Religion Matter? An Ecological Study
$ 10

IFSTA 7th Edition Written Exam Questions & Answers, (Complete)
$ 8.5

WGU C715 Organizational Behavior - Ch.7 Motivational Behavior, Top Exam Questions and answers, graded A+
$ 6

ANSC 4395 exam 3 QUESTIONS AND ANSWERS GRADED A
$ 5

Case Study 2
$ 7

MANAGEMENT 419 - The role and relevance of resource planning in the quality of service delivery in Health and Social Care.
$ 10

Groupthink Journal Article (Latest) 2020/2021
$ 12

Database Systems Class Notes
$ 6.5

Summary of ‘The Cruel Birth of Bangladesh_ School of General EducationEMB101: Emergence of Bangladesh
$ 8.5

Home Inspection Exam Prep Questions and Answers Graded A+
$ 15

eBook [PDF] Poetry of the New Woman Public Concerns, Private Matters 1st Edition By Patricia Murphy
$ 29

TEST BANK for Sports and Exercise Nutrition 5th Edition by William D. McArdle
$ 24

NURS 6501 FINAL EXAM 2023 WALDEN UNIVERSITY LATEST FILE A+
$ 6.5

PSY340 book summaries{ for A+ grade}
$ 13.5

APEA 3P RESPIRATORY 100 QUESTION AND ANSWER 2025
$ 8

CPC MEDICAL CODING TRAINING MIDTERM & FINAL EXAM 2024-2025 QUESTIONS AND VERIFIED ANSWERS
$ 17

Applied Statistics and Probability for Engineers, 7e Montgomery, Runger (eBook PDF)
$ 25

Purple Book NBCOT Prep ALL ANSWERS 100% CORRECT LATEST SOLUTION RATED GRADE A+
$ 14.5

Organizational Behavior Emerging knowledge, global reality, 9th Edition by McShane Test Bank
$ 35
Eastern Gateway Community College MGT 202 Organizational Behavior: Final Exam 2021: Organizational Behavior - MGT202_1012. Quiz Score: 97 out of 100
$ 10

SUMMARY > Summary of Quality and Trustworthiness in Qualitative Research in Counseling Psychology. Far Eastern University PSY 302









 is routinely diagnosed by detecting the presence of specific antibodies in the patient.png)