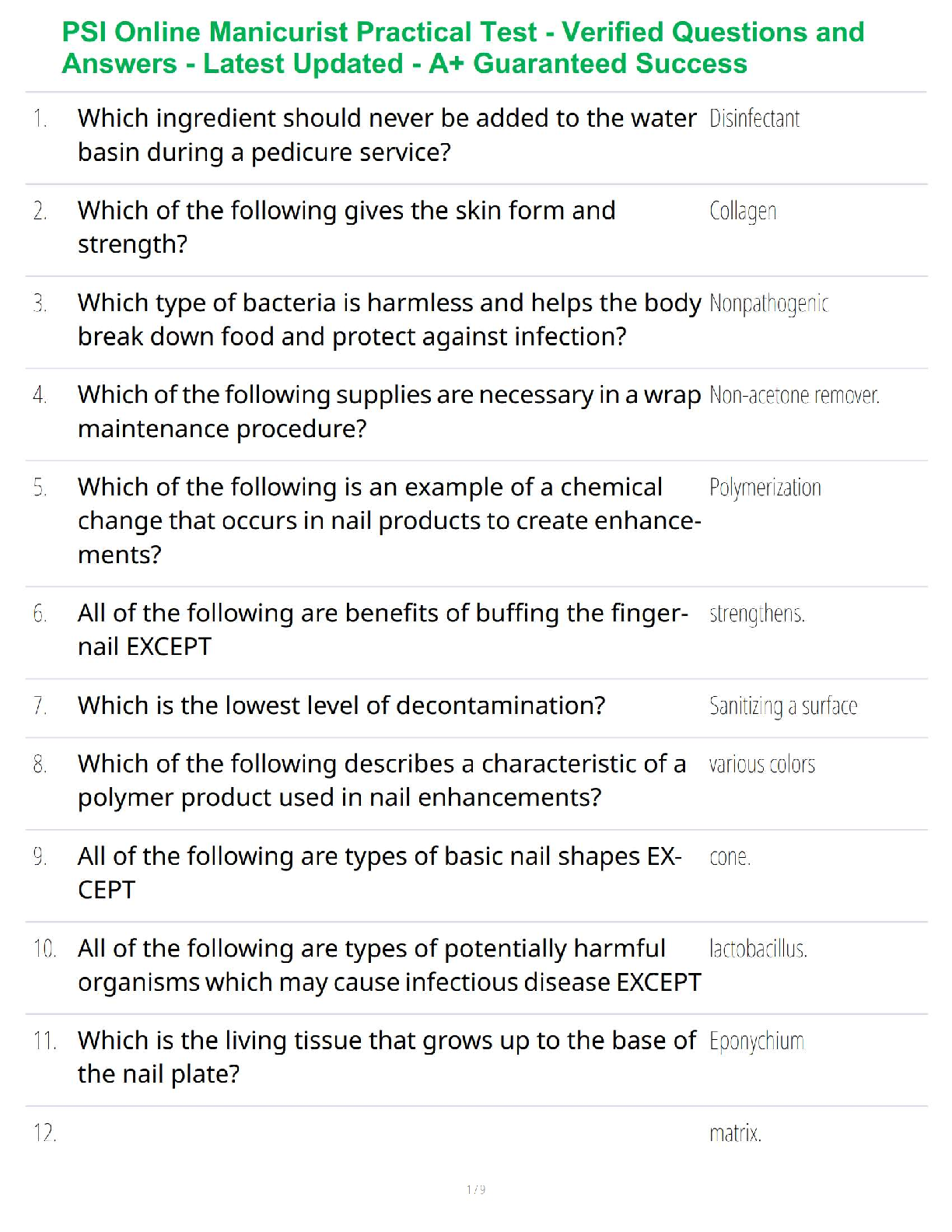
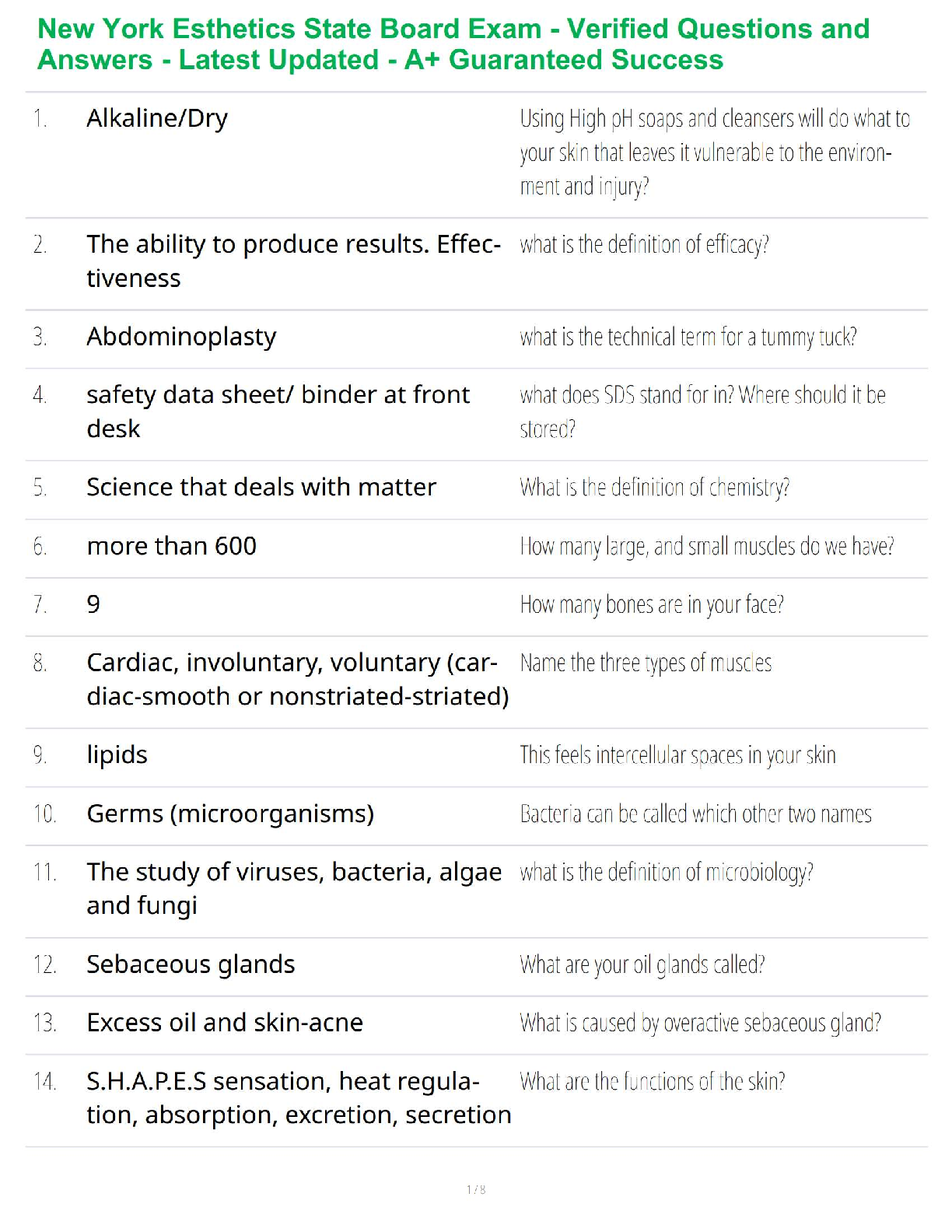
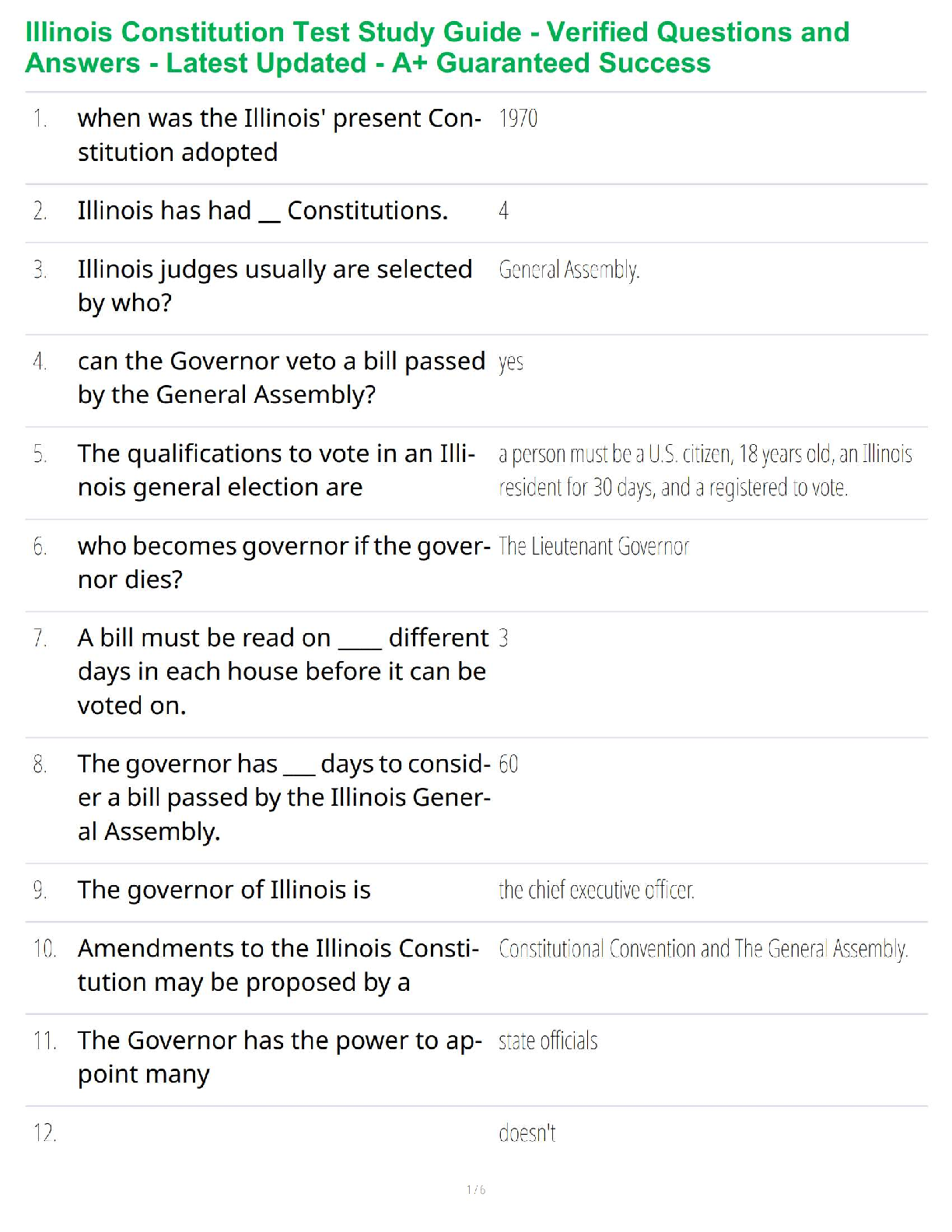
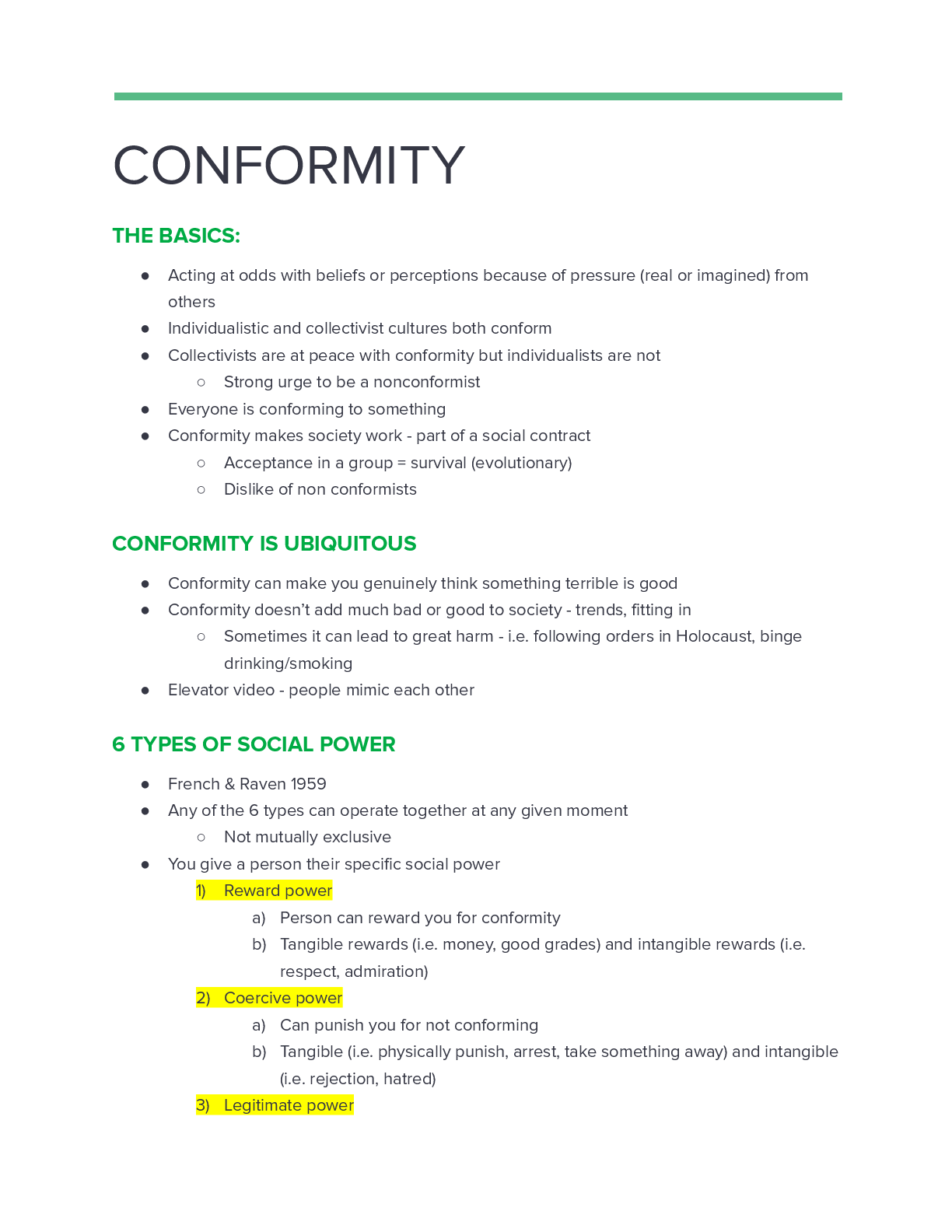
WGU D487 Pre-Assessment Secure Software Design KEO1 PKEO – Guaranteed Success with Verified Questions and Answers
$ 8.5

University of California, BerkeleyDATA 8 DATA8project3-Copy1-GRADED A
$ 20

HESI Maternity 2 2021
$ 8.5

AST 113 ASTRONOMY Lab 12
$ 9

NR 511 - Acute Otitis Externa CPG : Chamberlain College of Nursing.
$ 8

Software Engineering A Practitioner's Approach, 9th Edition By Roger Pressman, Bruce Maxim | [eBook] [PDF]
$ 19

D081-QBM3 Task 1 / Analyzing Organizational Culture & Structure at USFBM / Score 100% / New Version 2025 Update
$ 11

TEST BANK COMPLETE 200 QUESTIONS AND CORRECT DETAILED ANSWERS BRAND NEW! (VERIFIED ANSWERS) ALREADY GRADED A+ ATI RN MED SURG PROCTORED EXAM NEWEST 2024
$ 32.5

FLUID MECHANICS PUMPS LAB REPORT ( WELL WRITTEN )