CMIT 321 Final Exam Version 2
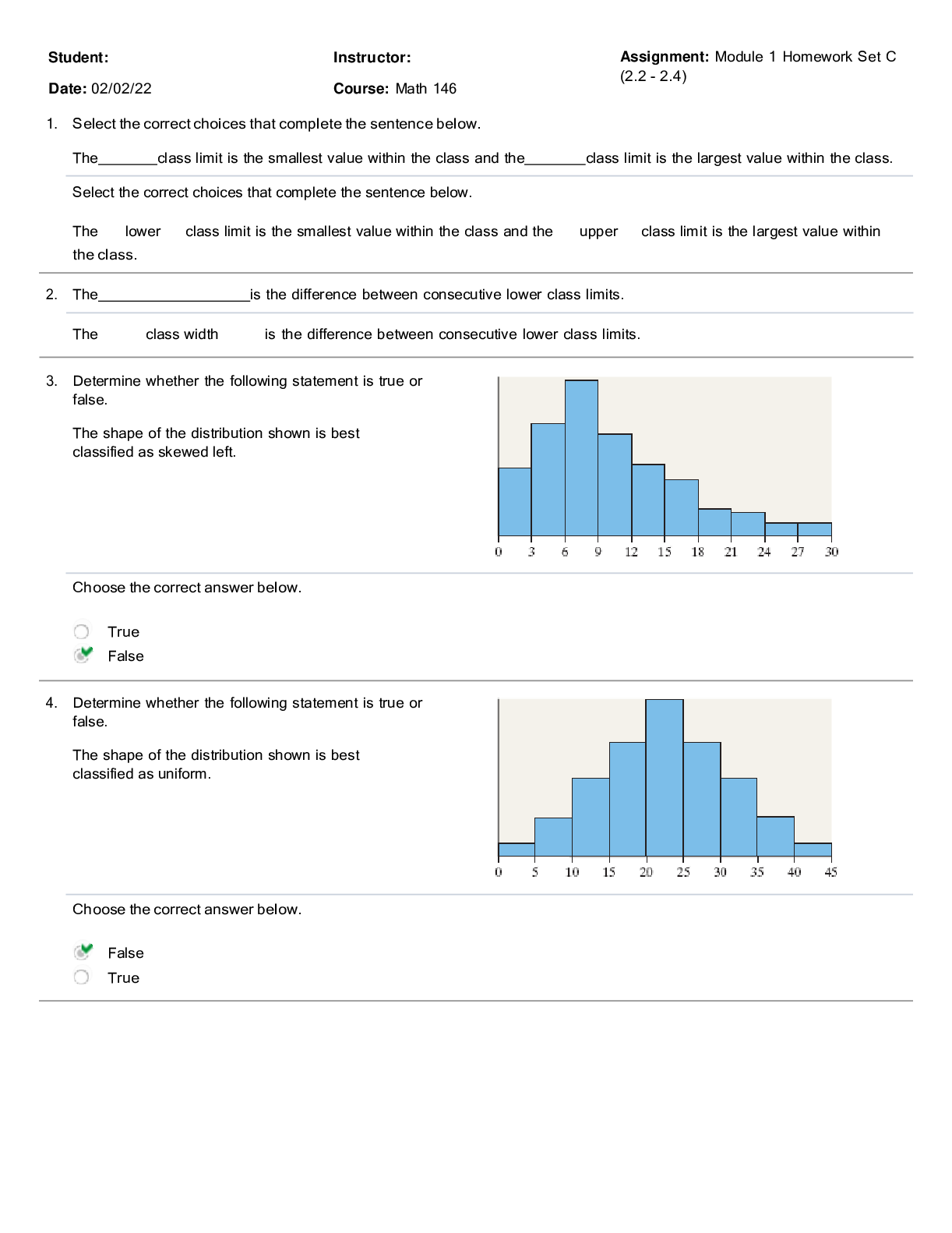
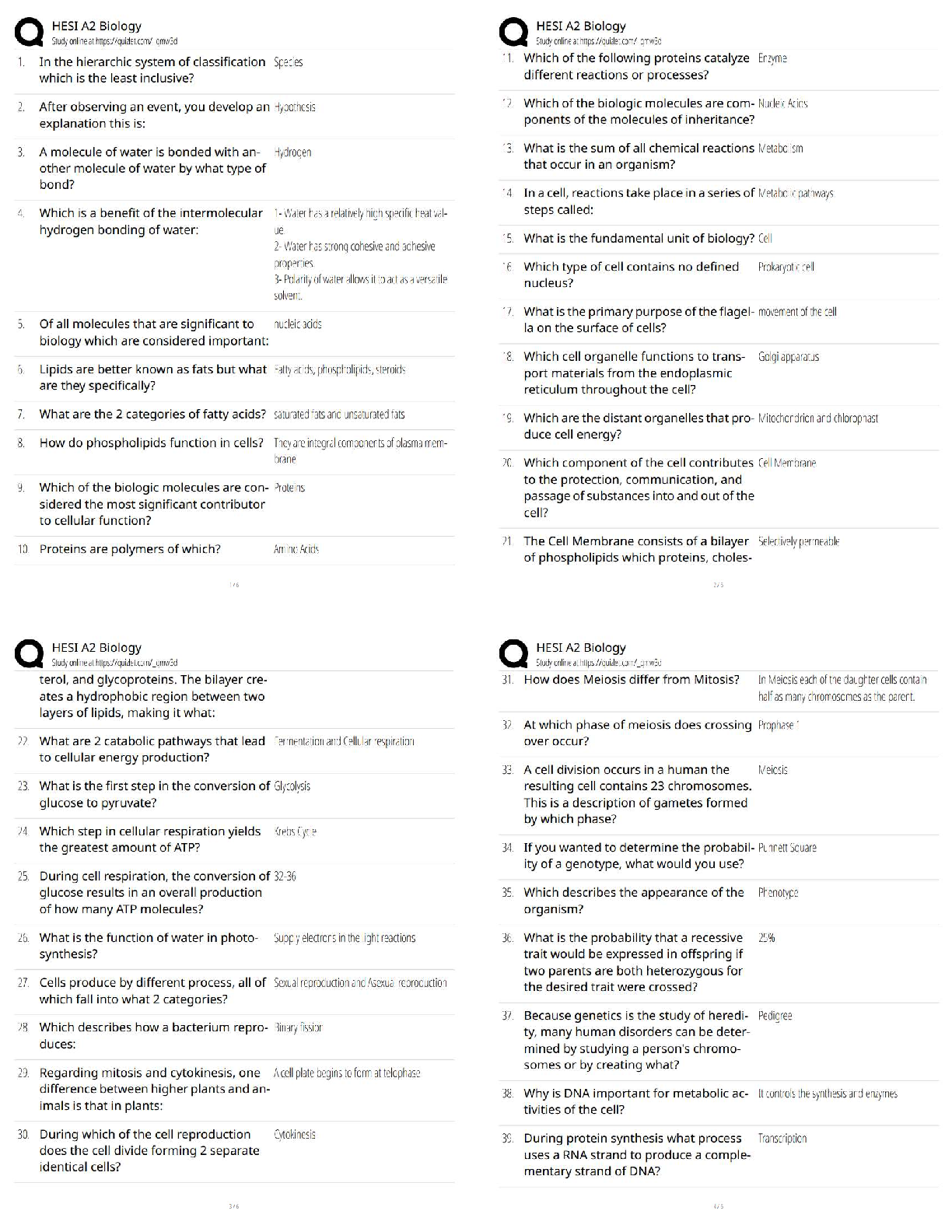
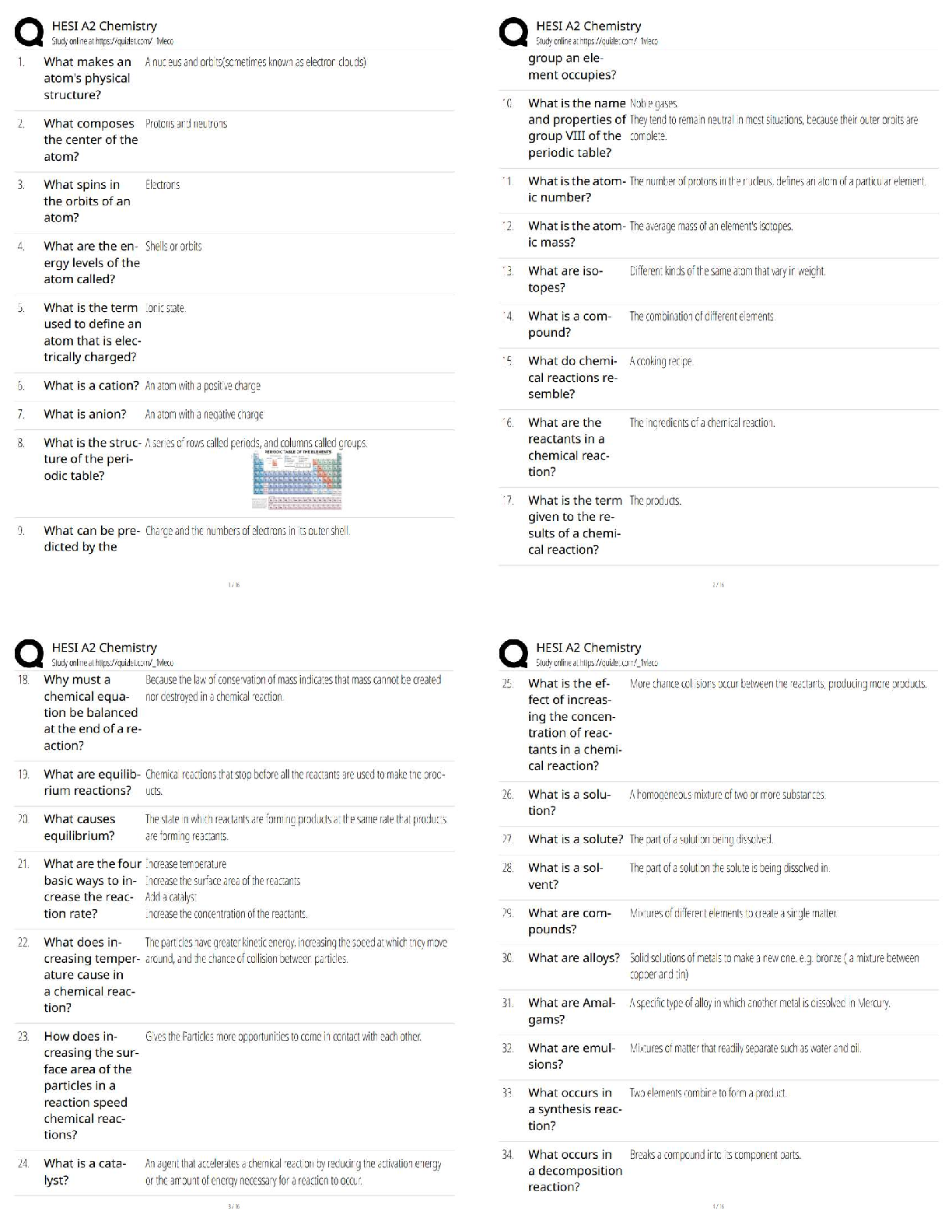
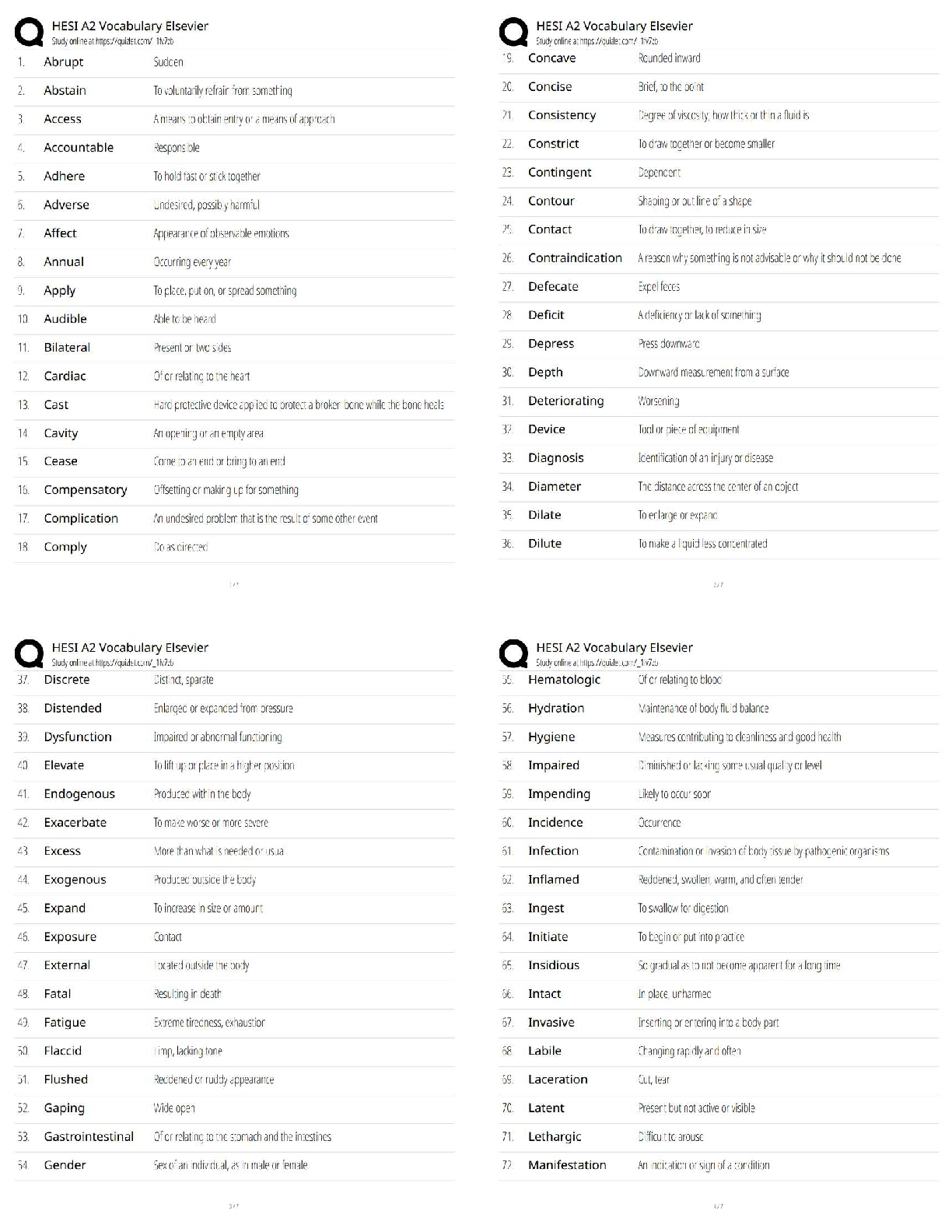
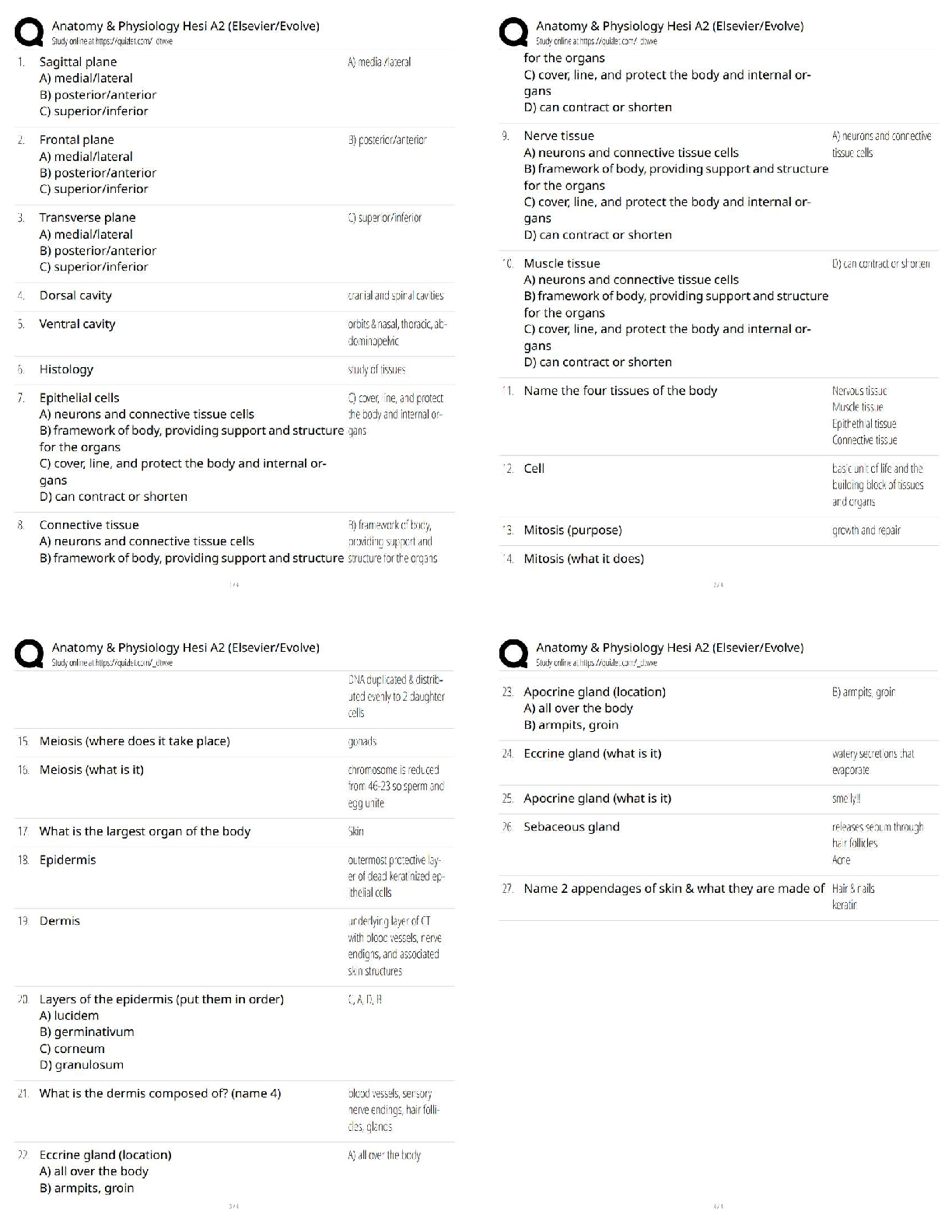
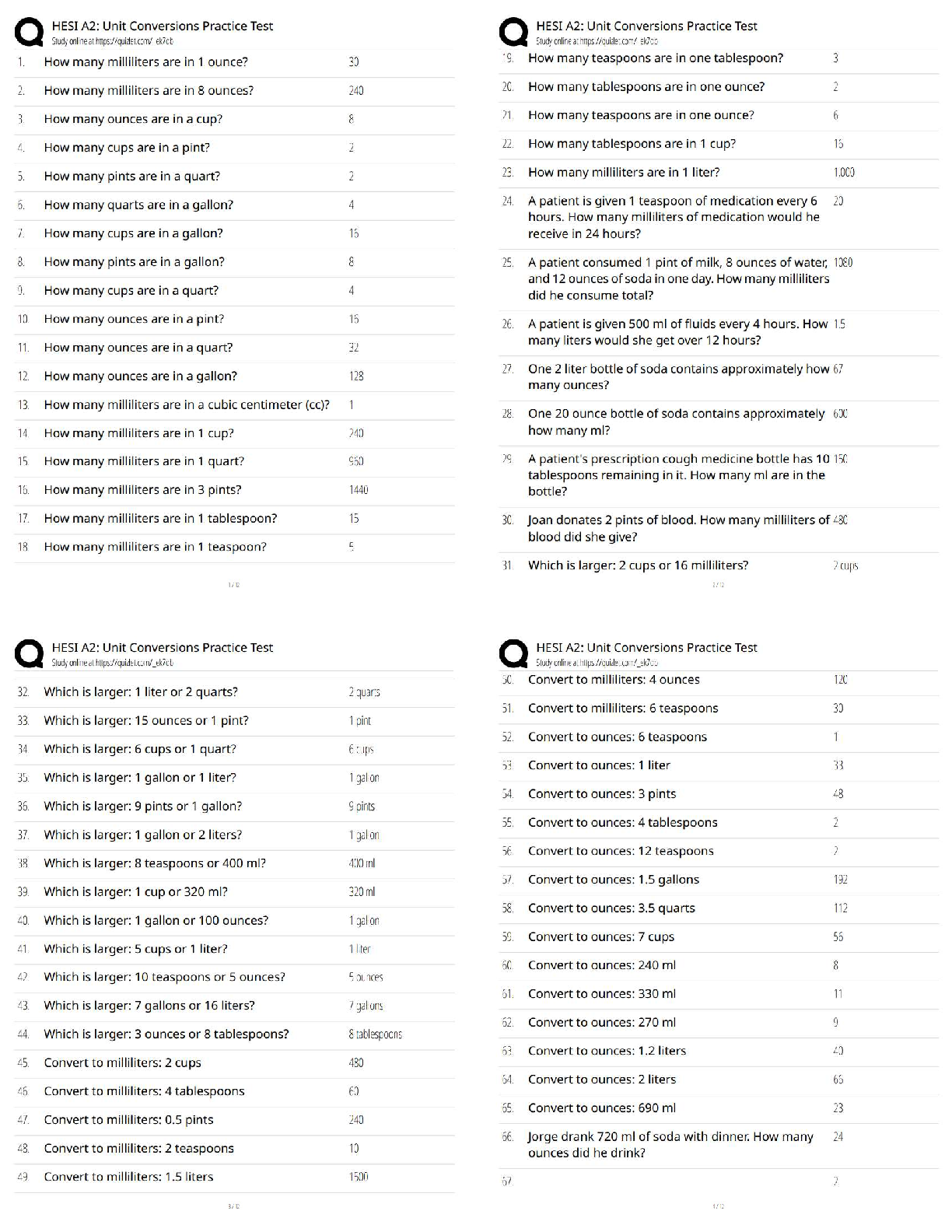
n 1 1 / 1 point
A __________ is a device that receives digital signals and converts them into analog signals, and vice
versa.
a. firewall
b. proxy
c. hub
d. modem
View Feedback
n 2
...
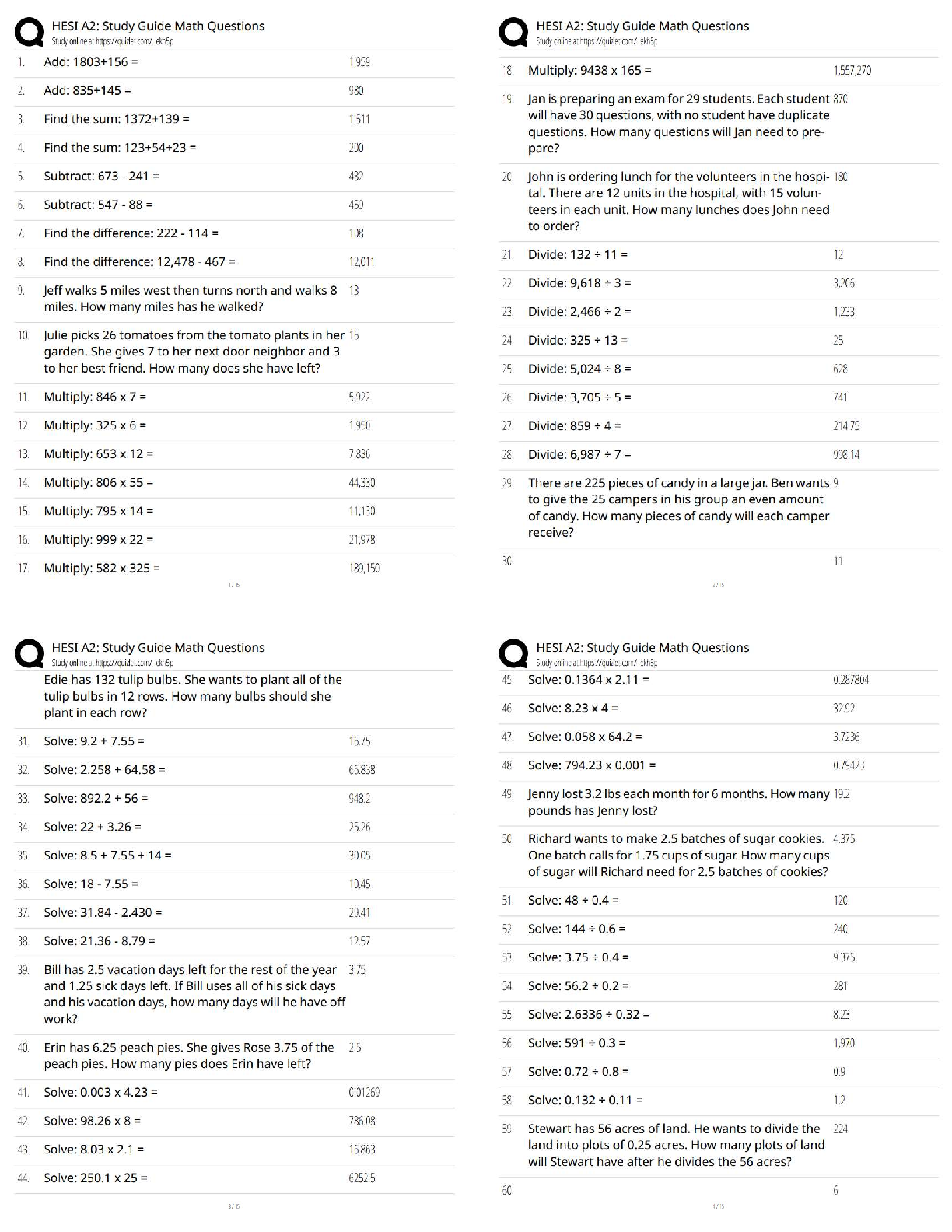
CMIT 321 Final Exam Version 2
n 1 1 / 1 point
A __________ is a device that receives digital signals and converts them into analog signals, and vice
versa.
a. firewall
b. proxy
c. hub
d. modem
View Feedback
n 2 1 / 1 point
__________ is a parallelized login cracker that supports numerous protocols for attack.
a. ADMsnmp
b. SING
c. Hydra
d. John the Ripper
View Feedback
n 3 1 / 1 point
An __________ share is a hidden share that allows communication between two processes on the same
system.
a. SMC
b. IPC
c. EPC
d. SMB
View Feedback
n 4 1 / 1 point
__________ monitors and audits databases for security issues in real time.
a. Selective Audit
b. AppDetective
c. AppRadar
d. FlexTracerCMIT 321 Final Exam Version 2
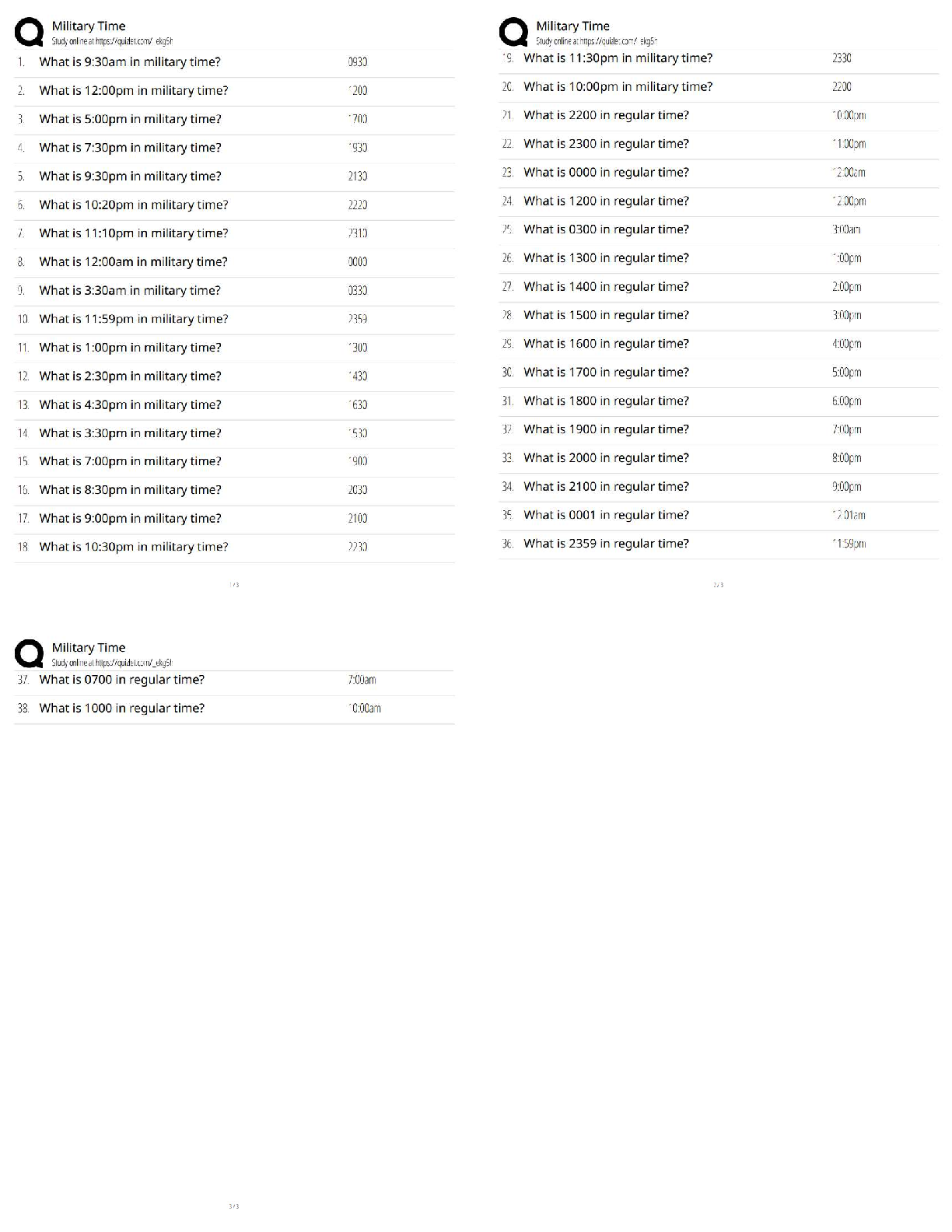
View Feedback
n 5 1 / 1 point
__________ is a command-line utility provided by Microsoft with SQL Server 2000 (and Microsoft SQL
Server 2000 Desktop Engine) that allows users to issue queries to the server.
a. ODBC
b. SQLP
c. OSQL
d. SSRS
View Feedback
n 6 1 / 1 point
__________ allows applications to read and write various image file formats, including GIF.
a. ImageCore
b. CoreText
c. ImageIO
d. CoreImage
View Feedback
n 7 1 / 1 point
Which of the following types of tools would be most effective in cracking UNIX passwords?
a. Ophcrack
b. KerbCrack
c. John the Ripper
d. RainbowCrack
View Feedback
n 8 1 / 1 point
A __________ is a device that cannot function in any capacity.
a. block
b. brick
c. rock
d. cageCMIT 321 Final Exam Version 2
View Feedback
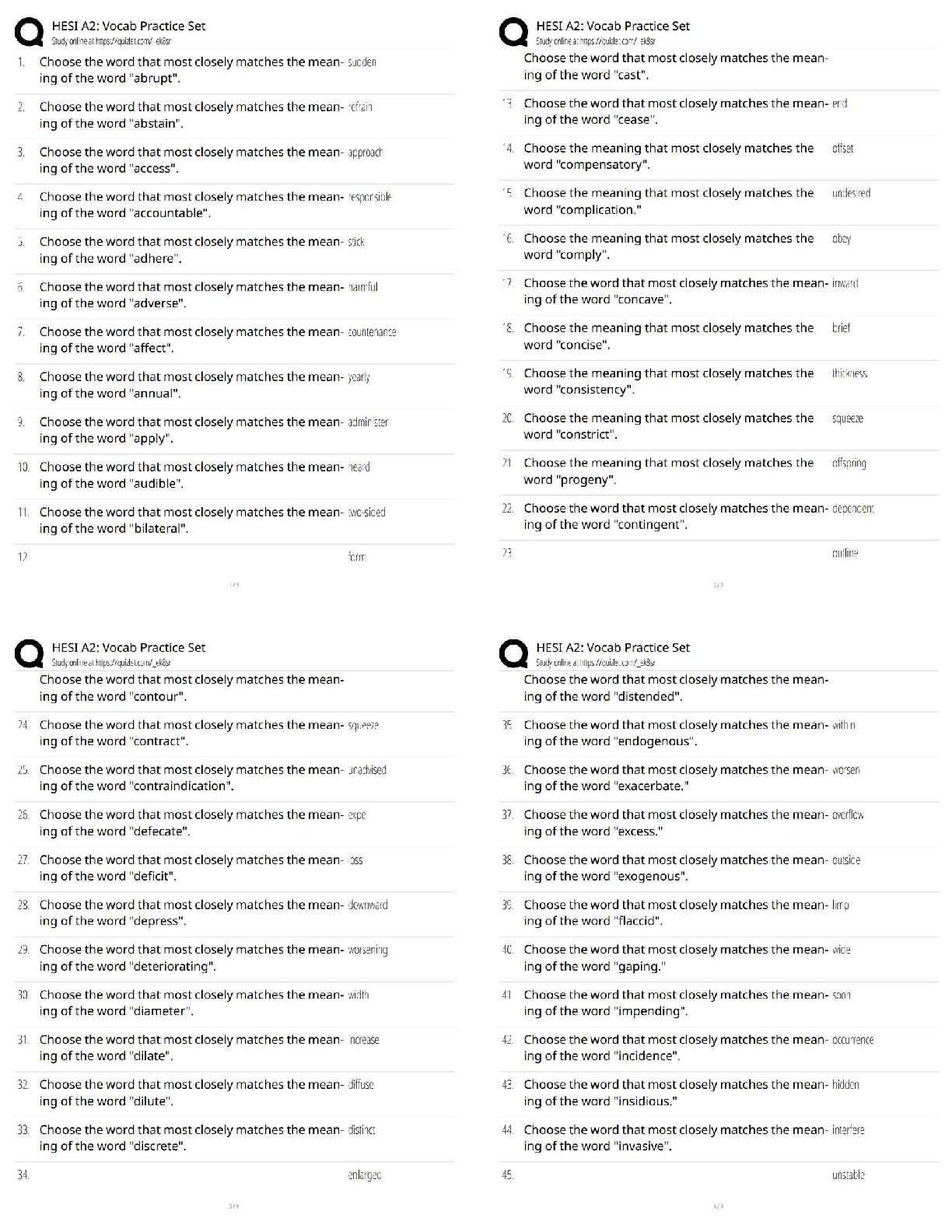
n 9 1 / 1 point
__________ can monitor a Simple Mail Transfer Protocol (SMTP) server regularly after connecting to it.
a. CheckOK
b. SMTPCheck
c. SMTPMon
d. SLCheck
View Feedback
n 10 1 / 1 point
In a hit-and-run attack, __________.
a. the attacker constantly injects bad packets into the router
b. the attacker mistreats packets, resulting in traffic congestion
c. the attacker injects a few bad packets into the router
d. the attacker alters a single packet, resulting in denial of service
View Feedback
n 11 1 / 1 point
__________ is the act of gathering information about the security profile of a computer system or
organization, undertaken in a methodological manner.
a. Tracerouting
b. Passive information gathering
c. Footprinting
d. Competitive intelligence gathering
View Feedback
n 12 1 / 1 point
__________, formerly called AppTapp, is a tool for jailbreaking and installing nonsanctioned third-party
applications on the iPhone.
a. iFuntastic
b. iNdependence
c. iActivator
d. AppSnappCMIT 321 Final Exam Version 2
View Feedback
n 13 1 / 1 point
__________ is a tool for performing automated attacks against web-enabled applications.
a. cURL
b. dotDefender
c. Burp Intruder
d. AppScan
View Feedback
n 14 1 / 1 point
A __________, also called a packet analyzer, is a software program that can capture, log, and analyze
protocol traffic over the network and decode its contents.
a. sniffer
b. recorder
c. logger
d. tapper
View Feedback
[Show More]













.png)

.png)